Method for establishing trust model of wireless sensor network
A wireless sensor and trust model technology, applied in wireless communications, services based on specific environments, electrical components, etc., can solve the problems of low detection rate of untrustworthiness and inaccurate measurement of trust, and achieve the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
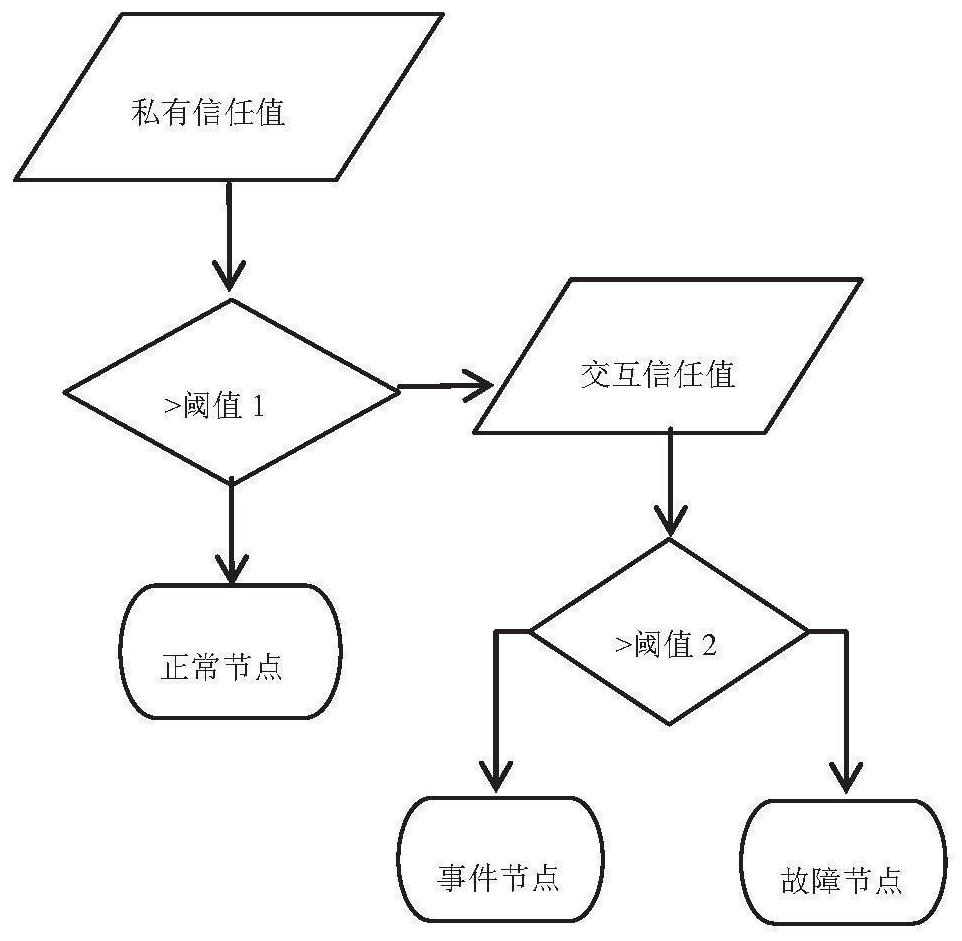
[0053] The method for establishing the wireless sensor network trust model of the present invention comprises the following steps:
[0054] 1. Construct interactive communication factors
[0055] The communication in the interaction factor is defined as: the continuous effective communication rate within Δt time, that is:
[0056]
[0057] Among them, s i,k (Δt) is the number of successful communication between nodes i and j at Δt, f i,j (Δt) is the number of communication failures between nodes i and j at time Δt. When the number of failures is greater than the number of successes, the two nodes i and j are considered untrusted. by dividing by Make the communication factor drop sharply. In particular, if f i,j (Δt) = 0, set DCT i,j (Δt)=100.
[0058] 2. Construct interactive data factors
[0059] The data in the interaction factor is defined as: the similarity rate of continuous data within Δt time, that is in
[0060] c i,j (Δt) is the number of data similar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com