Cryptographic technology security control method and system for core table data
A cryptographic technology and table data technology, applied in the direction of digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of hidden safety hazards, no supervision, etc., and achieve the effect of eliminating attacks, reducing the possibility, and reducing the requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] This example specifically illustrates the implementation of the method of the present invention.
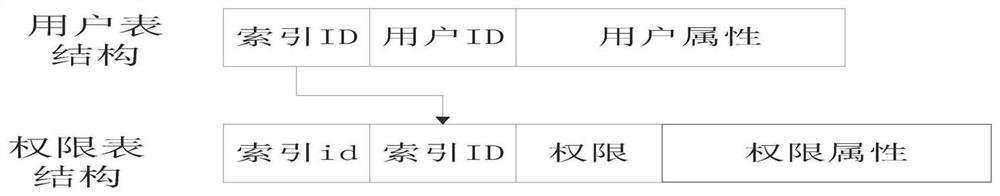
[0054] 1. Classify the database table structure and data according to the conventional user table structure, permission table structure, and pure data table structure
[0055] Existing information systems generally use user tables, permission tables, and business data tables to roughly classify them. There are also tables that integrate users and permissions into a single table, or create tables by hierarchical indexing according to data volume. No matter how the table is built, its purpose is to realize the application design under the premise of the minimum amount of calculation, so as to improve the response speed of the information system.
[0056] The data reorganization of this system in this system is equivalent to initializing the table structure to prepare for the subsequent implementation of cryptographic technology. The user table structure and authority table s...
Embodiment 2
[0090] This embodiment specifically illustrates the implementation of the system of the present invention.
[0091] A cryptographic technology security control system for core table data, including:
[0092] Database, a collection of various tables used to store business data;
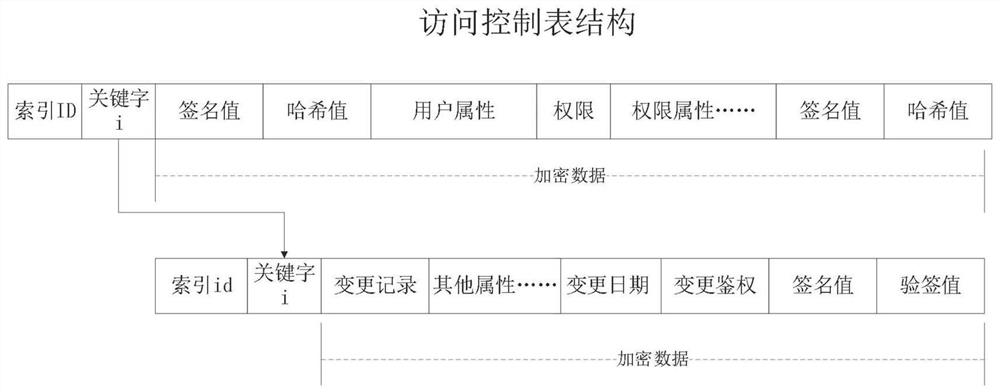
[0093]The data tables stored in the database are processed based on the following method: the user table structure and the authority table structure in the database are extracted to establish an access control table for the database, and the user access information is counted based on the user table and authority table data, according to the multiplier of the access frequency Perform statistical classification, set n-level access frequency, set up a frequency table, store index IDs, keywords and corresponding frequency grades and frequency attributes, and the frequency attributes store the attribute structure contained in the corresponding database index table, including data paths, Data characteristi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com