An authenticator and its communication method
An authenticator and client technology, applied in the field of communication, can solve the problems of low security, sensitive data theft, data insecurity, etc., and achieve the effect of improving security and ensuring interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
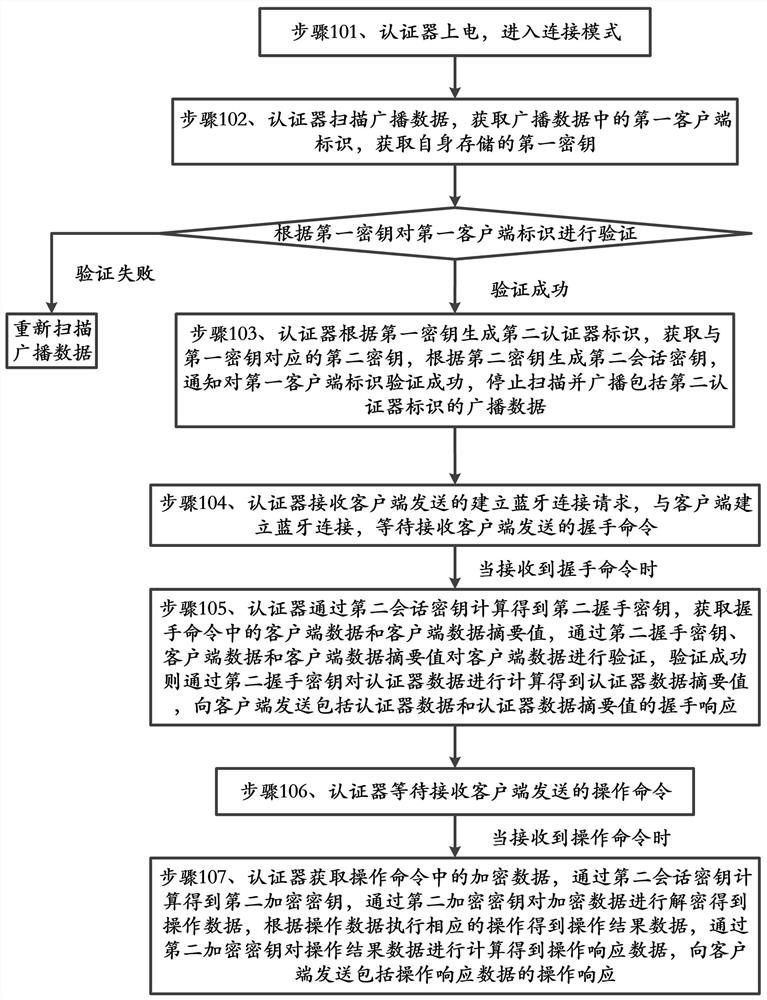
[0037] This embodiment provides a communication method for an authenticator, which is applicable to a system including a client and an authenticator, wherein the client is an application program installed in a mobile terminal with a Bluetooth function, and the authenticator has a Bluetooth function.
[0038] Such as figure 1 As shown, the method includes:
[0039] Step 101, the authenticator is powered on and enters the connection mode;
[0040] Step 102, the authenticator scans the broadcast data, obtains the first client ID in the broadcast data, obtains the first key stored by itself, and verifies the first client ID according to the first key, and if the verification is successful, execute step 103, If the verification fails, re-scan the broadcast data;
[0041] Step 103: The authenticator generates a second authenticator ID based on the first key, obtains a second key corresponding to the first key, generates a second session key based on the second key, and notifies th...
Embodiment 2
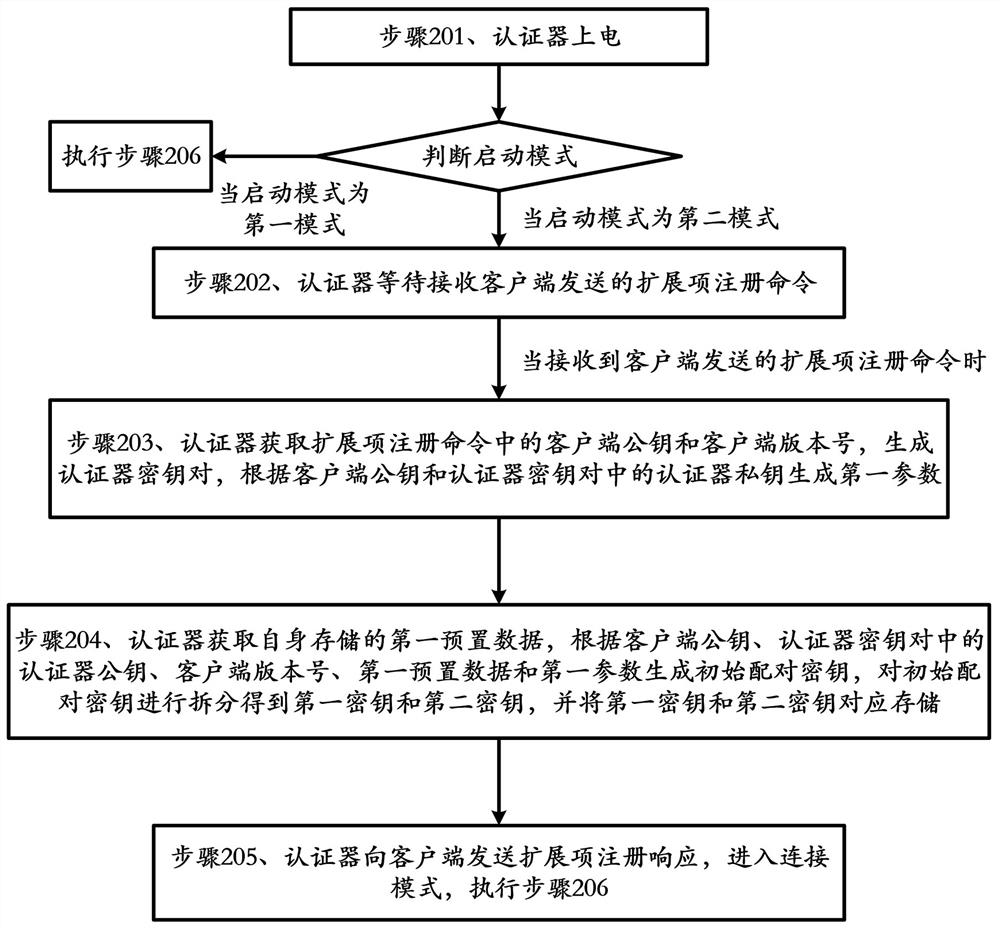
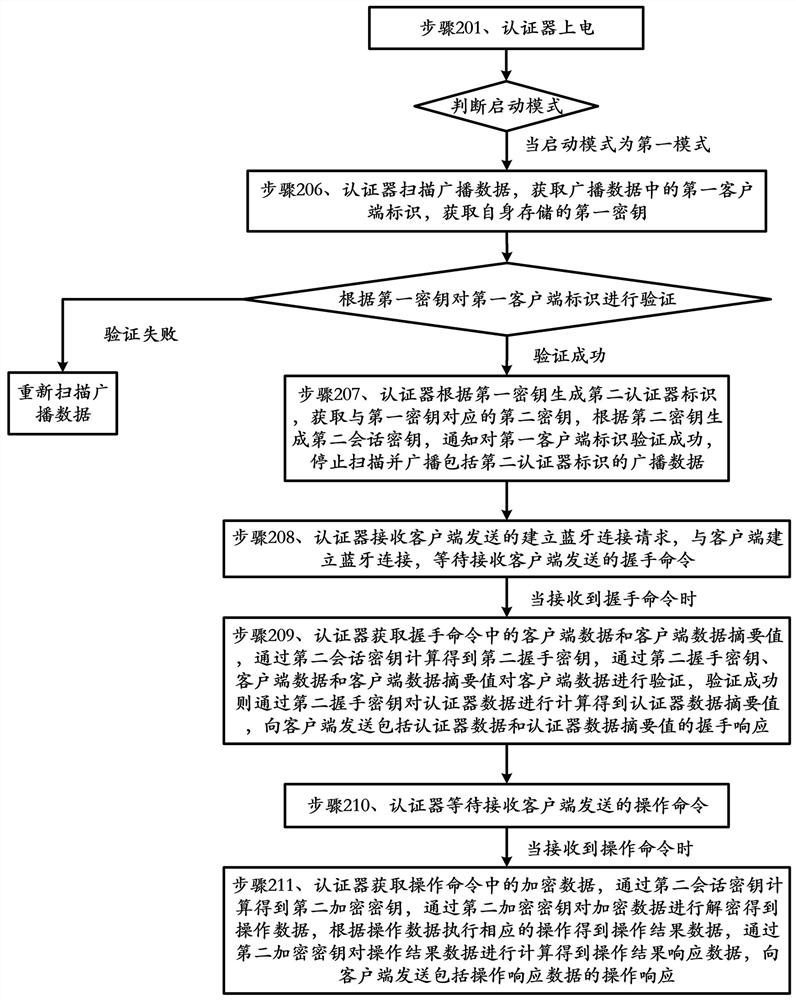
[0062] This embodiment provides a communication method for an authenticator, which is applicable to a system including a client and an authenticator, wherein the client is an application program installed in a mobile terminal with a Bluetooth function, and the authenticator has a Bluetooth function;
[0063] Such as figure 2 , 3 As shown, the method includes:
[0064] Step 201, the authenticator is powered on, and the startup mode is judged. When the startup mode is the second mode, it enters the pairing mode and executes step 202. When the startup mode is the first mode, it enters the connection mode and executes step 206;
[0065] In this embodiment, powering on the authenticator is specifically: when the key connected to the authenticator is pressed by the user, the authenticator is powered on;
[0066] Among them, the startup mode is specifically the type of key trigger;
[0067] Specifically, judging the startup mode specifically includes: the authenticator judges the...
Embodiment 3
[0189] Embodiment 3 of the present invention provides an authenticator, such as Figure 4 As shown, the authenticator includes:
[0190] The power-on processing module 11 is used to power on and enter the connection mode;
[0191] Scanning module 12, is used for scanning broadcast data, obtains the first client identification in broadcast data;
[0192] An acquisition module 13, configured to acquire the first key stored by itself;
[0193] The first verification module 14 is configured to verify the first client ID according to the first key;
[0194] The first generating module 15 is configured to generate a second authenticator ID according to the first key;
[0195] The obtaining module 13 is also used to obtain a second key corresponding to the first key;
[0196] The second generating module 16 is configured to generate a second session key according to the second key;
[0197] The notification module 17 is configured to notify that the identity v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com