Protection method for block interception attacks in block chains based on mining behaviors
A blockchain and behavioral technology, applied in the blockchain field, can solve problems such as inability to effectively reduce malicious miners, inability to effectively detect malicious miners, and inability to detect and eliminate malicious miners in a timely manner
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
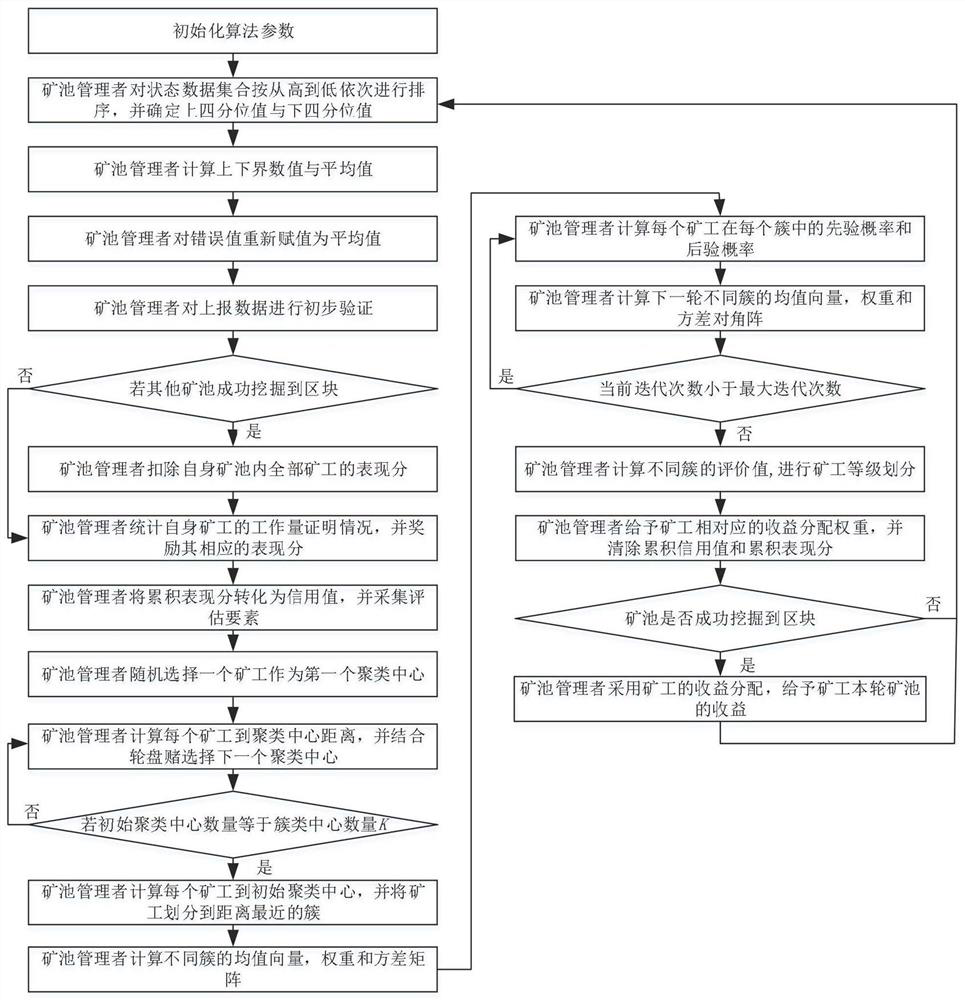
[0087] This embodiment discloses a protection method for block interception attacks in blockchain based on mining behavior, such as figure 1 As shown, it mainly includes the following steps:
[0088] Step 1): parameter initialization;
[0089] Initialize the number of miners N w and the number of mining pools N c , and initialize the following parameters: the number of errors, the number of offline times, the delay time and the threshold of the offline time Active time discrimination threshold ψ, performance score update factor The number of cluster centers K, the maximum number of iterations T max , the current number of iterations step=0 and other parameters;
[0090] Step 2): The mine pool manager preprocesses the data reported by the miners;
[0091] The mine pool manager uses the box plot detection algorithm to clean and normalize the data reported by the miners. If an error value is found, it will be replaced by the average value of the normal value. Among them,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com