Stamp safety management method, server and stamp
A security management and server technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as judicial injustice, company loss, fraud, etc., and achieve the effects of avoiding legal risks, eradicating injustice, and facilitating management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
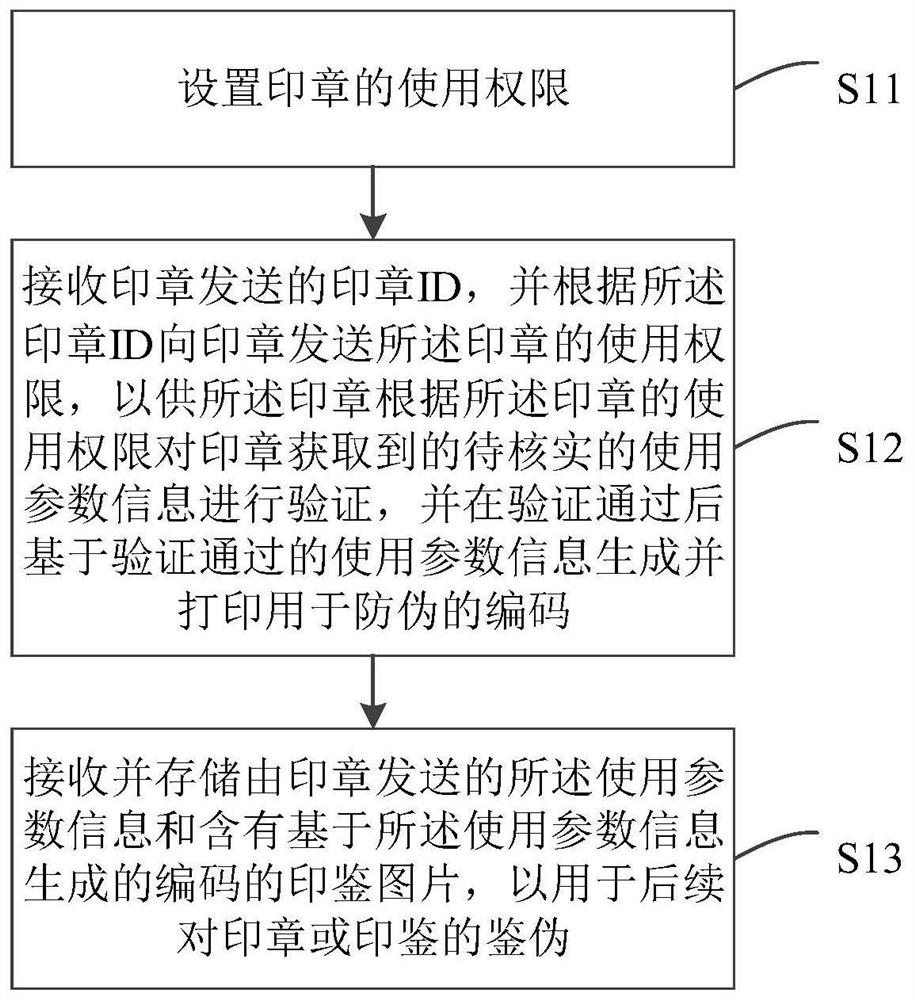
[0065] Embodiment 1 of the present invention provides a method for stamp security management, which is applied to a server, figure 1 It is a flowchart of a method for stamp security management according to Embodiment 1 of the present invention. Such as figure 1 As shown, the method includes:
[0066] Step S11: setting the usage authority of the seal;
[0067] Step S12: Receive the seal ID sent by the seal, and send the seal's use authority to the seal according to the seal ID, so that the seal can carry out the use parameter information to be verified obtained by the seal according to the use authority of the seal Verify, and after the verification is passed, generate and print an anti-counterfeiting code based on the verified use parameter information; and
[0068] Step S13: receiving and storing the use parameter information sent by the seal and the seal picture containing the code generated based on the use parameter information, for subsequent authentication of the seal...
Embodiment 2
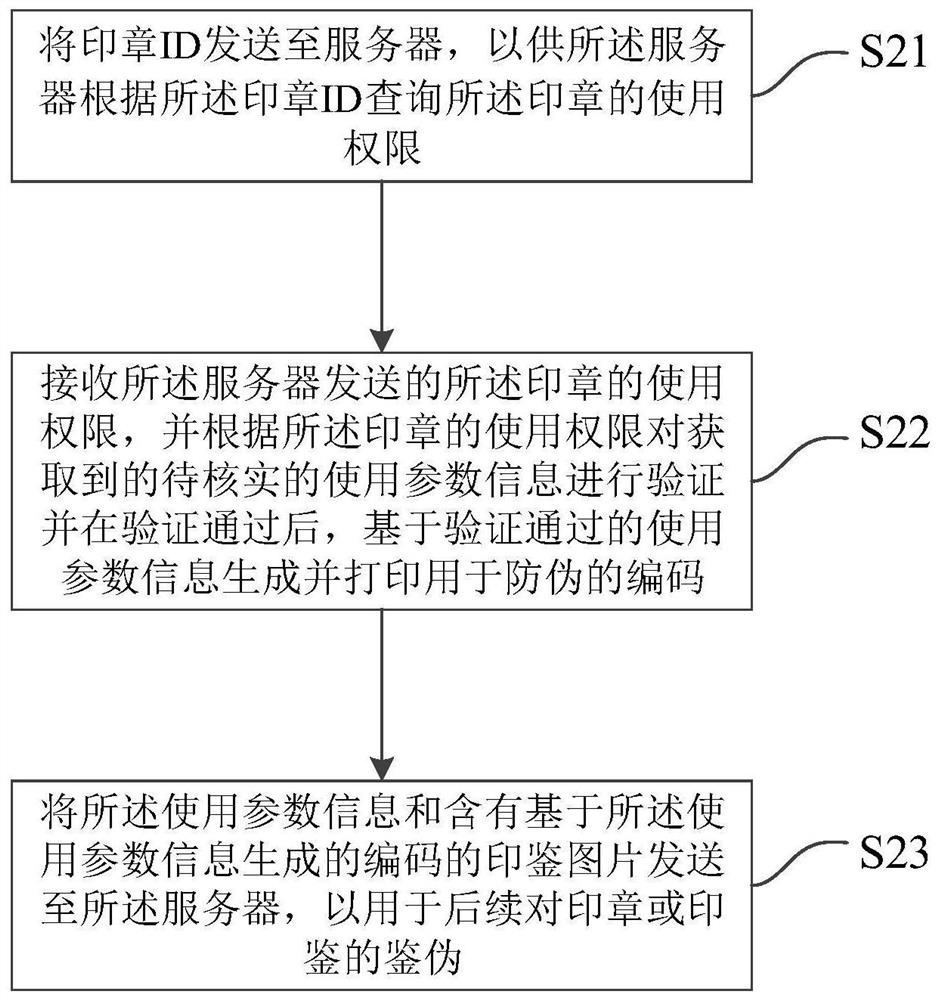
[0106] Embodiment 2 of the present invention provides a method for stamp security management, which is applied to stamps, figure 2 It is a flow chart of a method for seal security management according to Embodiment 2 of the present invention. Such as figure 2 As shown, the method includes:
[0107] Step S21: Send the stamp ID to the server, so that the server can inquire about the use authority of the stamp according to the stamp ID;
[0108] Step S22: Receive the usage authority of the seal sent by the server, and verify the obtained use parameter information to be verified according to the use authority of the seal, and after the verification is passed, based on the verified use parameter information generate and print an anti-counterfeiting code; and
[0109] Step S23: Send the use parameter information and the seal picture containing the code generated based on the use parameter information to the server for subsequent authentication of the seal or seal.
[0110] In ...
Embodiment 3
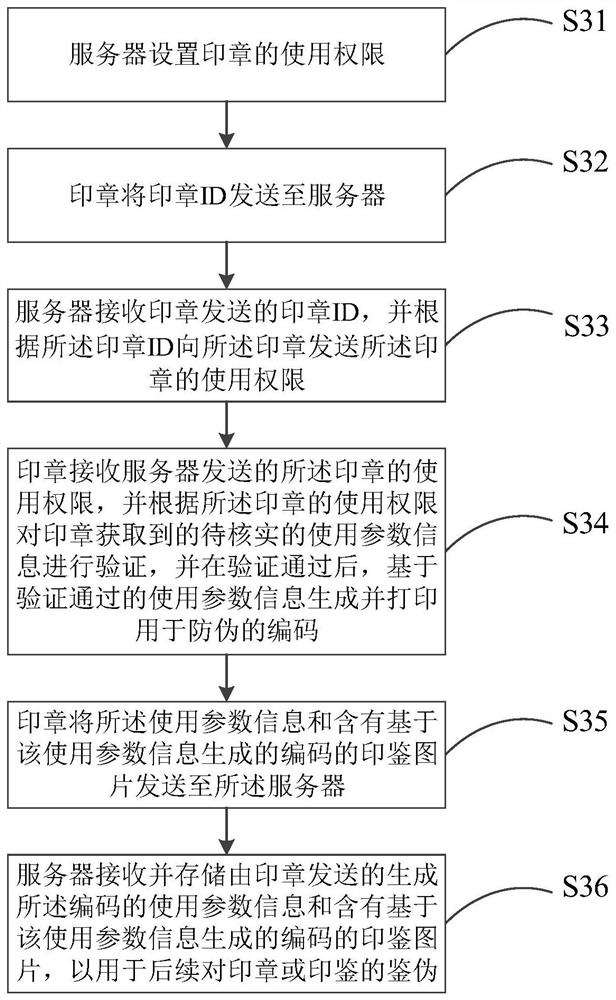
[0142] Embodiment 3 of the present invention provides a method for seal security management, which is applied to seals and servers, image 3 It is a flow chart of a method for stamp security management according to Embodiment 3 of the present invention. Such as image 3 As shown, the method includes:
[0143] Step S31: the server sets the usage authority of the seal;
[0144] Step S32: the seal sends the seal ID to the server;
[0145] Step S33: the server receives the seal ID sent by the seal, and sends the seal use authority to the seal according to the seal ID;
[0146] Step S34: The seal receives the use authority of the seal sent by the server, and verifies the use parameter information to be verified obtained by the seal according to the use authority of the seal, and after the verification is passed, based on the use parameter information passed the verification Generate and print codes for anti-counterfeiting;
[0147] Step S35: The seal sends the use parameter in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com