A security method and platform for sensitive areas
A sensitive area and community information technology, applied in the communication field, can solve problems such as data mining applications that are not considered, and achieve the effect of maintaining national security and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
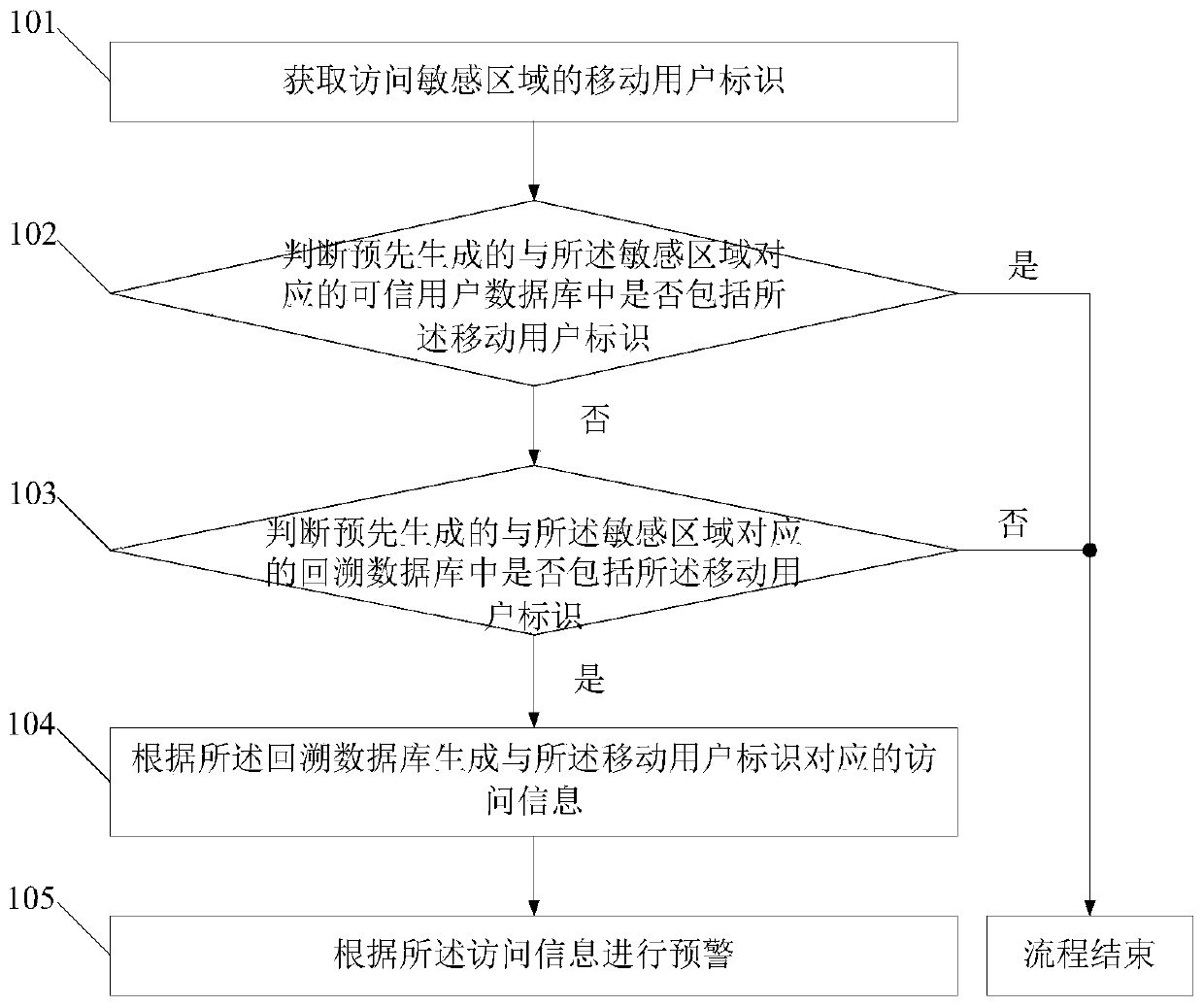
[0051] figure 1 This is a schematic flow diagram of a security method for a sensitive area provided in the first embodiment, such as figure 1 As shown, the method includes:
[0052] Step 101: Obtain a mobile user identification that visits a sensitive area.
[0053] Step 102: Determine whether the mobile user identifier is included in the pre-generated trusted user database corresponding to the sensitive area; if not, perform step 103; if so, the process ends.
[0054] Step 103: Determine whether the mobile user identifier is included in the pre-generated backtracking database corresponding to the sensitive area, if yes, execute step 104; if not, the process ends.
[0055] Step 104: Generate access information corresponding to the mobile user identifier according to the backtracking database.
[0056] Step 105: Perform an early warning based on the access information.
[0057] The security method for the sensitive area provided by this embodiment obtains the mobile user identification th...
Embodiment 2
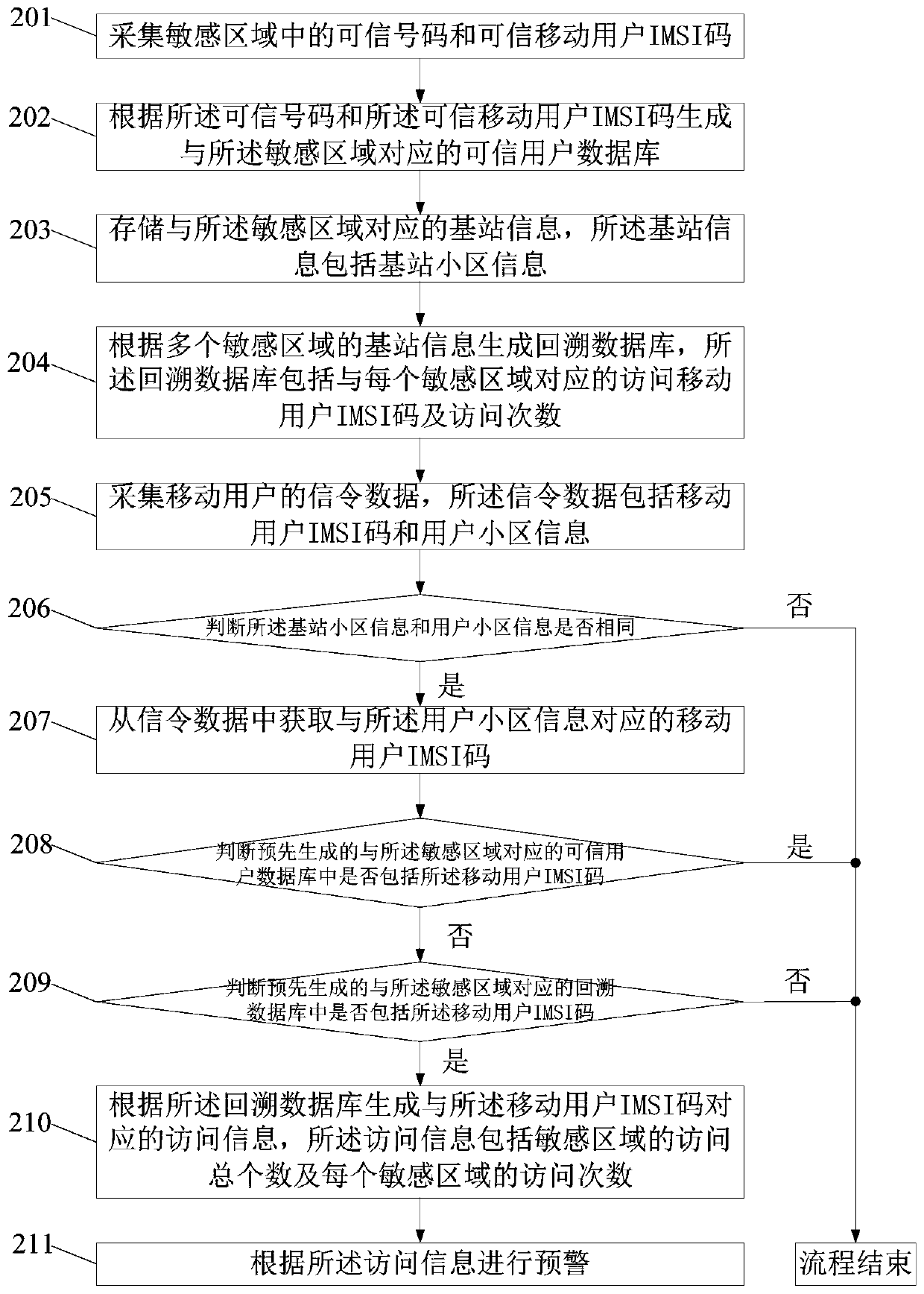
[0059] figure 2 This is a schematic flow chart of a security method for a sensitive area provided in the second embodiment, such as figure 2 As shown, the method includes:
[0060] Step 201: Collect trusted numbers and trusted mobile user IMSI codes in the sensitive area.
[0061] Preferably, each step in this embodiment is executed by a security platform in a sensitive area.
[0062] Sensitive areas can be the surrounding areas of multiple key security units involved in national security scattered throughout the country.
[0063] Specifically, the trusted number is the mobile phone number of the staff in the sensitive area, and the trusted mobile user IMSI code is the IMSI (International Mobile Subscriber Identification Number, International Mobile Subscriber Identification Number) of the mobile users in the resident sensitive area or around the sensitive area. The staff in the sensitive area and the mobile users who live in or around the sensitive area are all trusted users.
[006...
Embodiment 3
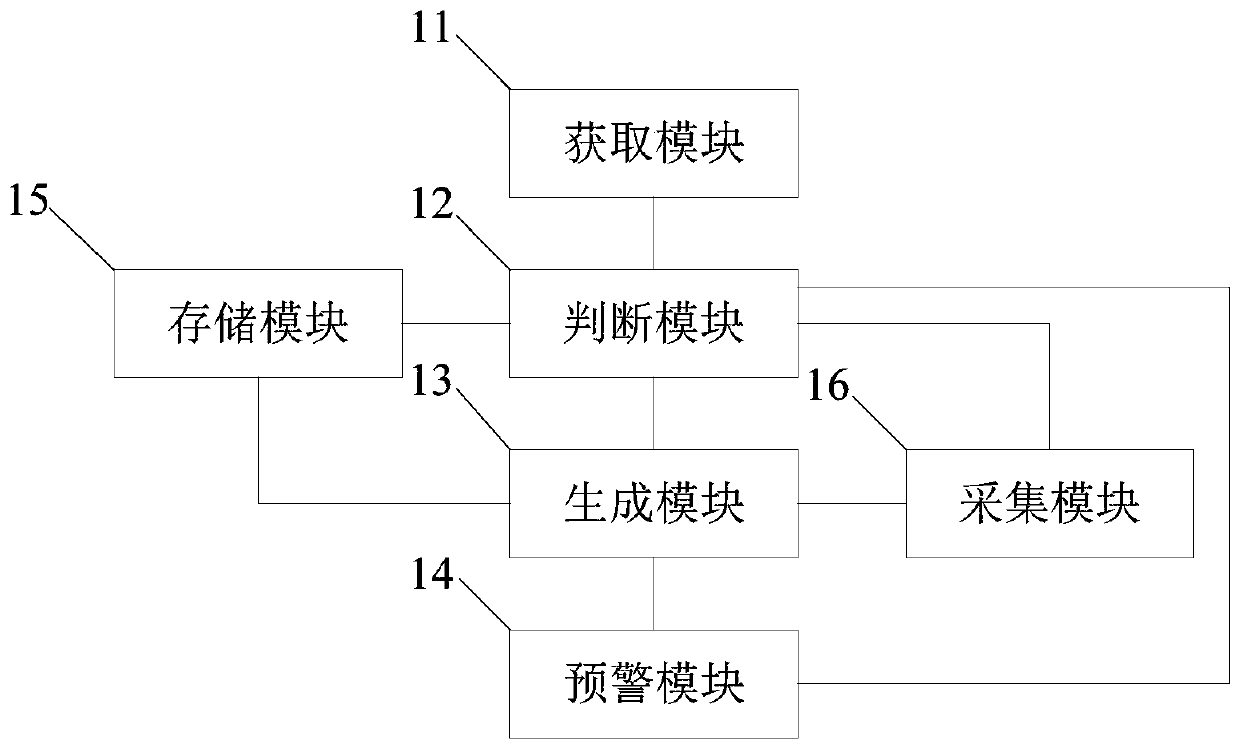
[0095] image 3 This third embodiment provides a schematic structural diagram of a security platform in a sensitive area, such as image 3 As shown, the platform includes an acquisition module 11, a judgment module 12, a generation module 13, and an early warning module 14.
[0096] The obtaining module 11 is used to obtain a mobile user identification that visits a sensitive area.
[0097] The judging module 12 is used to judge whether the mobile user identification is included in the pre-generated trusted user database corresponding to the sensitive area, and whether the mobile user identification is included in the pre-generated backtracking database corresponding to the sensitive area .
[0098] The generating module 13 is configured to generate access information corresponding to the mobile user identification according to the backtracking database.
[0099] The early warning module 14 is used for early warning based on the access information.
[0100] Further, the generating mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com