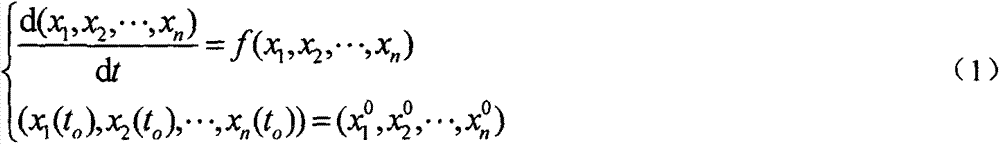Private key identity authentication taking equation as tool
A private key and identity verification technology, which is applied in user identity/authority verification, countermeasures against encryption mechanisms, digital transmission systems, etc., can solve problems such as self-stealing and self-theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] 1 Introduction
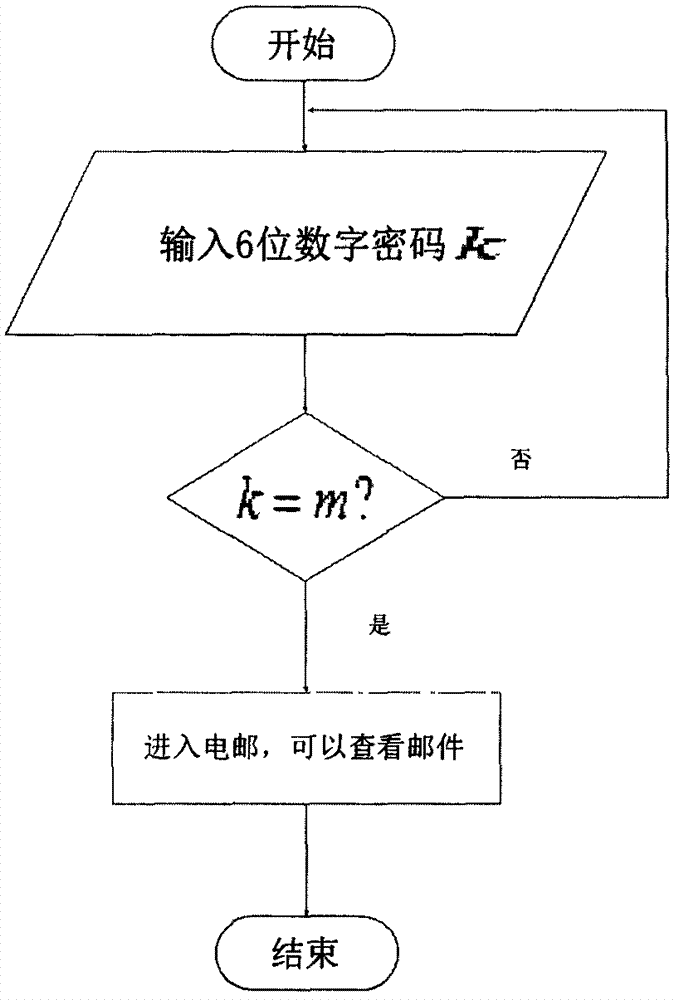
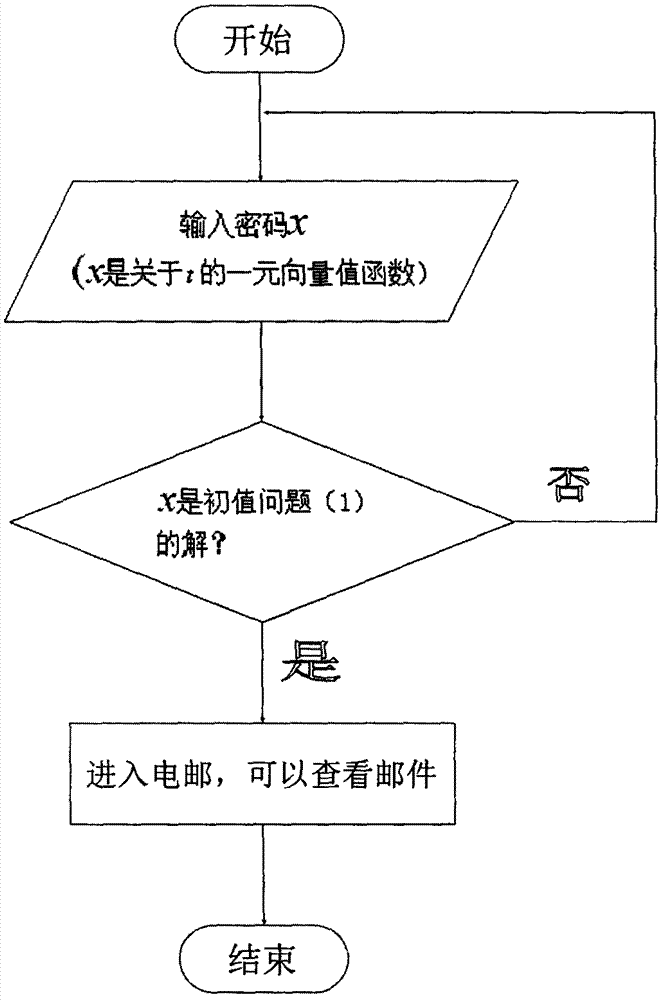
[0009] In daily life, identity verification is not uncommon. For example, the identity of the other party can be confirmed by checking the other party's certificate or scanning the other party's fingerprint. Although this common identity verification method also belongs to identity verification in a broad sense, the high-end identity verification technology that this article focuses on is more used in communications, friend-or-foe identification, artificial intelligence, secondary nuclear strikes, high-performance computing, and theater missiles. Defense, access control to computer systems and non-computer systems, access control mechanisms, etc.
[0010] The PRISM program that has been exposed in recent years has gradually made identity verification technology a research hotspot. Under the threat of password attacks, governments of various countries and multinational technology companies are forced to develop more advanced authentication technologies,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com