A Blind Signature Generation Method for Recoverable Messages Based on Identity
A blind signature and message technology, applied in the field of information security, can solve problems such as message transmission overhead, dispute resolution, and adverse effects of behavior tracking, so as to avoid certificate management problems, reduce communication and storage overhead, and reduce system operation and maintenance costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make it easier for those skilled in the art to understand the technical solution of this patent, and at the same time, in order to make the technical purpose, technical solution and beneficial effect of this patent clearer, and to fully support the protection scope of the claims, the following is a specific case in the form of this patent. The technical solution of the patent makes further and more detailed descriptions.
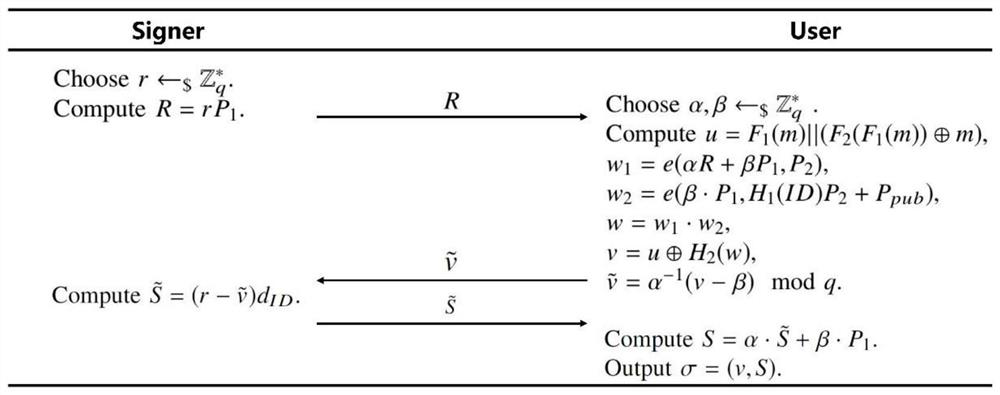
[0032] An identity-based blind signature generation method for recoverable messages involves four roles: key generation center KGC, signer, user and verifier. First, the KGC completes the system parameter setting and the generation of the system master key pair. Secondly, KGC issues the private key d corresponding to its identity ID to each signer ID . Afterwards, in the signature phase, the signer first challenges the user with a random point R, and the user uses blinding factors α, β to blind the message m to obtain The signer then u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com