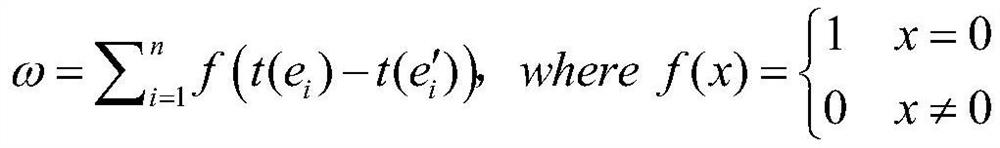Method for realizing information integrity based on continuous quantum walk hash algorithm
A hash algorithm and continuous quantum technology, applied in secure communication devices and key distribution, can solve the problem of low quantum hashing efficiency, and achieve the effect of high security and execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0038] First, according to the binary message M ∈ {0,1} * bits to select the Hamiltonian:
[0039] 2.1 Set two Hamiltonian operators H 0 = γ 0 L and H 1 = γ 1 L;
[0040] 2.2 In each time period t of walking x -t x-1 Inside, according to the binary message M∈{0,1} * bits to select which Hamiltonian to control the continuous quantum walk on the bounded one-dimensional crystal lattice, if M i =0(i=0,1,2....) select H 0 = γ 0 L, if M i =1(i=0,1,2....) select H 1 = γ 1 L;
[0041] Second, with the message M∈{0,1} * As the input of the hash algorithm, the probability value of walking to the node on the bounded one-dimensional crystal lattice is used as the output of the hash algorithm. The construction process of the hash algorithm to achieve information integrity is as follows:
[0042] 3.1 Select parameters Among them, m represents half o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com