A method for implementing an access control list circuit and its circuit
An access control list, circuit technology, applied in CAD circuit design, memory address/allocation/relocation, climate sustainability, etc., can solve the problems of high manufacturing cost, limited size of rule base, expensive, etc., to achieve flexible application, The effect of reducing search power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
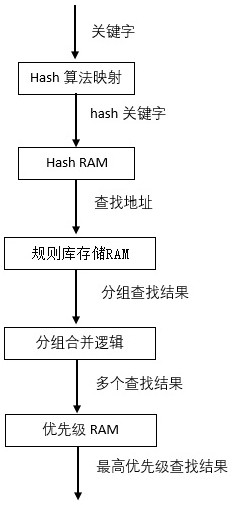
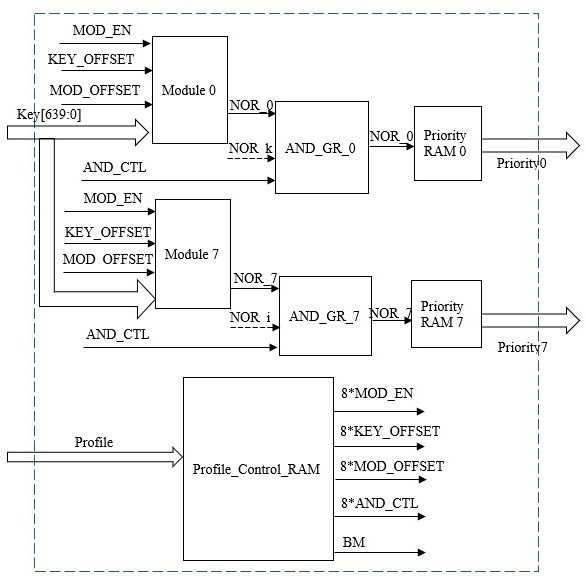
[0033] Embodiment 1, according to figure 2 An access control list circuit includes 8 Module circuits, 8 priority RAMs, 8 grouping and merging logic modules and a configuration control RAM.
[0034] By cascading several Module circuits according to different configuration information, keywords of different bit widths are searched.
[0035] The Module circuit includes a bit selection module, a Hash RAM, a data RAM, a keyword selection logic module, and a number of logic operation units; the bit selection module generates the address of the Hash RAM according to configuration information; the Hash RAM is in the figure The Hash RAM is used to store the storage address of the rule base entries; the data RAM is the Data RAM in the figure, and is used to store the rule base.
Embodiment 2
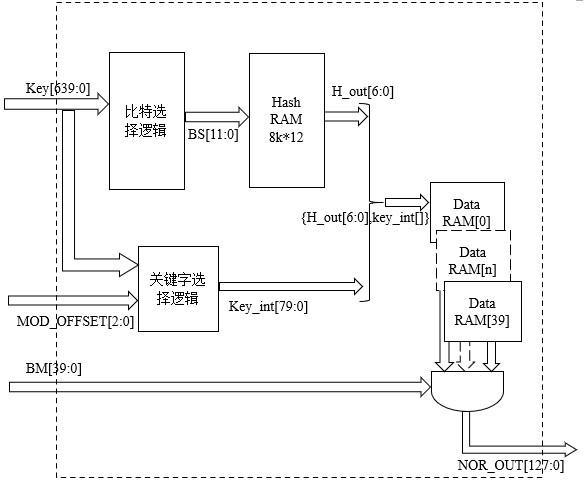
[0036] Embodiment 2, according to image 3 , Module circuit includes bit selection module, hash RAM, 40 data RAMs, keyword selection logic module and several logic operation units.
[0037] The data RAM is composed of several BinRAMs, and the BinRAM stores 2-bit-wide rule information, and the bit width of the rule base entries stored in the data RAM is determined by the number of BinRAMs contained therein.
Embodiment 3
[0038] Example 3, Figure 5 The mapping method between the 2bit rule and the 2bit keyword is given. The keyword 00 hits 00, 0X, X0 and XX in the rule, where "X" means "don't care", that is, the bit status is not considered when matching, so for There are multiple hits in keyword search; the rule base is the hit result of combining rules with keywords, and the rule base will be delivered to 40 Bin RAMs in the data RAM in advance.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com