Security configuration reinforcement method and system and medium
A technology of security configuration and configuration items, applied in the direction of platform integrity maintenance, etc., can solve problems such as the inability to guarantee the security of the operating system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
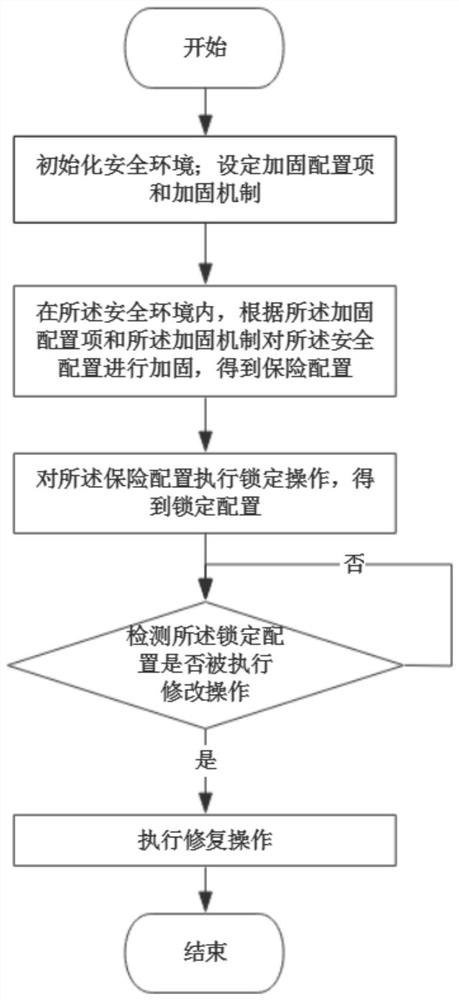
[0053] This embodiment provides a security configuration hardening method, such as figure 1 shown, including the following steps:
[0054] This embodiment is realized based on the Linux system;
[0055] S100. Initialize the security environment;
[0056] Specifically:
[0057] Create a security management terminal and perform initial configuration operations through the security management terminal;
[0058] The initial configuration operation is: obtain and install the security configuration hardening program; run the security configuration hardening program; set the security access right of the security configuration hardening program to be accessible only through the security management terminal; the security access right includes the process of the security configuration hardening program Control authority and operation authority;
[0059] Setting an initial configuration and a level threshold of the security configuration; the level threshold includes a first level th...
Embodiment 2
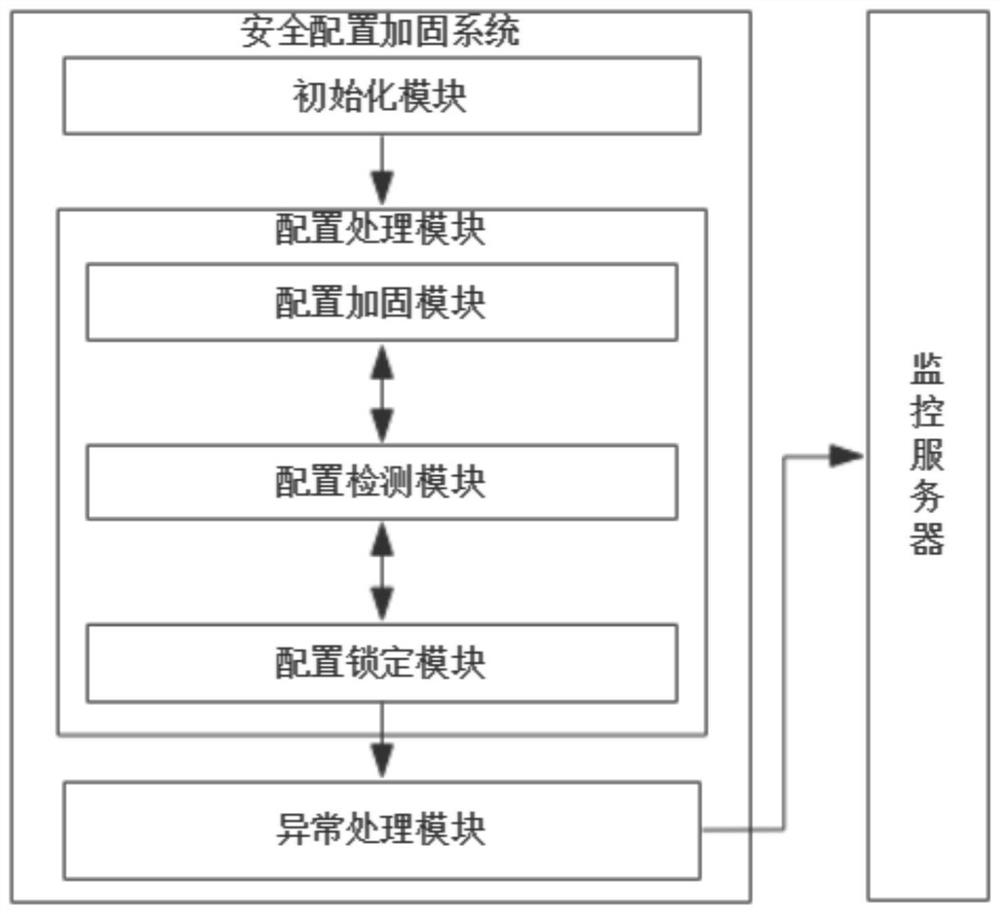
[0094] This embodiment provides a security configuration hardening system, such as figure 2 shown, including:
[0095] An initialization module, a configuration processing module and an exception processing module; the configuration processing module includes: a configuration reinforcement module, a configuration locking module and a configuration detection module; the exception processing module is connected to the monitoring server;
[0096] The initialization module creates a security management terminal, and the initialization module performs initial configuration operations through the security management terminal; specifically:
[0097] The initial configuration operation is: the initialization module obtains and installs the security configuration hardening program; the initialization module runs the security configuration hardening program; the initialization module sets the security access right of the security configuration hardening program to be accessible only th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com