A cloud-network-end collaborative defense method and system based on device-side edge computing
An edge computing and collaborative defense technology, applied in computing, transmission systems, computing models, etc., can solve problems such as the false alarm rate and detection rate are not very good, and the real-time performance cannot be guaranteed, so as to eliminate data fragmentation and prevent harm. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
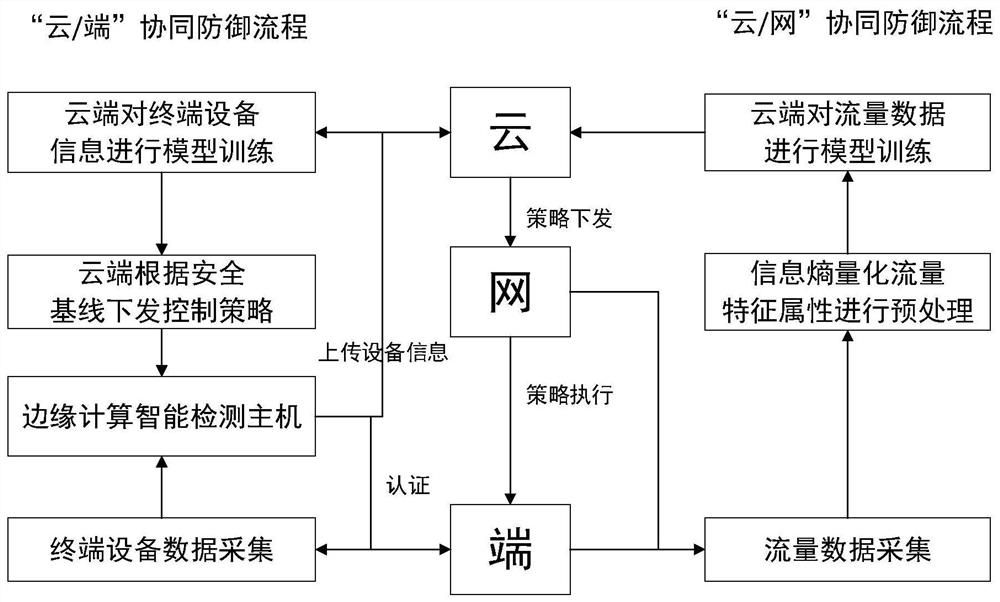
[0033] With the rapid development of intelligent power industrial control systems, the security problems of the power industrial control systems themselves are becoming increasingly severe, and the "eye" terminal data acquisition equipment of the power industrial control systems has become the target of attackers. The present invention sets up an edge computing center at the edge of the industrial control system to process authentication and flow detection tasks of end-side terminal equipment in real time, and the cloud computing center trains the flow detection model through machine learning, based on which, the safe and stable operation of the electric power industrial control system is ensured.
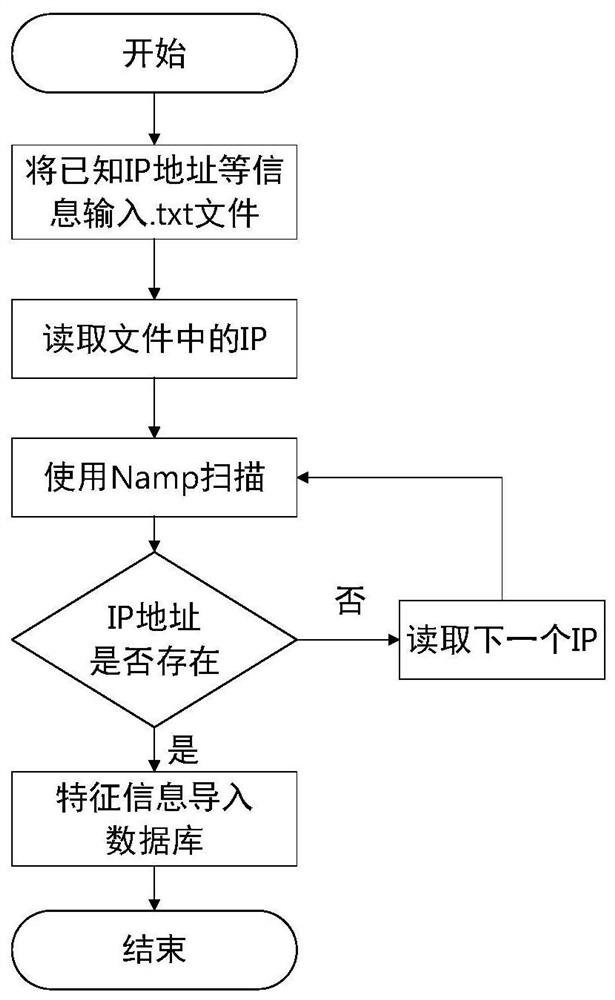
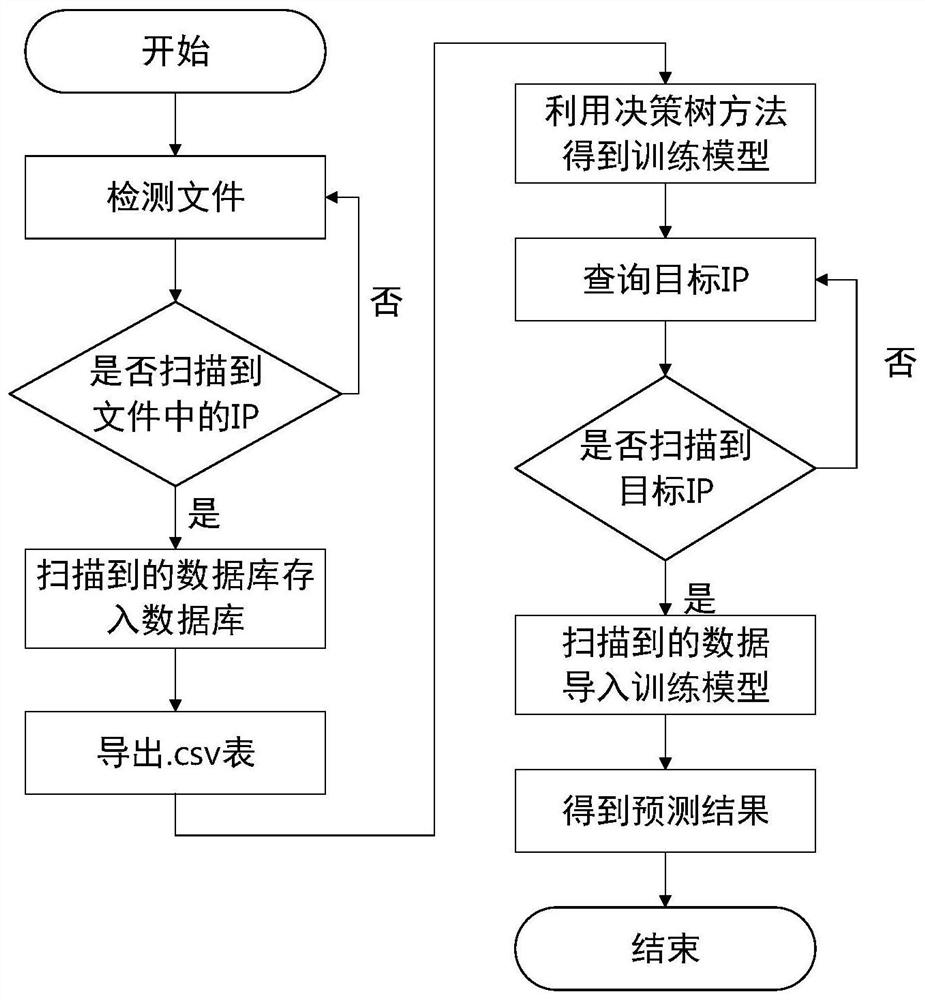
[0034] refer to figure 1 , the present invention focuses on the dynamic authentication and communication flow detection of the data collection ter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com