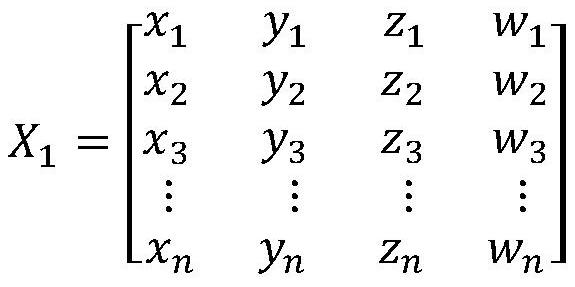Method for distinguishing DDoS attack and elephant flow based on PCA and random forest
A technology of random forest and random forest model, which is applied in the field of distinguishing DDoS attacks and elephant flows, and can solve problems such as discarding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
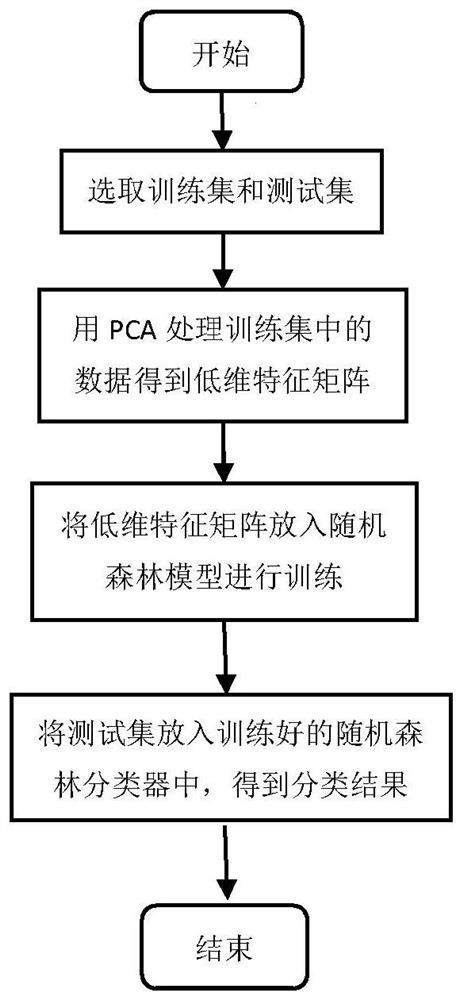
[0022] Embodiment 1: as figure 1 , 2 As shown, a method for distinguishing DDoS attacks and elephant flows based on PCA and random forest includes the following steps:
[0023] Step 1: Select the training set and test set from the DDoS data set, and add the elephant flow data set to the training set and test set respectively.
[0024] Step 2: The data in the training set is processed by PCA to reduce the dimensionality to obtain a low-dimensional feature matrix;
[0025] Step 3: put the low-dimensional feature matrix into the random forest model for training, and obtain a random forest classifier;
[0026] Step 4: Input the test set samples into the trained random forest classifier to obtain the classification results.
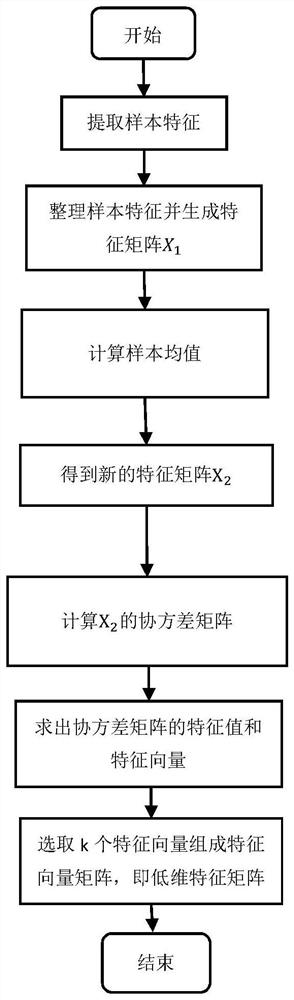
[0027] Further, as figure 2 As shown, in the second step, the data in the training set is processed by PCA to reduce the dimensionality to obtain a low-dimensional feature matrix. The specific process is as follows:
[0028] Step 1: Extract sample featur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com