Mobile edge computing network user access control method for heterogeneous service requirements
A technology for edge computing and business requirements, applied in access restrictions, network traffic/resource management, electrical components, etc., to achieve the effect of improving service efficiency and broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
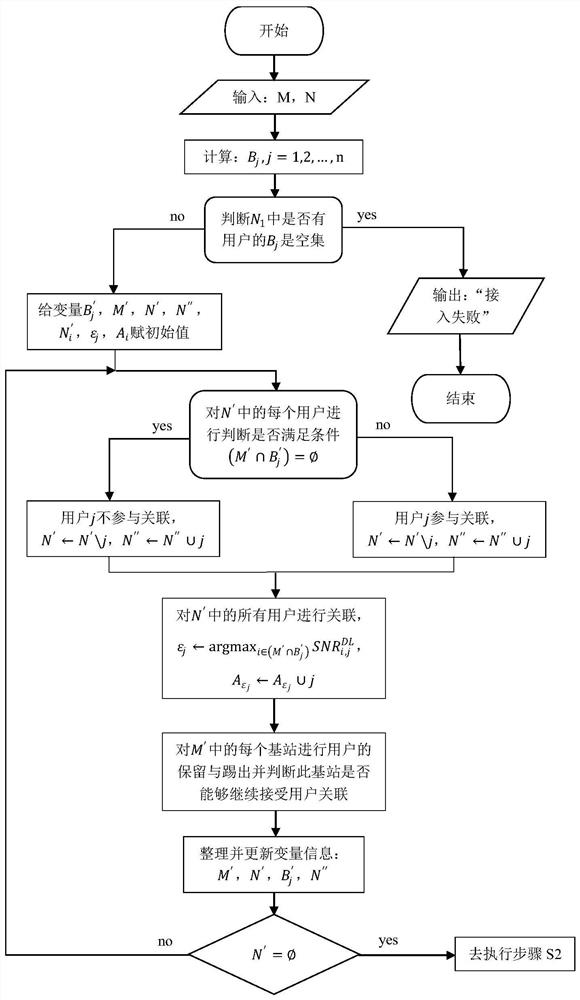
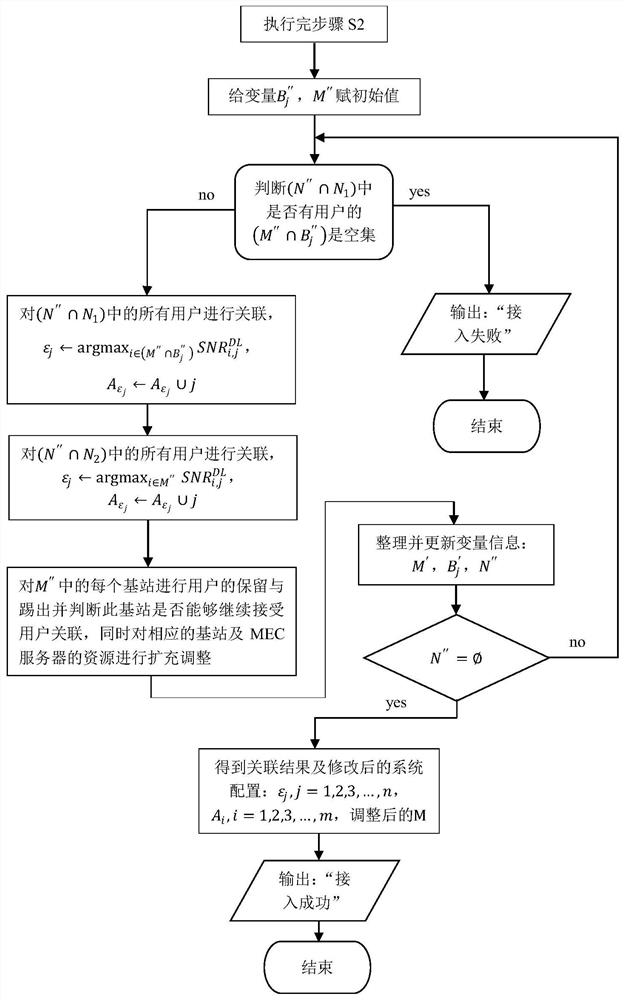
[0076] The invention discloses a mobile edge computing network user access control strategy oriented to heterogeneous service requirements, and the details are as follows.
[0077] A mobile edge computing network user access control method for heterogeneous service requirements.
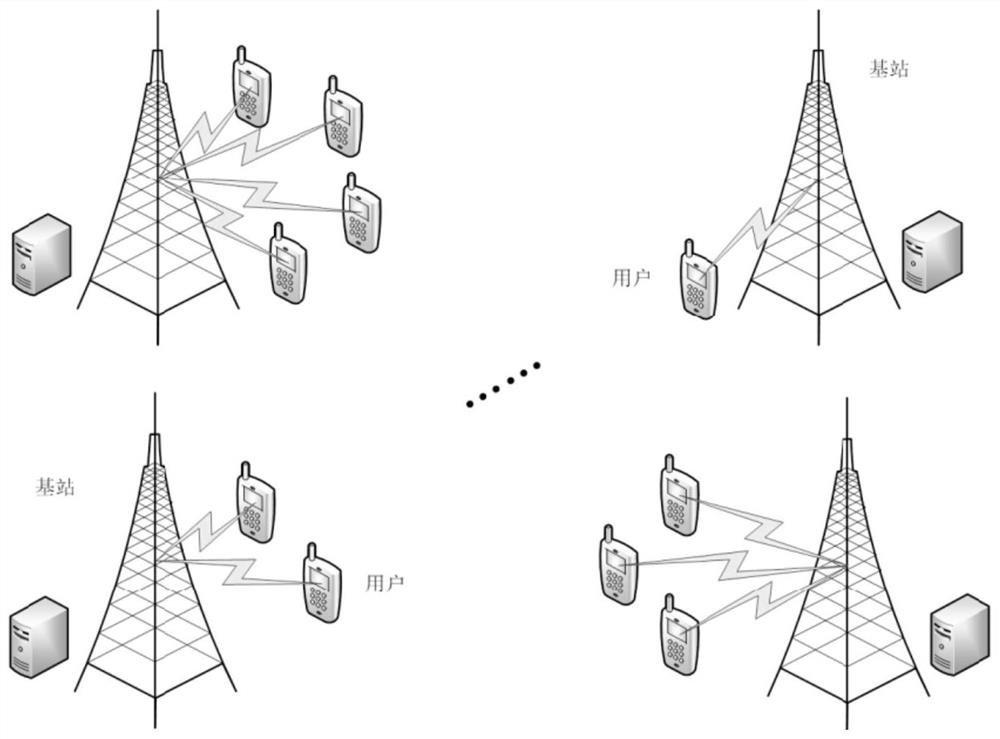
[0078] The mobile edge computing network includes n users, m base stations, and m corresponding MEC servers, where n 1 users have computing task offload requests, n 2 users have file download cache requests, n=n 1 +n 2 , each user who needs computing offload has only one computing task, and its computing task is represented by a quadruple, in is the input data size of the task, is the output data of the task, that is, the size of the task calculation result, τ j is the task completion time limit, β j Indicates the amount of computation required by the task, expressed in the number of CPU cycles, and the Zipf parameter of each user who needs to download a file is μ j , the maximum acceptabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com