A resource conflict detection method based on blockchain-based resource public key infrastructure
A public key infrastructure and resource conflict technology, which is applied in the detection field of resource public key infrastructure resource conflicts, can solve the problems of low detection efficiency and failure to consider the comprehensive scheme of CA resource anomaly detection, so as to ensure correctness and improve self-security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] Such as Figure 4 Shown, the present invention comprises the following steps:
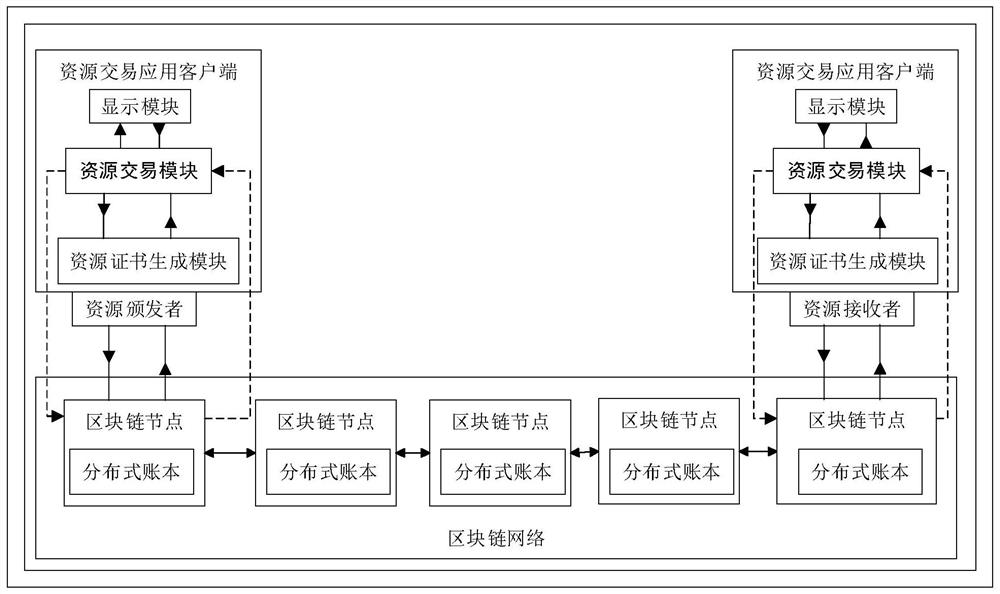
[0084] The first step is to build a blockchain-based resource public key infrastructure system RPKIB, such as figure 1 As shown, RPKIB is composed of a resource issuer, a resource transaction application client, a resource receiver, and a blockchain network.
[0085] The resource issuer and resource receiver are connected to the blockchain network, and the resource transaction application client is installed on the resource issuer or resource receiver. The resource transaction application client performs various operations of the resource certificate and the routing origin authorization ROA as transactions through the blockchain network, and saves the transaction records in the distributed ledger. Distributed ledgers exist in all blockchain nodes.
[0086] Resource Issuer The resource issuer is connected to the blockchain network as a client of the blockchain network.
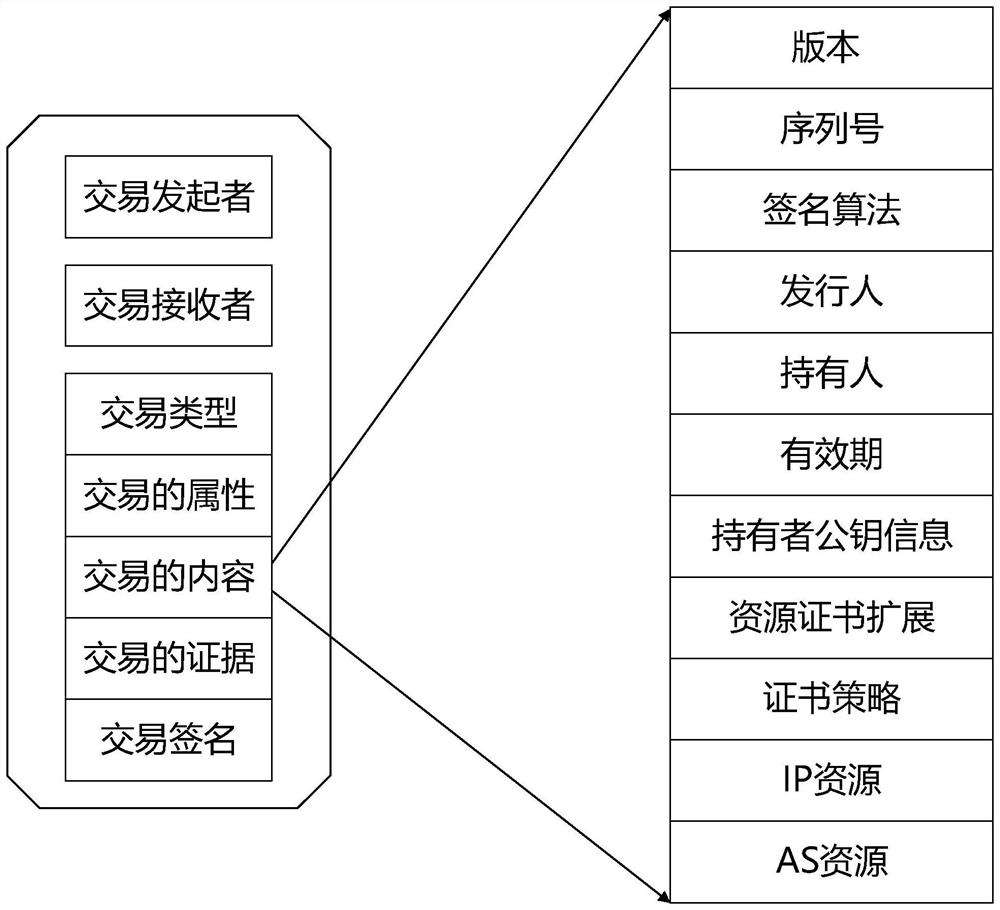
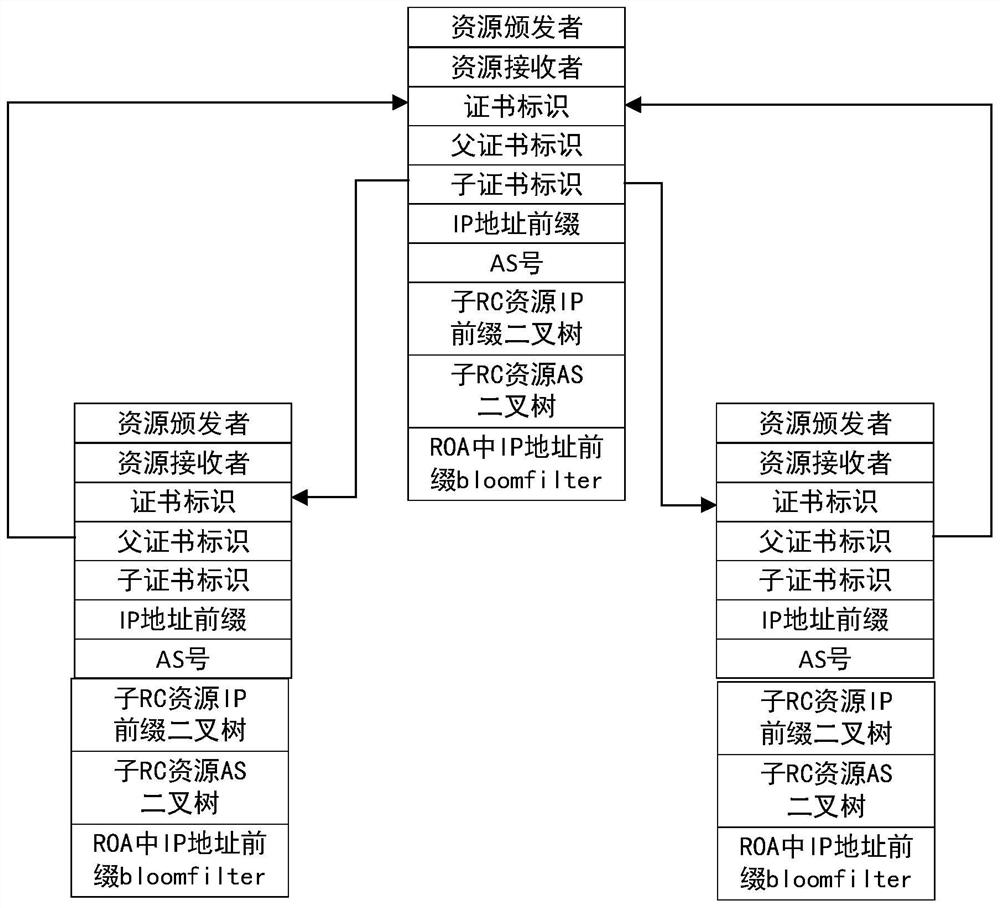
[0087] A resourc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com