Detecting security risks related to a software component
A security risk, software component technology, used in computer security devices, instruments, computing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
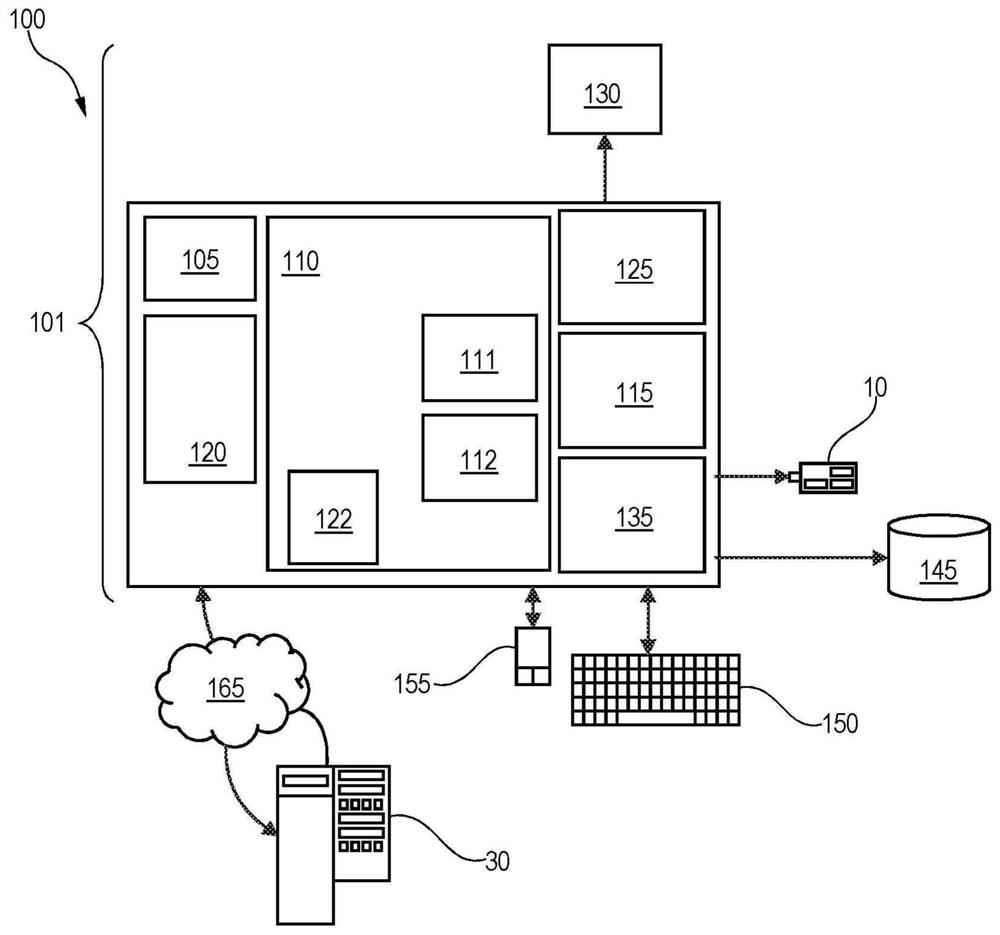
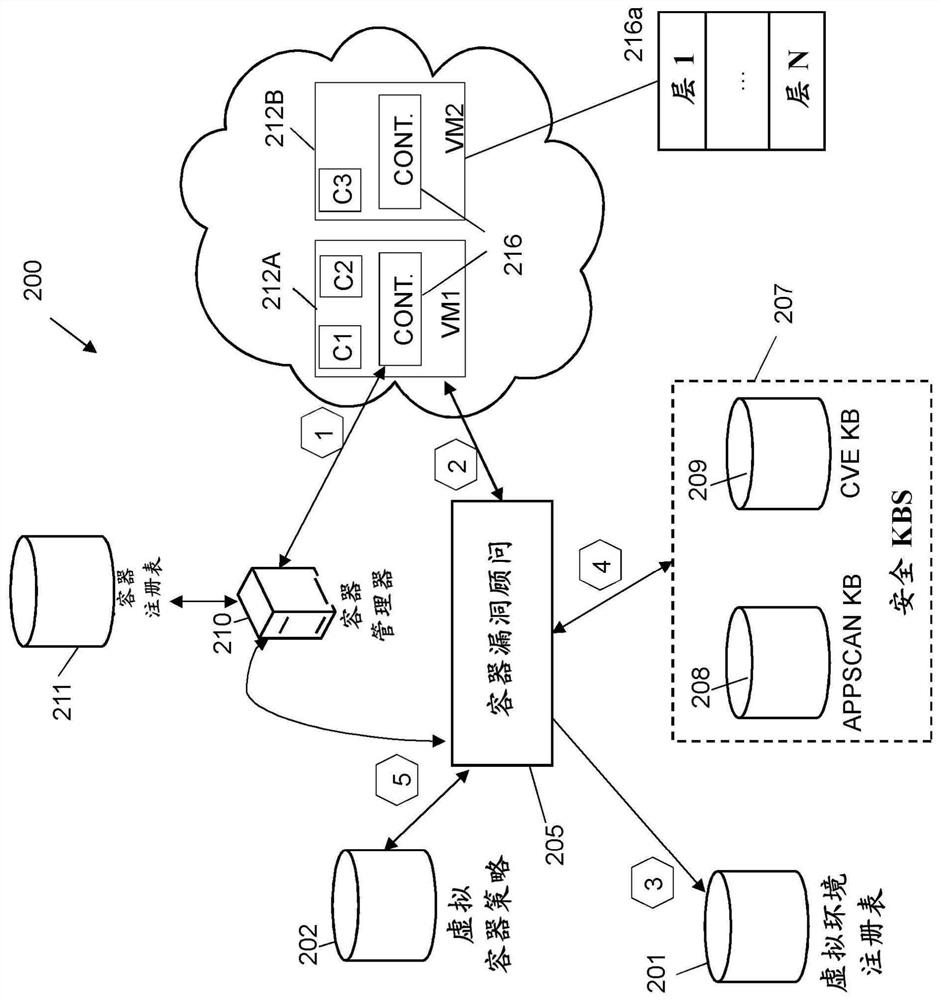
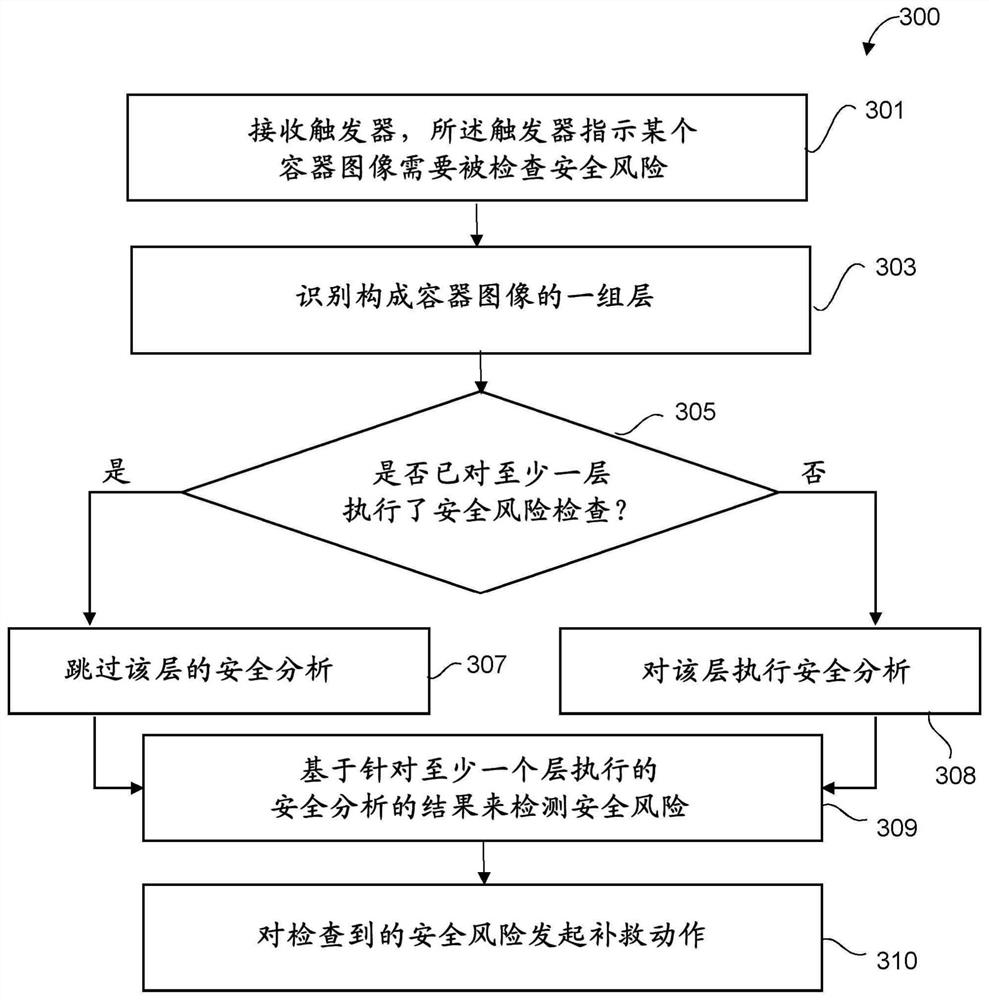
[0012] Aspects of the present disclosure relate generally to the field of digital computer systems, and more particularly to methods for detecting security risks associated with software components to be deployed in container-based runtime environments. While the present disclosure is not necessarily limited to such applications, various aspects of the disclosure can be appreciated through a discussion of different examples using this context.
[0013] Some embodiments of the method may enable detection of security exposures at runtime when the container is instantiated without installing any agents inside the container. Some embodiments of the method may prevent the use of proxies inside the container, and thus may allow inspection of the container without compromising the lightweight design of the container and without running multiple competing processes / agents inside the container. Based on the detected exposure, appropriate actions can be taken to manage the container (an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com