Illegal external connection detection method for NAT access equipment
A technology for external detection and access equipment, applied in the direction of electrical components, transmission systems, etc., can solve problems such as inability to effectively discover and detect communication conditions, and achieve the effect of reducing the probability of missed detection and facilitating deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
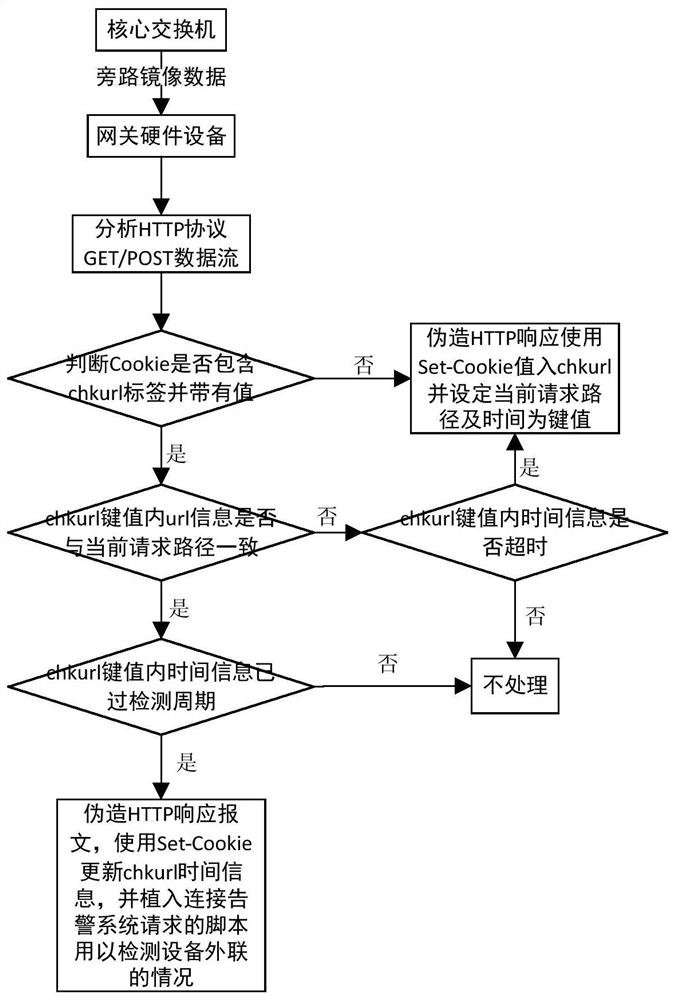
[0018] refer to figure 1 , the embodiment of the present invention provides a method for detecting illegal outreach for NAT access devices, including the following steps:
[0019] S1. Deploy the gateway hardware device in a bypass on the core switch, and provide all network traffic information flowing through the core switch to the gateway hardware device in the form of a mirror image;
[0020] S2. The gateway hardware device analyzes the traffic information obtained in real time, separates the HTTP data stream, and conducts in-depth analysis of the GET\POST message information;
[0021] S3, parse the cookie information in the GET\POST message, extract the chkurl key value information, if there is no chkurl information, go to step S4, if the chkurl information is extracted, then go to step S5;
[0022] S4. The gateway hardware device forges the HTTP response message according to the HTTP flow information, and uses the Set-Cookie value to enter the chkurl key and the chkurl ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com