Deep integrated learning model construction method for malicious WebShell detection
An integrated learning and deep technology, applied in the Internet field, can solve problems such as low detection rate, complexity, and high detection rate, and achieve the effect of ensuring interpretability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The principles and features of the present invention will be described below with reference to the accompanying drawings, and the exemplary examples are intended to be construed as they are intended to limit the scope of the invention.
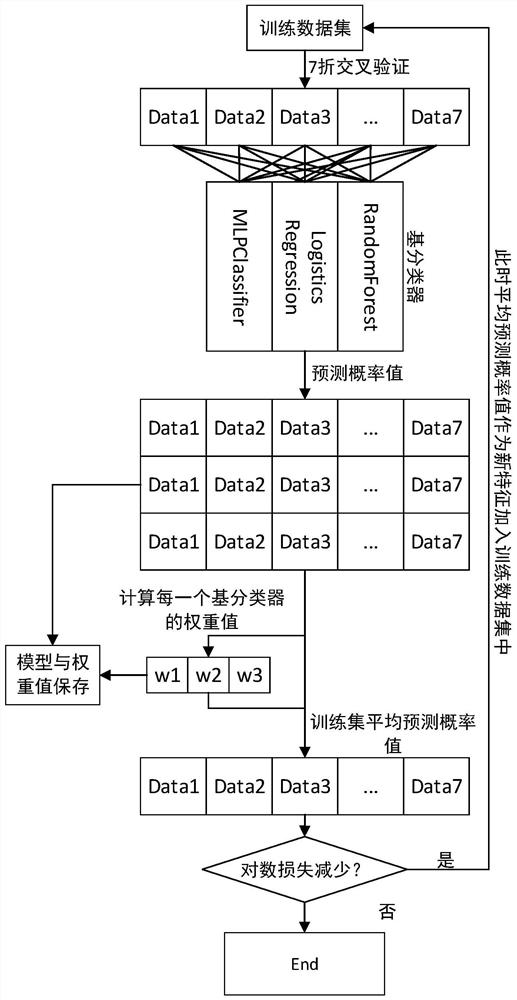
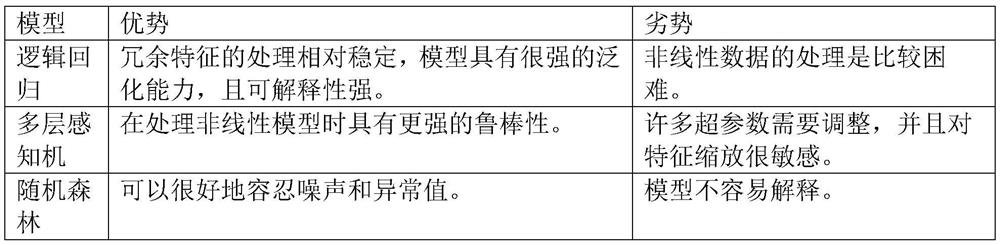
[0056] Embodiments of the present invention provide a method of constructing a depth integrated learning model for malicious WebShell detecting, including the following steps,
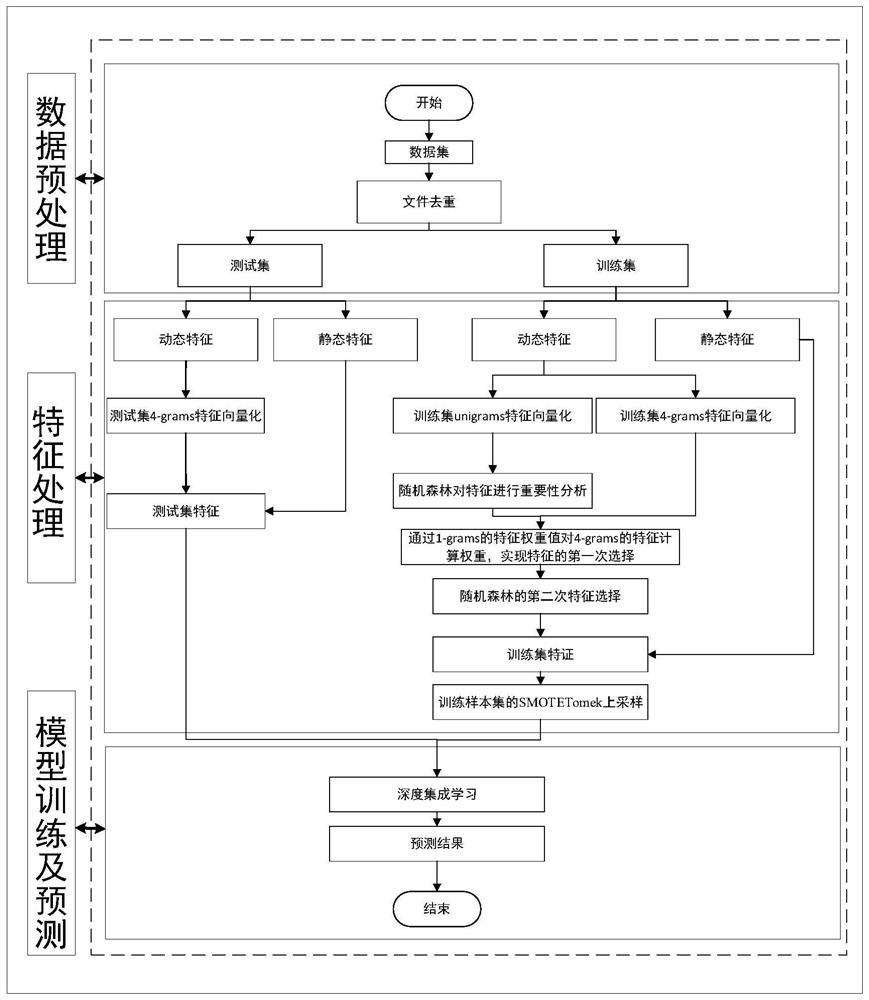
[0057] A: Data pretreatment section ( figure 1 ):
[0058] 1: Download the model from the Internet and malicious Webshell samples, which will have certain repetitive files in our downloaded files, so we will focus on the files in MD5. First, MD5 encryption is performed, as long as the file content is exactly the same, the generated MD5 value is the same, so that it can be removed according to this principle.
[0059] After the MD5 file of the data set is heavy, it has a total of 571 samples in the WebShell sample, and the normal sample is 5379 samples.
[0060] 2: R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com