A method and system for user login verification and security detection based on domestic CPU
A technology of login verification and detection method, applied in the computer field, can solve the problems of destroying the normal authentication process of the system, affecting the user experience, illegal interception of authentication marks, etc., so as to improve the security detection mechanism, realize free customization, and improve the security of use. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
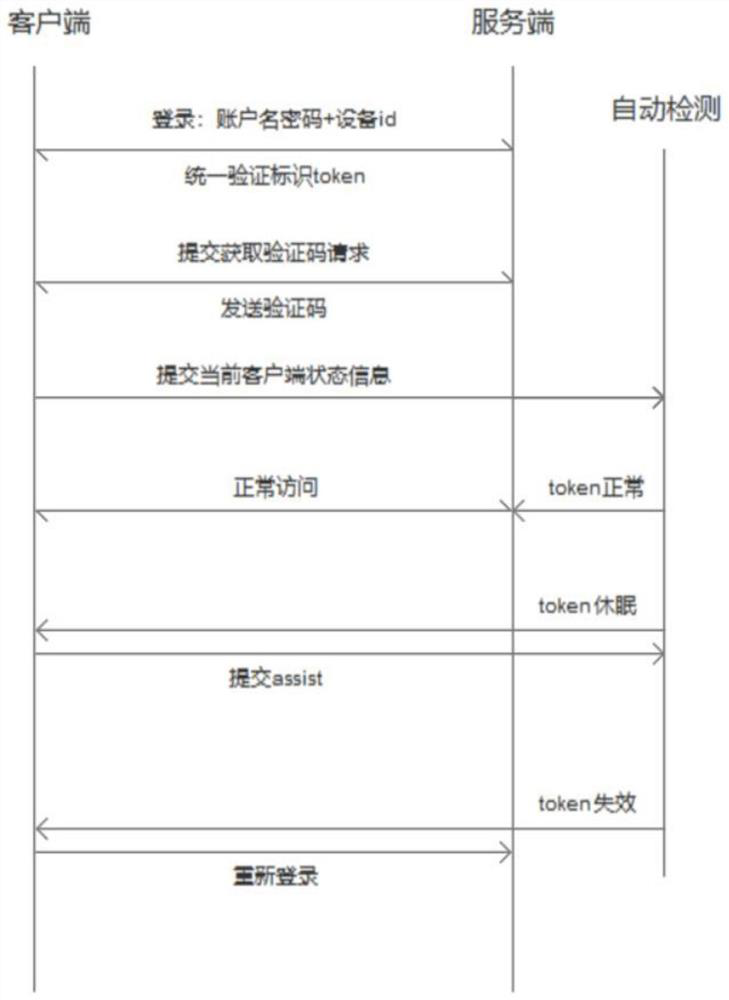
[0035] The present invention will be further described below in conjunction with accompanying drawing and specific embodiment, so that those skilled in the art can better understand the present invention and can be implemented, but the embodiment given is not as the limitation of the present invention, in the case of no conflict Next, the embodiments of the present invention and the technical features in the embodiments can be combined with each other.
[0036] It should be understood that in the description of the embodiments of the present invention, words such as "first" and "second" are only used to distinguish the purpose of description, and cannot be understood as indicating or implying relative importance, nor can they be understood as indicating or imply order. "Multiple" in the embodiments of the present invention refers to two or more.
[0037] The term "and / or" in the embodiment of the present invention is only an association relationship describing associated obje...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap