Slicing control method and device
A control method, slicing technology, applied in the computer field, can solve problems such as no solution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
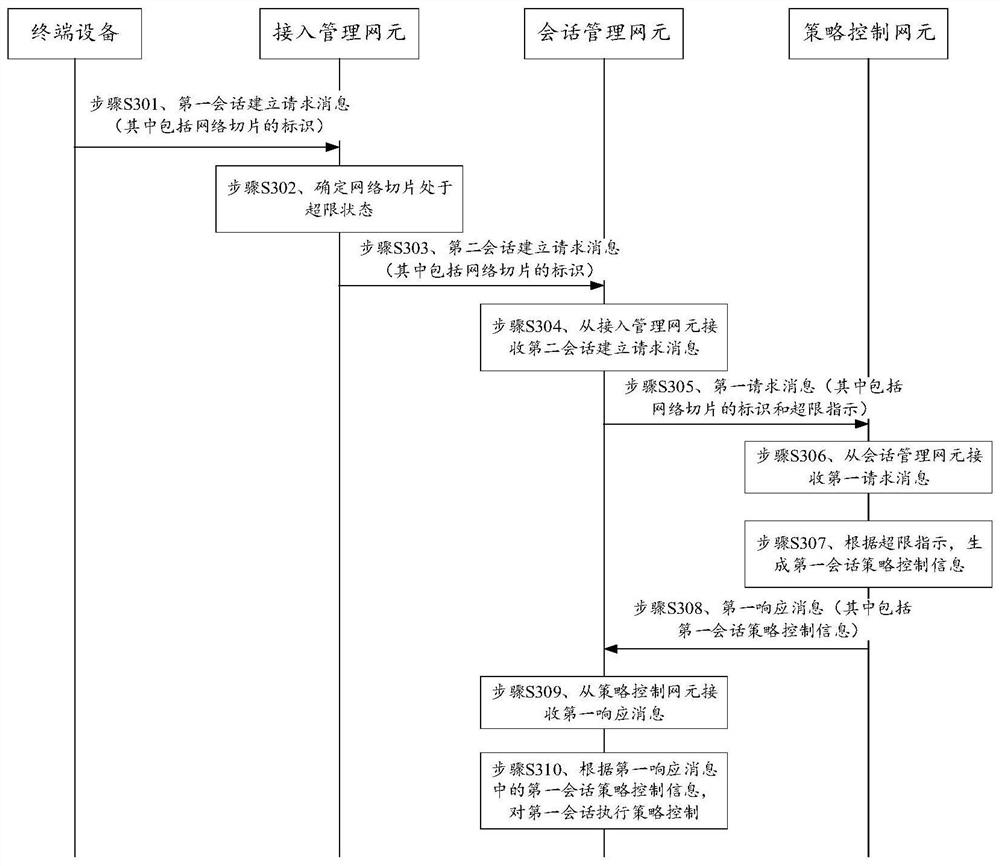
[0117] Please refer to image 3 , which is a schematic flowchart of a slice control method provided in the embodiment of the present application, the method specifically includes the following steps:
[0118] Step S301, the access management network element receives a first session establishment request message from a terminal device, and the first session establishment request message includes an identifier of a network slice.
[0119] In this embodiment of the present application, the first session establishment request message is used to request establishment of the first session of the terminal device, and the first session may specifically be a protocol data unit (protocol data unit, PDU) session. Optionally, the first session establishment request message may include an identifier of the first session (that is, a PDU session ID) and / or an identifier of a terminal device (that is, a UEID), and the identifier of a terminal device may also be understood as a user identifier...
Embodiment 2
[0206] The embodiment of the present application also provides another slice control method. The main difference between the slice control method and the slice control method provided in Embodiment 1 is that the slice access decision can be performed by the session management network element. That is, after the access management network element receives the session establishment request message from the terminal device, it does not need to judge whether the network slice is in an overrun state, and the session establishment request message sent by the access management network element to the session management network element may not include Limit indication, after the session management network element receives the session establishment request message from the access management network element, it can determine whether the network slice is in the limit state, and decide whether to allow the session to be established in the limit state.
[0207] Please refer to Figure 10 , i...
Embodiment 3
[0229] The embodiment of the present application also provides another slice control method. The main difference between this slice control method and the slice control methods provided in Embodiment 1 and Embodiment 2 is that the policy control network element can judge the overrun state of the network slice . That is, the session establishment request message received by the session management network element from the access management network element, and the first request message received by the policy control network element from the session management network element may not include an overrun indication, and may be received by the policy control network element After receiving the first request message, judge whether the network slice is in an overrun state, and generate corresponding policy control information.
[0230] Please refer to Figure 11 , is a schematic flowchart of another slice control method provided in the embodiment of the present application. The meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com