Information data fusion method and device
A technology of intelligence data and fusion method, which is applied in the field of network security, can solve the problems of uneven fusion effect and low efficiency of intelligence data fusion, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
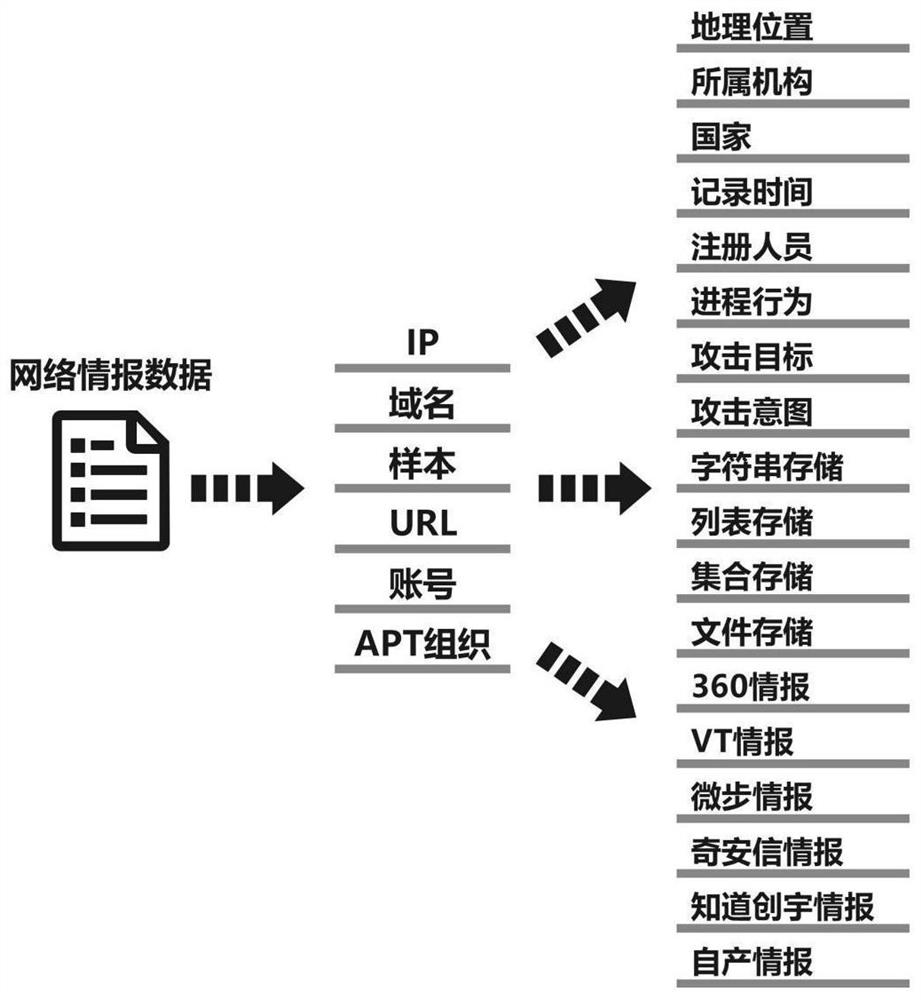
[0031] Such as figure 1 Shown is an intelligence data fusion method, which is divided into several stages in implementation, including preprocessing, generating fusion rules, and fusing intelligence data and intelligence database data according to the rules.
[0032] S1 preprocesses the original network intelligence data to obtain structured data that conforms to the data model of the intelligence database;
[0033] Table 1 is an exemplary intelligence database data model:
[0034] Table 1 Information database data model
[0035]
[0036] figure 2 A flow chart showing data preprocessing steps in an intelligence data fusion method provided by an embodiment of the present invention;
[0037] Such as figure 2 As shown, the preprocessing step is mainly to process raw intelligence data. The data source can be Weibu online report data, 360 threat intelligence data, Zhichuangyu intelligence data, Qi Anxin intelligence data, and self-developed intelligence data, etc., depending...
Embodiment 2
[0069] Further, another embodiment of the present invention provides an intelligence data fusion device as an implementation of the methods shown in the above embodiments. This device embodiment corresponds to the foregoing method embodiment. For the convenience of reading, this device embodiment does not repeat the details in the foregoing method embodiment one by one, but it should be clear that the device in this embodiment can correspond to the foregoing method implementation. Everything in the example. In the device of this embodiment, there are following modules:
[0070] 1. Preprocessing module: configured to preprocess the original network intelligence data to obtain structured data conforming to the data model of the intelligence database; this module corresponds to step S1 in Embodiment 1.
[0071] Include submodules:
[0072] Entity extraction submodule: configured to identify intelligence entities in the original network intelligence data, and extract and save en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com