Internet of Things terminal access monitoring method, computer program and storage medium
An Internet of Things terminal and Internet of Things technology, applied in the field of Internet of Things, can solve problems such as personal privacy exposure and personal information security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
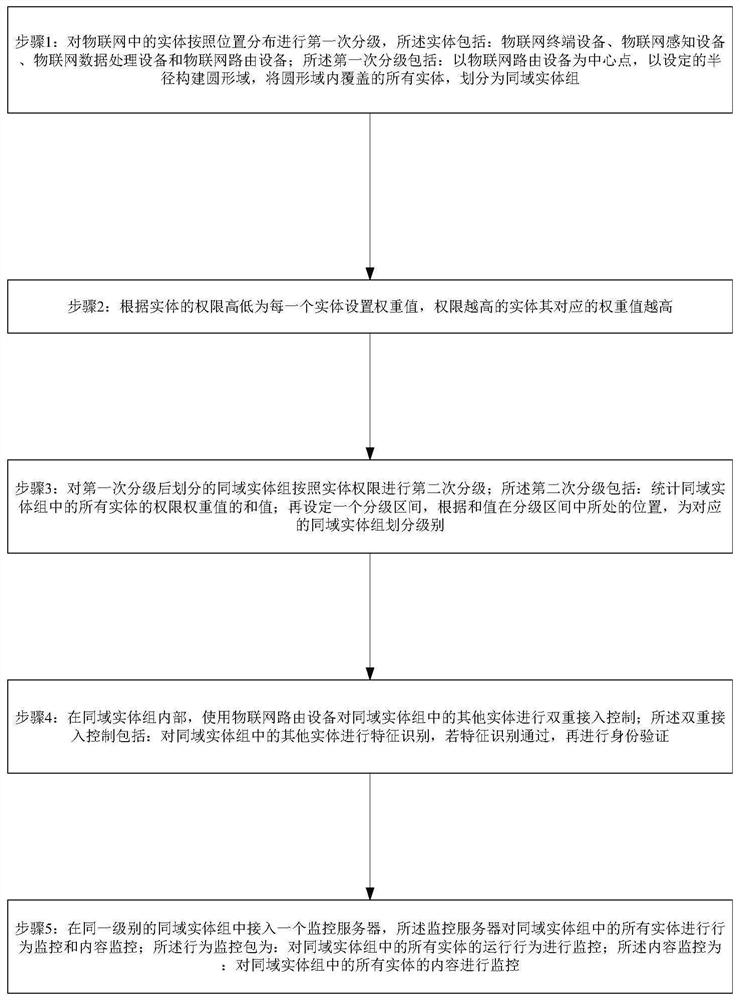
[0028] like figure 1 As shown, the Internet of Things terminal accesses the monitoring method, and the method performs the following steps:
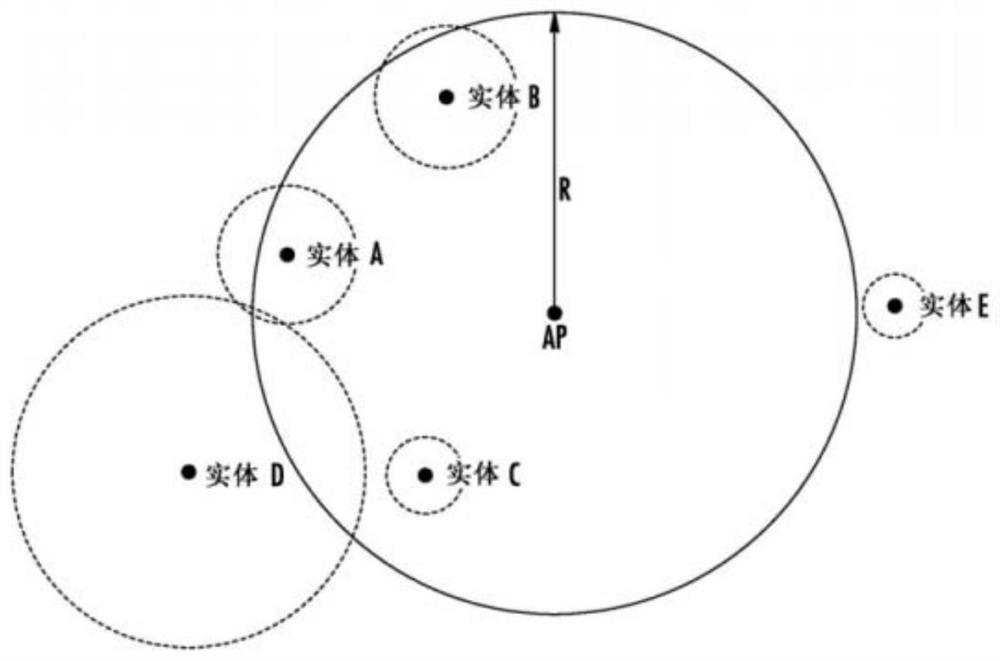
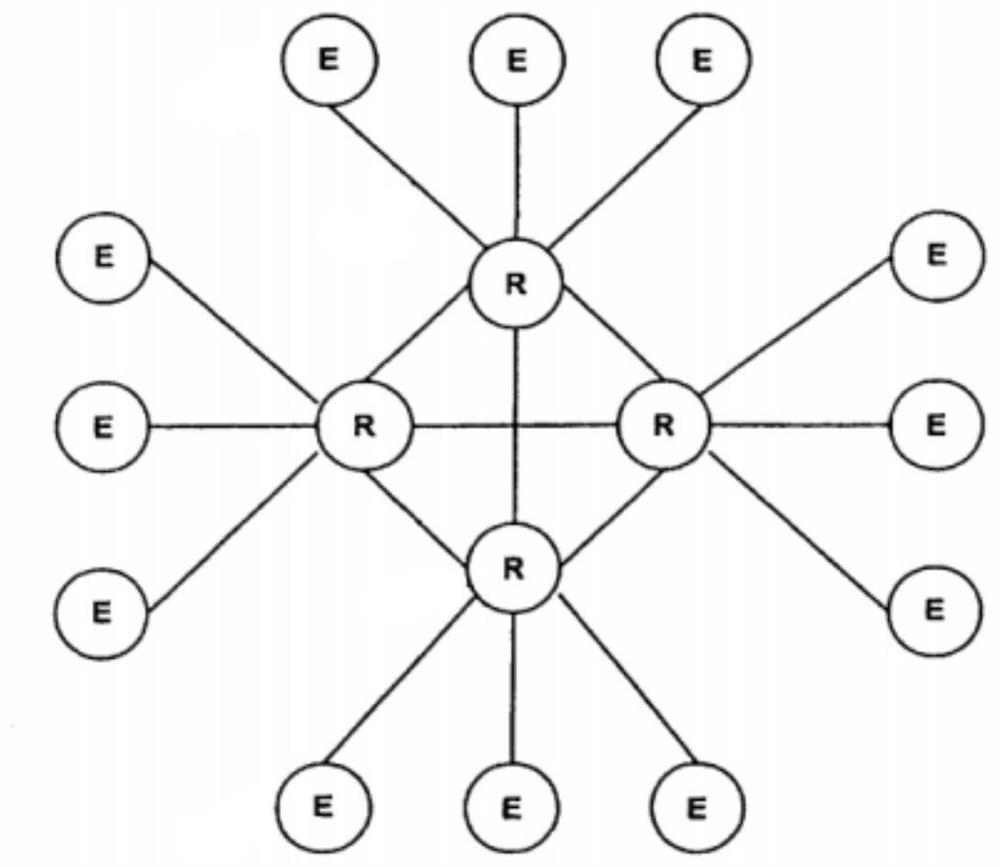
[0029] Step 1: Perform a first classification of entities in the Internet of Things according to their location distribution, the entities include: Internet of Things terminal equipment, Internet of Things sensing equipment, Internet of Things data processing equipment, and Internet of Things routing equipment; the first classification Including: taking the IoT routing device as the center point, constructing a circular domain with a set radius, and dividing all entities covered in the circular domain into same-domain entity groups;
[0030] Step 2: Set a weight value for each entity according to the level of authority of the entity. The entity with higher authority has a higher corresponding weight value;
[0031] Step 3: Perform a second classification on the same-domain entity group divided after the first classification according to...
Embodiment 2
[0036] On the basis of the previous embodiment, in step 3, the method for identifying the features of other entities in the same-domain entity group by the IoT routing device includes: a list of legal entity information preset in the IoT routing device; the IoT routing device The routing device is used to control the security of the Internet of Things routing device connected to it, and the list of legal entity information includes the unique identification of the entity that is allowed to access; when the Internet of Things routing device monitors the access of the entity, the calculation The unique identification of the entity; the unique identification is sent to the Internet of Things routing device, and the Internet of Things routing device determines whether the unique identification exists in the list of legal entity information, and if so, allows the entity the access of the entity; if not, the access of the entity is rejected; when the Internet of Things routing device...
Embodiment 3
[0039] On the basis of the previous embodiment, if the operation of writing the feature identifier into the entity fails, the information about the failure of the writing operation is sent to the Internet of Things routing device; the Internet of Things routing device according to the writing If the entry operation fails, the entity's access is denied.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com