E-mail security control method, client and system
An e-mail and security control technology, applied in the field of network security, can solve the problems that cannot be detected in time, the defense effect is difficult to meet expectations, and the protection effect is difficult to obtain, so as to achieve the effect of improving detection reliability and effective detection confirmation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
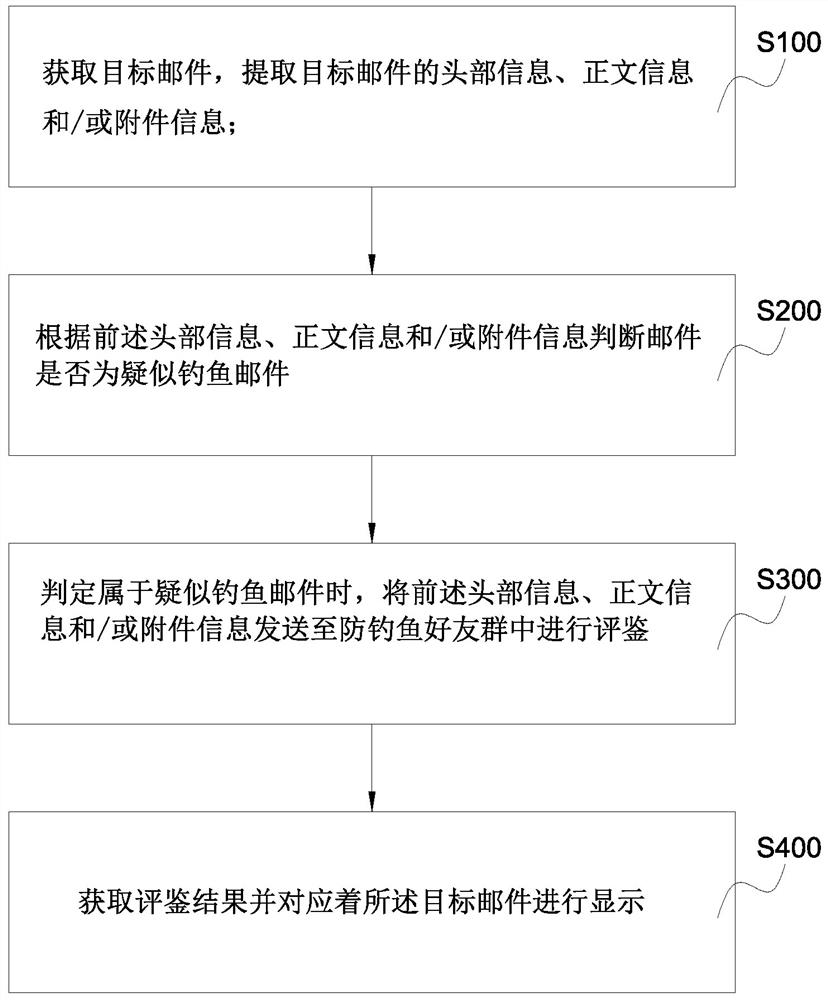
[0050] see figure 1 As shown, it is an email security control method provided by the embodiment of the present invention. The method comprises the steps of:
[0051] S100. Obtain a target email, and extract header information, text information and / or attachment information of the target email.
[0052] The target email may be any email received by the user, or may be an email actively selected by the user.
[0053] The header information, in this embodiment, may include multi-dimensional information such as sender address, return address, sending time, sender Message-ID, subject and format. The text information refers to the text content of the email. The attachment information refers to link attachment information of the email.
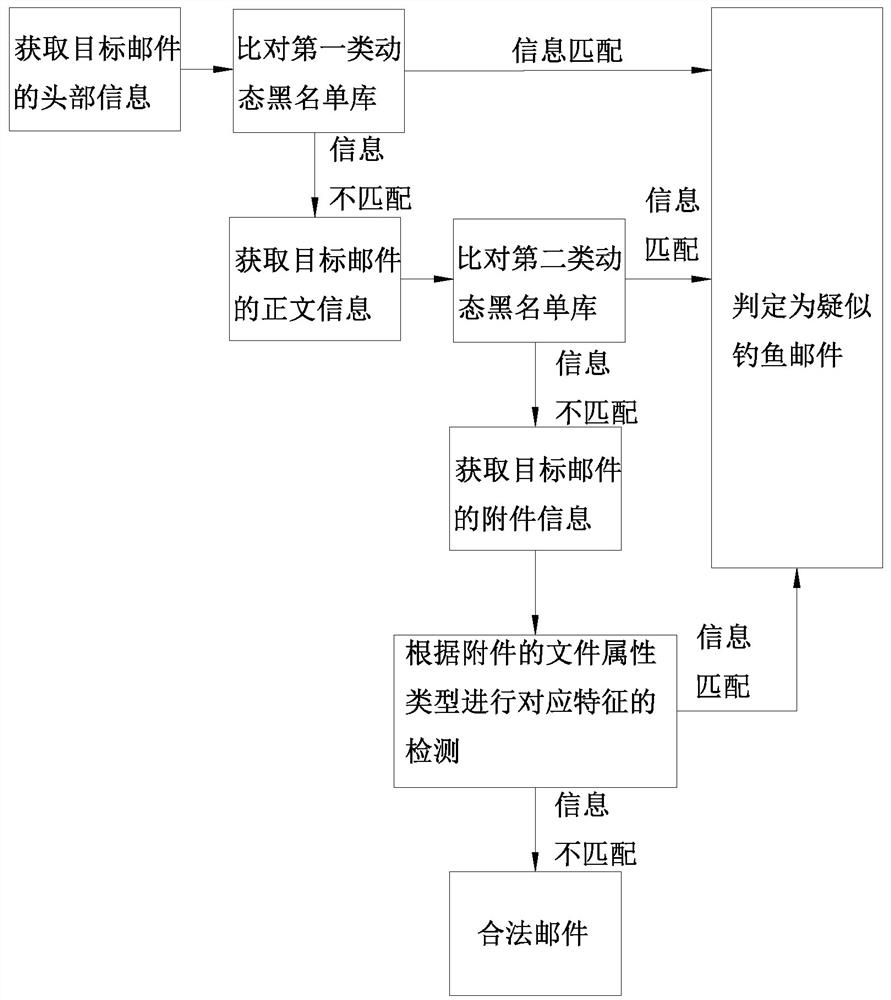
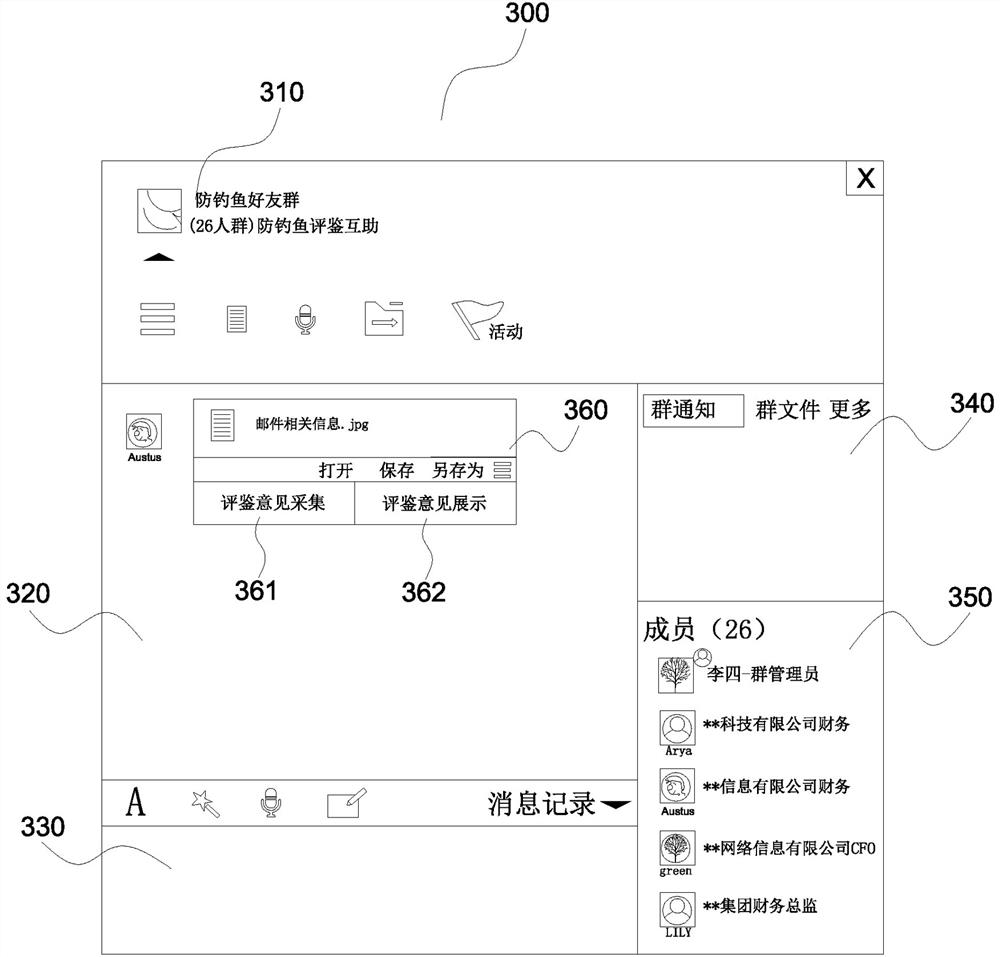
[0054] For the extraction of attachment information, it is first necessary to detect whether the email to be detected contains attachments. During specific implementation, it can be judged by detecting whether the attachment (attachment) field o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com