Data processing method, device and storage medium based on intelligent security equipment
A technology of intelligent security and data processing, applied in the field of data processing, can solve problems such as inability to send data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
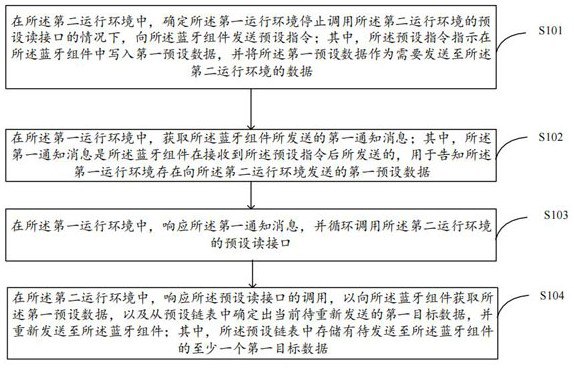
[0113] Example 1, the specific steps include:
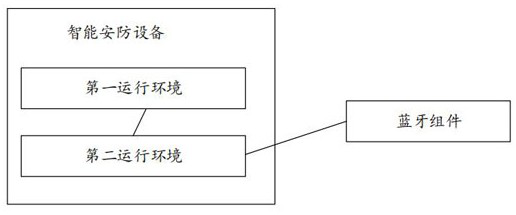
[0114]Step 1-1: In the case that the REE has the first target data that needs to be sent to the Bluetooth component, the REE calls the preset write interface of the TEE (that is, the second operating environment), and uses the preset write interface to write The first target data is passed into the TEE.
[0115] Here, it should be noted that both the preset writing interface and the preset writing interface described in this example are software interfaces.
[0116] Step 1-2: In the TEE, determine whether there is data in the preset linked list, that is, whether there is historical data. If there is no data in the preset linked list, execute step 1-3; otherwise, execute step 1-4.
[0117] Here, it should be noted that the preset linked list is preset in the TEE, and the preset linked list is used to store data to be sent to the Bluetooth component, for example, used to store the first target data, and at the same time, record t...
example 2
[0133] Example 2, the specific steps include:
[0134] Step 2-1: In the case that the REE has the first target data that needs to be sent to the Bluetooth component, the REE calls the preset write interface of the TEE (that is, the second operating environment), and uses the preset write interface to write The first target data is passed into the TEE.
[0135] Here, it should be noted that both the preset writing interface and the preset writing interface described in this example are software interfaces.
[0136] Step 2-2: In the TEE, respond to the call of the preset writing interface to write the first target data into the preset linked list; and, after successfully storing in the preset linked list, Send the first target data to the bluetooth component to complete the write operation to the bluetooth component. Go to steps 2-3.
[0137]Here, it should be noted that the preset linked list is preset in the TEE, and the preset linked list is used to store data to be sent t...
Embodiment approach 1
[0150] Embodiment 1: The data that needs to be reported to the TEE in the Bluetooth component is the second target data or the first preset data; here, in practical applications, the Bluetooth component will notify the REE of the existence of the second target data or The first preset data needs to be reported to TEE; the specific steps include:
[0151] Step 1: The Bluetooth component notifies the REE of the existence of the second target data to be reported to the TEE by wireless communication. Specifically, the Bluetooth component sends a second notification message to the REE by wireless communication, and the second notification message is used to notify There is data sent to the TEE in the REE Bluetooth component; for example, it is the response data sent after the Bluetooth component successfully processes the received first target data, that is, the second target data.
[0152] Step 2: In the REE, periodically call the preset read interface of the TEE, that is, the REE...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com