Method, system, and computer-readable storage medium for detecting a Trojan horse image
A detection method and picture technology, applied in computer parts, computer security devices, computing, etc., can solve the problems of great difficulty, limited image classification accuracy, and disordered text, and achieve the effect of comprehensive feature dimensions and improved detection accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In order to illustrate the embodiments of the present invention more clearly, the specific implementation manners of the present invention will be described below with reference to the accompanying drawings. Obviously, the accompanying drawings in the following description are only some embodiments of the present invention, and those skilled in the art can obtain other accompanying drawings based on these drawings and obtain other implementations.
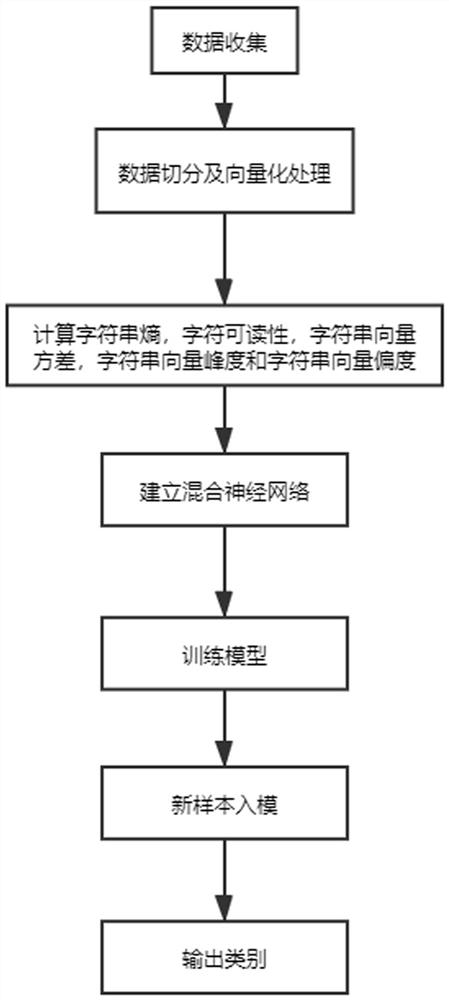
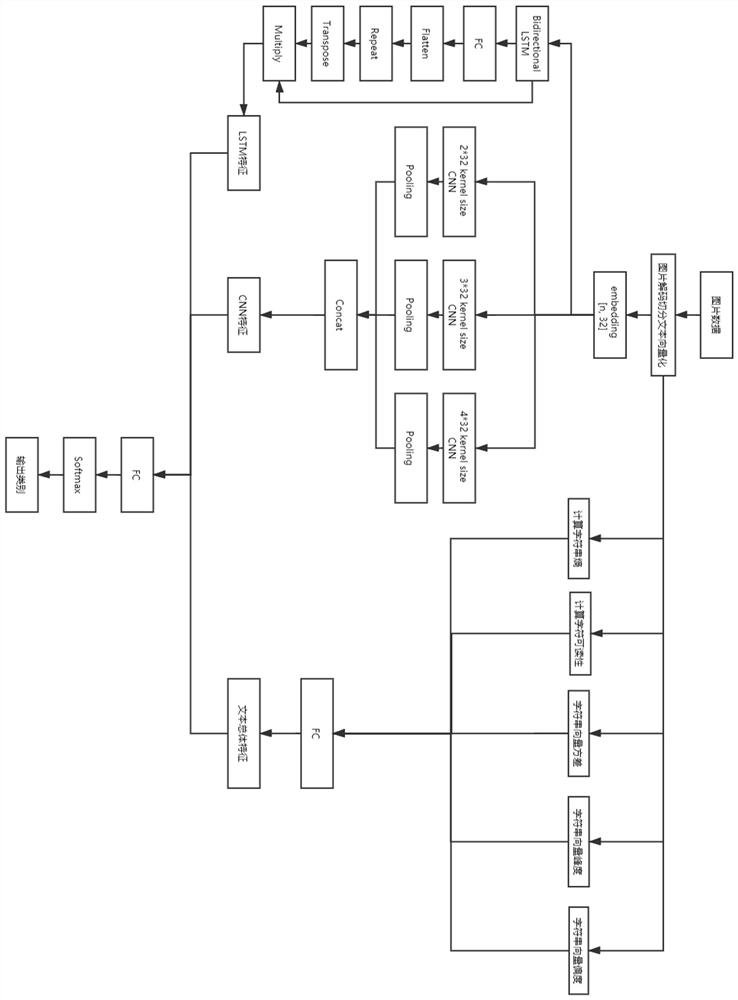
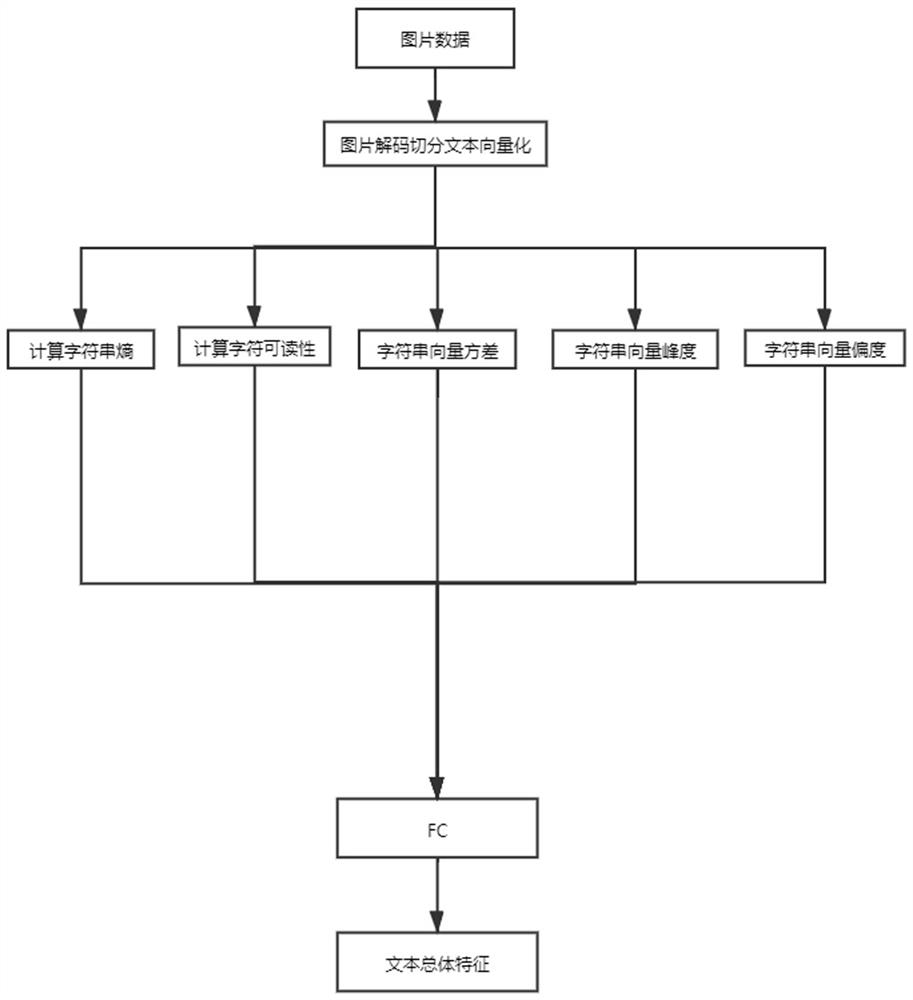
[0052] Such as figure 1 and figure 2 As shown, the Trojan horse picture detection method of the embodiment of the present invention comprises the following steps:
[0053] S1. Data collection, creating an image data set, decoding and segmenting pictures in the image data set;
[0054] Among them, the image data set includes normal pictures, Windows Trojan pictures, linux Trojan pictures and webpage Trojan pictures.
[0055] Specifically, after each picture is decoded, each K character segmentation as a text sample, ins...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com