A low-voltage user electricity stealing identification method based on edge-end fusion
A technology for stealing electricity and users, applied in the direction of measuring electric variables, data processing applications, instruments, etc., can solve the problems of difficult anti-stealing electricity, achieve strong adaptability of the method, reduce user data analysis work suspected of stealing electricity, and achieve good engineering The effect of practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The specific implementation of the present invention will be further described below with reference to the accompanying drawings and examples.
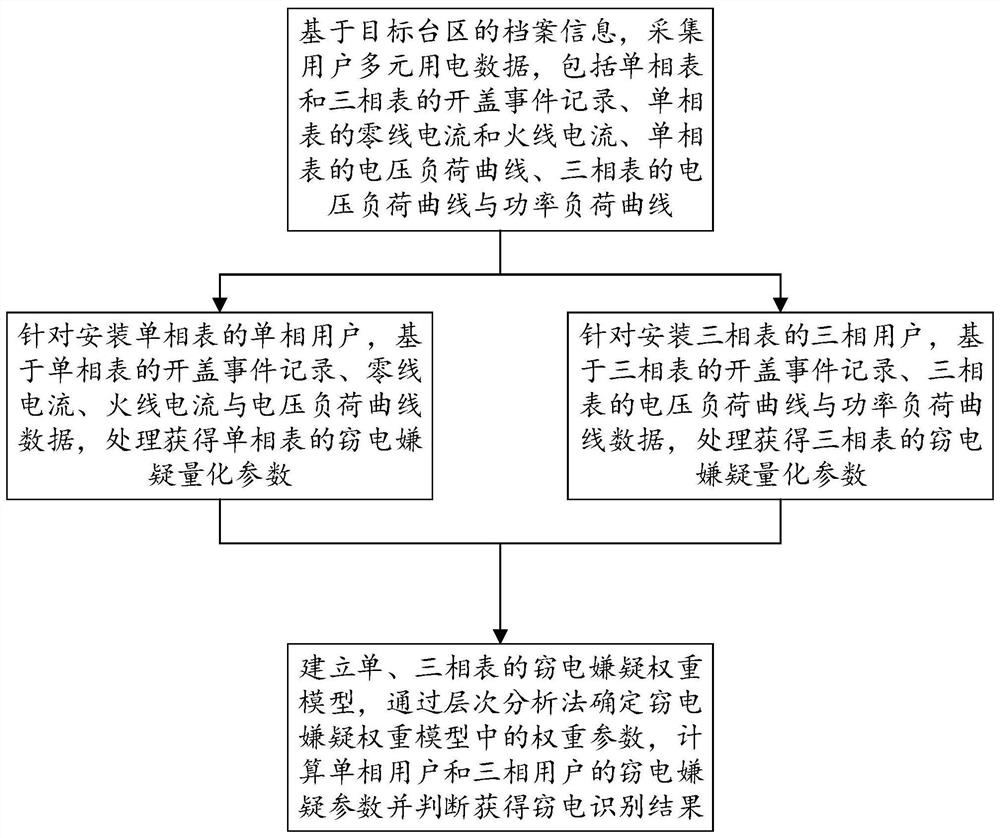
[0063] like figure 1 The implementation process provided for the embodiment of the present invention specifically includes the following steps:
[0064] Step 1: Based on the file information of the target station area, collect the multivariate electricity consumption data of the user's electricity meter, including the cover-opening event record of the single-phase meter and the three-phase meter, the neutral current and live line current of the single-phase meter, and the voltage of the single-phase meter. Load curve, voltage load curve and power load curve of three-phase meter;
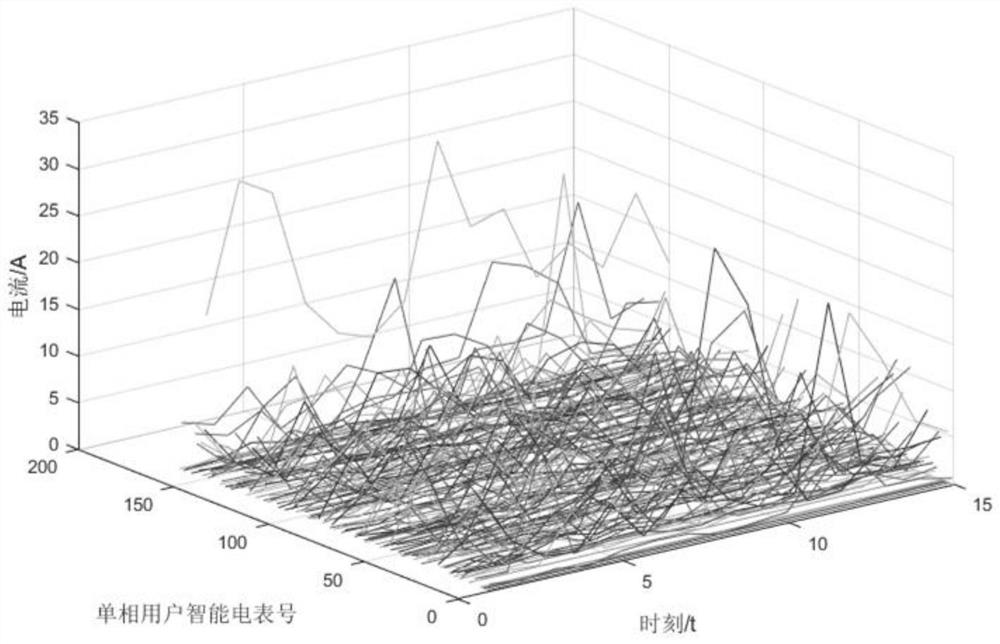
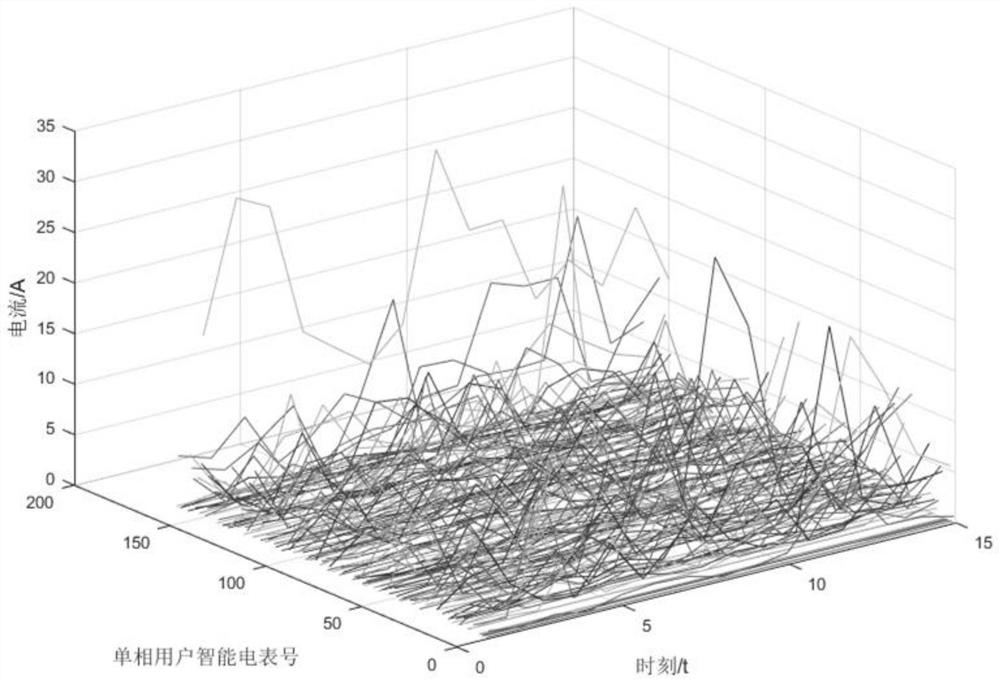
[0065] Specifically, the terminal-side equipment (ie the electricity meter) is used to collect the zero-line current, live-line current and voltage load curve data of the single-phase meter, and the abnormality of the zero-line current deviation and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com