Low-voltage user electricity stealing identification method based on side-end fusion
An identification method and electricity stealing technology, which is applied in the direction of measuring electrical variables, data processing applications, instruments, etc., can solve the problems of high difficulty in anti-electricity theft, and achieve the effects of strong adaptability, low cost, and good engineering practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The specific implementation of the present invention will be further described below in conjunction with the accompanying drawings and examples.
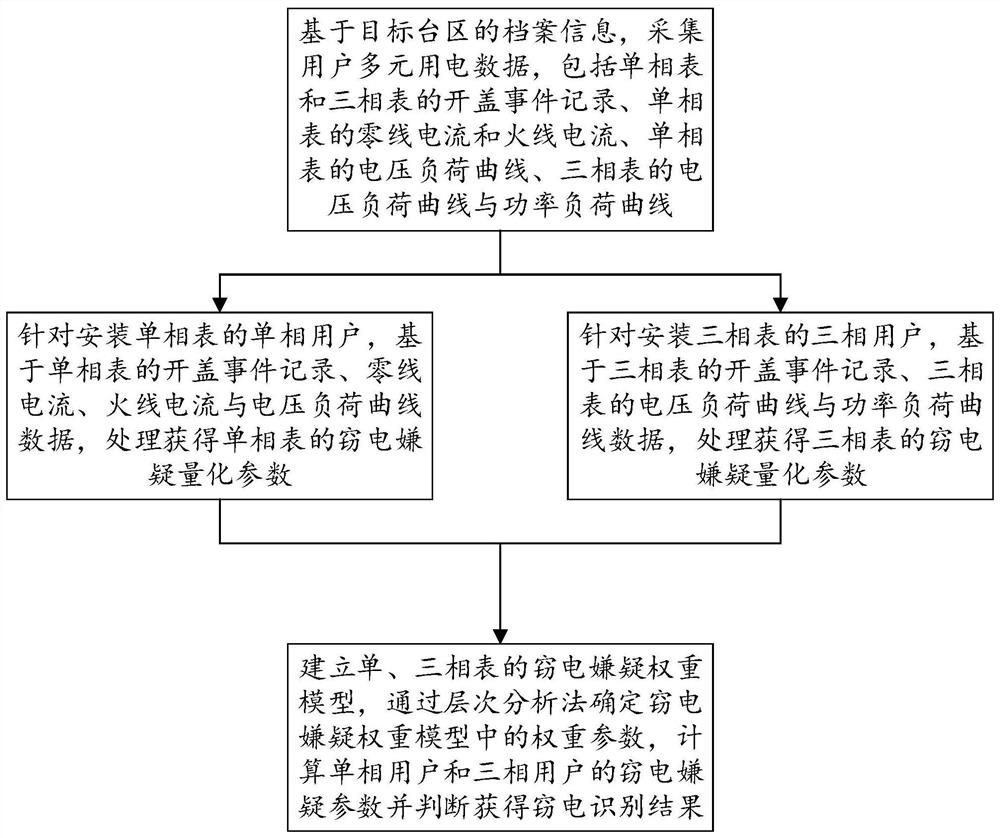
[0063] Such as figure 1 The implementation process provided for the embodiment of the present invention specifically includes the following steps:
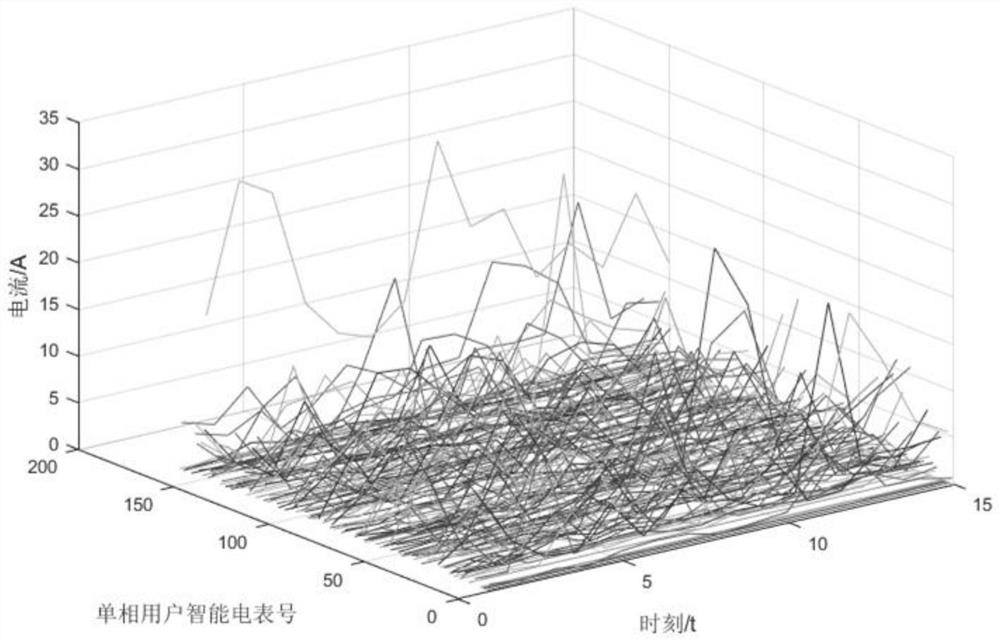
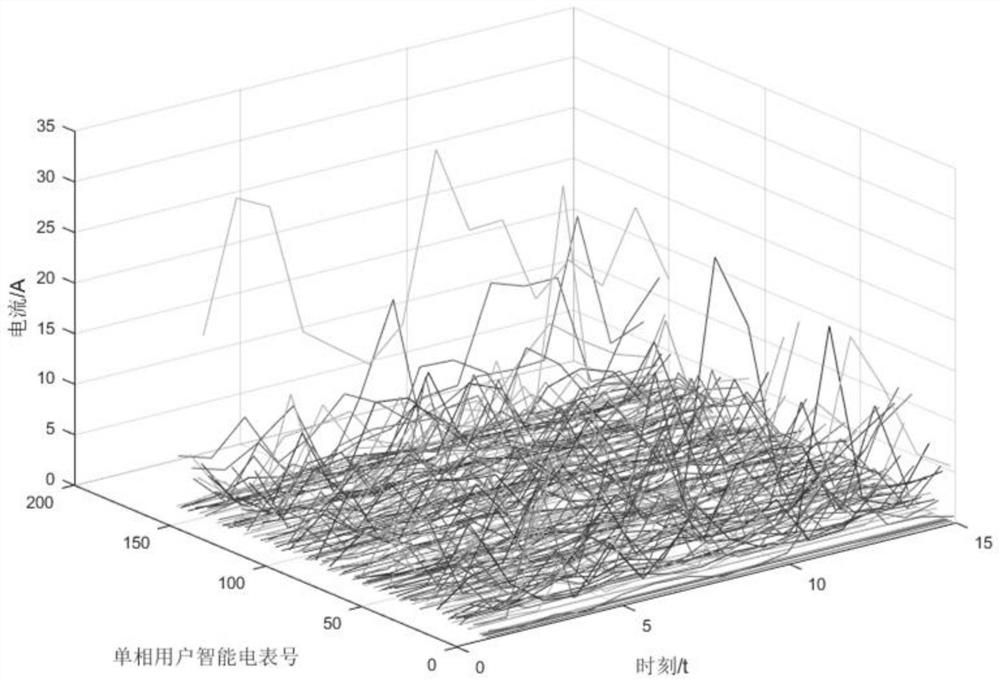
[0064] Step 1: Based on the file information of the target station area, collect multiple electricity consumption data of the user's electricity meter, including the event record of opening the cover of the single-phase meter and the three-phase meter, the neutral current and the live wire current of the single-phase meter, and the voltage of the single-phase meter Load curve, voltage load curve and power load curve of three-phase meter;
[0065] Specifically, the end-side equipment (that is, the electric meter) is used to collect the zero line current, live line current and voltage load curve data of the single-phase meter, and the current deviation and voltage abnormality of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com