DDoS attack traffic identification and detection method in SDN (Software Defined Network)
A technology for attacking traffic and detection methods, applied in character and pattern recognition, instruments, digital transmission systems, etc., to achieve the effect of strong practicability, improved accuracy, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
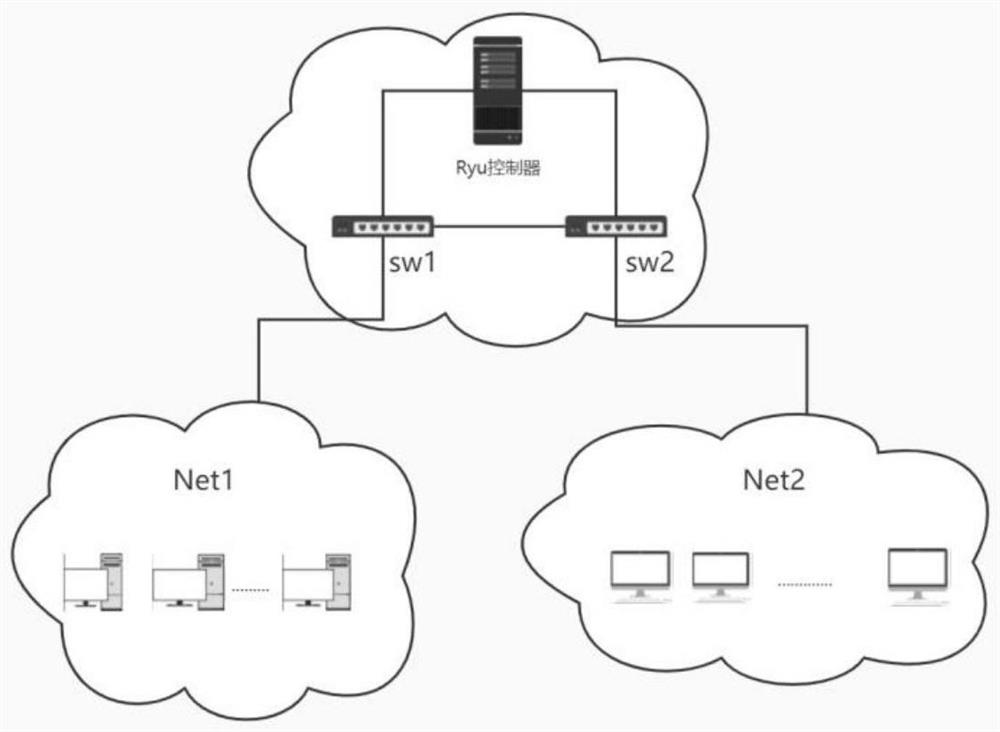
[0091] A specific implementation scenario of the present invention is introduced below, the SDN controller selects the Ryu controller, the southbound protocol between the controller and the switch is the OpenFlow protocol, the Net1 network connected to the switch sw1 includes 25 hosts, and the Net2 network connected to the switch sw2 includes 10 hosts. Net1 is the packet sending network, and Net2 is the attacked network. Net1 can send DDoS attack traffic or normal packets to Net2. Use the DDoS attack tool hping3 to send TCP SYN Flood, UDP Flood, and ICMP Flood attack packets from the Net1 network to a specific host on the Net2 network. See the attached network topology diagram figure 1 .
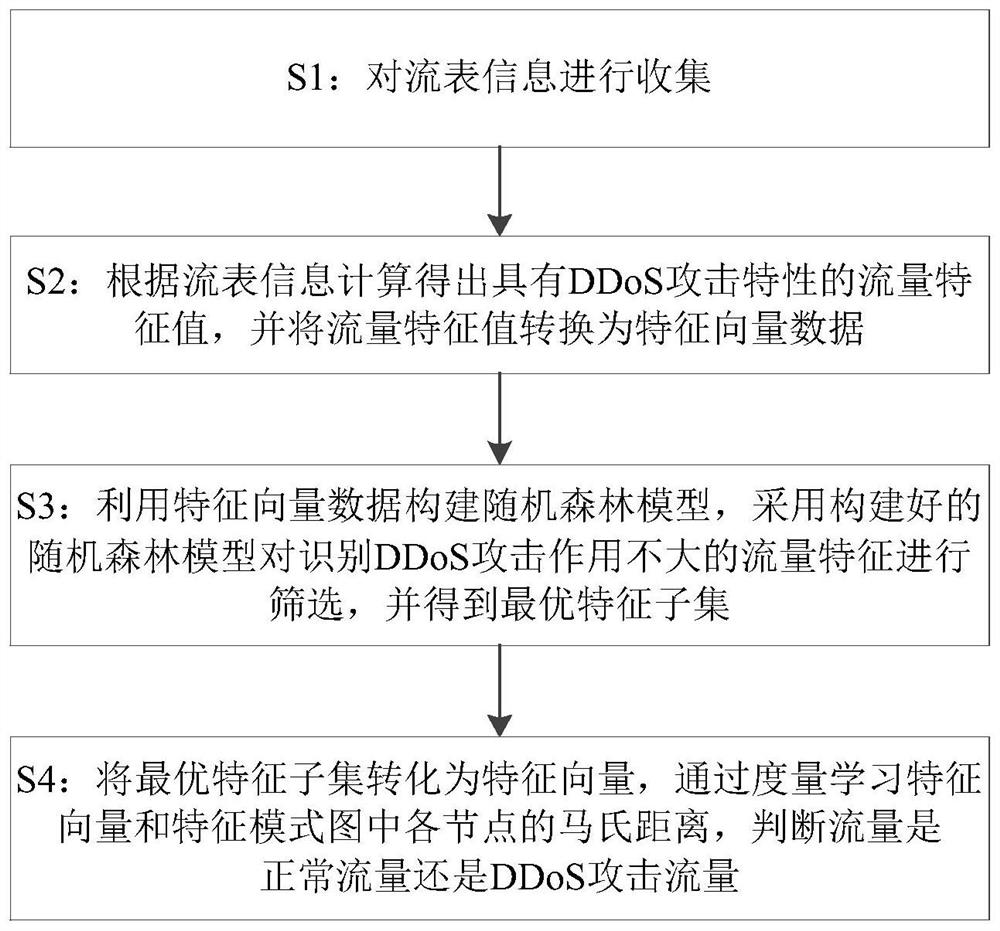
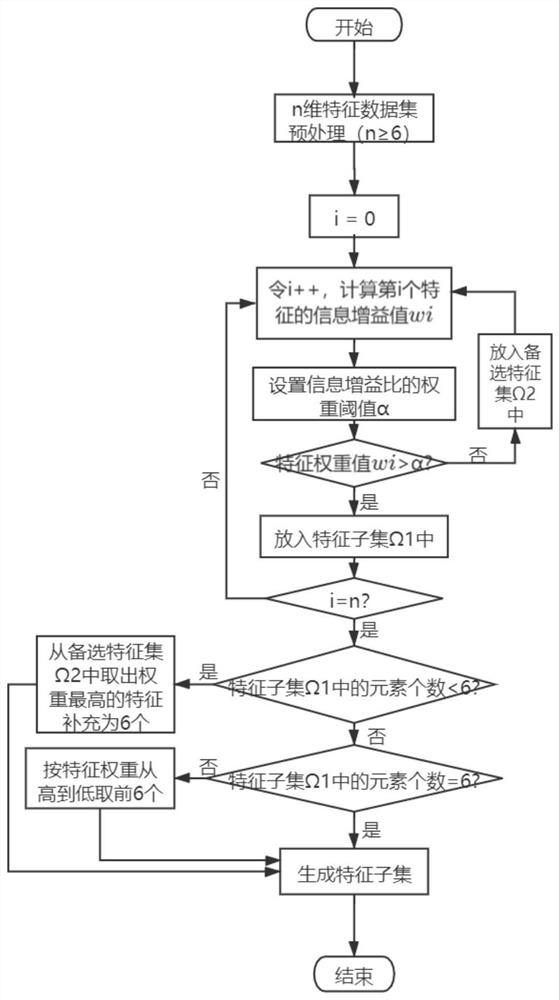
[0092] The present invention provides a method for identifying and detecting DDoS attack traffic under an SDN network, and the method includes the following steps:
[0093] S1: Collect flow table information;
[0094] The flow table information is collected through the OpenFlow protocol,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com