SQL injection statement transformation method based on context-independent grammar
A context and statement technology, applied in the field of network security, can solve the problems that SQL injection cannot be triggered normally, cannot guarantee functionality and maliciousness, and achieve the effect of avoiding functional damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
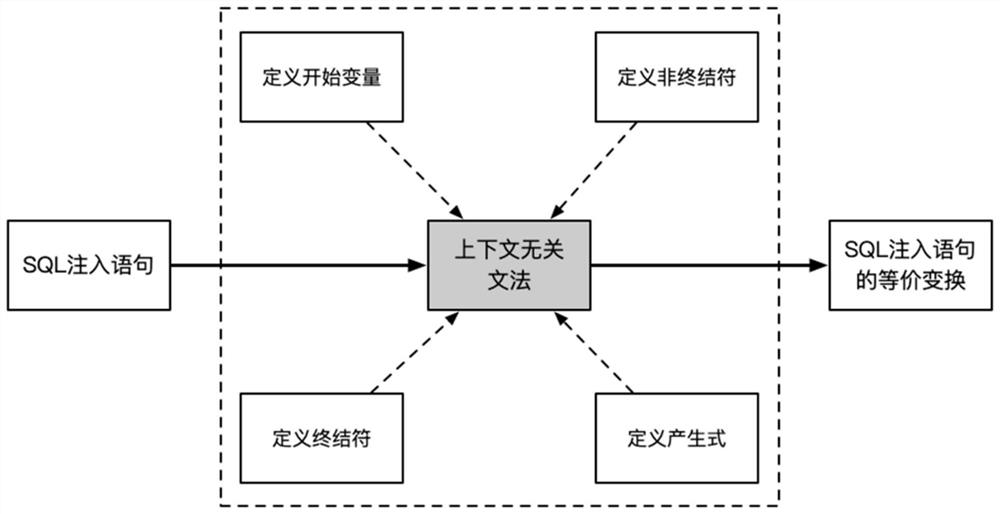
[0018] Such as figure 1 As shown, the present invention is based on a context-free grammar SQL injection statement transformation method, by defining the start variable set, terminal symbol set, non-terminal symbol set, production formula, etc., to construct the context-free grammar, and then through the context-free grammar for SQL The injection statement generates a large number of equivalent transformations, making the transformation result of the SQL injection statement more realistic, that is, retaining its functionality and maliciousness. Specifically include the following steps:
[0019] (1) Construct a context-free grammar rule set G, including four parts: non-terminal symbol set V, terminal symbol set Σ, start variable set S, and production set R, namely G=(V,Σ,S,R).
[0020] (1.1) Construct a non-terminal set V, which is used to expand the generation range of SQL injection statements, representing the intermediate state, that is, the potential generation target.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com