Multi-level multi-tenant cross authorization management method
An authorization management and multi-tenant technology, applied in the direction of electrical digital data processing, instruments, digital data authentication, etc., can solve the problems of being unable to access the resources of the intermediate tenant 2, unable to access the resources of the intermediate tenant 2, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
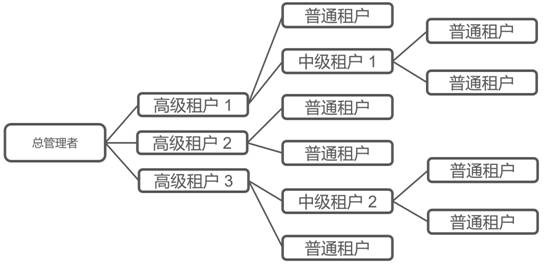
[0063] Such as Figure 4 As shown, according to one aspect of the present disclosure, a multi-level multi-tenant cross-authorization management method is provided, including the following steps:
[0064] S100. Define several management roles in different organizations, and configure access rights and resources for the management roles;
[0065] This technology first needs to define the basic information of each management role. The configuration of the basic information of the management role includes the configuration of access rights and resources. Through the configuration of access rights and resources, it can be specified:
[0066] Which tenants (organizations) each management role can manage; which resources each management role can access for a specific tenant; which operation means each management role can use for specific accessible resources of a specific tenant (list , read-only, writable, deleteable, etc.).
[0067] Such as Figure 5 The information configuratio...
Embodiment 2
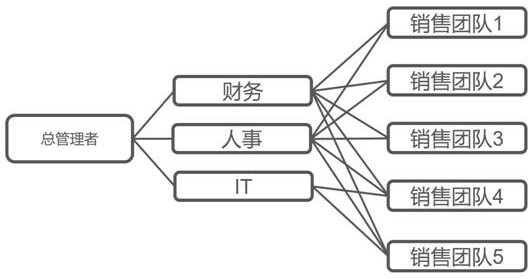
[0101] According to another aspect of the present disclosure, an authorization tree is provided. When traversing nodes of the authorization tree, the multi-level multi-tenant cross-authorization management method is implemented.
[0102] The specific structure of the authorization tree and the specific implementation and application of the multi-level multi-tenant cross-authorization management method in Embodiment 1 when traversing the authorization tree are specific to Embodiment 1, and will not be described in detail in this embodiment.
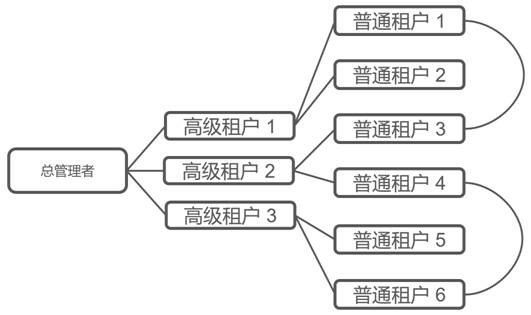
[0103] In practical applications, since there are multiple users under each tenant, each user may have its own unique authorization tree, and the flattened tenant list of the authorization tree and their resources and permissions are different for the same tenant. Say, every user is basically the same. In this case, if a new tenant is introduced, the authorization trees of all roles will be modified in batches, and the workload will be ver...
Embodiment 3
[0108] Based on the technical implementation principles and methods of Embodiments 1 and 2, this embodiment correspondingly proposes a management device to implement a multi-level multi-tenant cross-authorization management method.
[0109] In this embodiment, the functions of each module and the information interaction mode between the modules are referred to Embodiments 1 and 2, and will not be repeated here.
[0110] In addition, the connection between modules is not limited to wired or wireless.
[0111] According to another aspect of the present disclosure, there is also provided an apparatus for implementing the multi-level multi-tenant cross-authorization management method, including:
[0112] Role definition and configuration module: used to define several management roles in different organizations, and perform access rights and resource configuration on the management roles; mount module: used to select cross-server users who are in different organizations from the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com