Patents
Literature
43 results about "Cross organizational" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
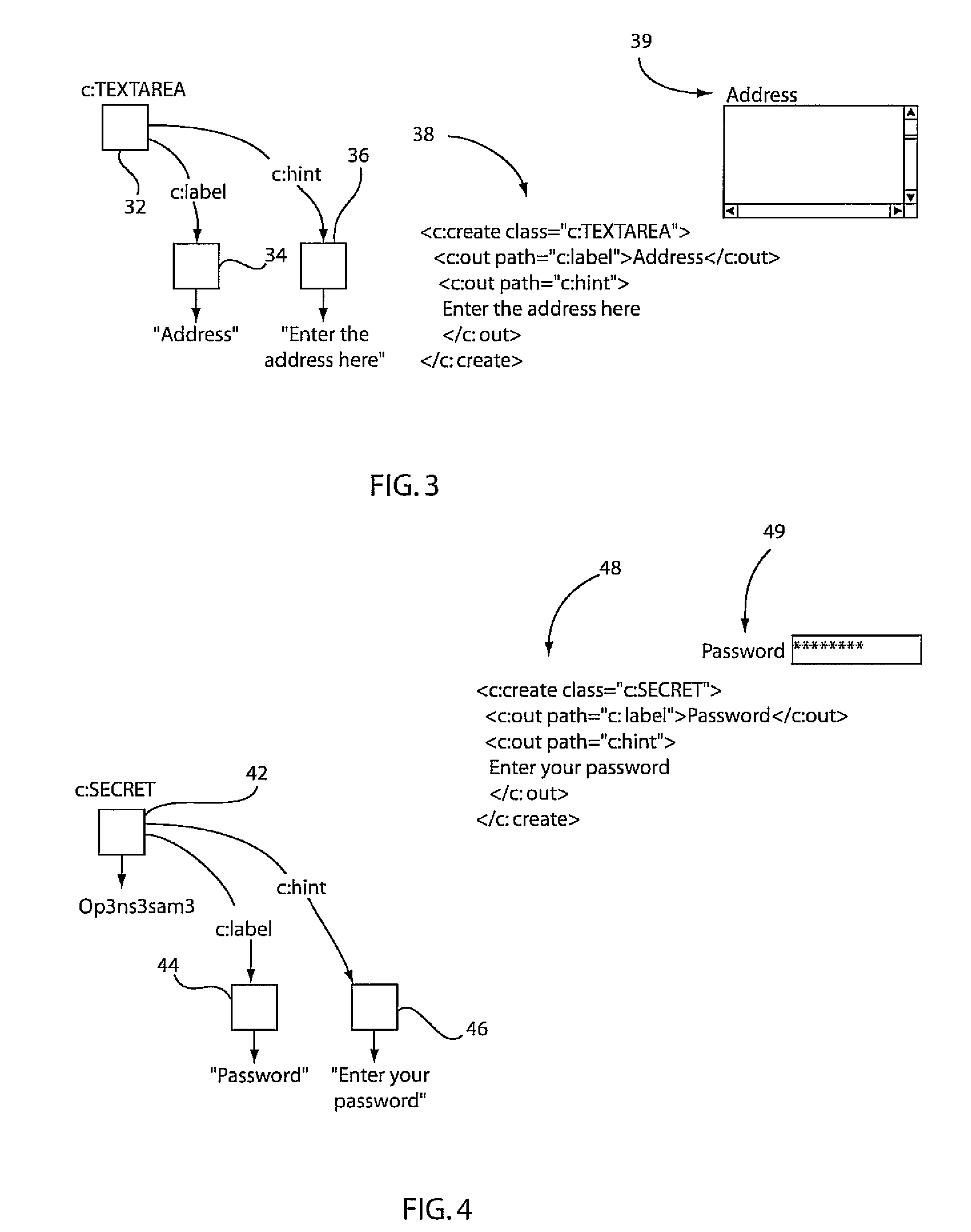
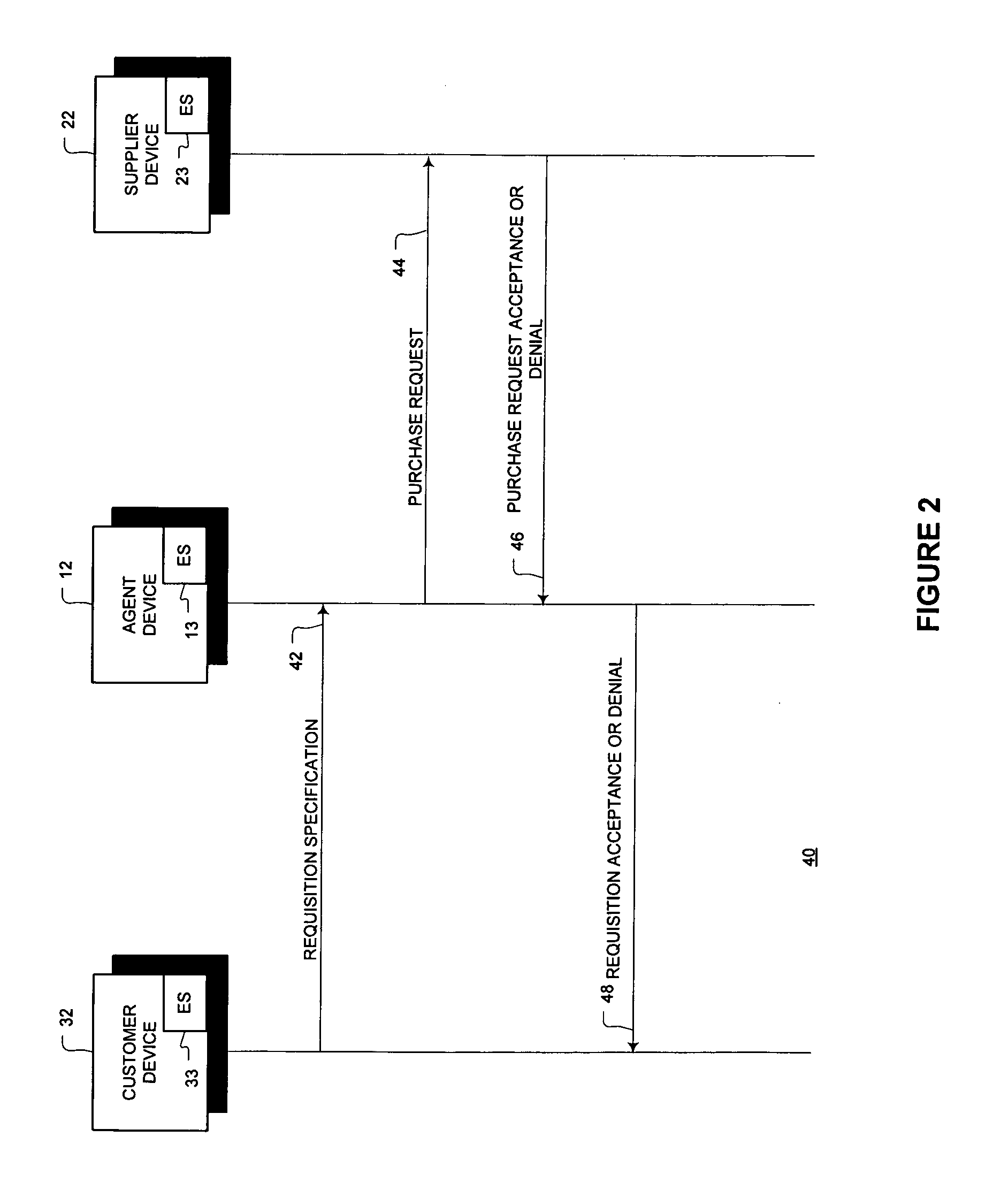
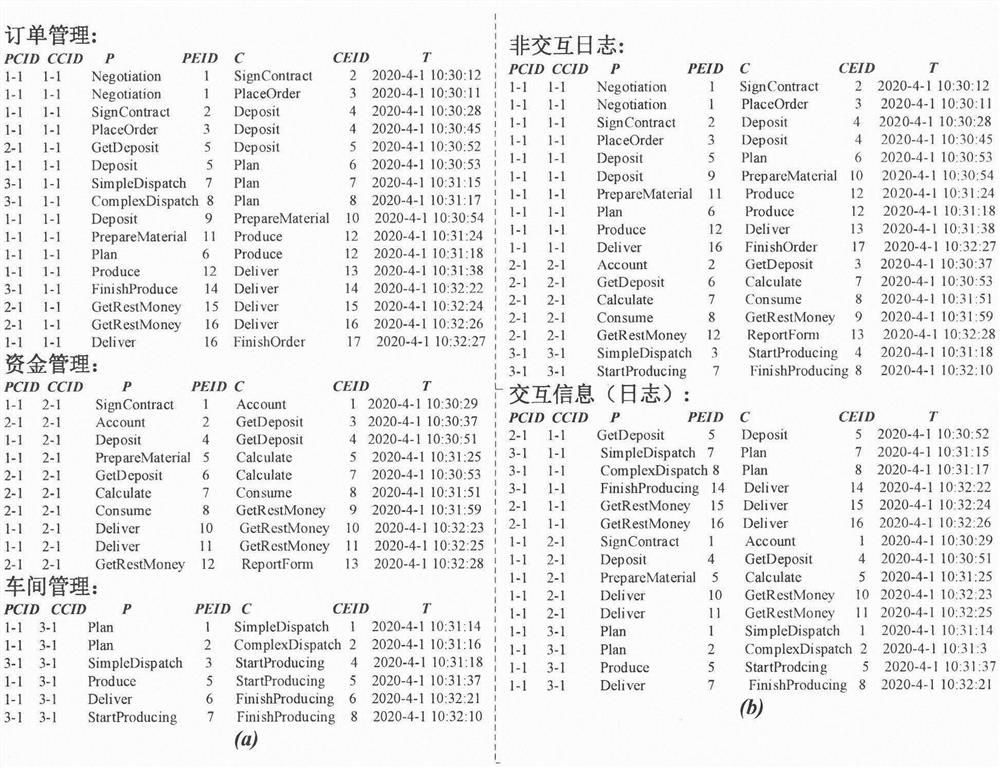
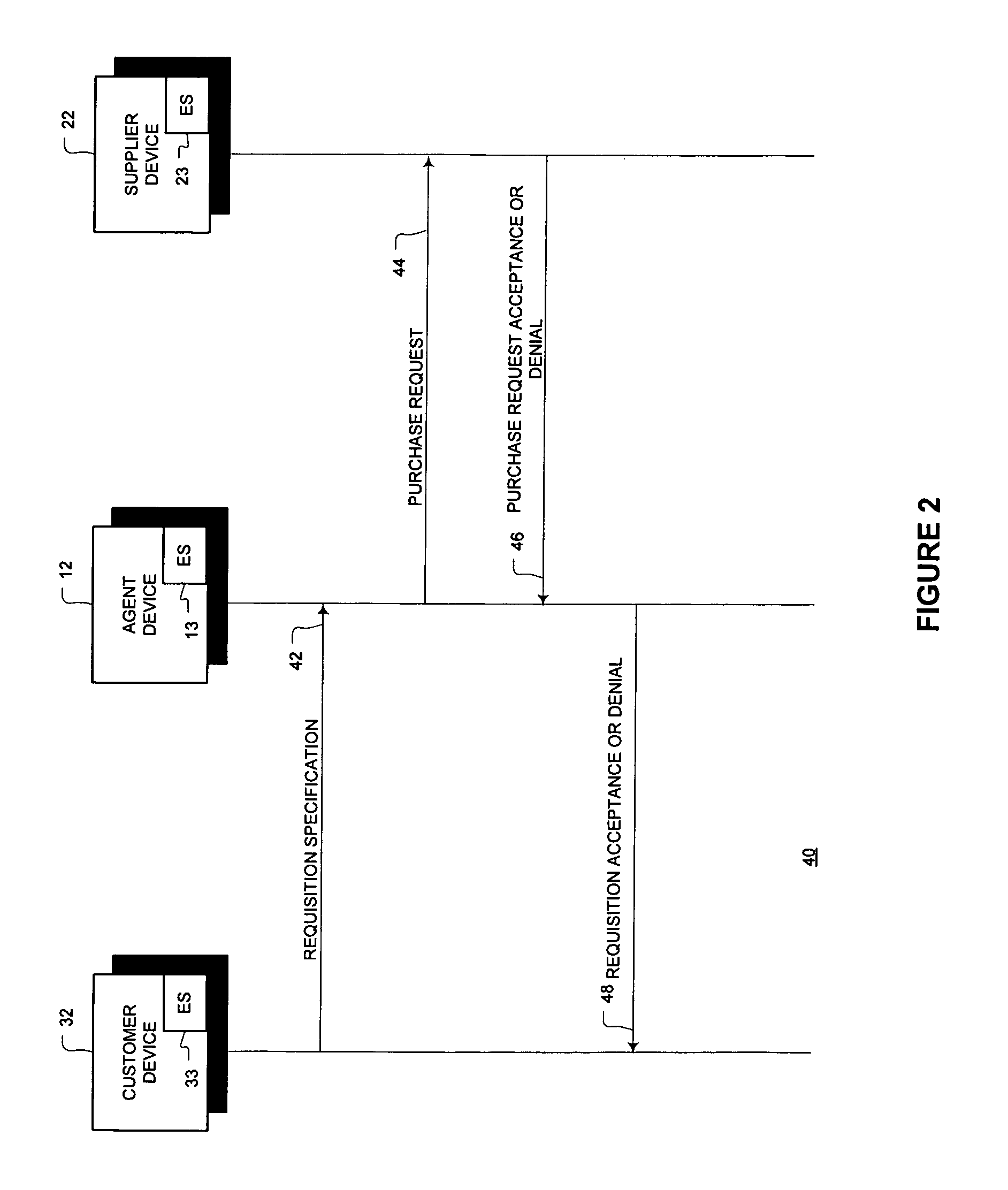
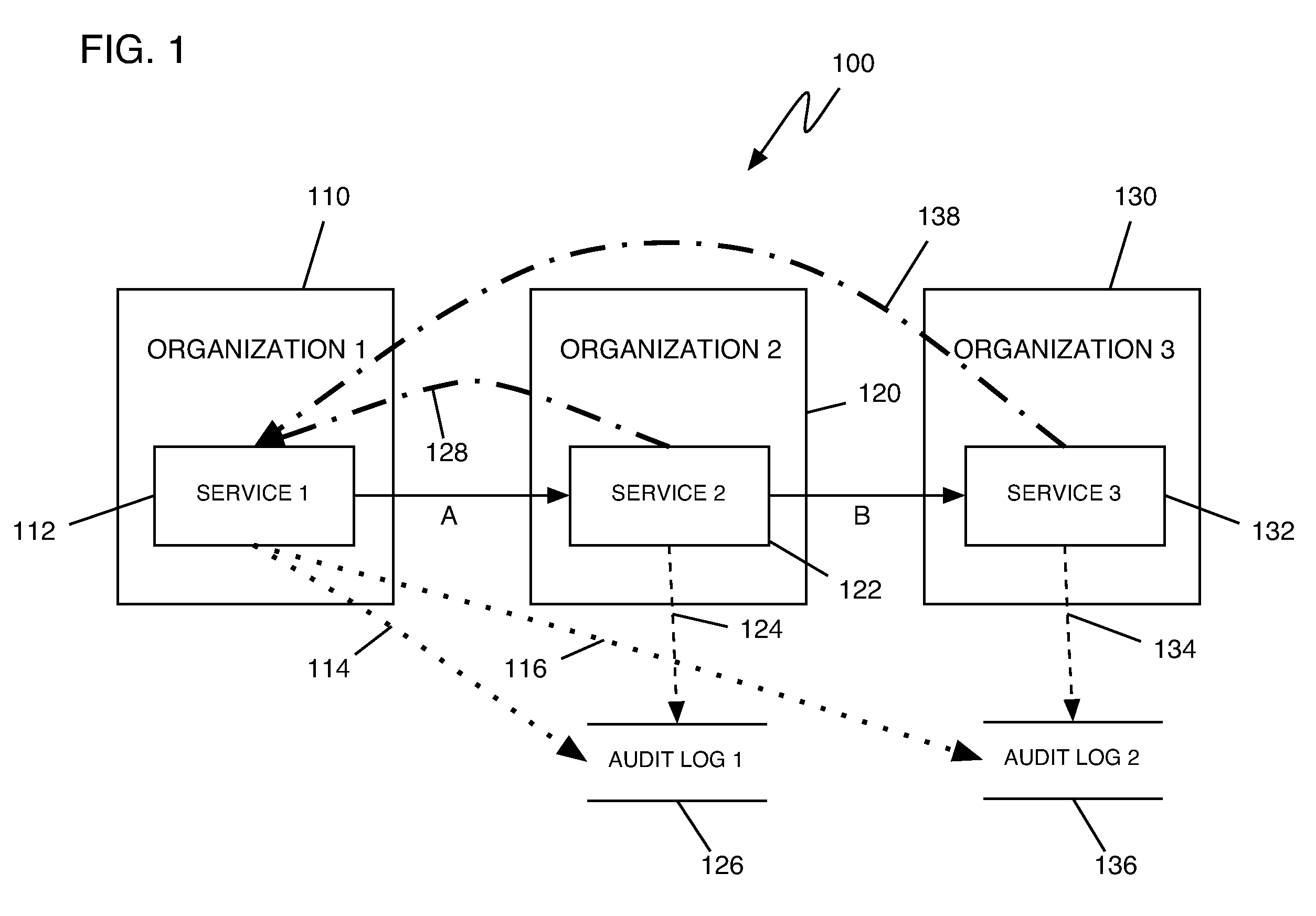
In the Defense Travel System (DTS), the Cross-Organization (X-Org) Funding feature allows an organization to share a Line of Accounting (LOA), to make funding available to another organization or to a specific traveler.
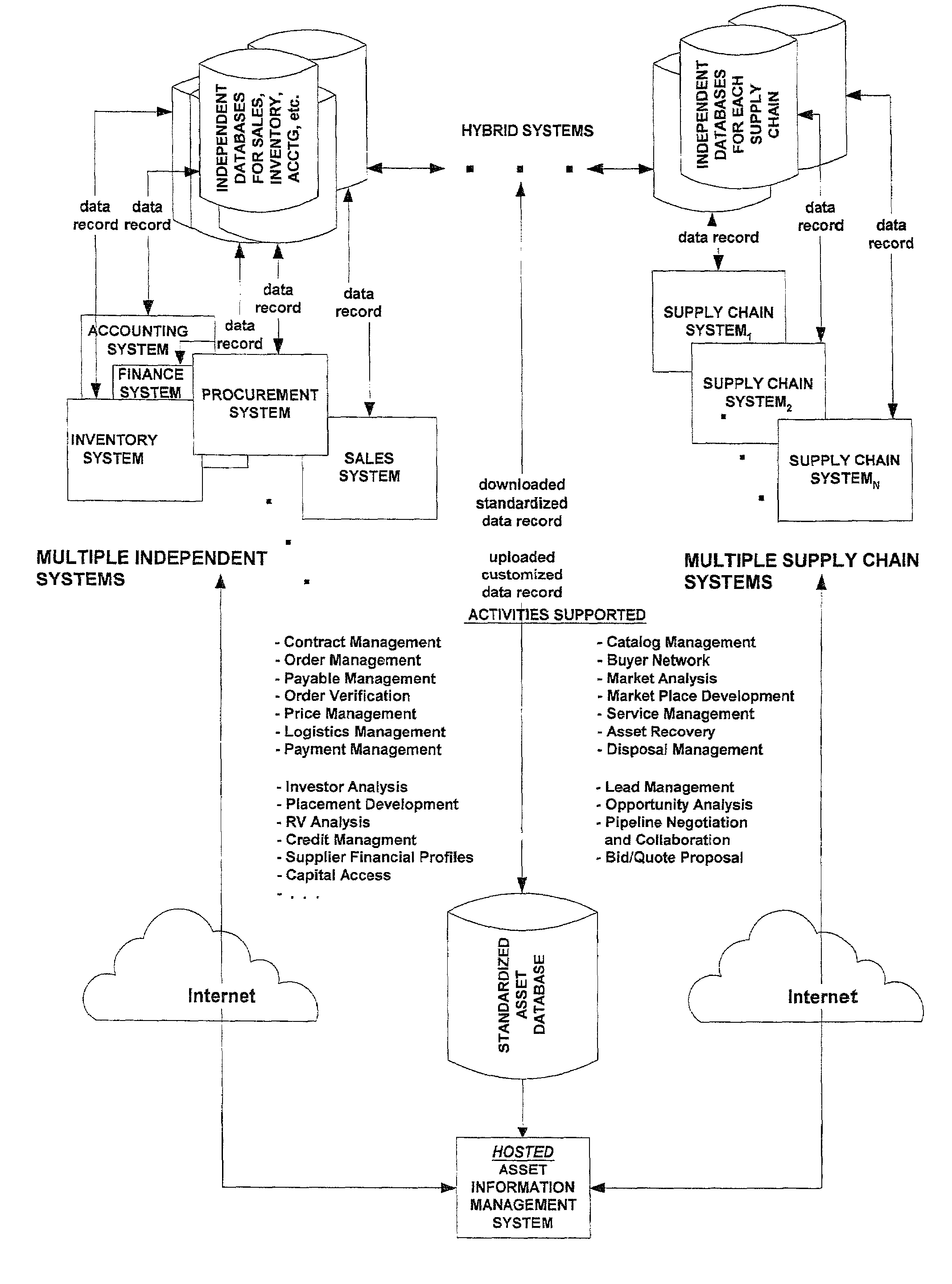
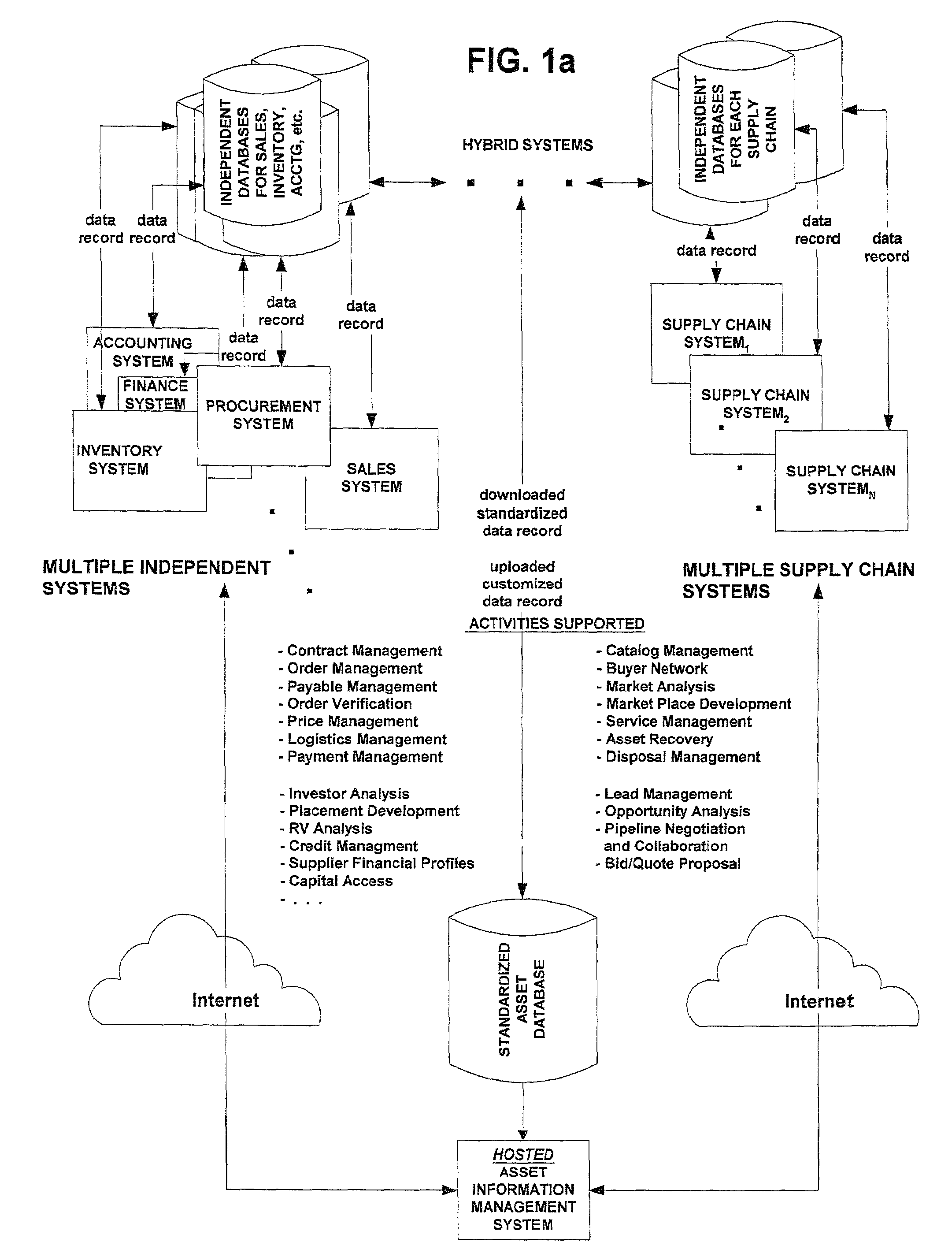
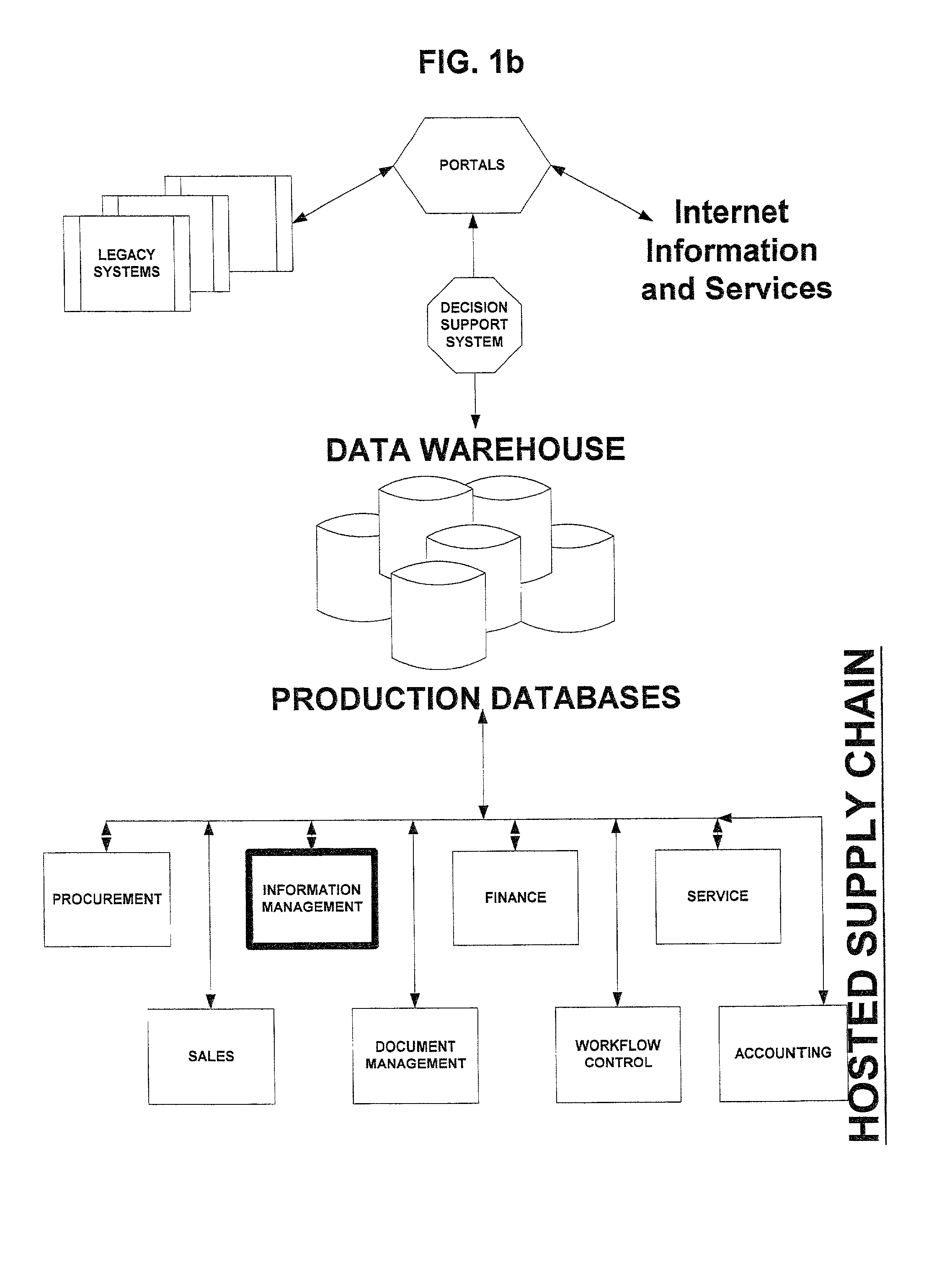
Hosted asset information management system and method
InactiveUS7552134B2Low costThe result is validSpecial service provision for substationDigital data processing detailsLegacy systemEngineering
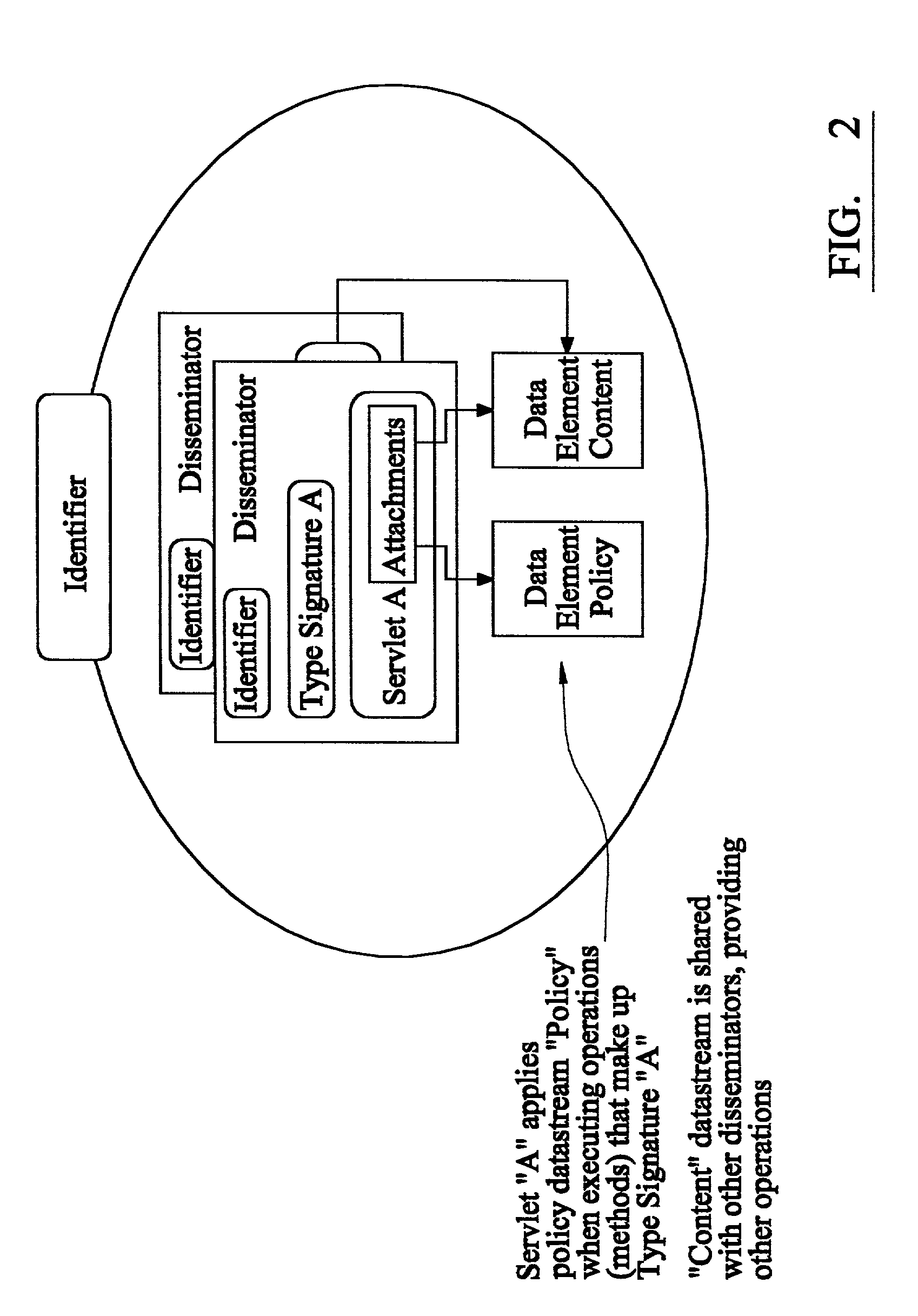
A system and method for managing asset information is presented for both a standalone architecture and as a component of a total asset management system. The range of users for the system and method of the present invention spans single users to partners of a supply, chain and in the latter case, cross-organization asset detail information is provided to supply chain partners. The system and method of the present invention is intended to be interfaced with other components of a total asset management system, e.g., a procurement system for asset acquisition, and may be interfaced to legacy systems.
Owner:EPLUS
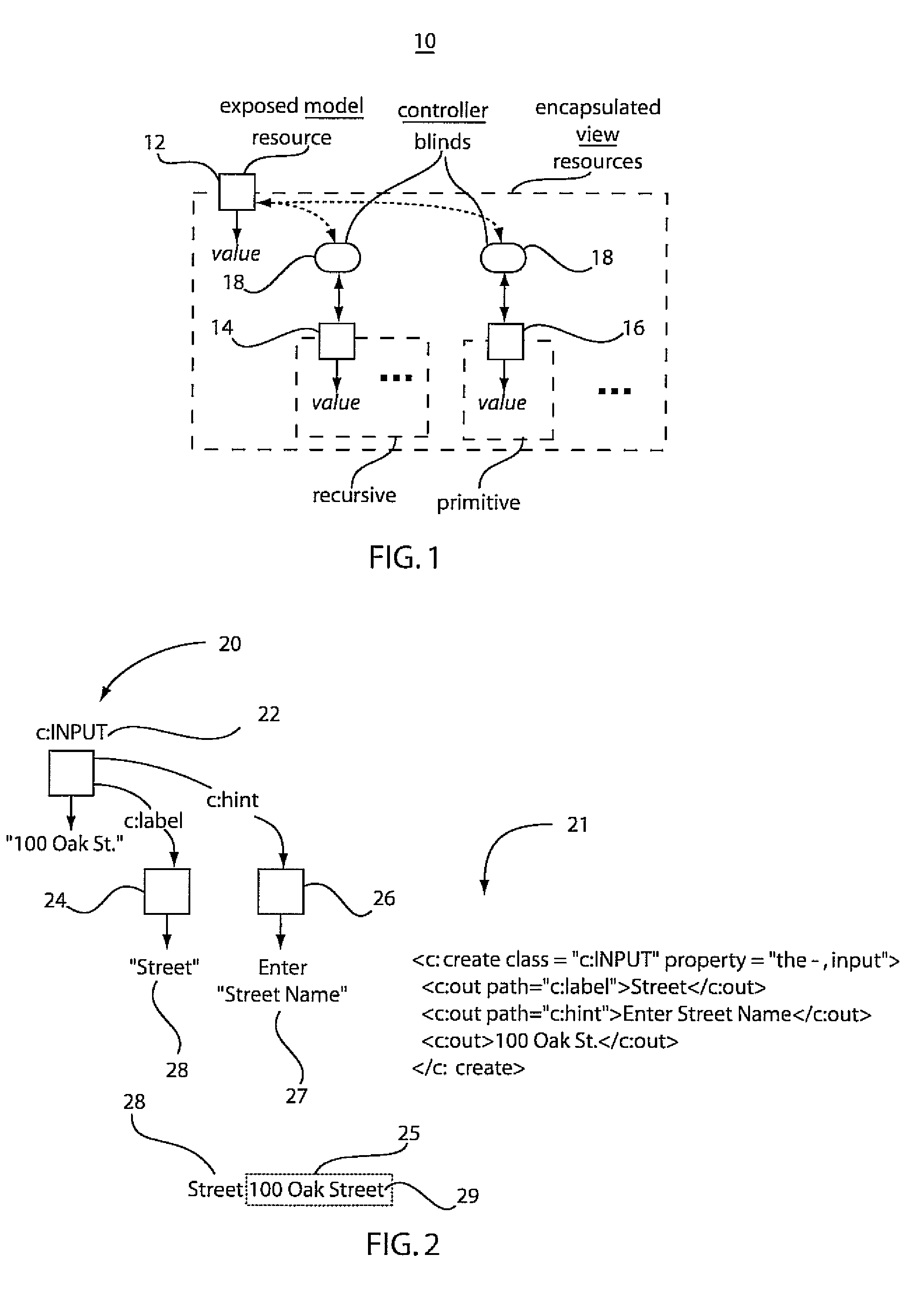
System and method for presentation of cross organizational applications
ActiveUS20090235230A1Reduce complexitySoftware designVisual/graphical programmingSoftware engineeringApplication software
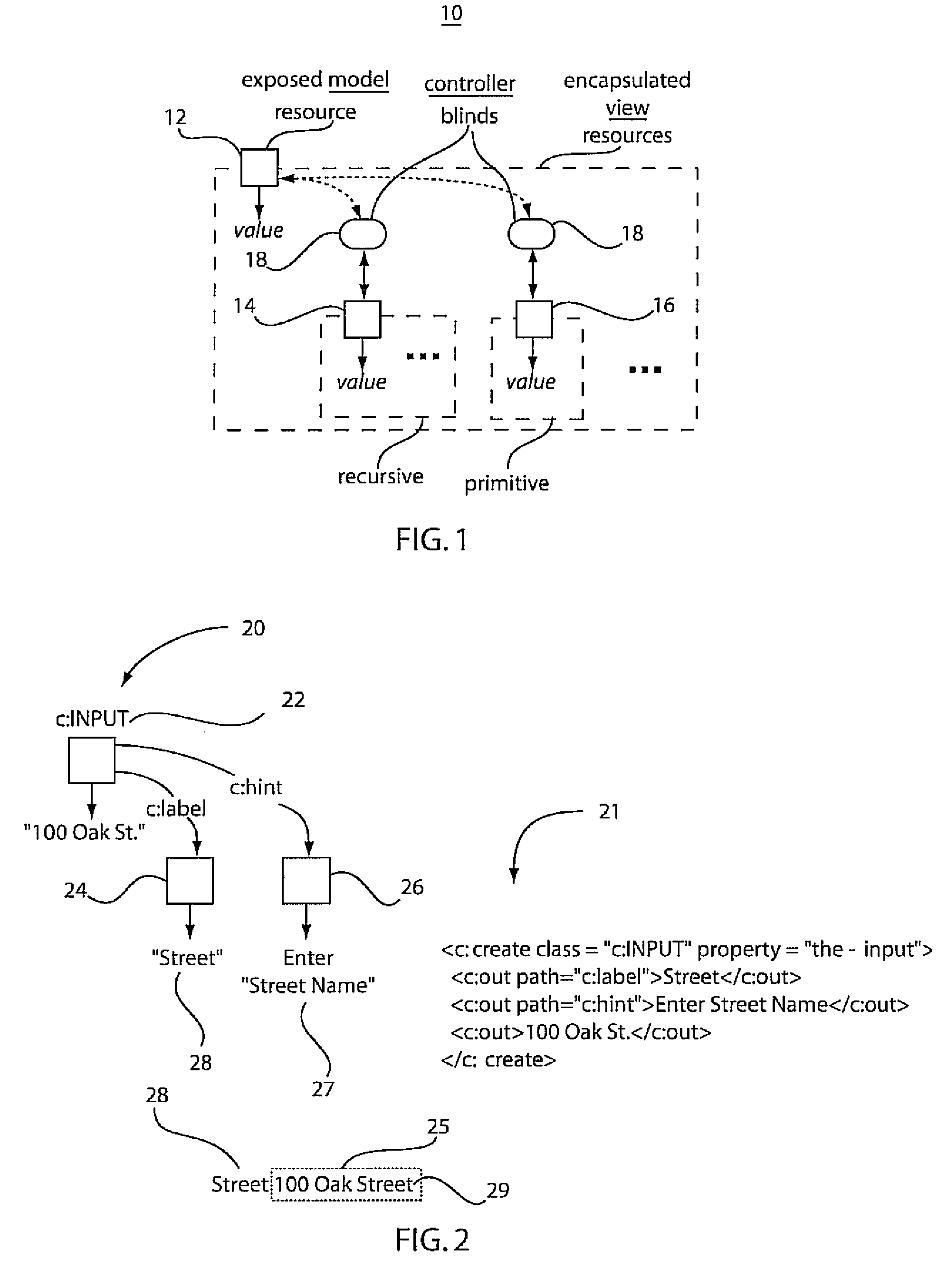
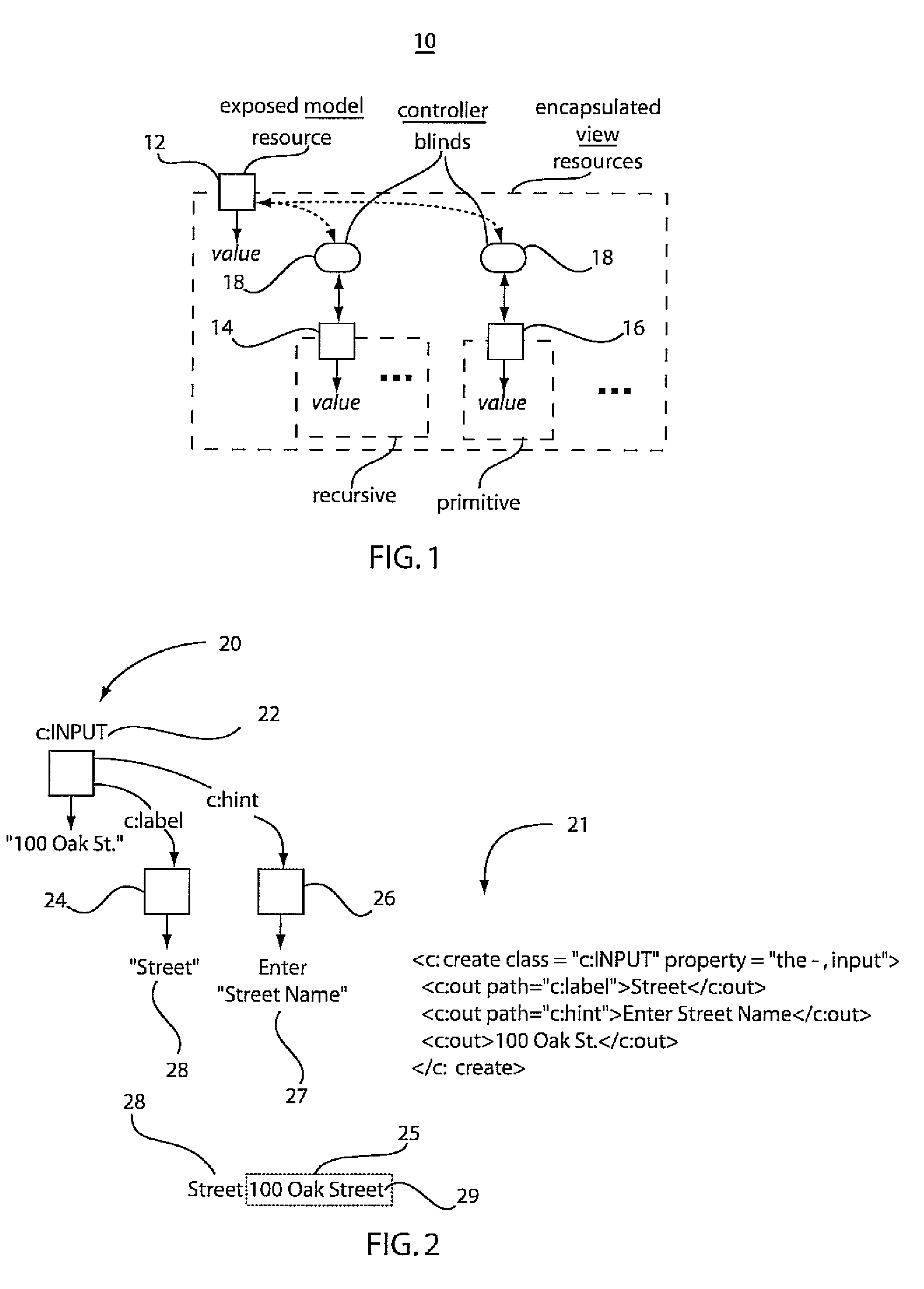
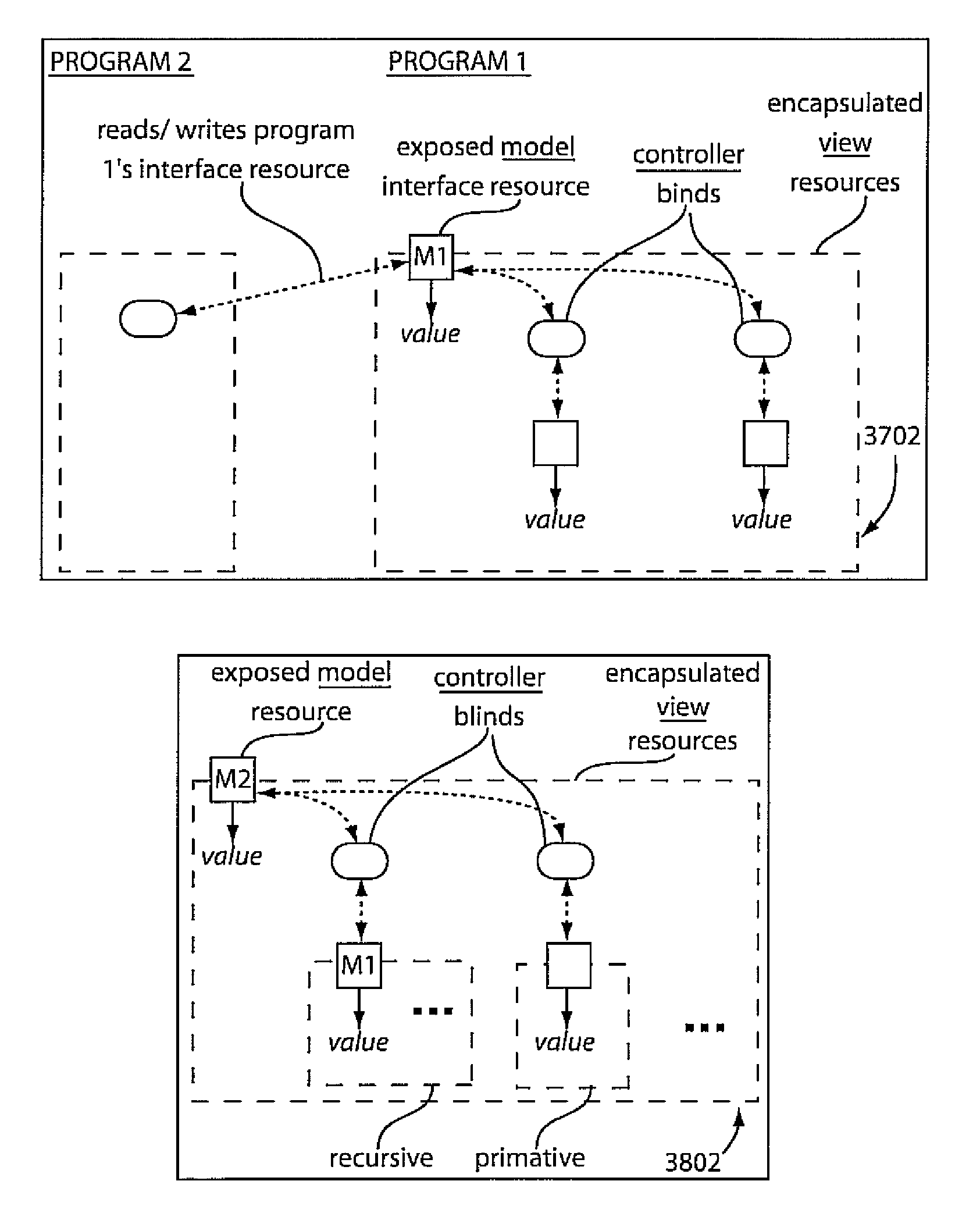
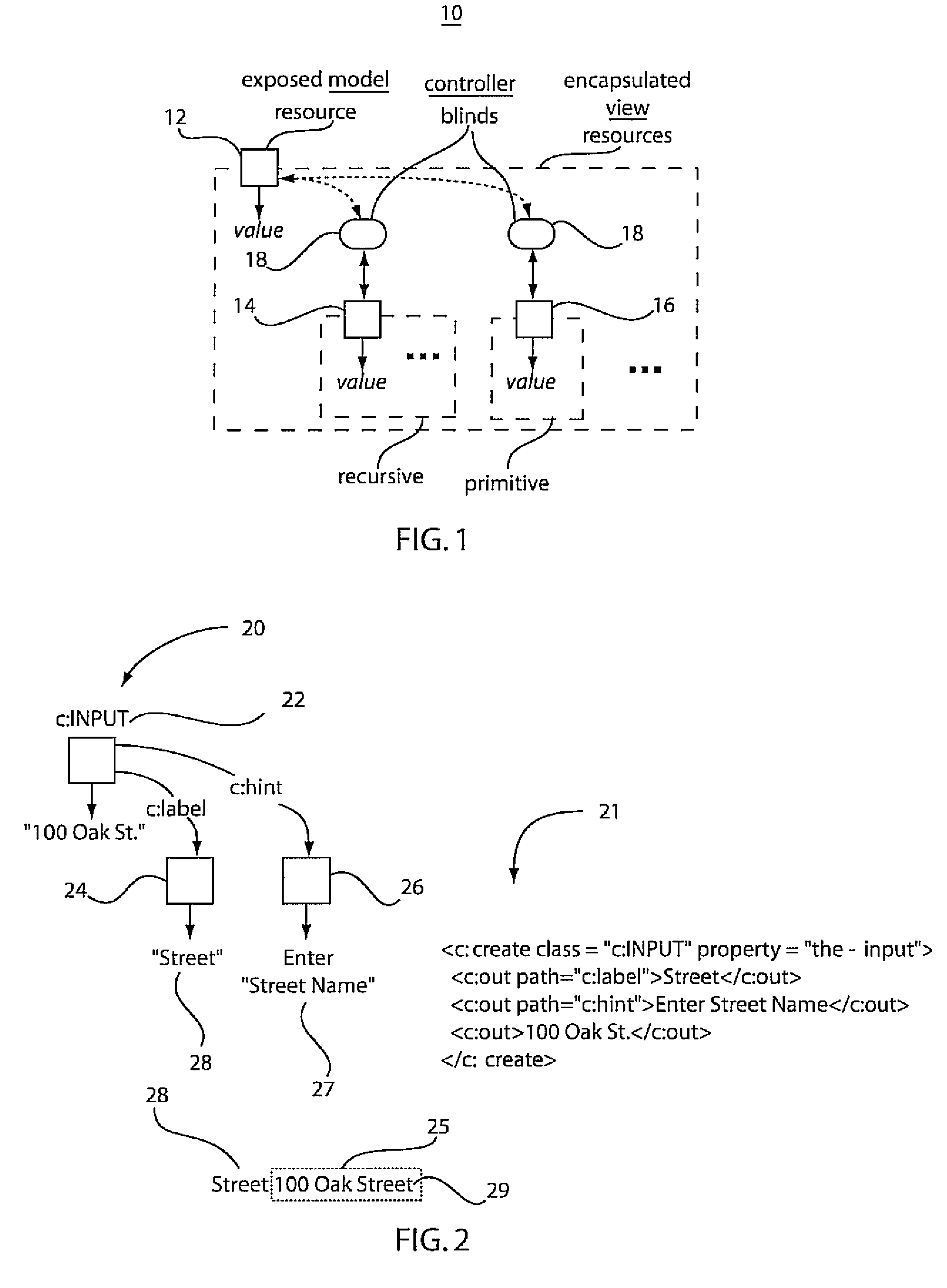
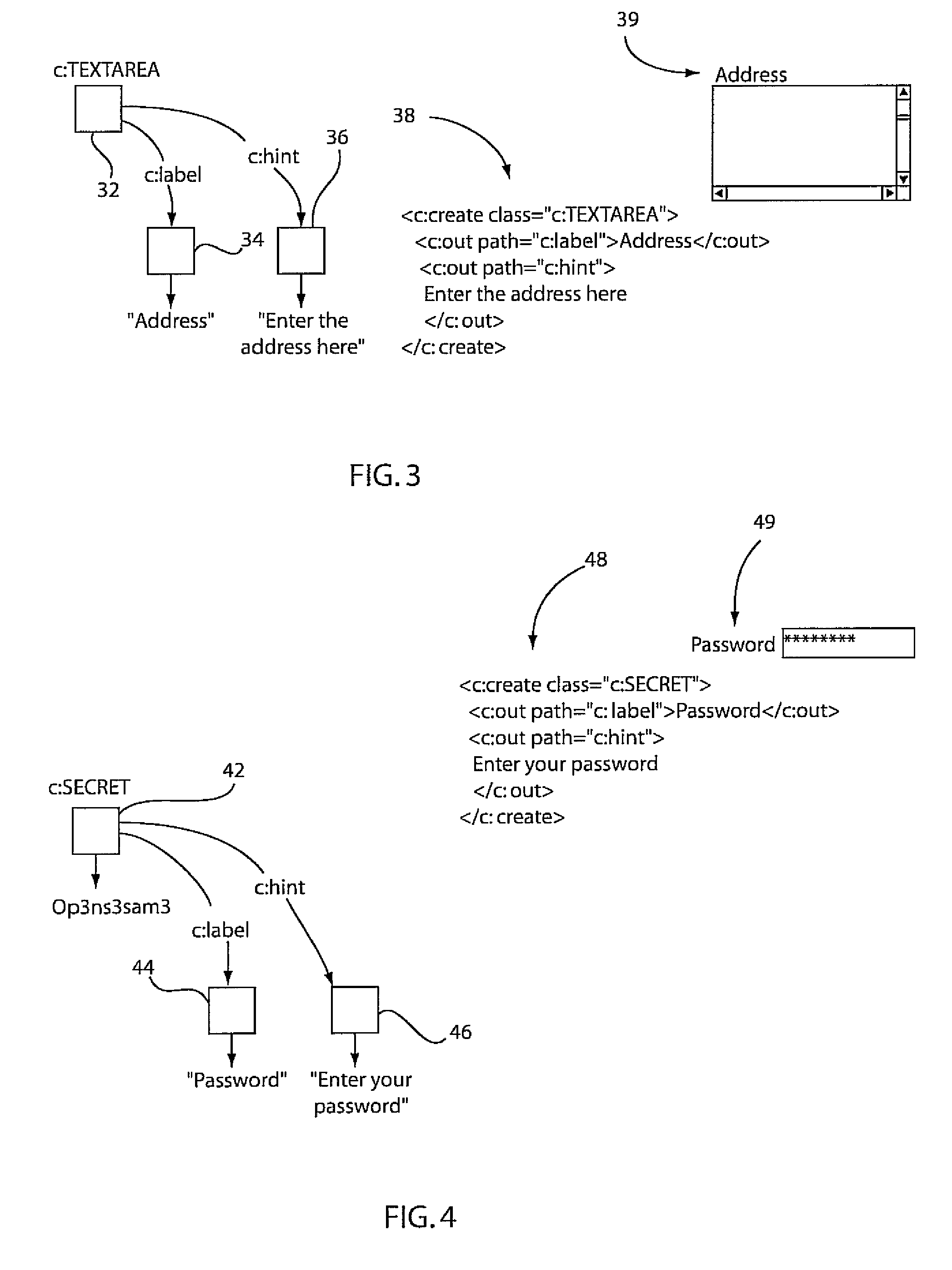
A system and method for reducing complexity by reuse of programming models includes defining a model controller view (MVC) unit as a programming model abstraction in a first program and permitting access by a second program to a model in the MVC unit. The first program and the second program communicate to employ the model in the second program. Access of the model by the second program is responded to in the first program to execute an action.
Owner:IBM CORP
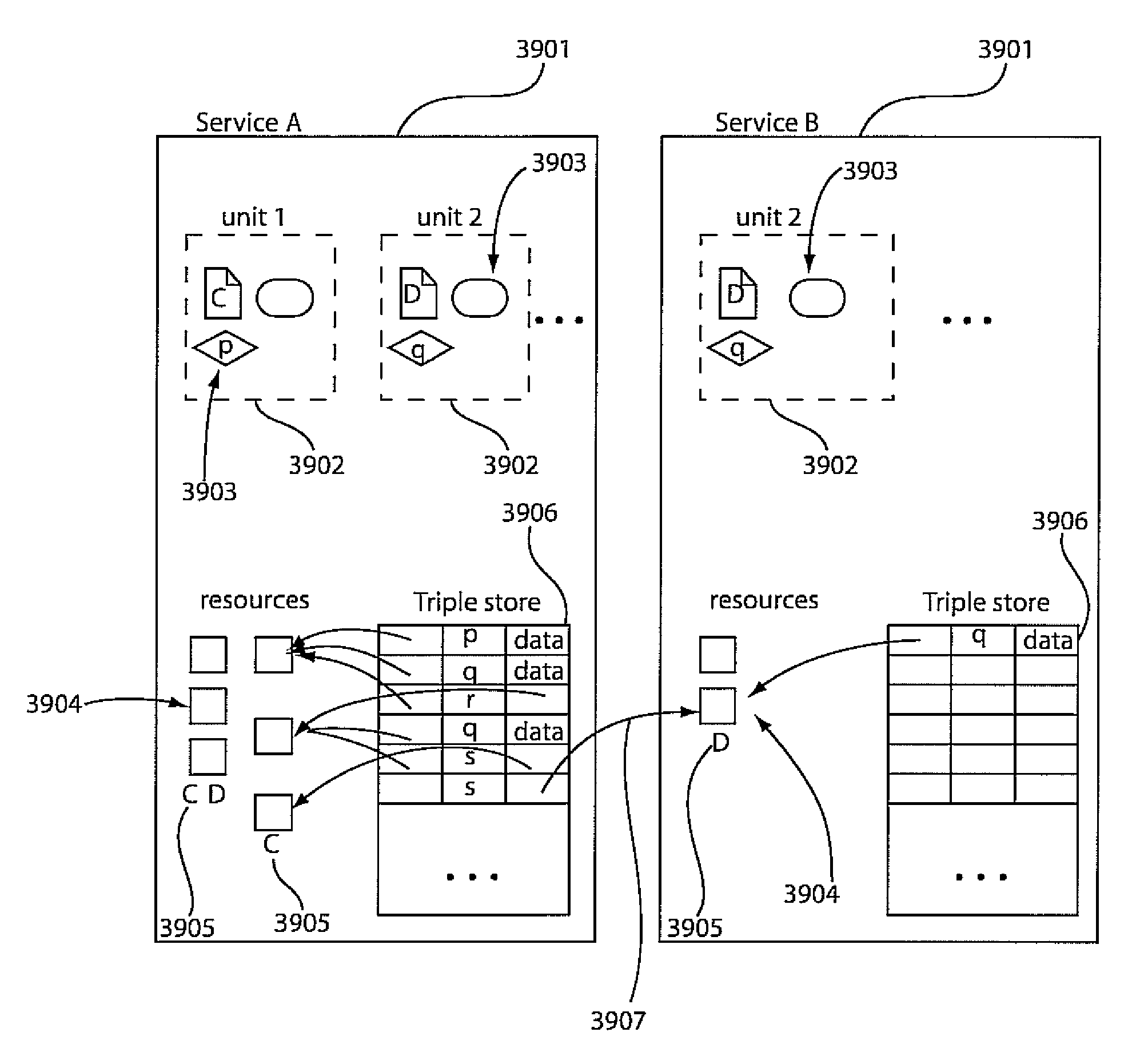
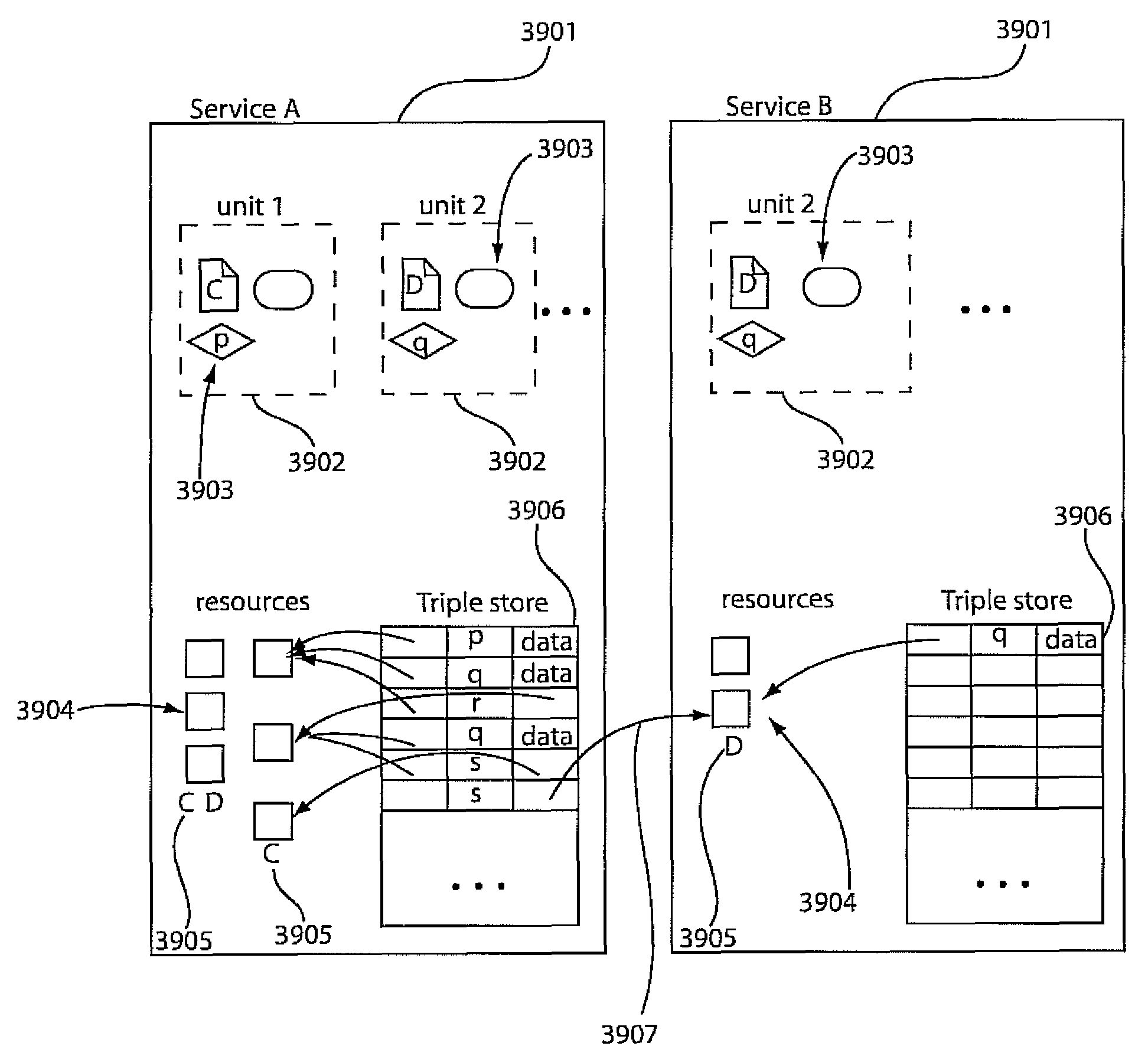
Distributed execution model for cross-organizational declarative web applications
ActiveUS20090276479A1Software engineeringMultiple digital computer combinationsCross organizationalApplication software
A system and method for distributed computation includes providing a first service of a first computation node in a network of nodes, the first service having a first resource, the first resource including one of references to data and other resources. In a second service on a second computation node, the first resource is reference-able by associating the first resource in the second service for use in the second service. A distributed computation is performed across node boundaries using the references of the first resource to perform the computation in the first service and in the second service.
Owner:IBM CORP
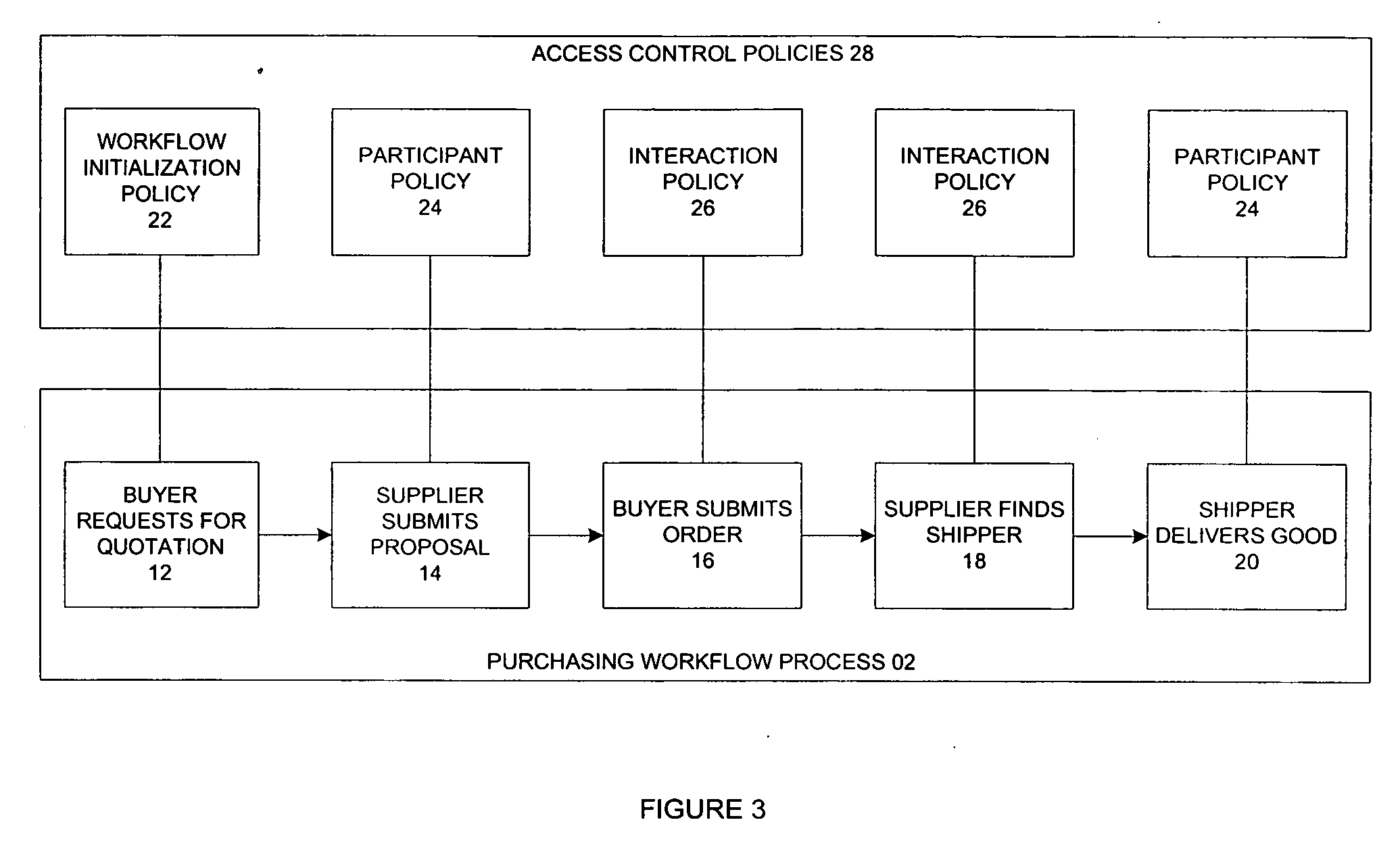
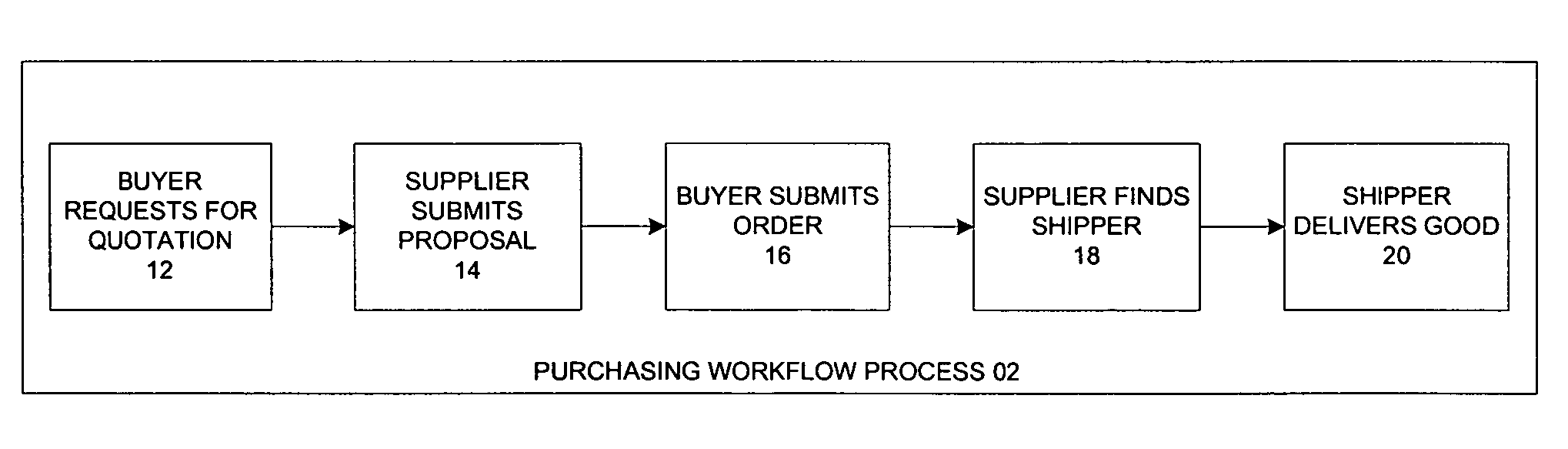
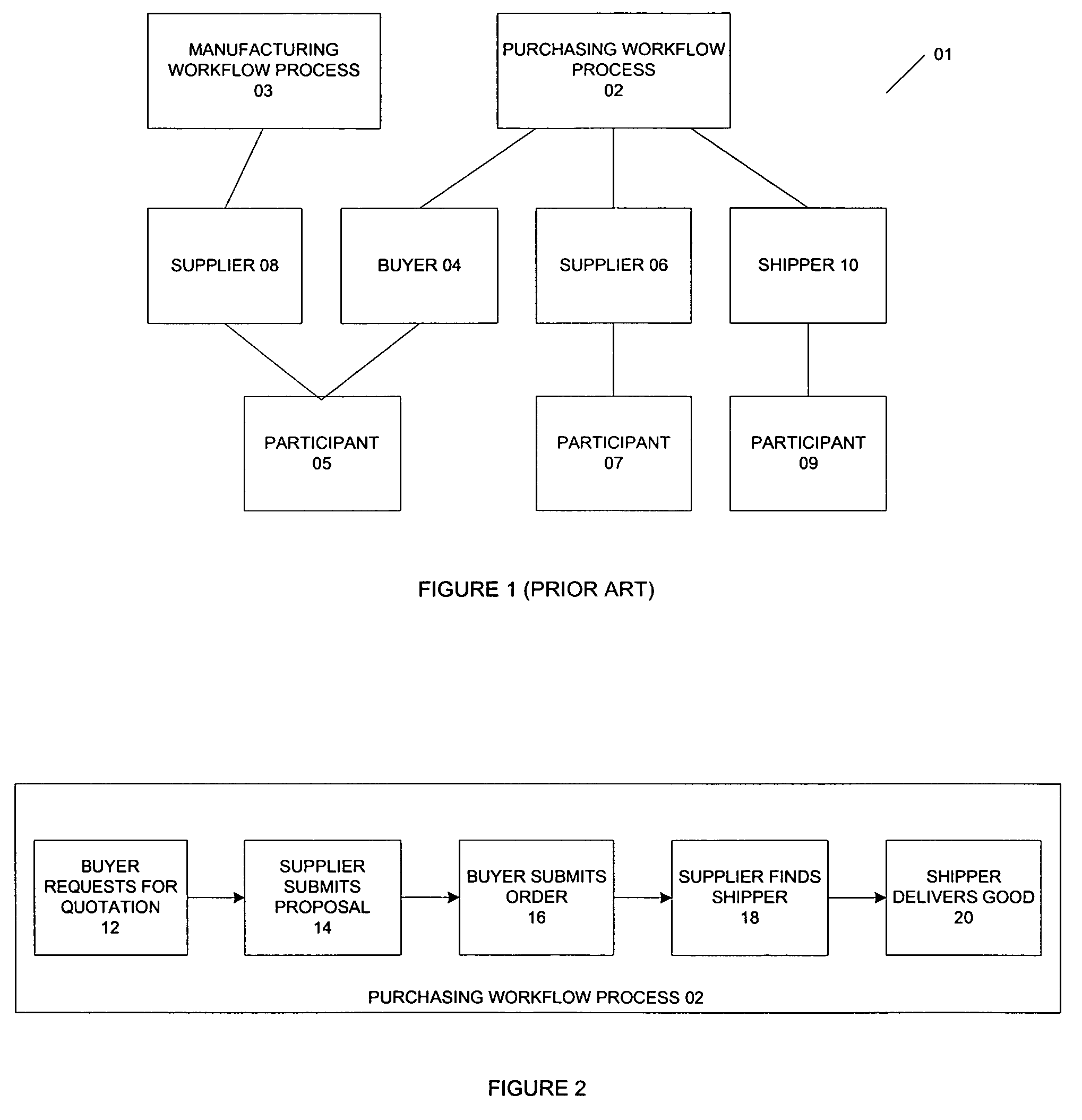
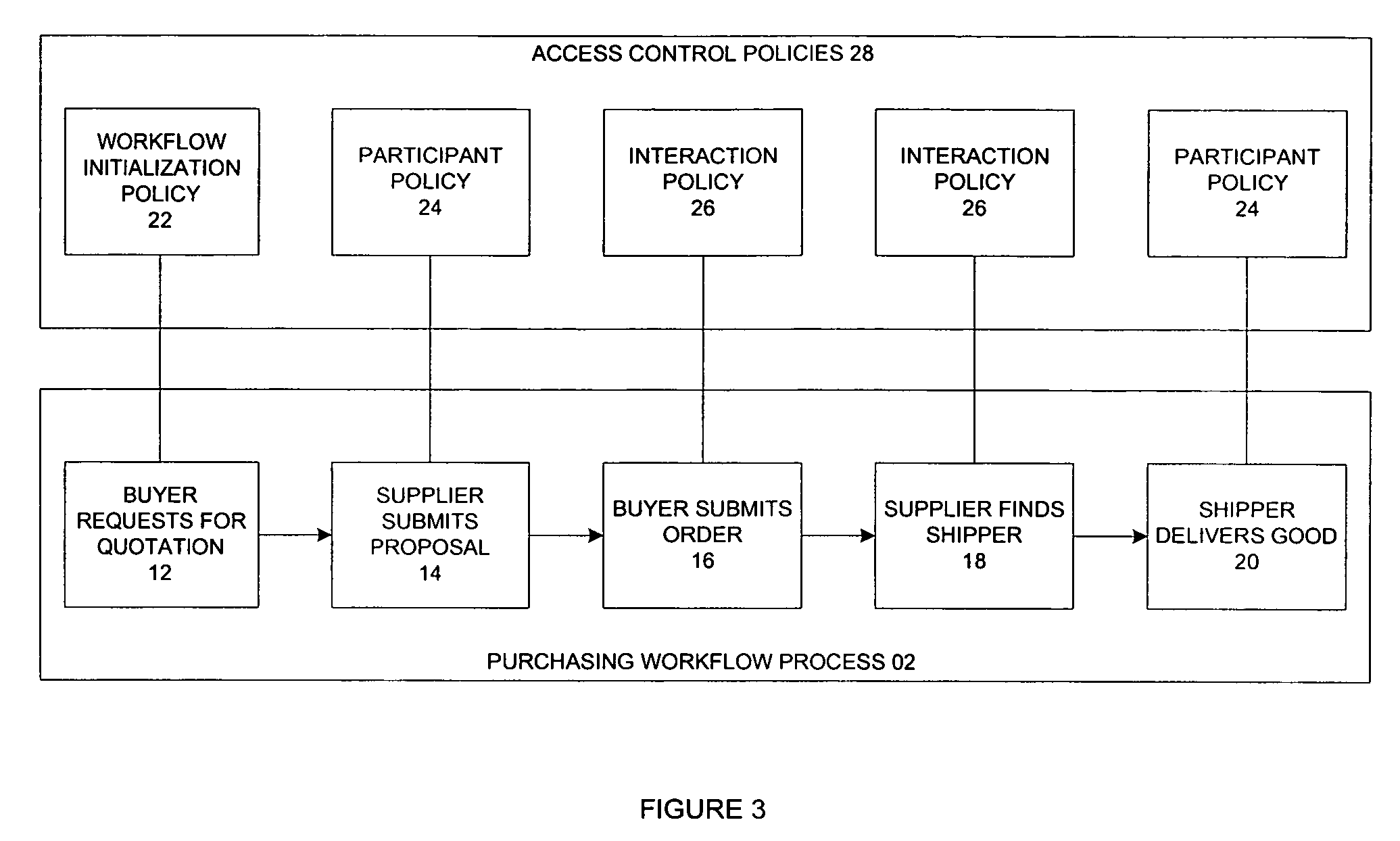
Automated generation of access control policies in cross-organizational workflow
ActiveUS20060253314A1Digital computer detailsOffice automationPolicy decisionActivity classification
A method and system to control an interaction of a plurality of participants in a workflow process. The method classifies the plurality of activities as (1) first activity of the workflow process, (2) first activity of a participant in an on-going workflow process, and (3) interaction activity. A set of access control policies is generated for each type of activity. The policies include workflow initialization policy, participation policy and interaction policies. The policies determine if a requesting participant is permitted to interact with a responding participant. In addition, the system includes a policy enforcement point for receiving a request from a requesting participant, wherein the request is for activating an activity of a responding participant. The policy enforcement point forwards the request to a policy decision point where the request is evaluated based on the set of access control policies.
Owner:SAP AG
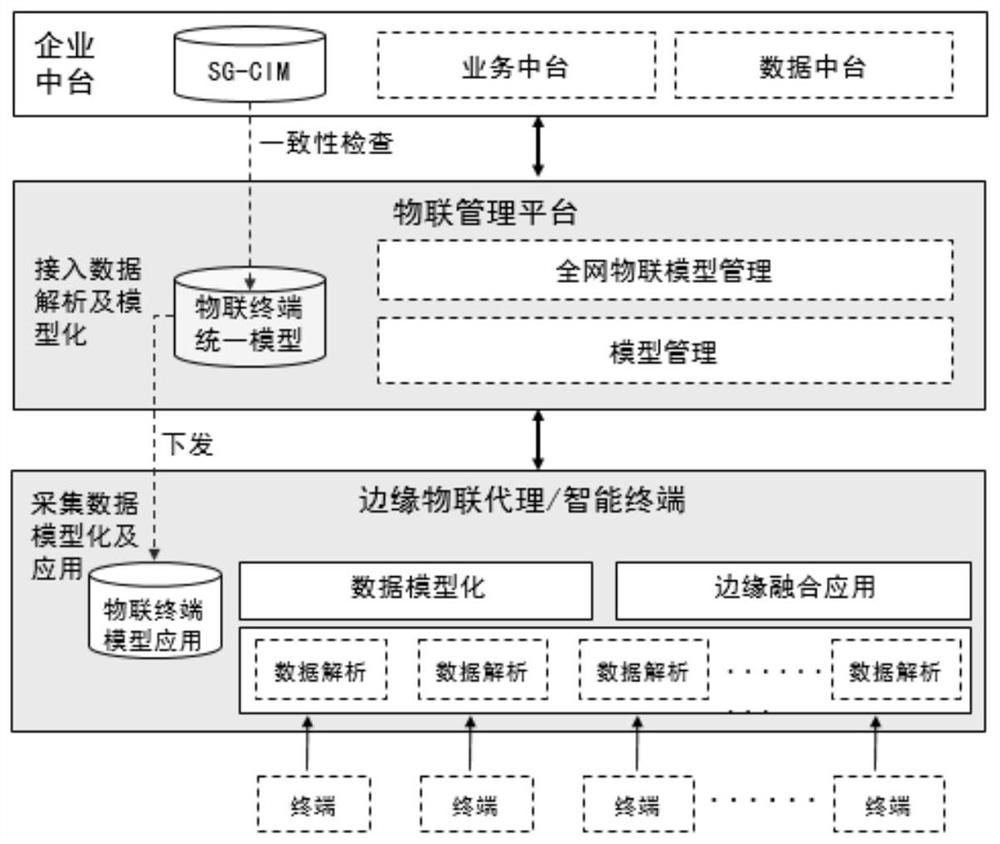
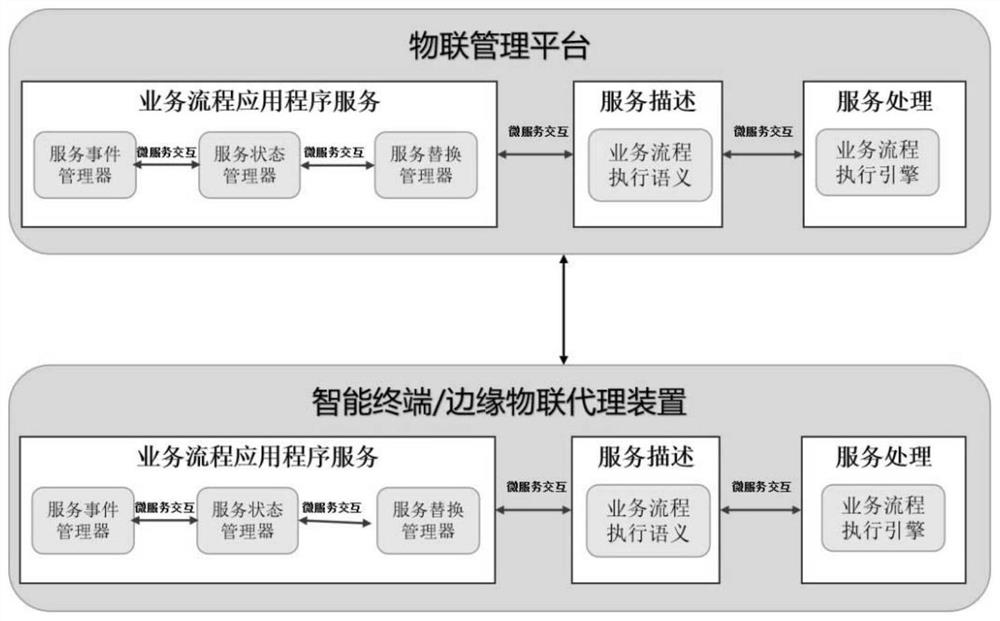
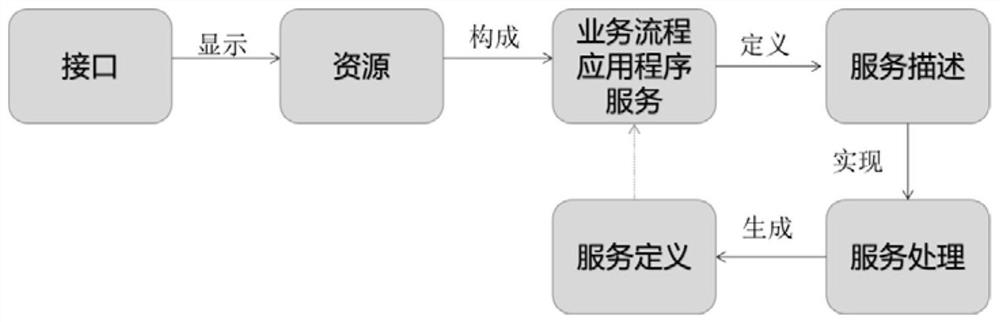
Event-driven message interaction method of electric power internet of things
The invention discloses an event-driven message interaction method of an electric power internet of things. The method comprises the following steps: firstly, modeling a cross-organization or cross-department collaborative service process in an Internet of Things management platform and an edge Internet of Things agent / intelligent terminal of the electric power Internet of Things; then defining execution semantics of the service process resource model, then proposing an analysis mechanism of a process execution engine to the service model, and finally realizing message interaction in the micro-service system architecture, thereby realizing message interaction. According to the invention, the problem of direct mapping and interaction between large-scale distributed sensors, power intelligent terminals and service data streams can be effectively solved.
Owner:STATE GRID SHANXI ELECTRIC POWER +3
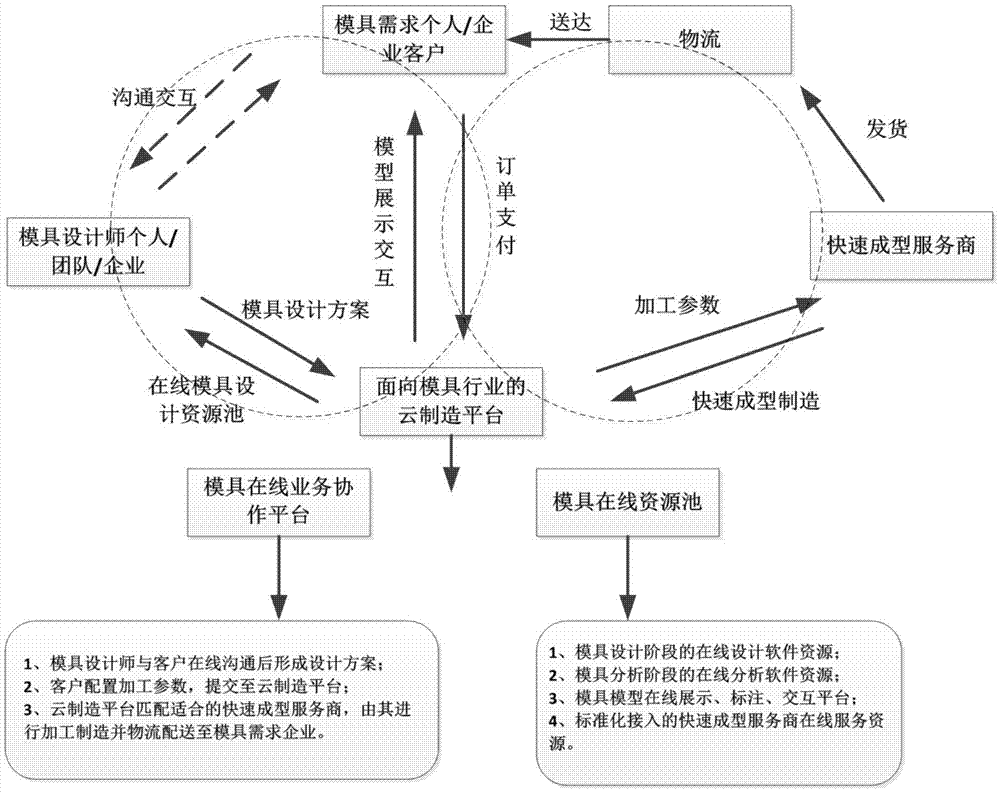
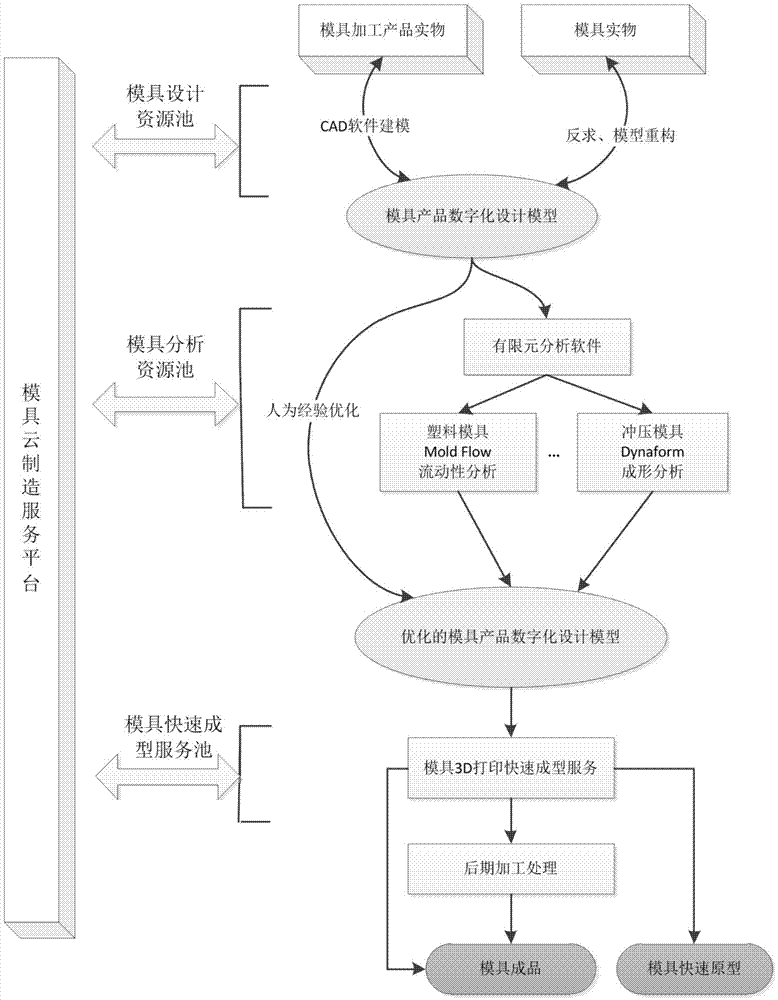
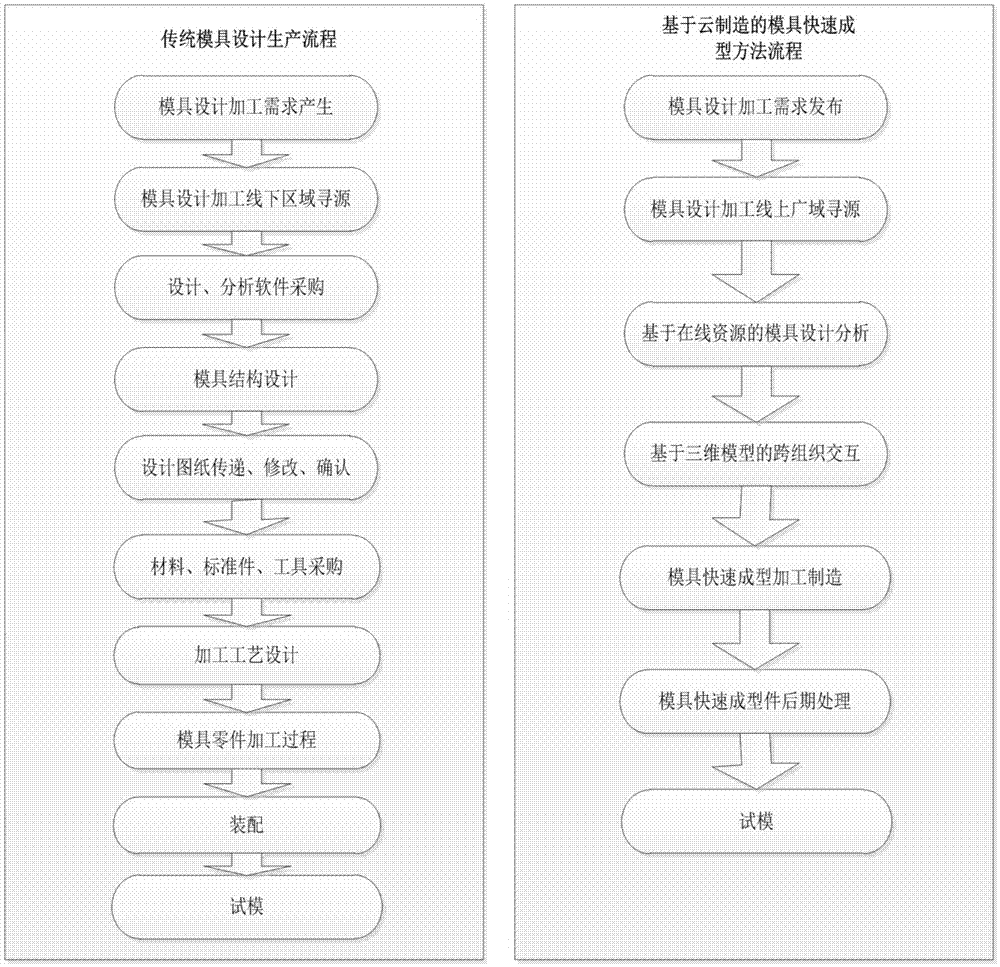
Mold rapid molding method based on cloud manufacturing
InactiveCN107016138AImprove machining accuracyImprove abilitiesGeometric CADAdditive manufacturing apparatusDesign teamInter organizational
The invention discloses a mold rapid molding method based on cloud manufacturing. Steps of the method comprises: S1, based on a mold cloud manufacturing service platform, establishing online requirement interaction of mold demand sides, mold design teams / enterprises, mold rapid molding service providers, determining a mold model design scheme corresponding to the mold demand sides; S2, based on the mold cloud manufacturing service platform, performing online design analysis on the molds of the demand sides, to obtain a model file of the mold design scheme; S3, using inter-organizational interactive iteration of a three-dimensional model to repeatedly modify and improve the model file of the mold design scheme, submitting a final version model file of the mold design scheme to the mold demand side; S4, based on the mold cloud manufacturing service platform, converting the model files in different formats, to obtain model files in a standard STL format; S5, based on communication of the mold demand sides and the mold rapid molding service providers, using the model files in a standard STL format to manufacture molds.
Owner:BEIJING SIMULATION CENT
Distributed execution model for cross-organizational declarative web applications
ActiveUS7836119B2Software engineeringMultiple digital computer combinationsWeb applicationApplication software
Owner:INT BUSINESS MASCH CORP
Cross-organization workflow operation method and system based on block chain
ActiveCN112465448APrevent integrationClear responsibilitiesDatabase distribution/replicationDigital data protectionWorkflow engineOperating system
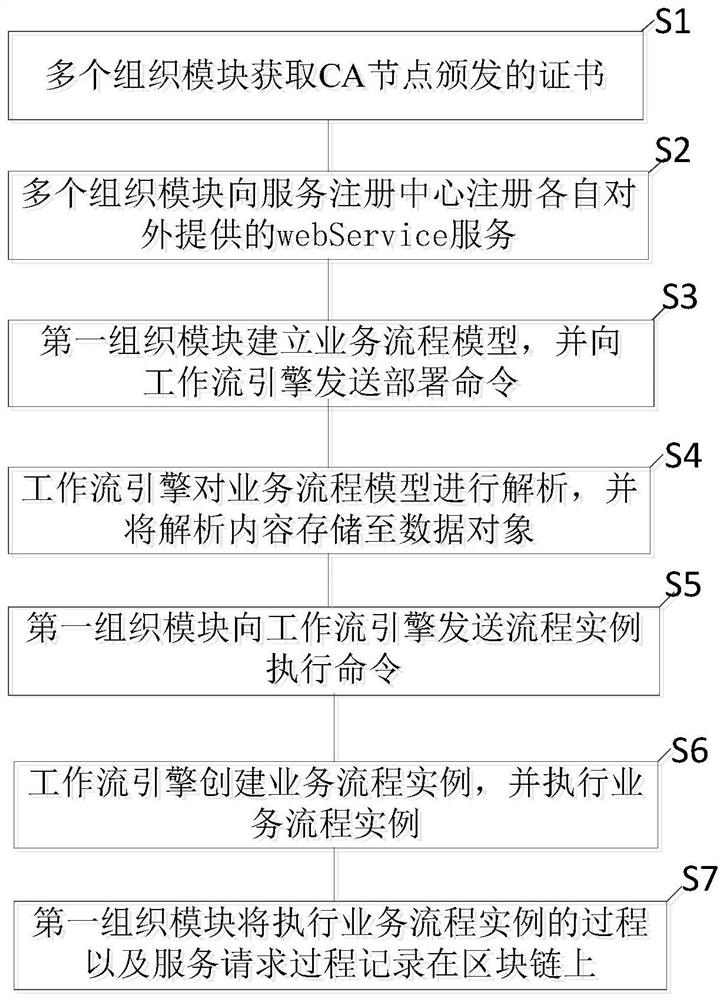
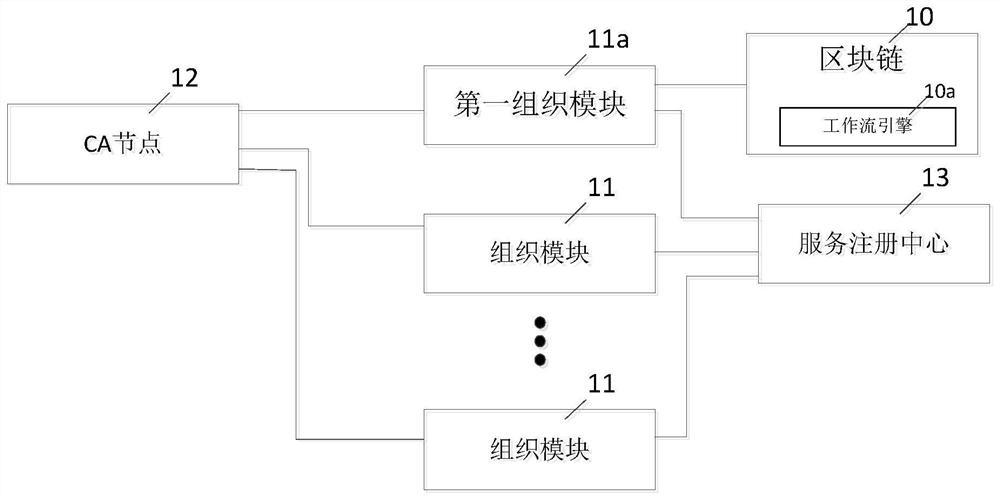
The invention discloses a cross-organization workflow operation method and system based on a block chain. The method comprises the steps that a plurality of organization modules obtain certificates issued by CA nodes; the plurality of organization modules register webService services respectively provided for the outside to the service registration center; the first organization module establishesa business process model and sends a deployment command to the workflow engine; the business process model is parsed by the workflow engine, and thus storing the analyzed content to the data object;the first organization module sends a process instance execution command to the workflow engine; and the workflow engine creates a business process instance and executes the business process instance,and the first organization module records a process of executing the business process instance and a service request process on the blockchain. According to the invention, the data coupling degree ofthe cross-organization service system can be reduced, the data integration cost is reduced, and the multi-party trust problem of the cross-organization service process is solved.
Owner:RENMIN UNIVERSITY OF CHINA
Workflow engine for mobile internet
The invention discloses a workflow engine for a mobile internet. Files, pictures and data are transmitted in sequence through the workflow technology, automation of the office approval process is achieved, and the office efficiency of workers is improved. Besides, a graphical operation interface oriented to the user mobile terminal is researched and developed, so that the user can directly design the flow conveniently, the engine is decoupled from the service analysis, and the intervention of information management personnel on the service flow is reduced. And a WeChat applet is introduced to realize the support of the system on the mobile Internet, so that a user can directly operate the process on the mobile terminal. In order to deal with the server access pressure under the application background of the mobile internet, the system is constructed in an asynchronous non-blocking system construction mode. The organization architecture of a user is investigated and researched, modeling is carried out on the organization architecture, and cross-organization and cross-function application support is achieved.
Owner:江苏元图信息技术有限公司
Policy enforcement and access control for distributed networked services
ActiveUS7904504B2User identity/authority verificationMultiple digital computer combinationsDistributed objectData access control
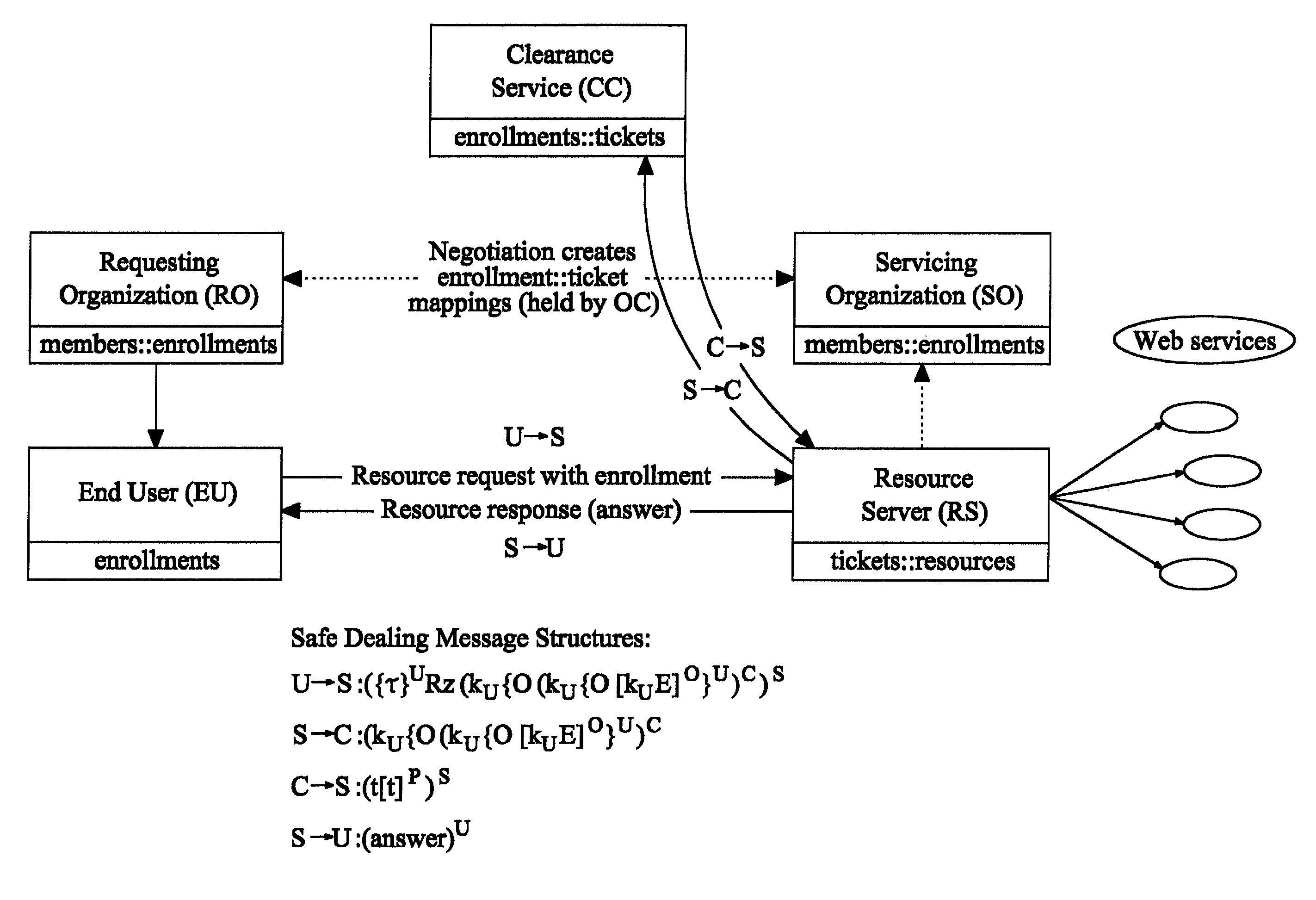
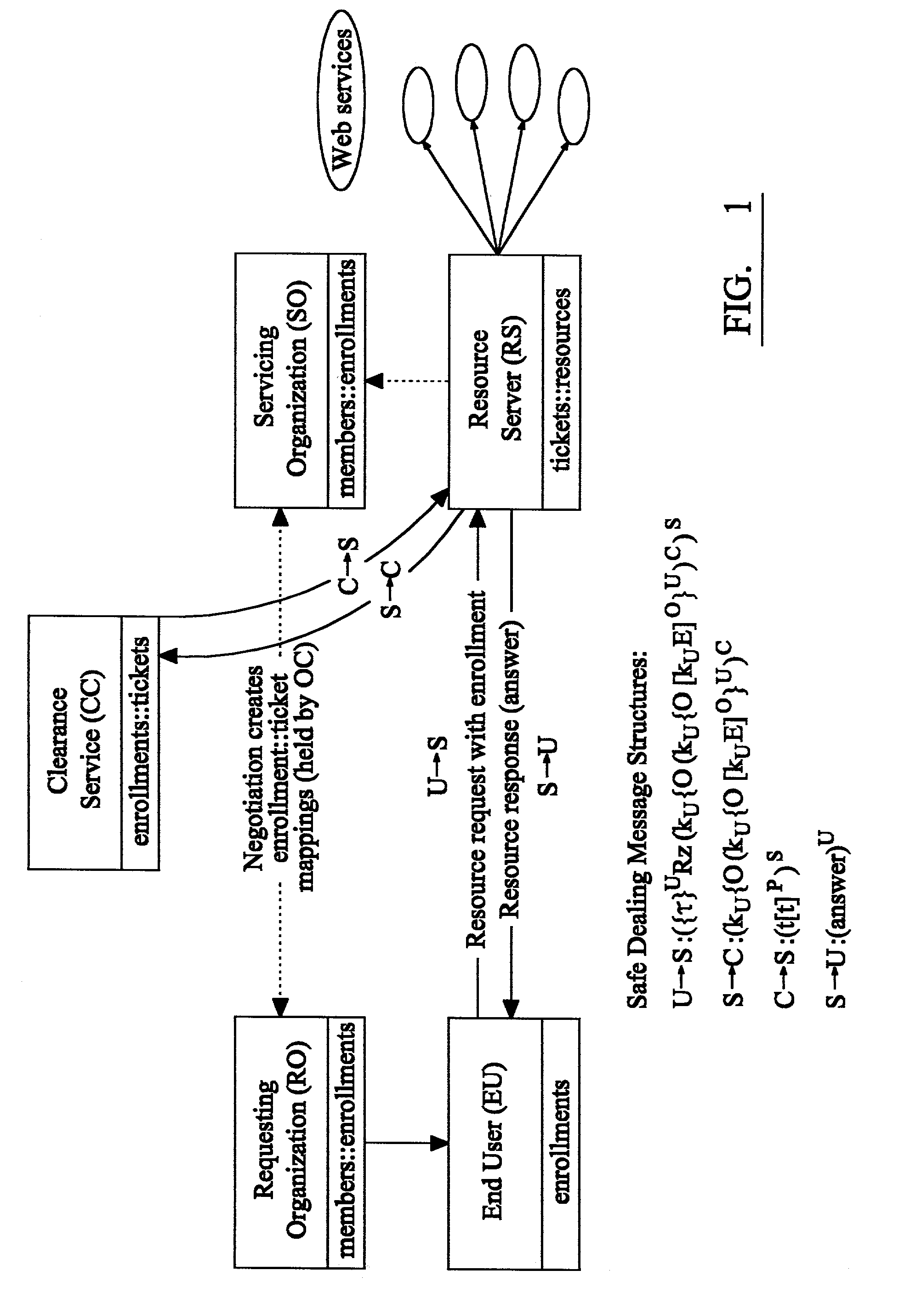
Apparatus for controlling cross-organizational access by end users associated with a plurality of organizations to one or more distributed object services available via a resource server across an information technology communications network. The apparatus comprises at least one Requesting Organization (RO) having access to services via the resource server, the Requesting Organization being adapted to issue enrollments to one or more end users upon request and electronically transmitting the enrollments to the respective end users. The apparatus further comprises at least one Servicing Organization (SO) communicating with the Requesting Organization and defining the credentials required for access to a service via the resource server by end users associated with each of the organizations. A Clearance Service (CS) is provided in which is stored one or more mappings of enrollments to credentials, the end user being adapted to transmit to the resource server a request for access to a resource together with data relating to their respective enrollment, in response to receipt of which request, the Requesting Organization is adapted to transmit the data relating to the enrollment to the Clearance Service which is adapted to map the enrollment to one or more respective credentials and return data representative of the credentials to the resource server which in turn is adapted to compare the data representative of the credentials to the original resource request and to comply (or otherwise) with the request. The Requesting Organization the resource server and the Clearance Service are all implemented as web or e-services.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Across-organization collaborative share system and method based on groups
InactiveCN108711112AImprove work efficiencyReduce operating costsData processing applicationsIntellectual propertyThe Internet
Owner:广州三德信息科技有限公司
Block chain business process management method and system driven by timed layout diagram
PendingCN114298529AResolve trust issuesReduce consumptionOffice automationResourcesLayoutSmart contract
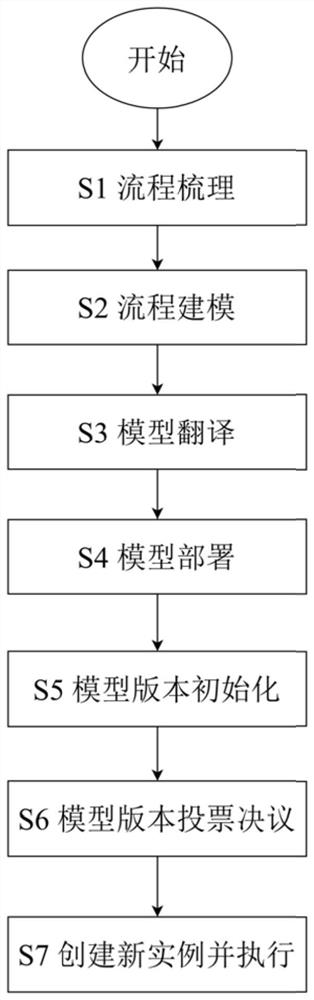
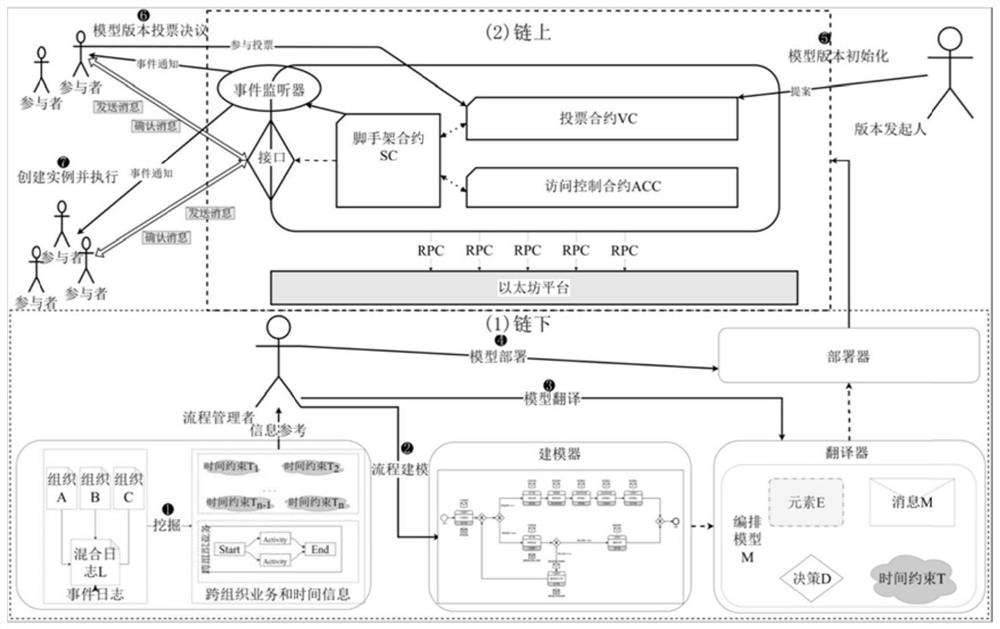
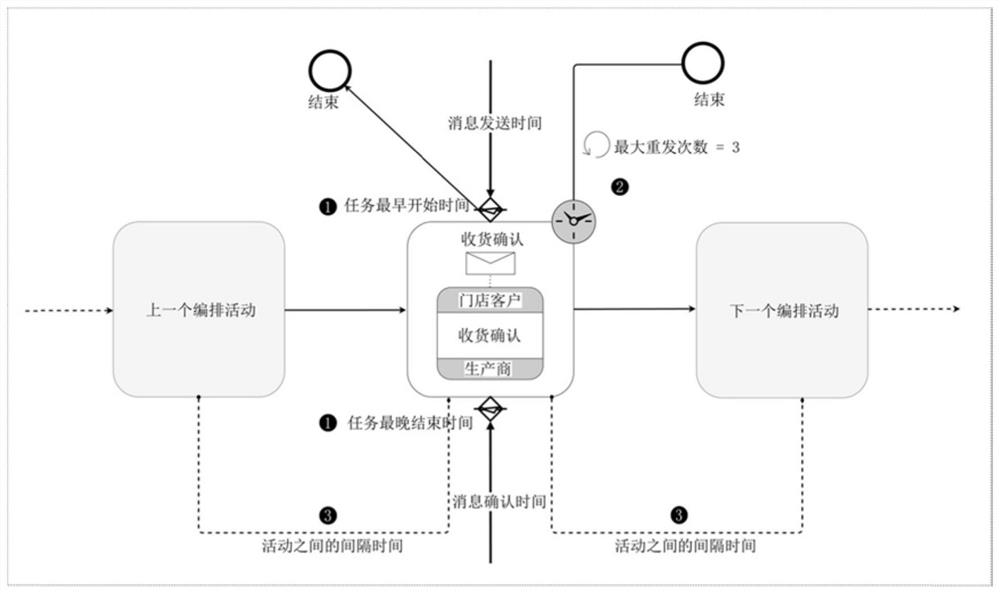
The invention discloses a blockchain business process management method and system driven by a timed layout diagram. According to the method, three types of time constraints of a single duration constraint, an activity maximum duration constraint and an activity interval time constraint of a process activity are introduced, so that effective time management of an on-chain business process is realized. According to the method, an explanatory deployment mode based on the meta-model is adopted, the deployed smart contract can be arranged and reused by different process instances, and different from a one-to-one compilation method of instances and smart contracts during deployment, the method can greatly reduce the consumption of the block chain Gas. According to the method provided by the invention, the problem of trust missing caused by violation of time constraints in a cross-organization business process can be solved, a meta-model version control strategy based on a voting mechanism is integrated, and the method has the advantages of relatively high decentration degree and relatively easy version iteration.
Owner:HANGZHOU DIANZI UNIV
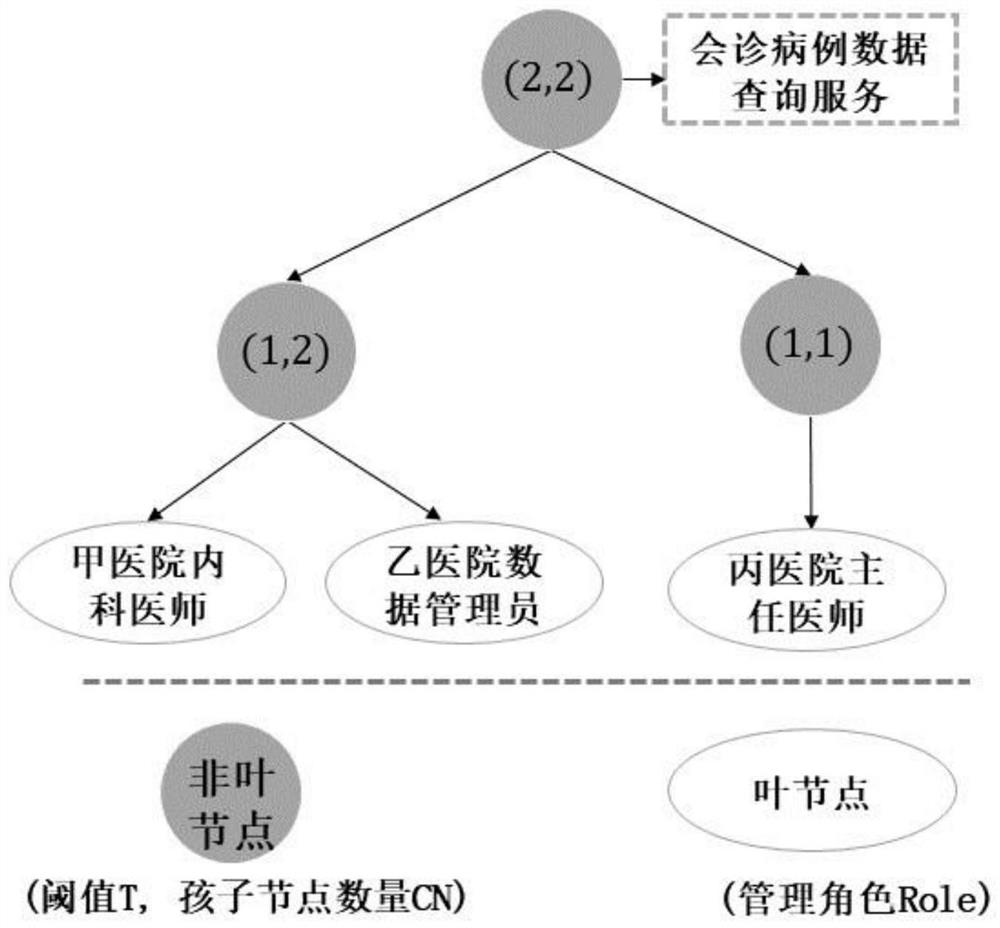
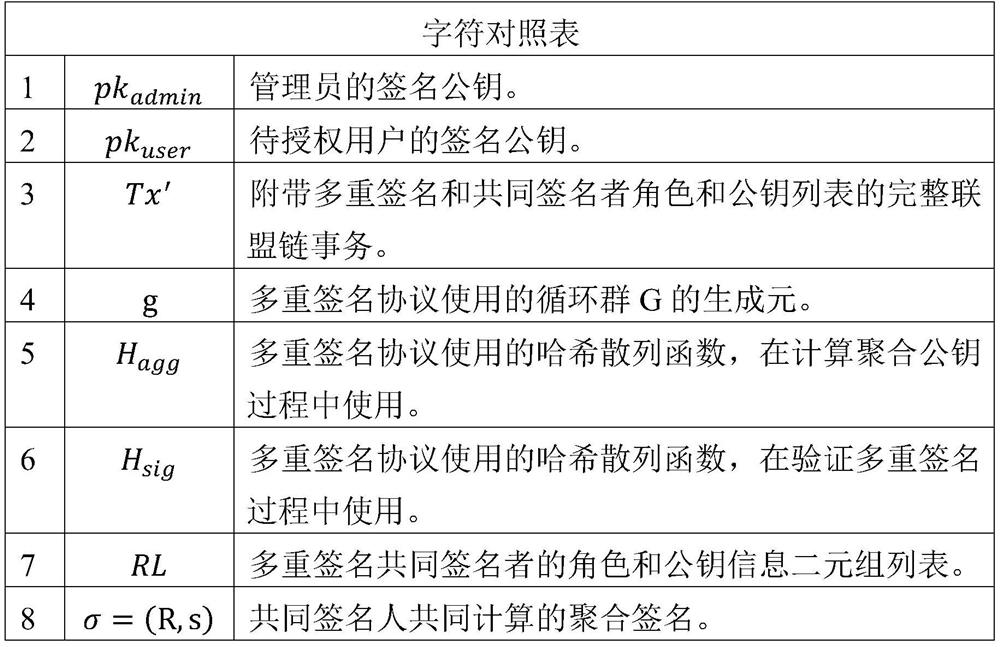
Cross-organization access control method based on alliance chain and multiple signatures
ActiveCN113660206APrevent malicious tamperingImprove securityUser identity/authority verificationDigital data protectionThird partyNode deployment
The invention relates to a cross-organization access control method based on an alliance chain and multiple signatures, and belongs to the technical field of block chains. According to the method, a non-centralized alliance chain technology is used as a trusted machine, distribution, updating and recovery of cross-organization access control authority are realized under the condition of no participation of a centralized third party, and authorization decision is carried out on a cross-organization access request based on an alliance chain intelligent contract. A single-point fault of the centralized node or malicious tampering of the access control authority can be effectively prevented. According to the method, participant nodes are added or removed based on an alliance chain admission mechanism, contract logic is deployed or updated, the method is effectively used for dynamic joining of participants and business logic change in a resource sharing system, and good expansibility is achieved. On the basis of a multi-signature technology, multi-party management control over the co-governance service is provided, and a group of role sets belonging to multiple organizations can jointly manage one co-governance service.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
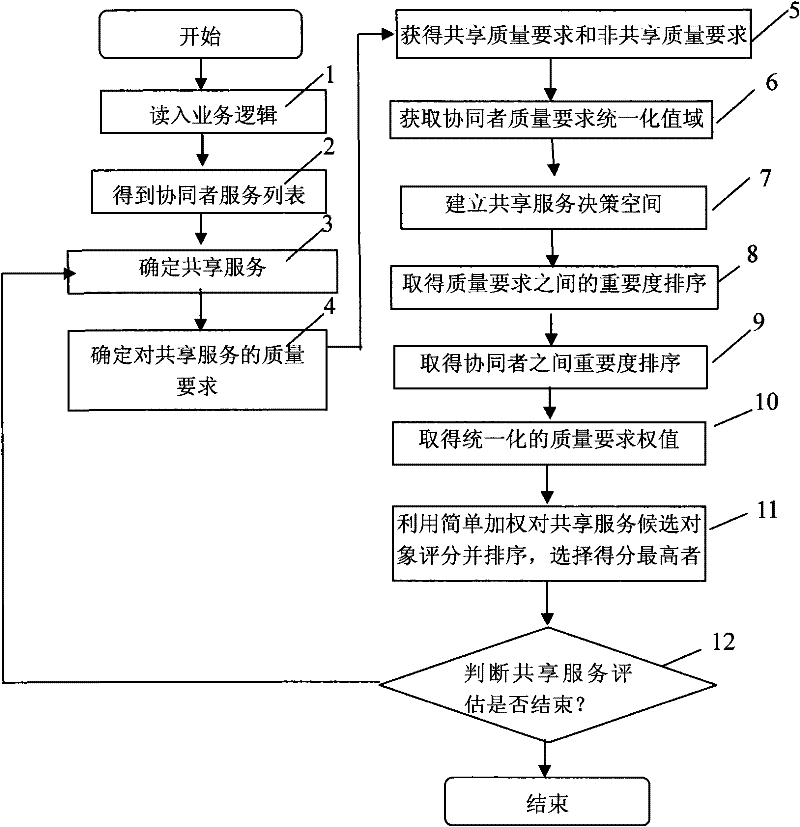
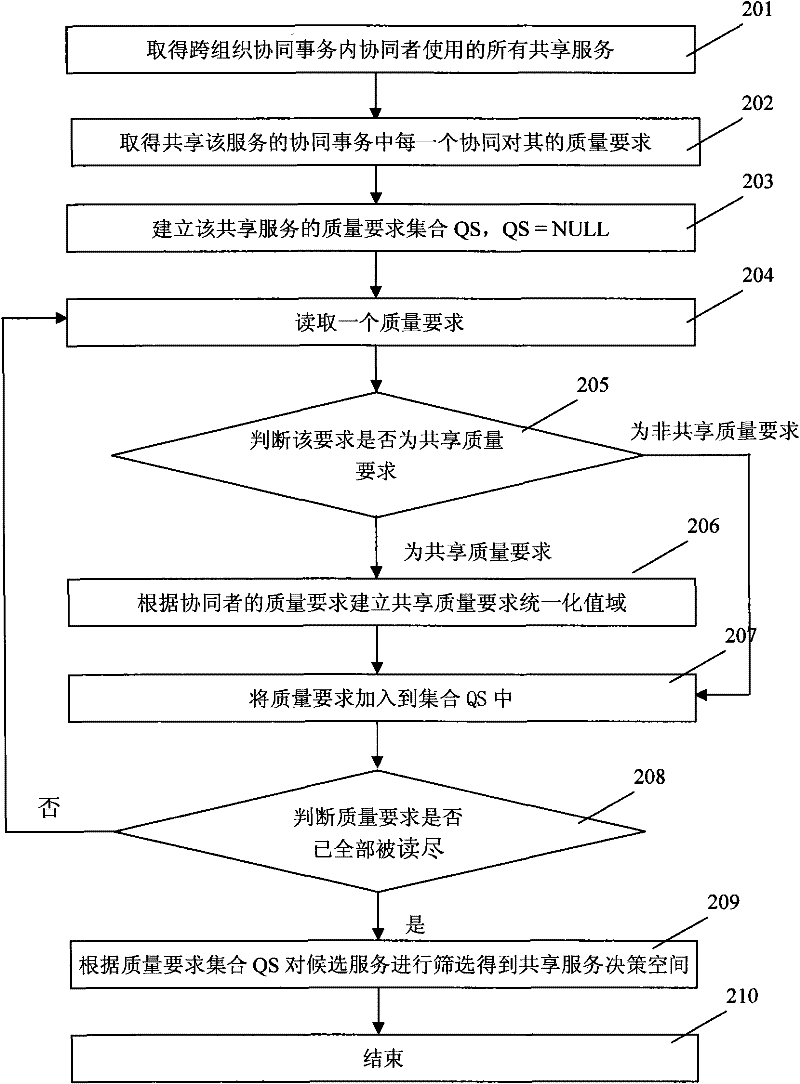
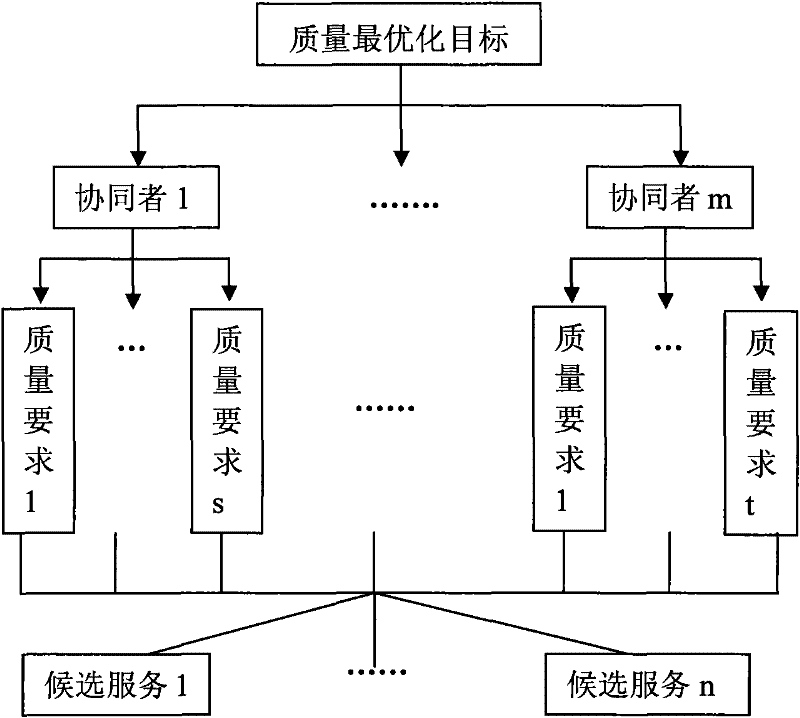
A service selection method supporting cross-organizational collaborative transactions
InactiveCN101567902BImprove objectivityImprove operational efficiencyTransmissionCommercePairwise comparison matrixService selection
The invention discloses a service selection method supporting cross-organization collaborative affairs, comprising the following steps: the main server CPU reads the information of each participant in this collaboration and stores it in a memory; obtains the information of each participant in this collaboration The list of services used in collaboration; analyze and obtain the shared services of the collaborative participants; determine the quality requirements of the collaborators for the shared services; construct the decision space for the candidate objects of the shared services; The weight of the quality requirement is transmitted to the master server; the quality requirement weight of each collaborator is normalized; the degree of satisfaction of each shared service candidate object in the decision space for the quality requirement of each collaborator is calculated; the master server selects the appropriate Serve. The invention starts from establishing the service description, and the whole selection process is automatically calculated by the computer, which improves the credibility and operating efficiency.
Owner:NANJING UNIV
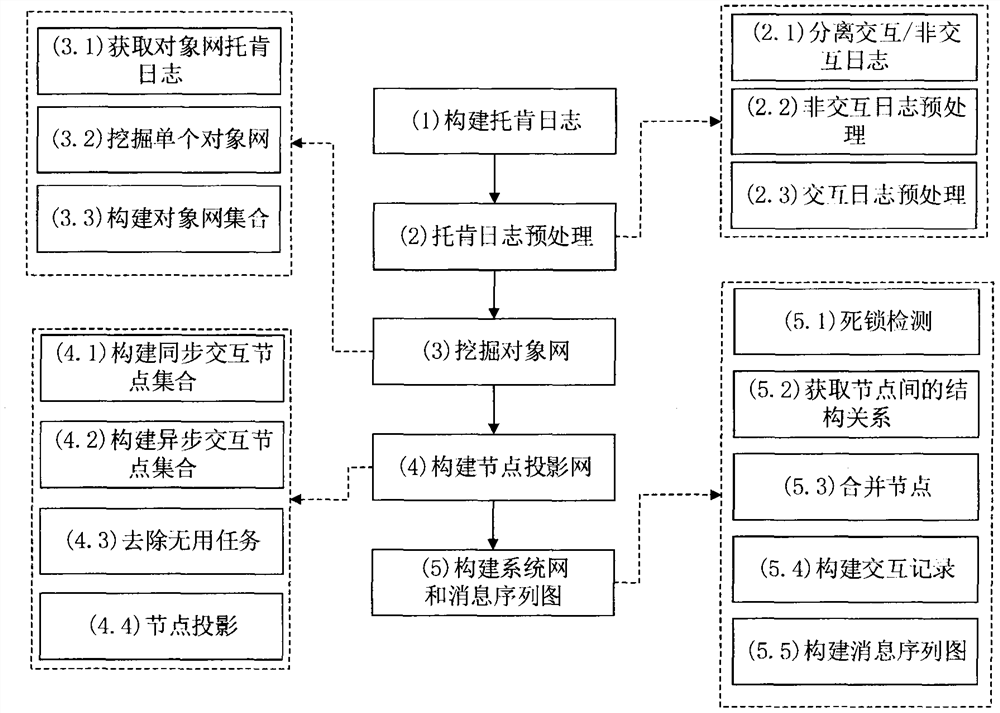
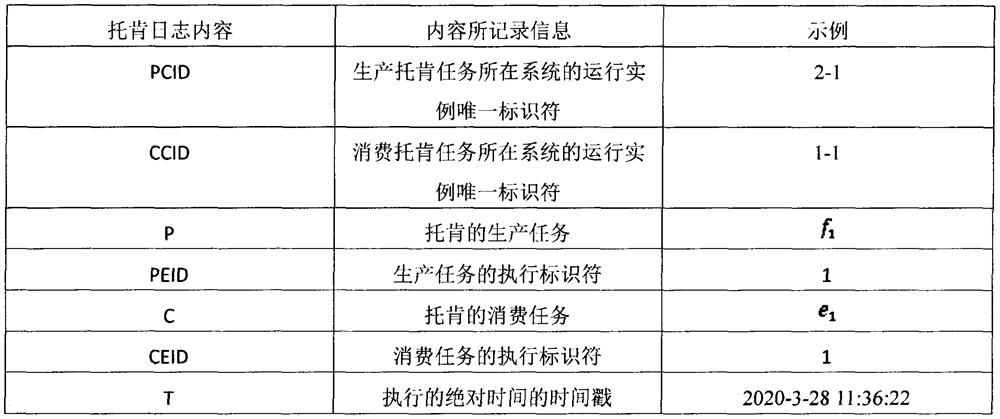
Modeling and constructing method for cross-organization business process interaction
PendingCN112435017AClear captureOffice automationSpecial data processing applicationsBusiness enterpriseModelSim
The invention relates to a modeling and construction method for cross-organization business process interaction. The method comprises the following steps: constructing a Token log according to actualbusiness process interaction; preprocessing the Token log; constructing an object network of a cross-organization business process based on the preprocessed non-interactive Token log; for an interactive Token log, constructing a node projection graph of an object network according to interactive nodes, and then constructing a system network and a message sequence graph of a cross-organization service process by utilizing a merging algorithm and interactive details. The method can help enterprises to dynamically change the models according to actual implementation conditions from the aspect ofactual models, including task change, execution sequence change and resource change, so as to achieve a common target.
Owner:NANJING UNIV
System and method for presentation of cross organizational applications
ActiveUS8839192B2Software designVisual/graphical programmingSoftware engineeringApplication software
A system and method for reducing complexity by reuse of programming models includes defining a model controller view (MVC) unit as a programming model abstraction in a first program and permitting access by a second program to a model in the MVC unit. The first program and the second program communicate to employ the model in the second program. Access of the model by the second program is responded to in the first program to execute an action.
Owner:INT BUSINESS MASCH CORP
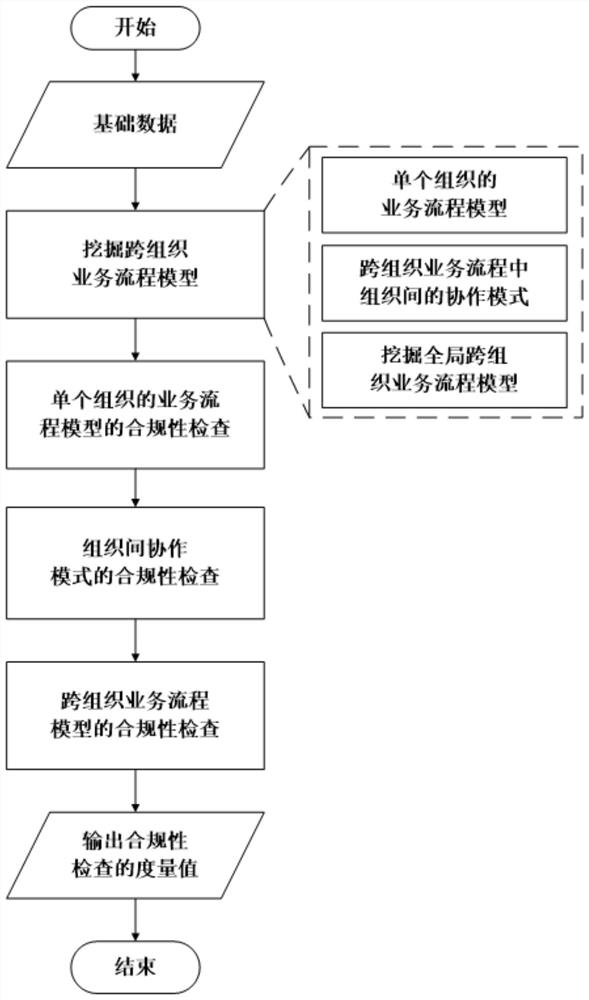
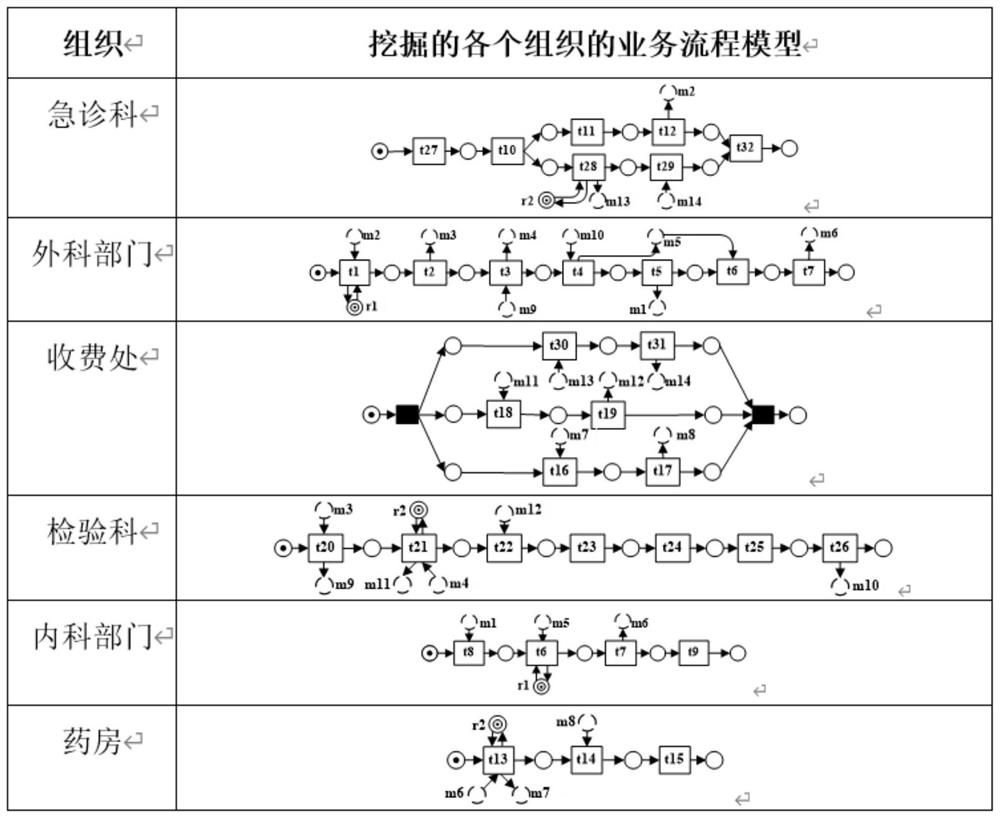
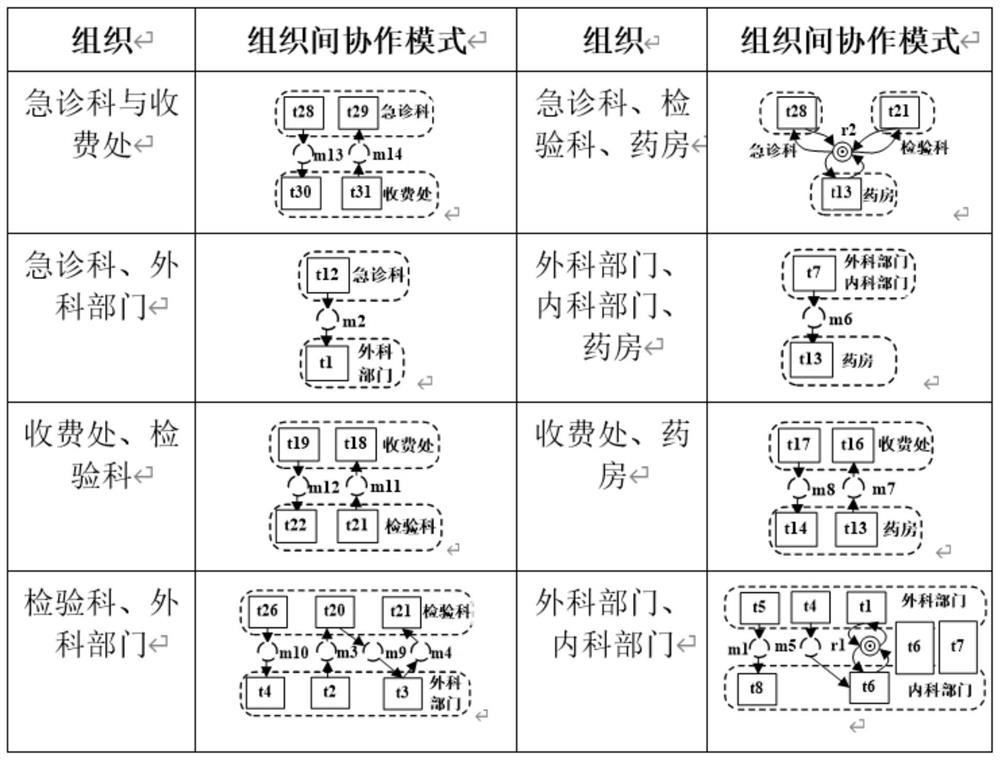
Cross-organization business process model mining and compliance checking method and system
PendingCN113780844ABreak through limitationsAccurate analysisDigital data information retrievalResourcesLog miningInter organizational
The invention discloses a cross-organization business process model mining and compliance checking method and system. The method comprises the following steps: 1) acquiring a cross-organization business process event log; 2) mining a business process model of each organization and a cooperation mode existing between any two organizations by using the obtained cross-organization business process event logs; 3) integrating the mined business process models of different organizations and cooperation modes between the organizations to obtain a global cross-organization business process model; 4) performing compliance check on the business process model of each organization and the cooperation mode between the organizations in the mined cross-organization business process event log; and 5) performing compliance check on the global cross-organization business process model and obtaining a conclusion. The cross-organization business process models in various scenes can be mined, and the problem that the mined cross-organization business process models cannot be effectively measured through an existing compliance checking method is solved.
Owner:北京杰成合力科技有限公司
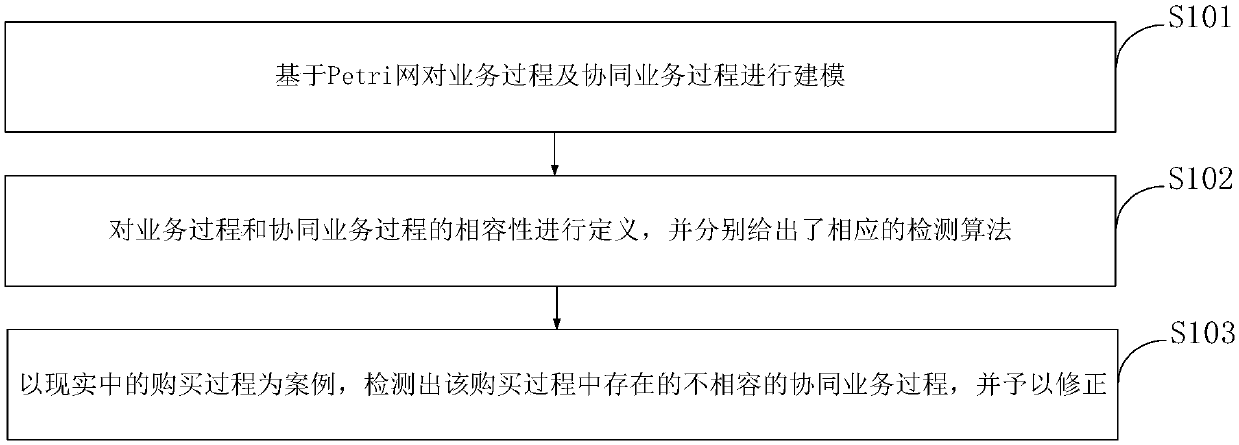
Compatibility detection and correction method of collaborative service process
InactiveCN107748983AImprove accuracySave manpower, material and financial resourcesOffice automationEnterprise servicesWork flow
The invention belongs to the enterprise service collaboration technology field and discloses a compatibility detection and correction method of a collaborative service process. The method is characterized by based on a cross-organizational work flow network, carrying out modeling on a service process and the collaborative service process respectively; providing corresponding detection algorithms for incompatibility conditions of the service process and the collaborative service process; and correcting the detected incompatible collaborative service process. A purchase process instance shows that the method can be used to correct the incompatible collaborative service process and a good collaborative service process model satisfying compatibility can be finally acquired. Under the conditionthat a local service process is not changed, the incompatible collaborative service process is corrected and the good collaborative service process model satisfying the compatibility can be finally acquired.
Owner:YUNNAN UNIV
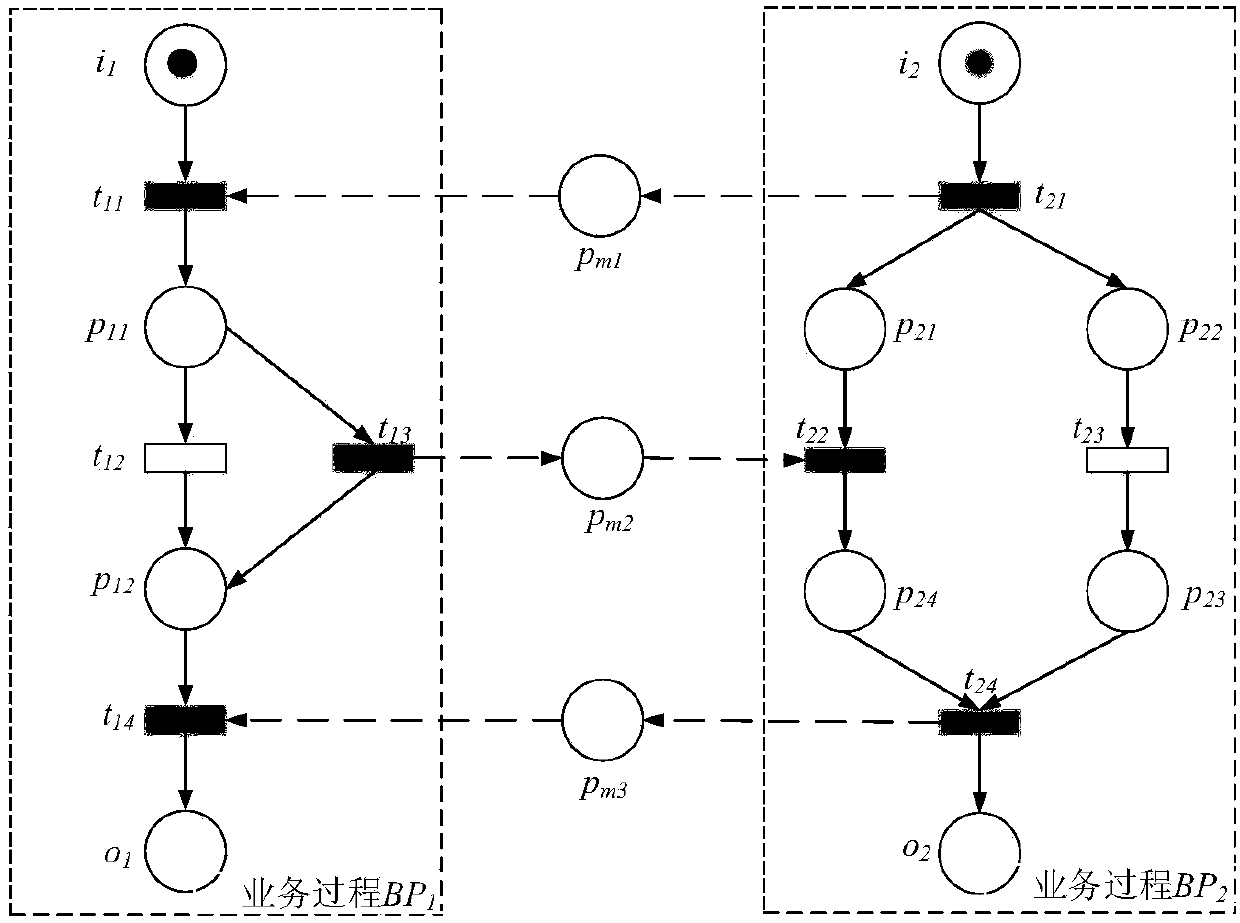
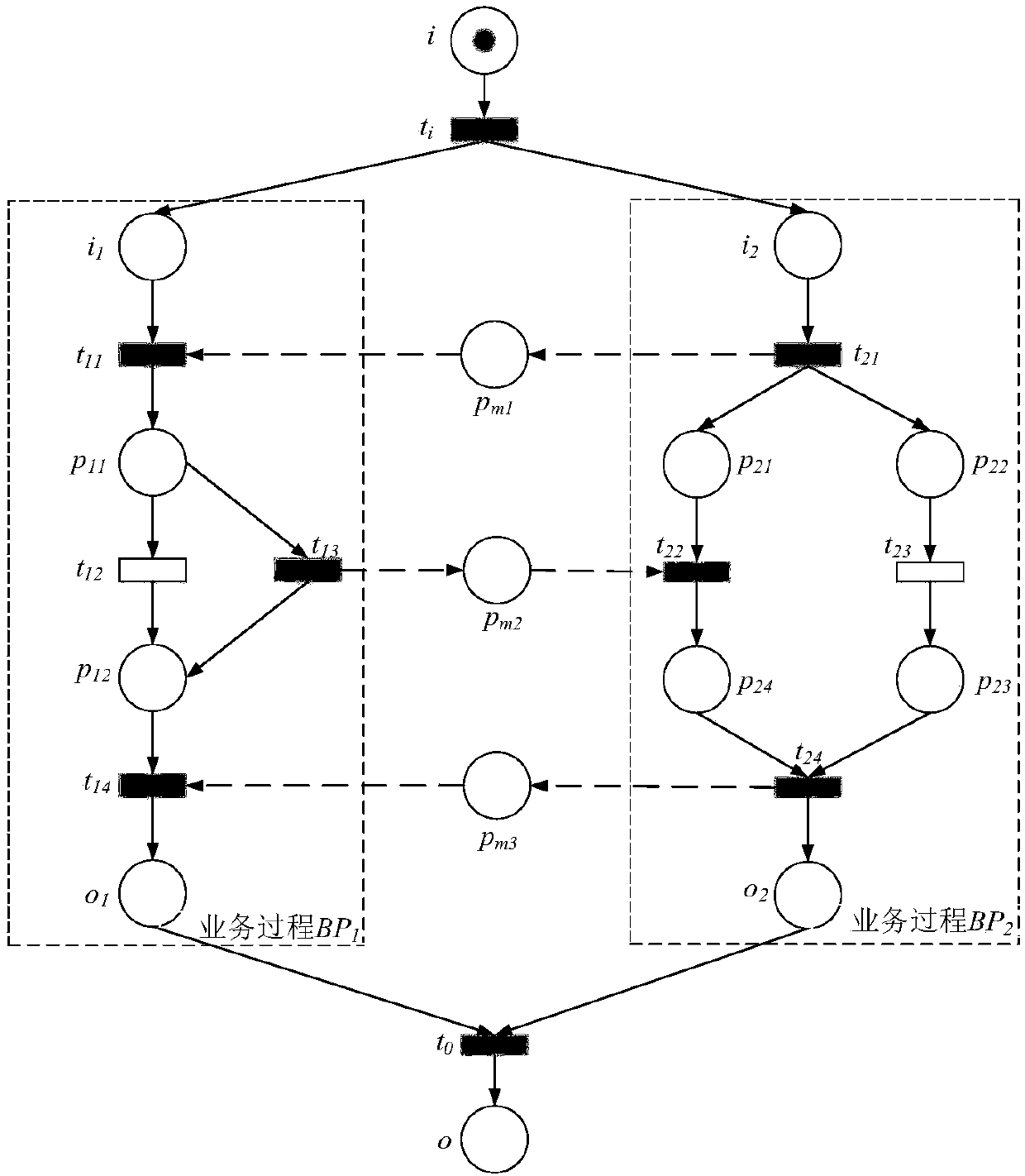
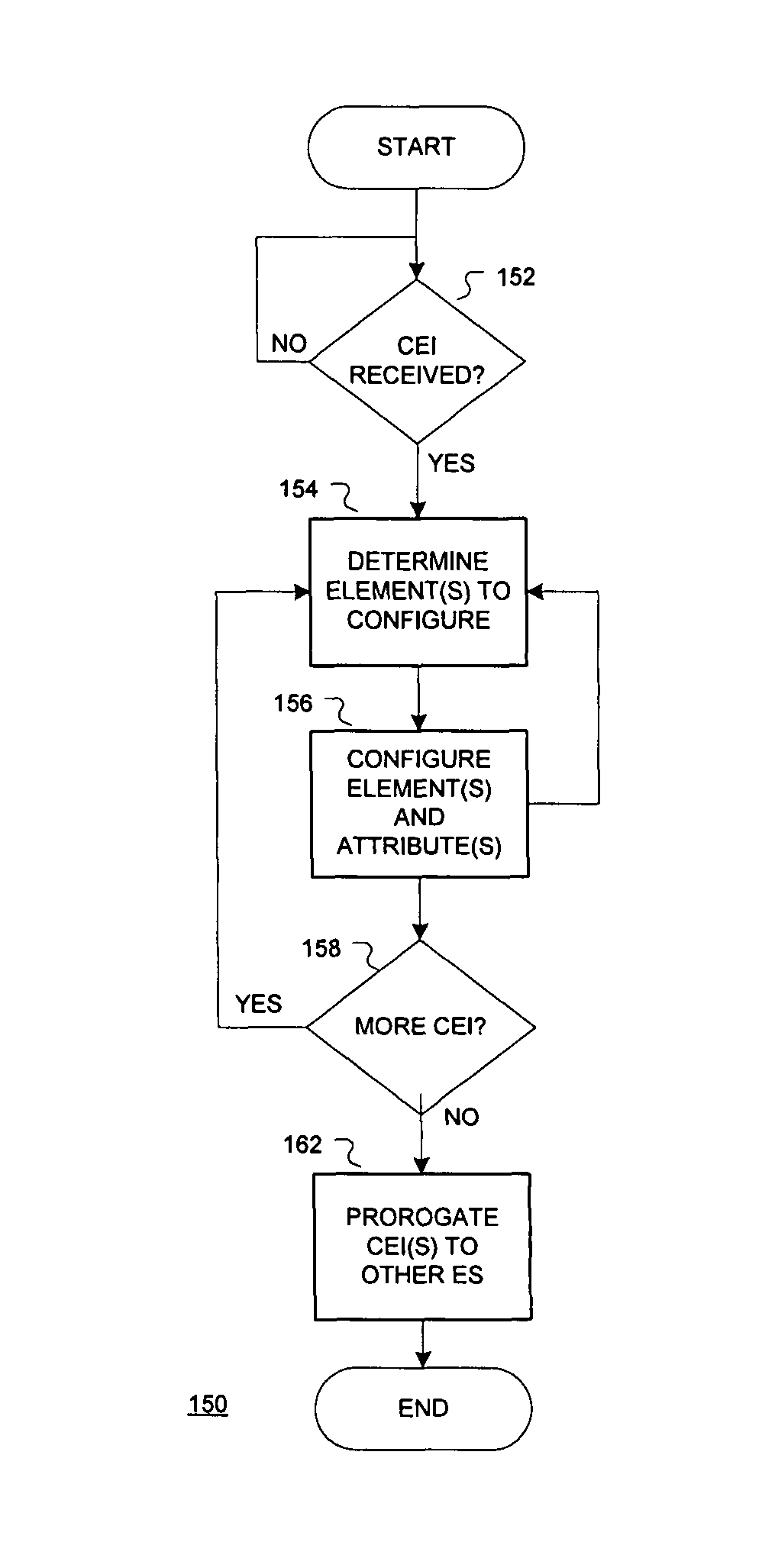
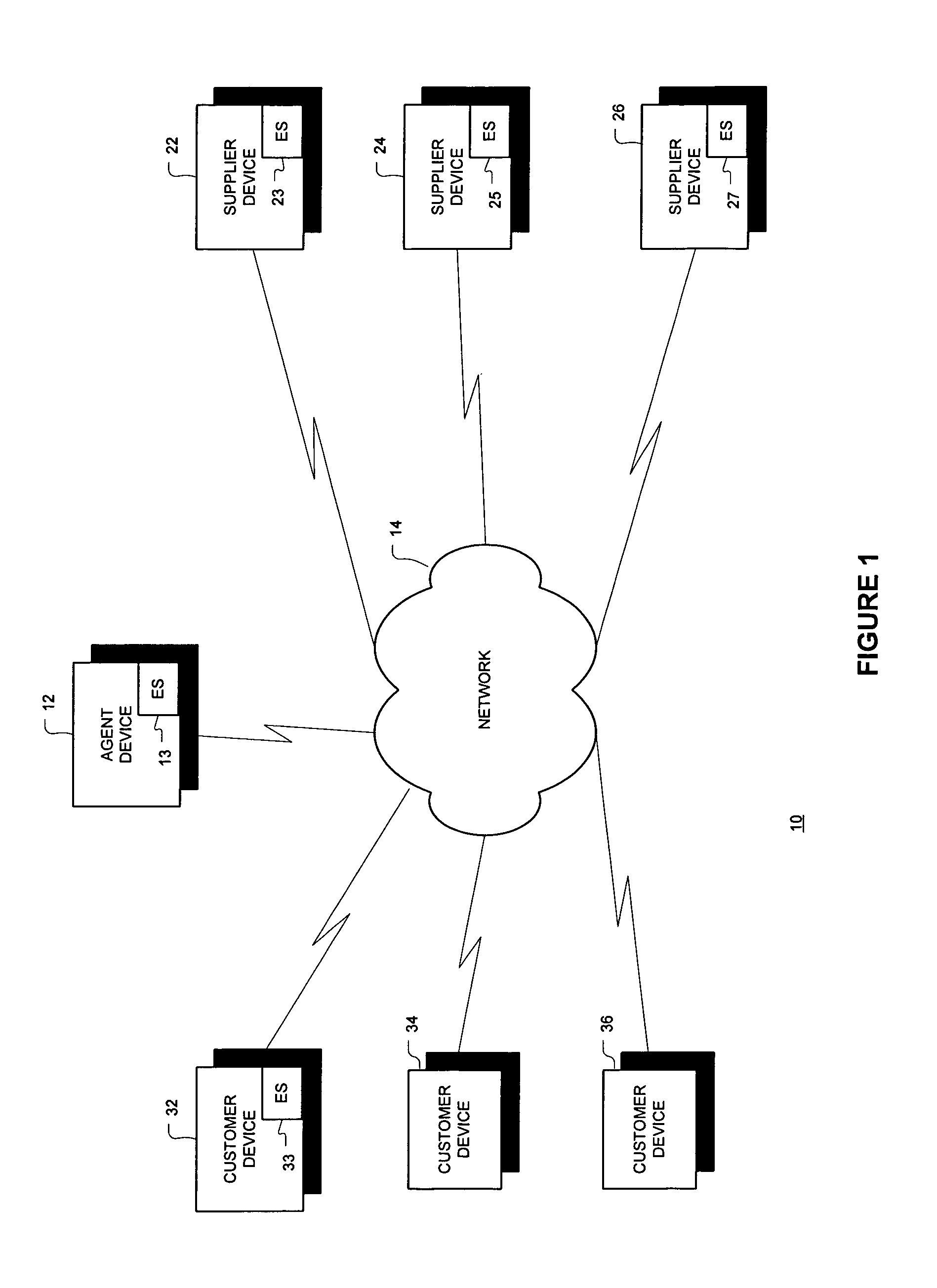
Integrated configuration of cross organizational business processes
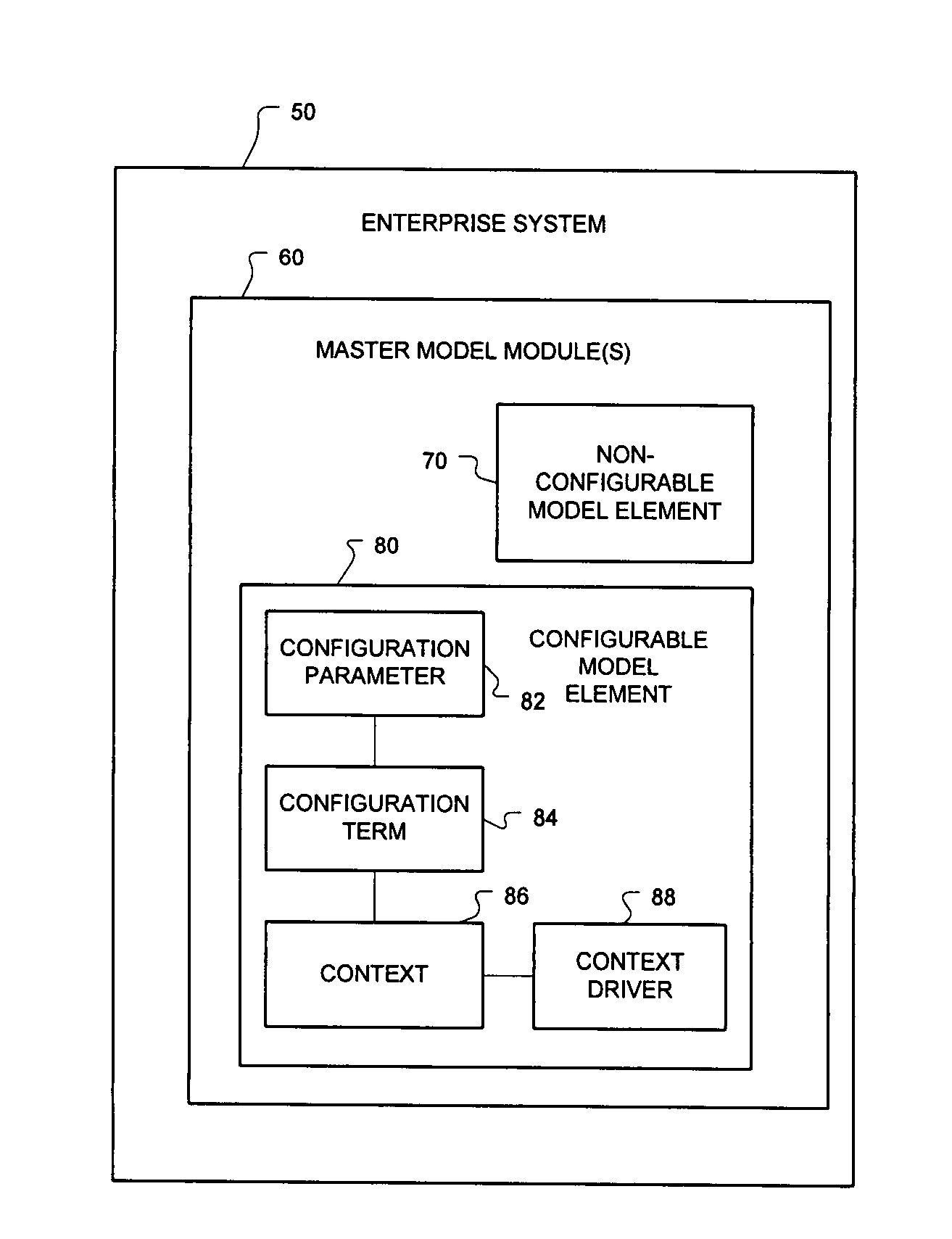
Embodiments of configuring elements of a first enterprise system (ES) and a second ES in mechanisms are described generally herein. For example, in an enterprise system (ES) module for a first ES may include a plurality of configurable elements and a configuration module. The configuration of a first configurable element of the plurality of configurable elements may affect the configuration of a second configurable element of a second ES. The configuration module may configure the a portion of the plurality of the configurable elements of the first ES based on a configuration of the first configurable element. The configuration module may further and generate a configuration element information (CEI) message for the second ES that includes an indication of the configuration of the first configurable element. Other embodiments may be described and claimed.
Owner:SAP AG
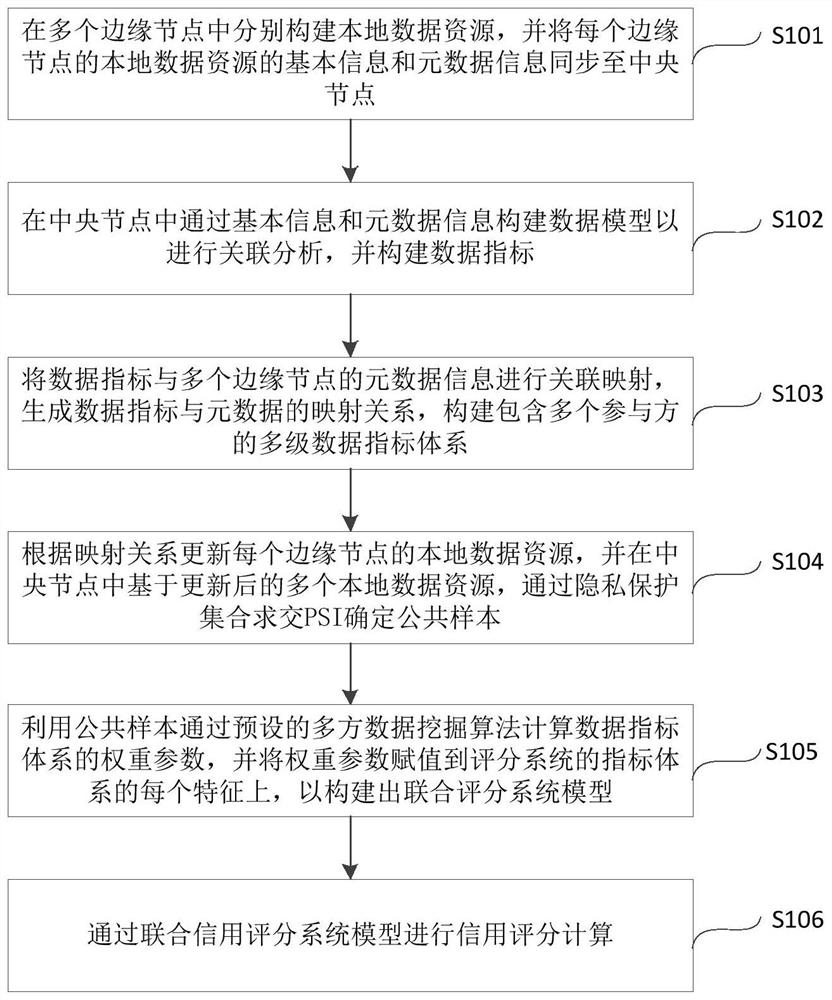
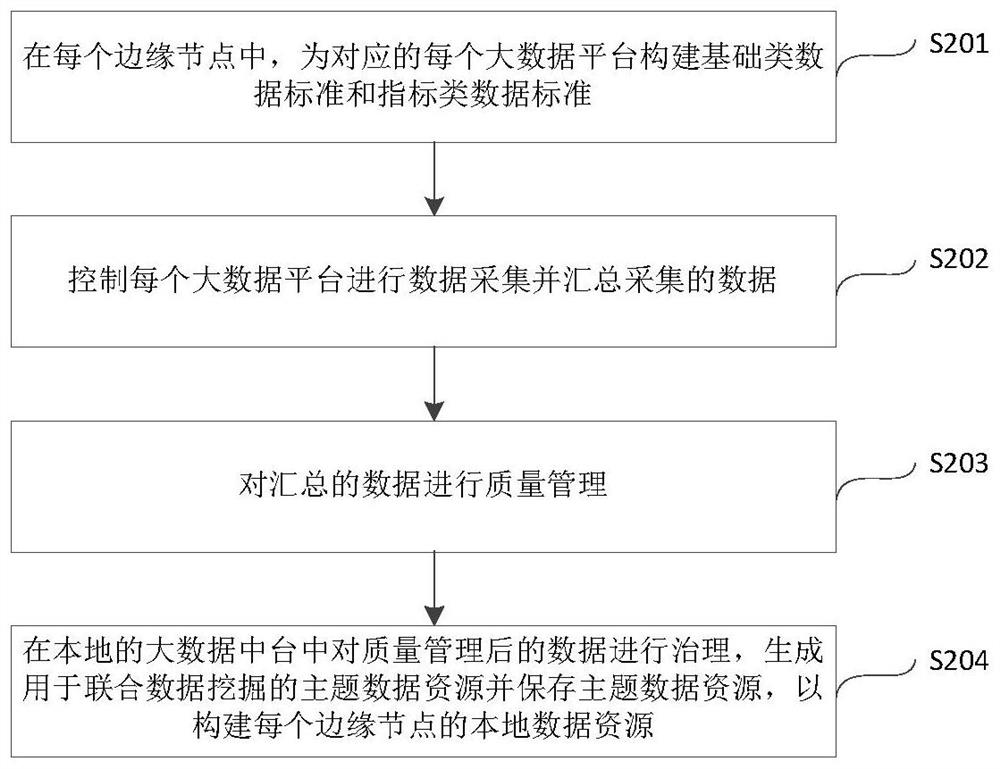
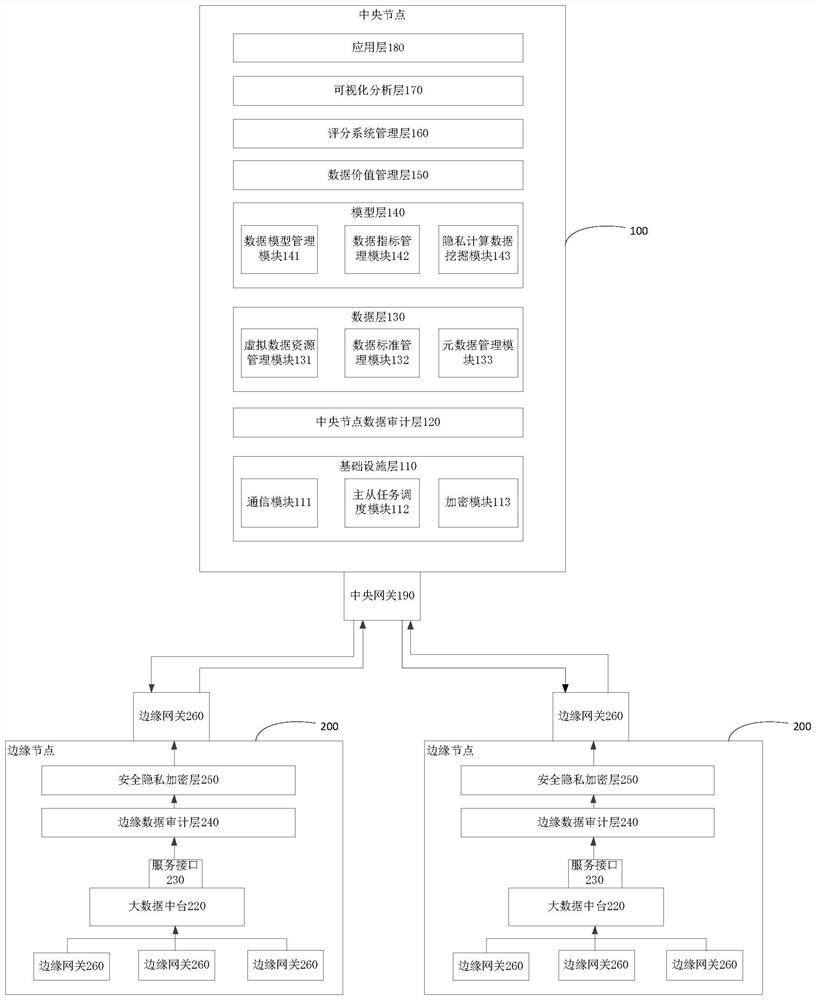
Joint credit scoring method and device based on privacy protection calculation and cross-organization
PendingCN114398669ARealization of security and privacyGuaranteed privacy and securityFinanceCharacter and pattern recognitionPrivacy protectionEdge node
The invention provides a joint credit scoring method and device based on privacy protection calculation and cross-organization, and the method comprises the steps: constructing local data resources in a plurality of edge nodes, and synchronizing the basic information and metadata information of the local data resources to a central node; constructing a data model in the central node through the synchronized information to carry out association analysis, and constructing a data index; performing association mapping on the data index and the metadata information of the plurality of edge nodes; on the basis of the multiple updated local data resources, a public sample is determined through privacy protection set intersection; calculating a weight parameter of the data index system through a multi-party data mining algorithm, and assigning the weight parameter to each feature of the index system of the scoring system; and carrying out credit scoring through the constructed joint scoring system model. According to the method, a cross-organization joint scoring card system architecture is generated under a security privacy adding mechanism, and a high-dimensional complex scoring system can be constructed by effectively utilizing multi-dimensional data.
Owner:BEIJING UNIV OF POSTS & TELECOMM
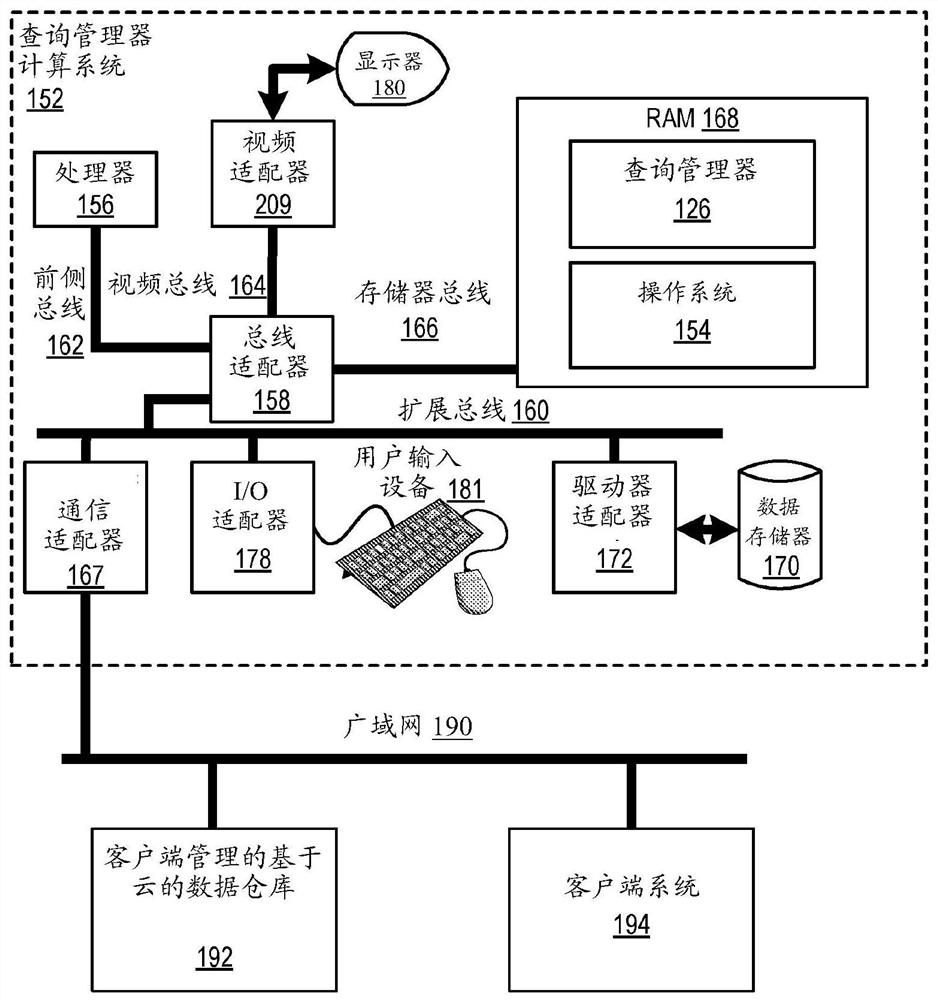
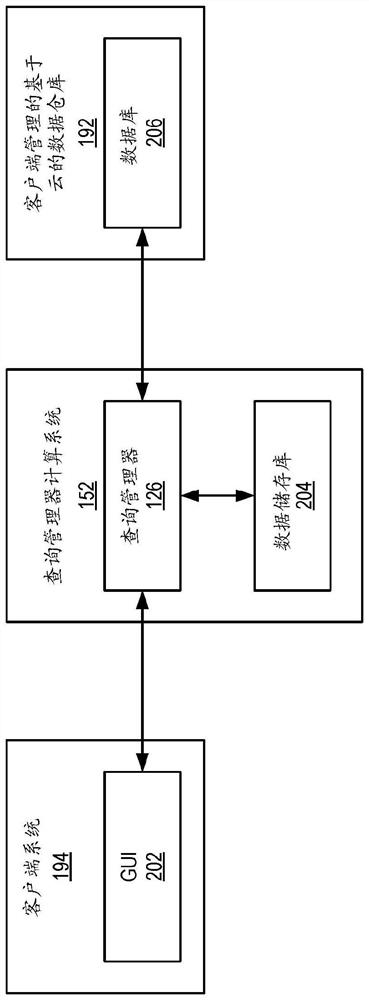
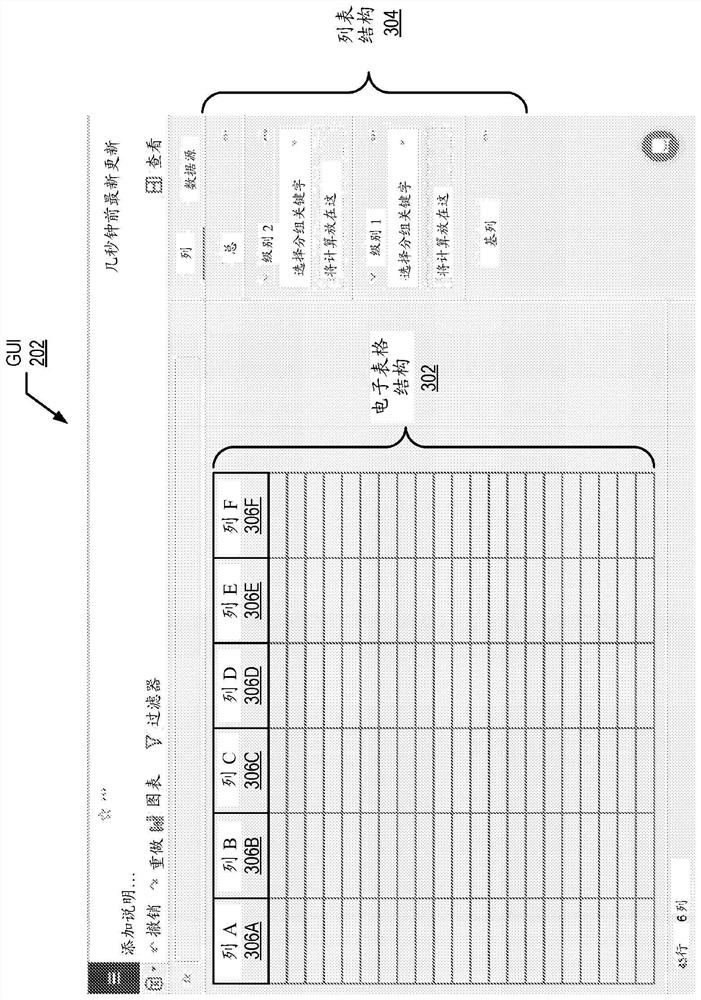
Cross-organization worksheet sharing
Cross-organization worksheet sharing including receiving, from a client, a data set configuration for a worksheet, wherein the data set configuration comprises permissions for a data set from a database stored on a cloud-based data warehouse managed by the client; generating worksheet metadata for the worksheet using the data set configuration; and in response to receiving, from a client system, a request for the worksheet: sending a database query to the cloud-based data warehouse, wherein the database query is generated using the worksheet metadata including the permissions for the data set; receiving, in response to the database query, the data set from the cloud-based data warehouse; and presenting, to the client system, the worksheet containing the data set using the data set configuration including limiting the presentation based on the permissions for the data set received from the client.
Owner:SIGMA COMPUTING INC
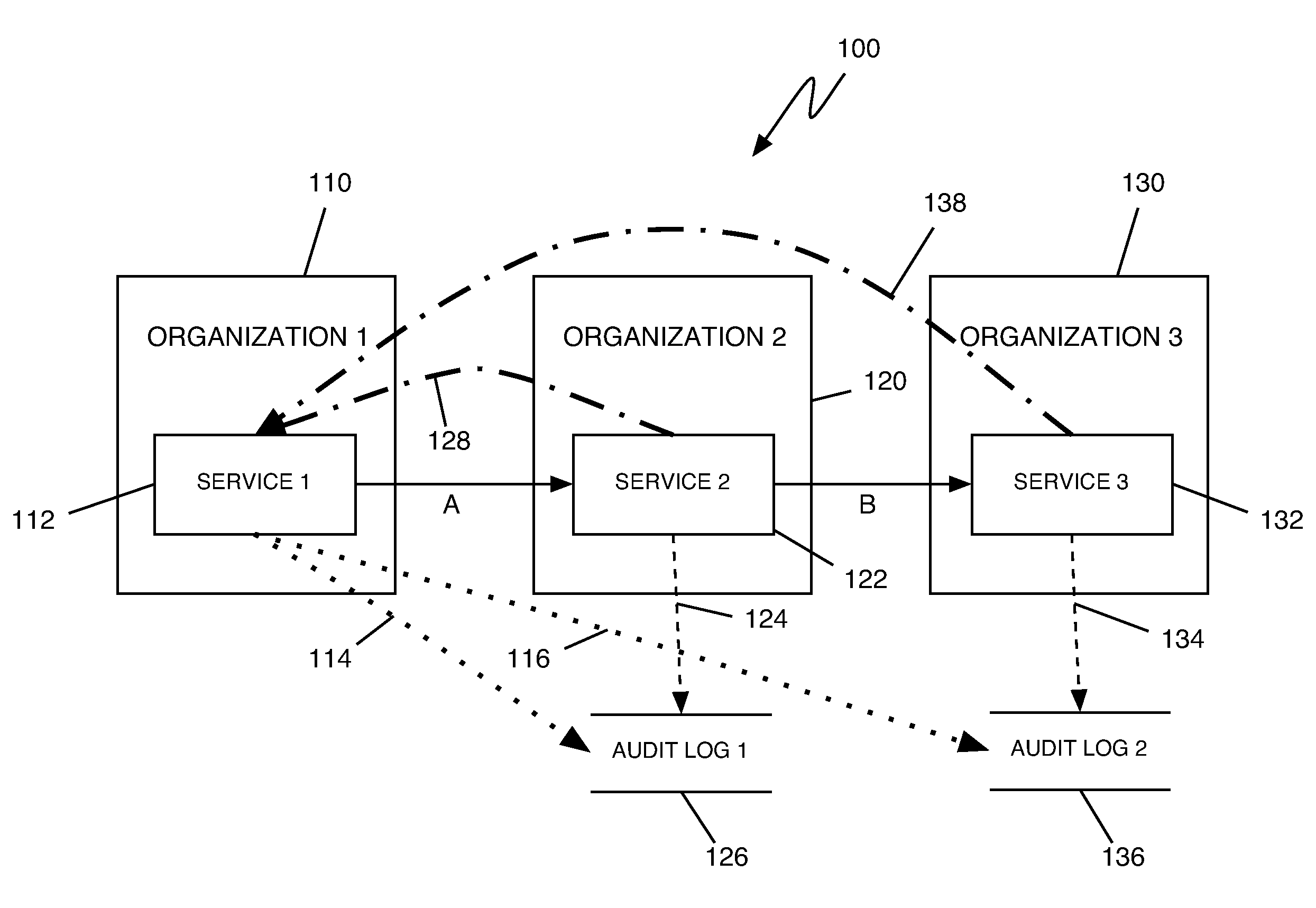
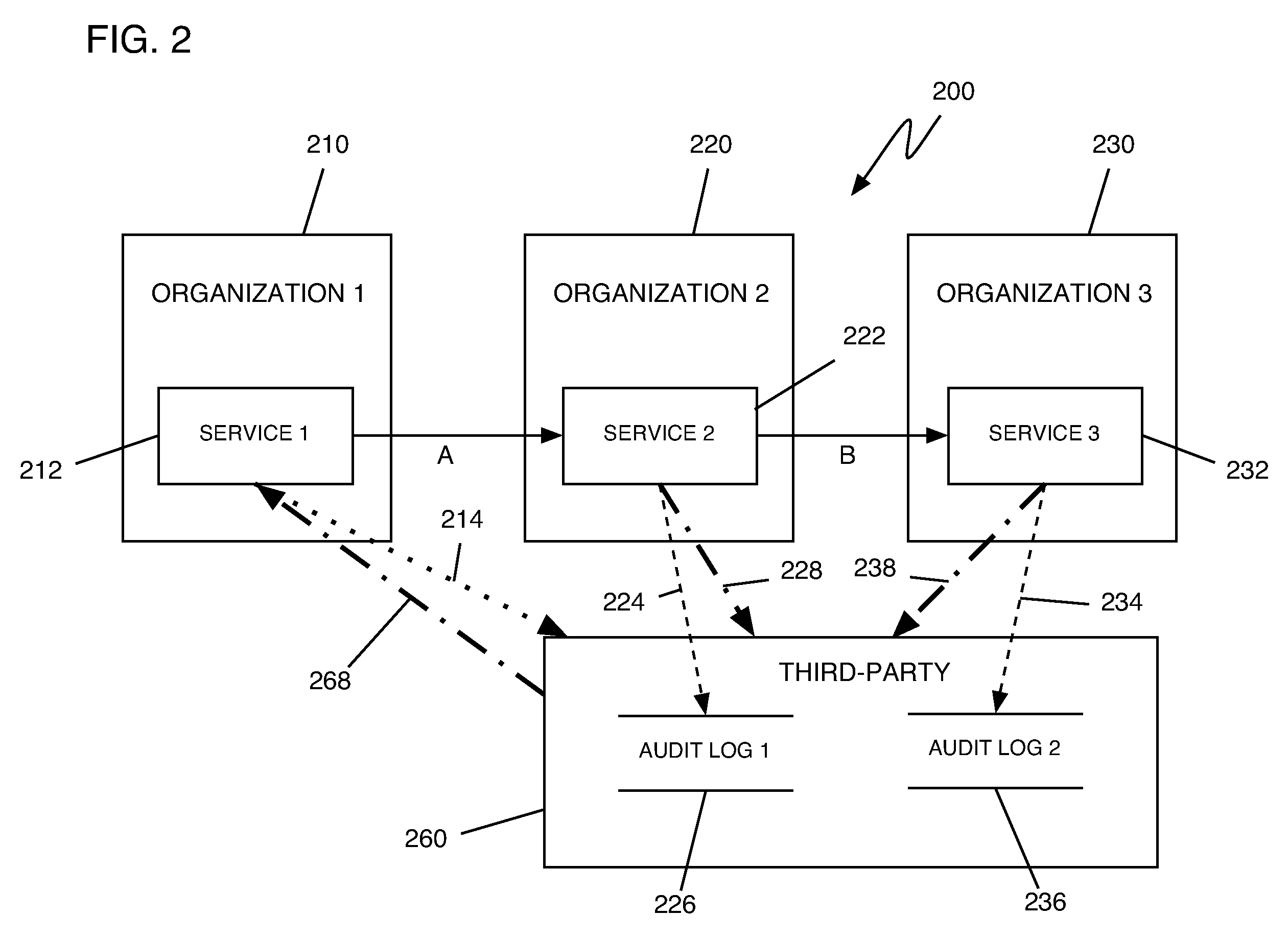
Method, system, and program product for conducting a cross-organizational transaction audit
InactiveUS20070271271A1Office automationBuying/selling/leasing transactionsOperating systemCross organizational
The invention provides a method, system, and program product for conducting a cross-organizational transaction audit. In one embodiment, the invention includes a first entity requesting that a second entity perform a task; a third entity creating a log of information related to the second entity's performance of the task and verifying to the first entity that the task was performed; the first entity examining the log to determine at least one of the following: whether the second entity's performance of the task was satisfactory and how the second entity used information provided by the first entity in performing the task; and the first entity verifying that the second entity's performance of the task was satisfactory.
Owner:IBM CORP
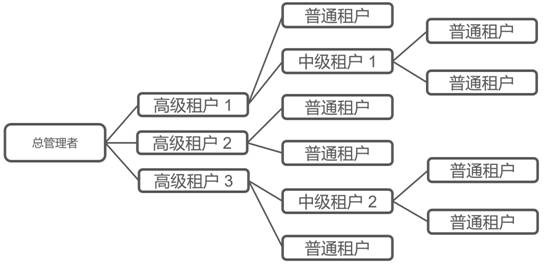
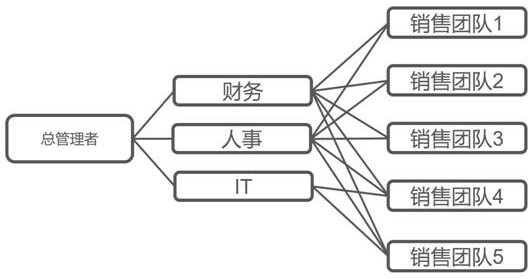
Multi-level multi-tenant cross authorization management method
The invention relates to a multi-level multi-tenant cross authorization management method, which comprises the following steps: defining a plurality of management roles in different organizations, and carrying out access permission and resource configuration on the management roles; selecting cross-server users in different organizations from the management role, and mounting the cross-server users on the management role to form a cross management role; and presetting a role consignment rule, and endowing the cross management role to a user according to the role consignment rule. The cross authorization and resource access of different management nodes can be carried out across organizations, the authorization tree can realize cross authorization management on all tenants, the authorization trees of all roles do not need to be modified in batches for newly introduced tenants, and the workload is very small. According to the invention, on the basis of a plurality of stackable tree-shaped management architectures, a plurality of layers of special management relationships are stacked, and cross authorization of a classical architecture and special requirements is considered, so that a management architecture which cannot be realized by a multi-tenant system of a traditional tree-shaped management architecture can be met.
Owner:北京天维信通科技股份有限公司
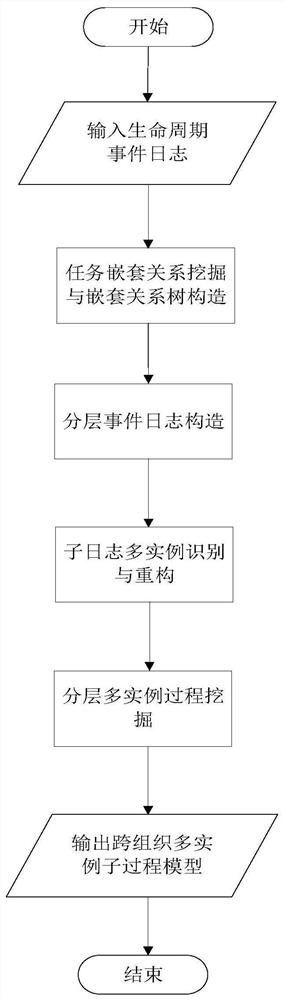
Cross-organization multi-instance sub-process model mining method and system
PendingCN113342495AEasy to digConducive to expression level callsProgram initiation/switchingExecution paradigmsData packLog mining
The invention discloses a cross-organization multi-instance sub-process model mining method and system, and the method comprises the following steps: 1) obtaining basic data, including a life cycle event log of a cross-organization multi-instance sub-process; 2) utilizing the obtained life cycle event log to mine a nesting relation between life cycle event log activities, and representing the nesting relation by a nesting relation tree; 3) constructing a hierarchical event log by using the nested relationship obtained by mining; 4) performing multi-instance identification and reconstruction on the sub-logs by utilizing the layered event log obtained by mining to obtain a reconstructed layered event log; and 5) mining a cross-organization multi-instance sub-process model from the reconstructed hierarchical event log. According to the invention, the limitation that a traditional process mining technology cannot support mining of multiple calling sub-processes in a cross-organization business scene is broken through, and the efficiency and effect of designing and modeling cross-organization multi-instance sub-processes in process mining are effectively improved.
Owner:北京杰成合力科技有限公司
Method and system for realizing business cross-organization circulation based on process engine
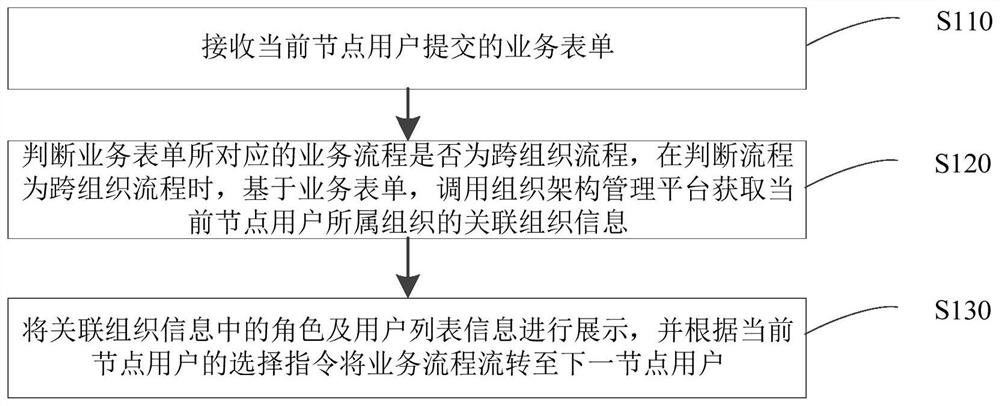
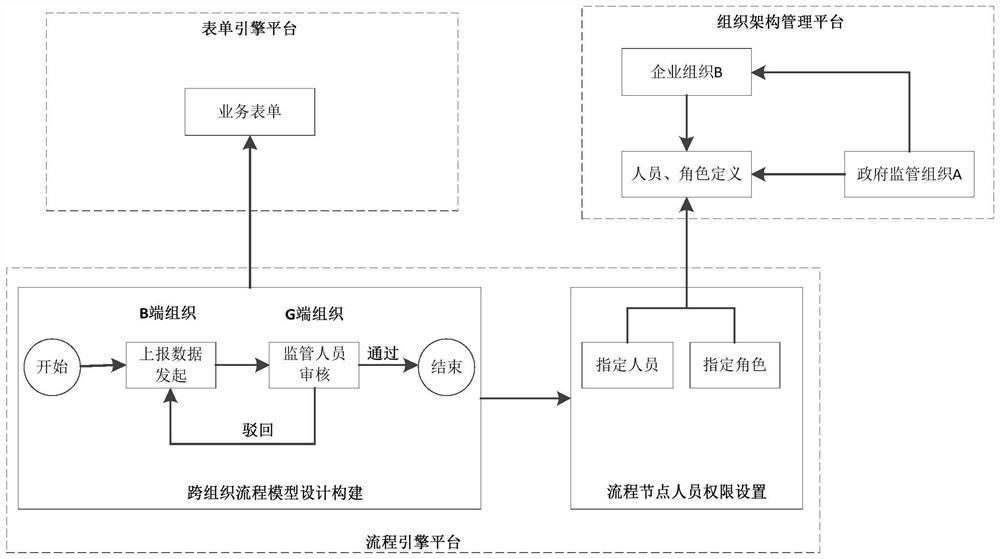
PendingCN114548915AReduce complexityAchieve circulationEnergy industryOffice automationBusiness processOrganizational architecture
The invention relates to a method and system for achieving service cross-organization circulation based on a process engine, and belongs to the technical field of office automation. The method comprises the steps that a service form submitted by a current node user is received; judging whether a business process corresponding to the business form is a cross-organization process or not, and when the process is judged to be the cross-organization process, calling an organization structure management platform to obtain associated organization information of an organization to which the current node user belongs based on the business form, definition information of users and roles under different organizational structures and mapping relation information among the different organizational structures are configured in the organizational structure management platform; and displaying roles and user list information in the associated organization information, and transferring the business process to a next node user according to a selection instruction of the current node user. According to the method and the device, cross-organization circulation of the business process can be better realized.
Owner:BEIJING JINHER SOFTWARE
Business data sharing method and device based on saas cloud platform
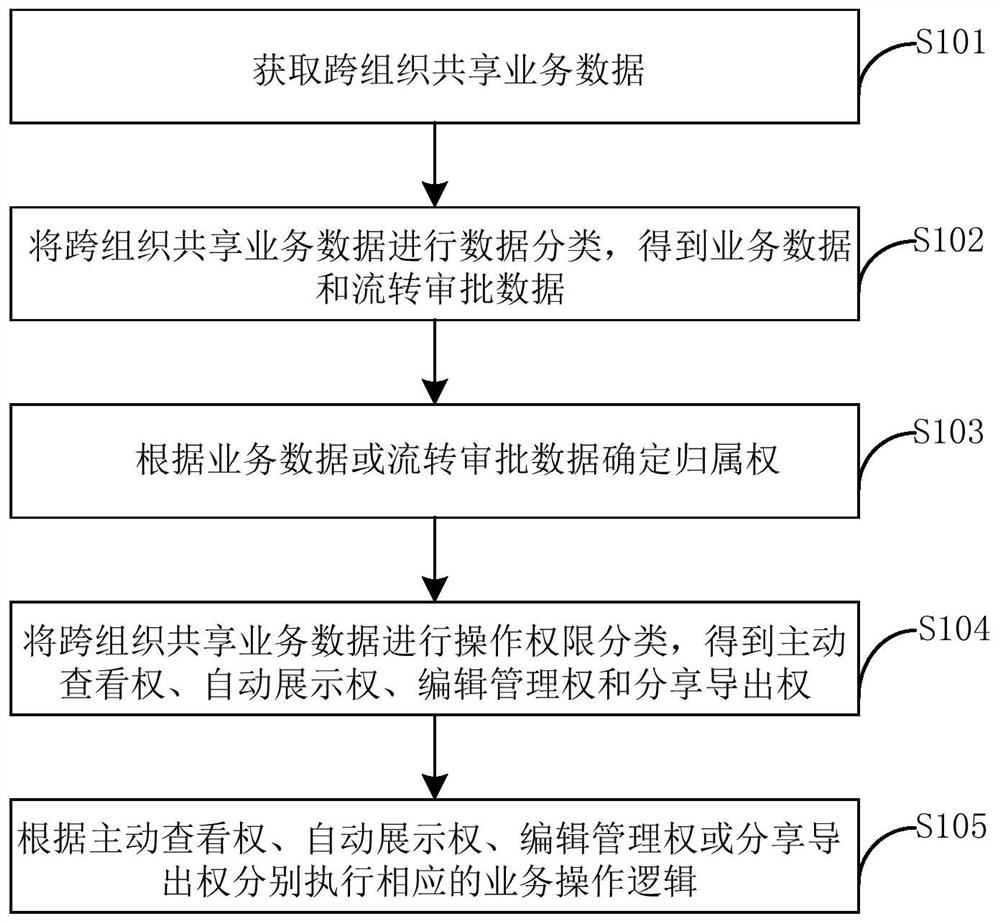
ActiveCN108282477BReduce workloadReduce operational complexityDigital data protectionTransmissionAuthorization ModeClassification methods
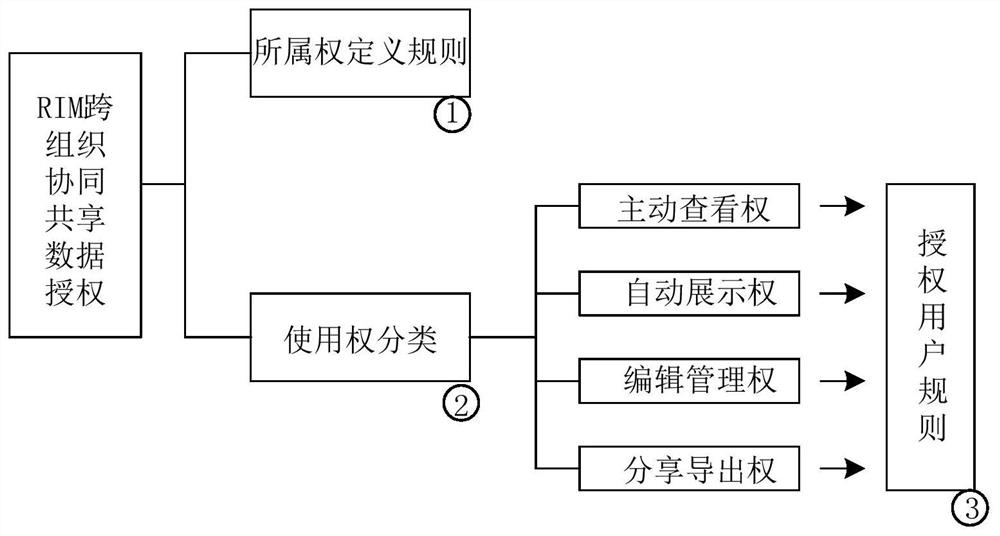
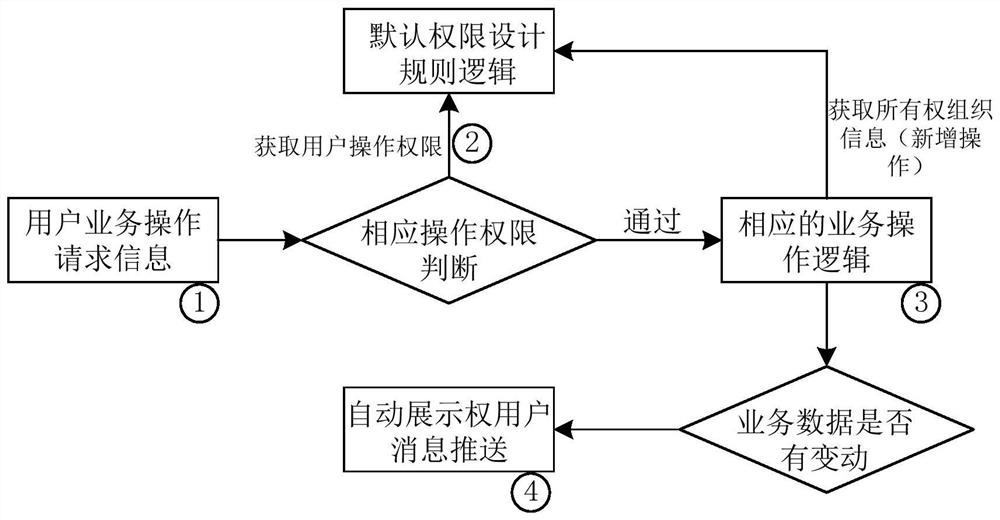
The present invention provides a business data sharing method and device based on a SaaS cloud platform, including: acquiring cross-organization shared business data; classifying cross-organization shared business data to obtain business data and circulation approval data; Determine the ownership right; classify the operation authority of cross-organization sharing business data, and obtain the active viewing right, automatic display right, editing management right, and sharing and exporting right; respectively execute according to the active viewing right, automatic displaying right, editing management right, or sharing and exporting right The corresponding business operation logic can reduce the workload and operational complexity of manual data authorization by sharing business data ownership judgment rules, data usage authority classification methods, and automation device authorization methods across organizations, and also provide basic authorization for the RIM big data platform Classification.
Owner:REM TEC SRL
Network security service guarantee method
ActiveCN113098890AReduce R&D costsFully reflect the parallel relationshipTransmissionTransmission protocolConfidentiality
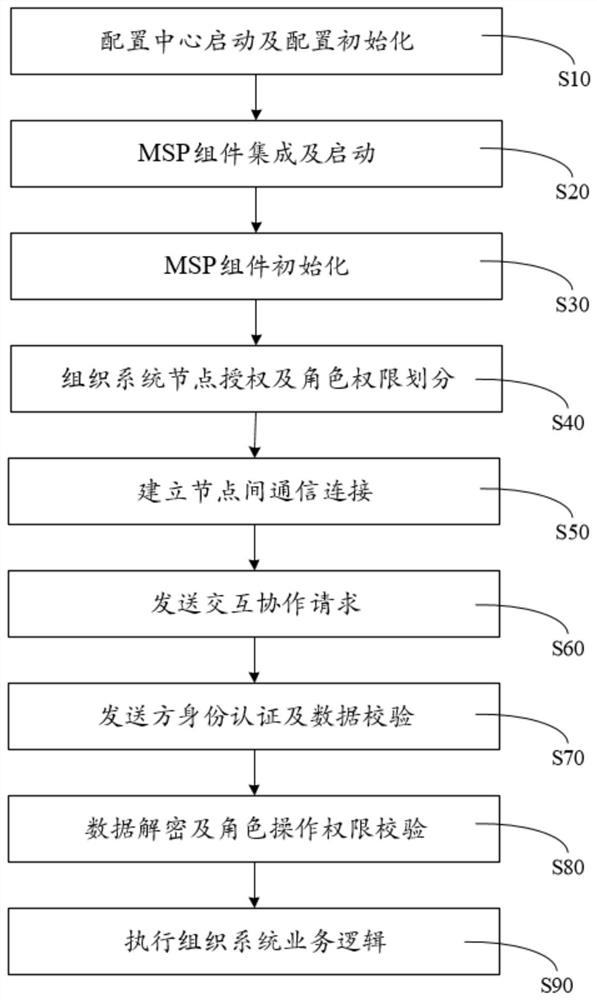
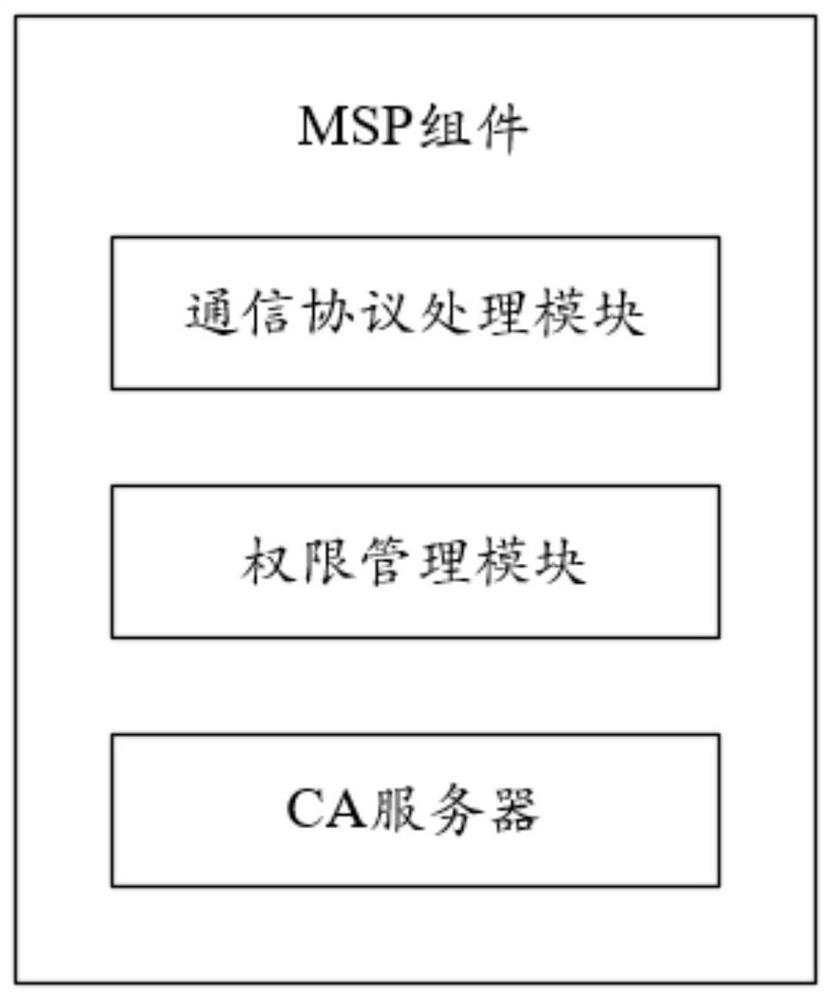
The invention relates to a network security service guarantee method, which is used for providing equal mutual trust and communication data security guarantee for transmitting sensitive data and business cooperation on a public network among different organization systems. The network security service guarantee method is implemented by an MSP component, a configuration center and a user-defined transmission protocol. The method comprises the following steps: starting the configuration center and initializing configuration; integrating and starting an MSP component; initializing the MSP component; organizing system node authorization and role permission division; establishing communication connection between the nodes; sending an interactive cooperation request; carrying out identity authentication and data verification on a sender; performing data decryption and role operation authority verification; and executing the business logic of the organization system. The network security service guarantee method provided by the invention has the core positive effects that a traditional single-party credit authentication mode is abandoned, cross-organization and cross-system cooperation is established on the basis of two-party or multi-party equal mutual trust, and the confidentiality and integrity of data transmission in the cooperation process are ensured by an enough security means.
Owner:深圳市骑换科技有限公司
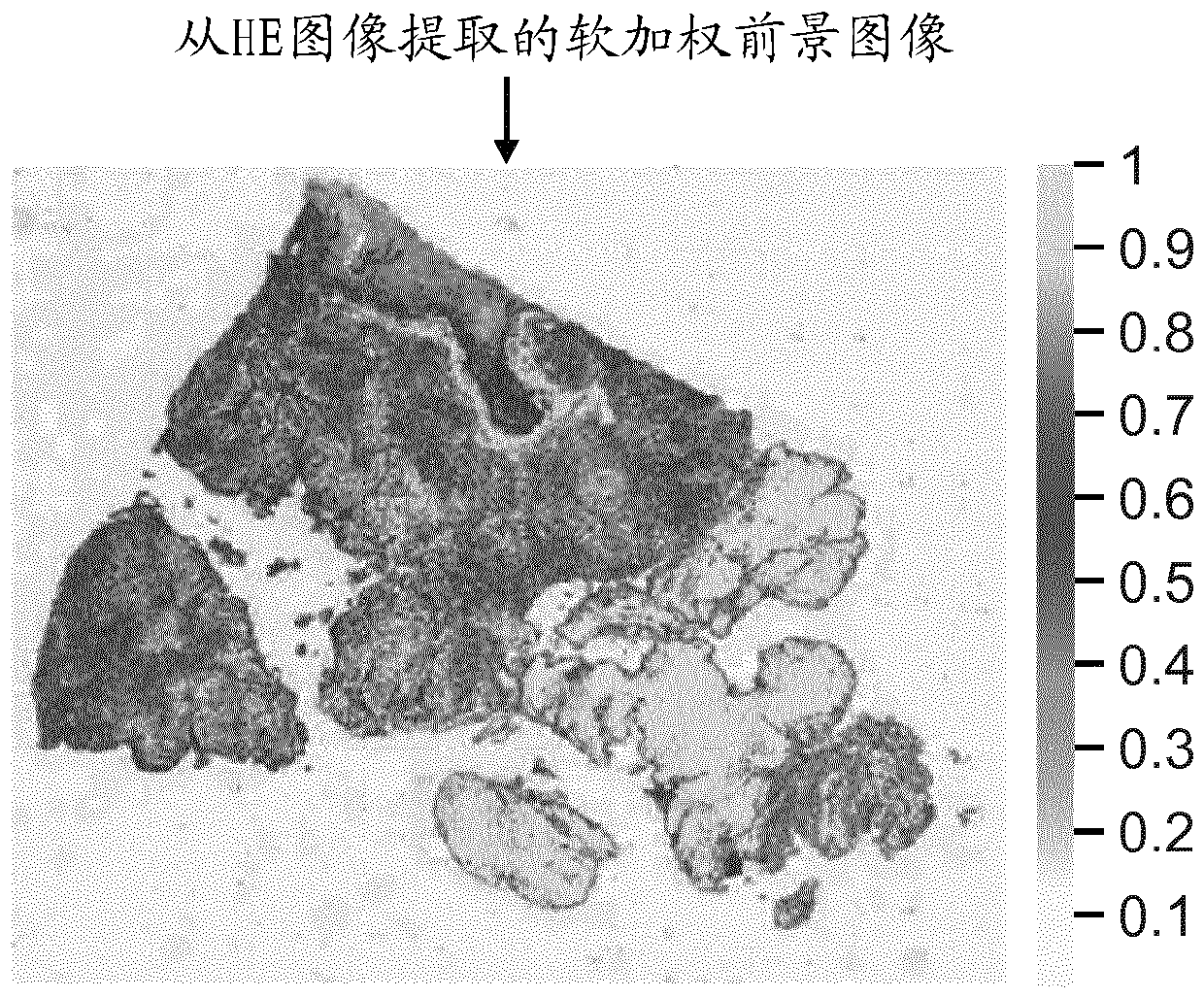
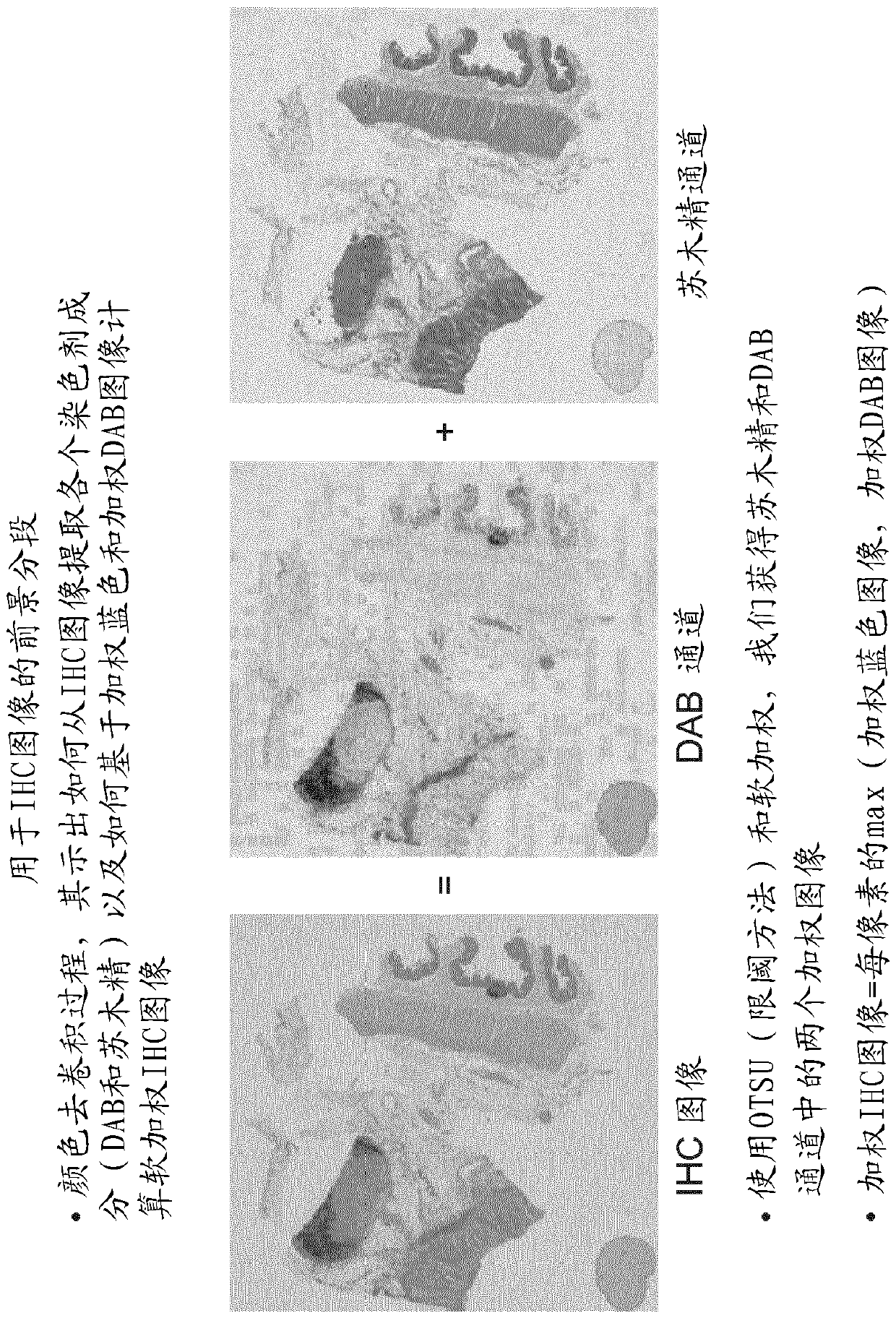
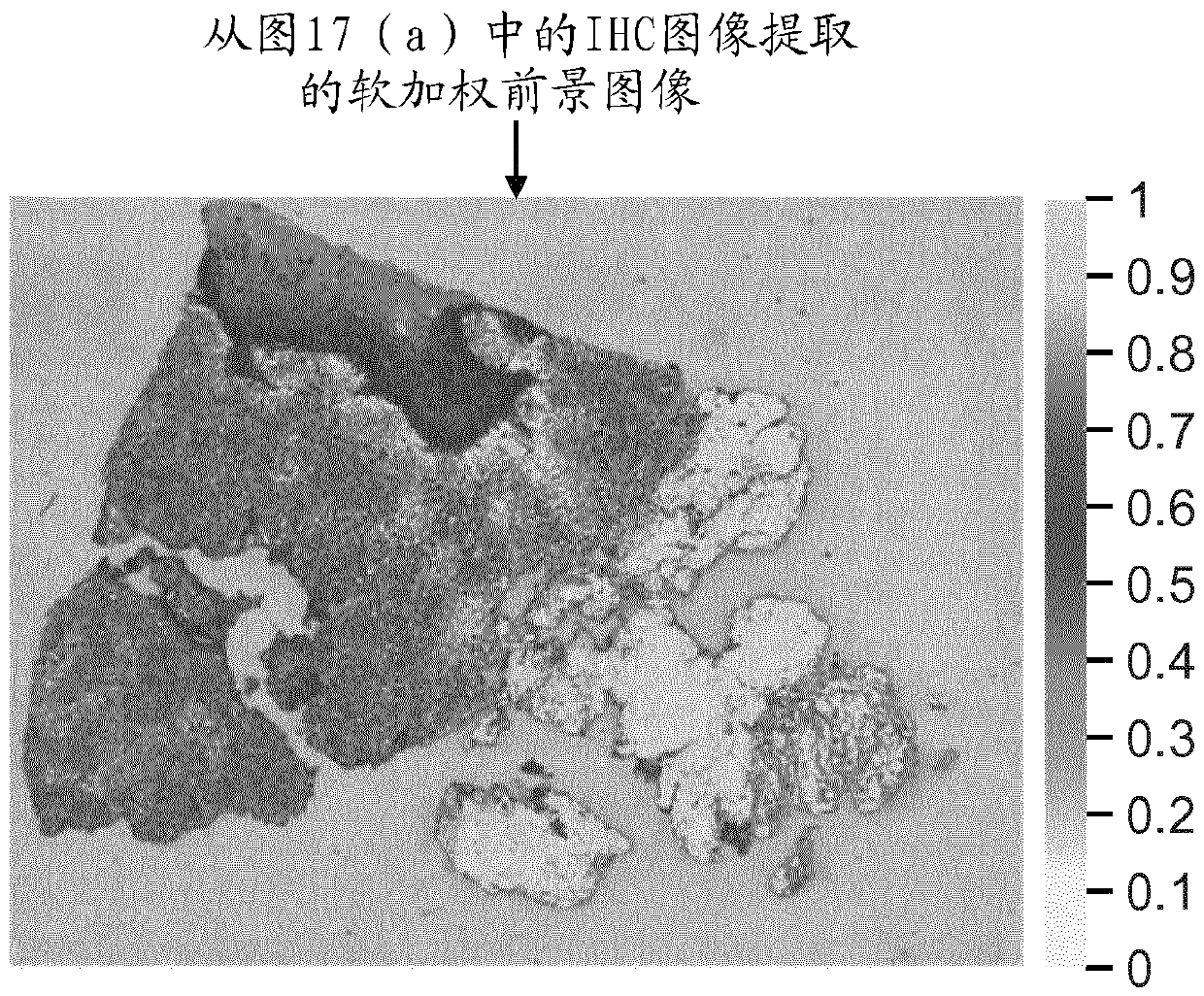
Complete slide image registration and cross-image annotation apparatus, system and method
The present disclosure relates to devices, systems and methods for image registration and annotation. The apparatus includes a computer software product for aligning digital images of a full slide on a common grid and transferring annotations from one aligned image to another on the basis of matching tissue structures. The system includes computer-implemented systems such as workstations and networked computers for performing tissue-based image registration and cross-image annotation. The method includes procedures for aligning digital images corresponding to adjacent tissue slices on a common grid based on tissue structure and transferring annotations from one adjacent tissue image to another adjacent tissue image.
Owner:VENTANA MEDICAL SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com