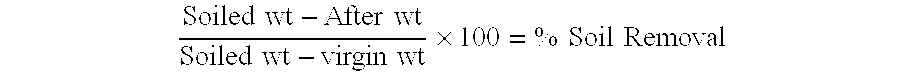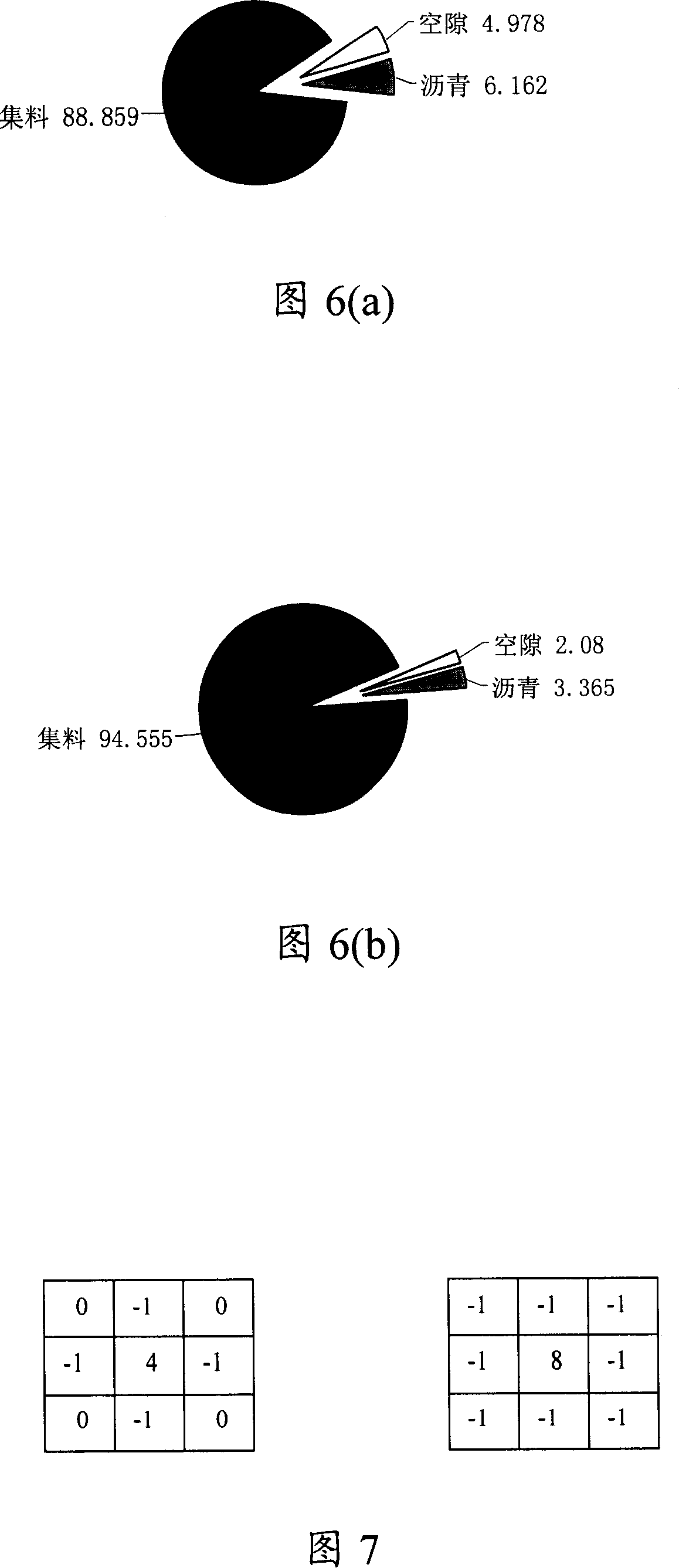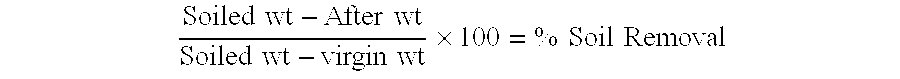Patents
Literature
277results about How to "The result is valid" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
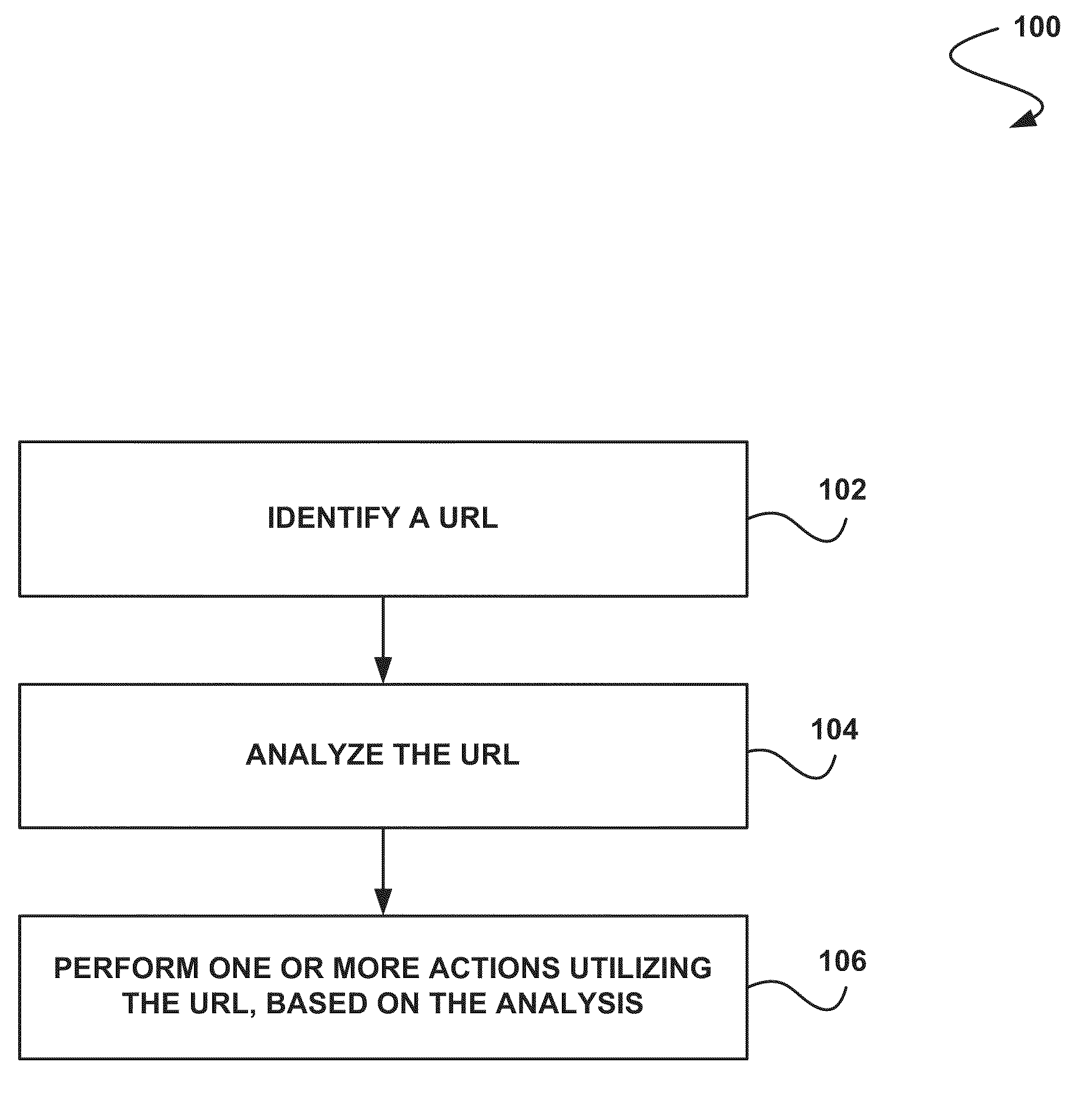
System, method and computer program product for performing one or more actions utilizing a uniform resource locator
ActiveUS20110218958A1Improve URL comprehensionImprove useNatural language data processingFuzzy logic based systemsComputer programUniform resource locator
In accordance with embodiments, there are provided mechanisms and methods for performing one or more actions utilizing a uniform resource locator. These mechanisms and methods for performing one or more actions utilizing a uniform resource locator can enable improved overall URL usage, more efficient search engine URL results, improved URL comprehension by users, etc.
Owner:SALESFORCE COM INC
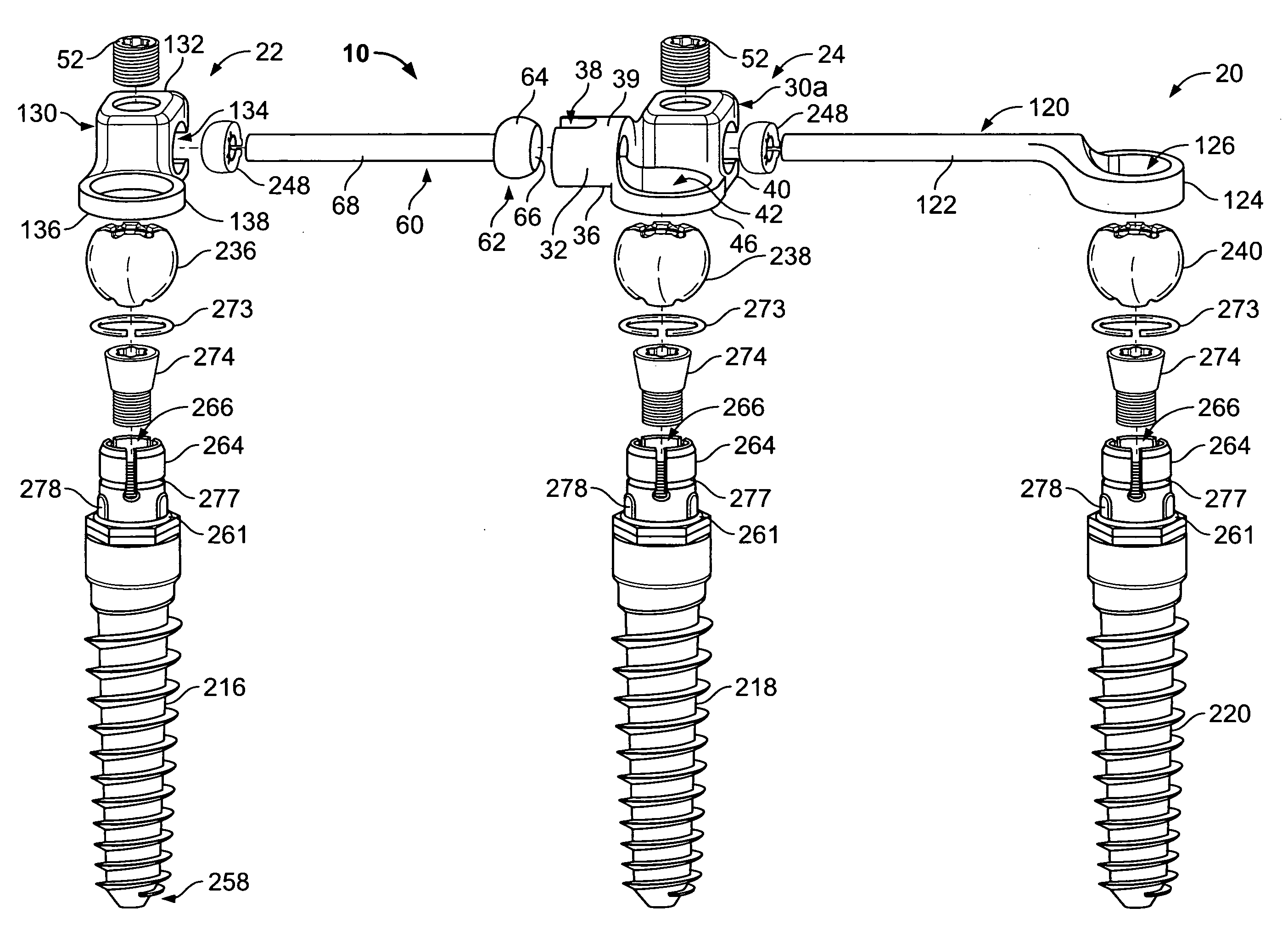
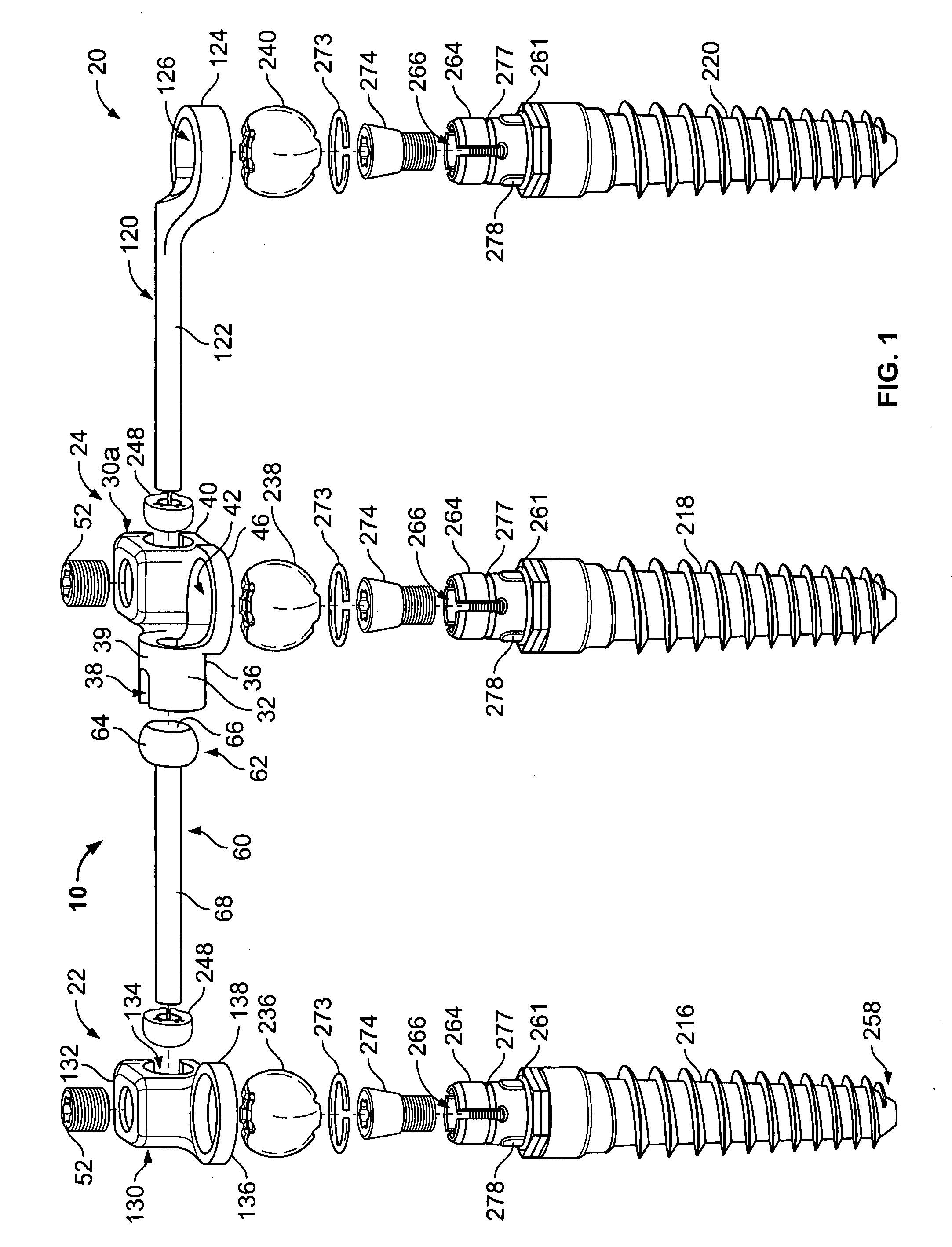
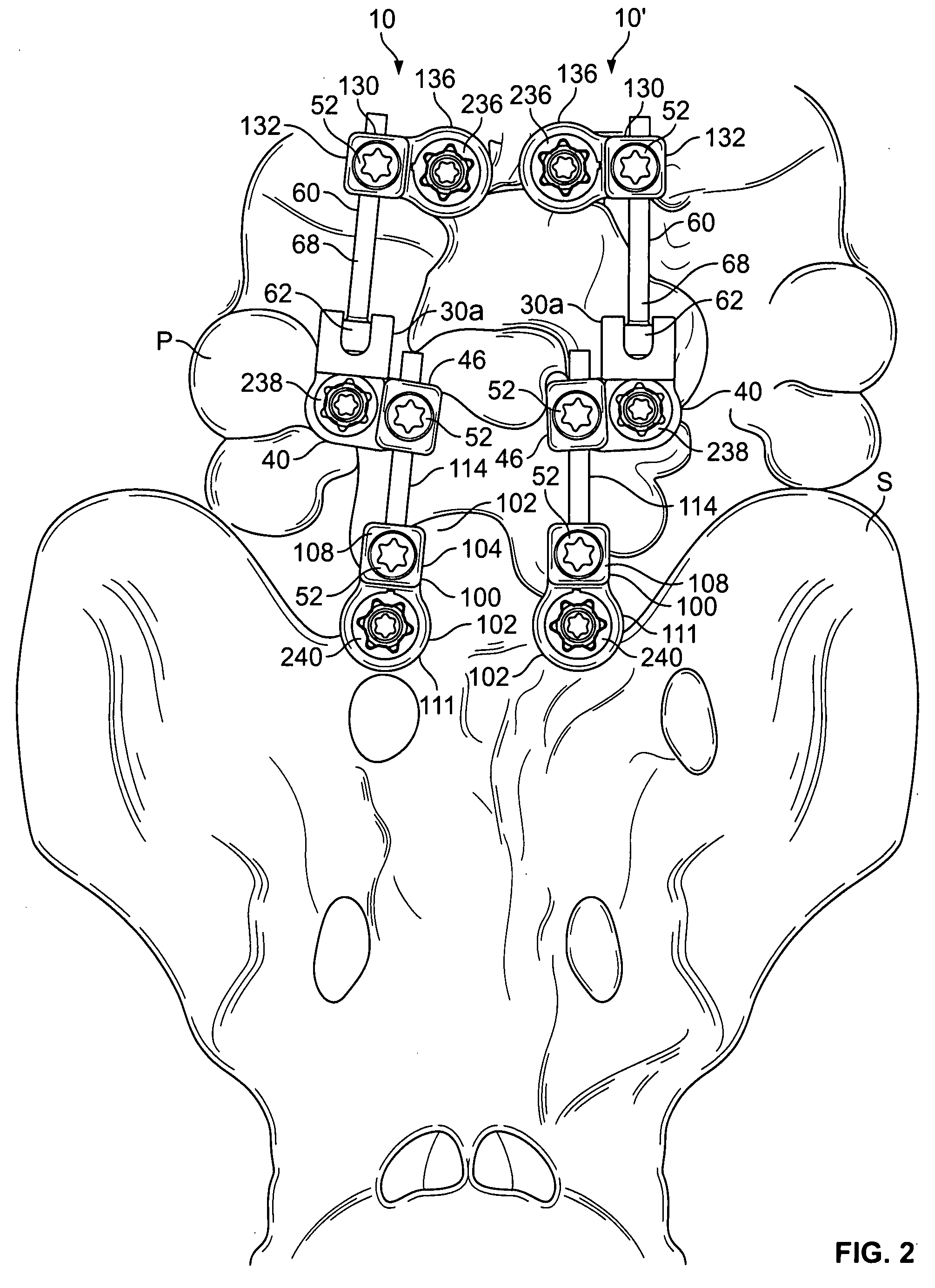
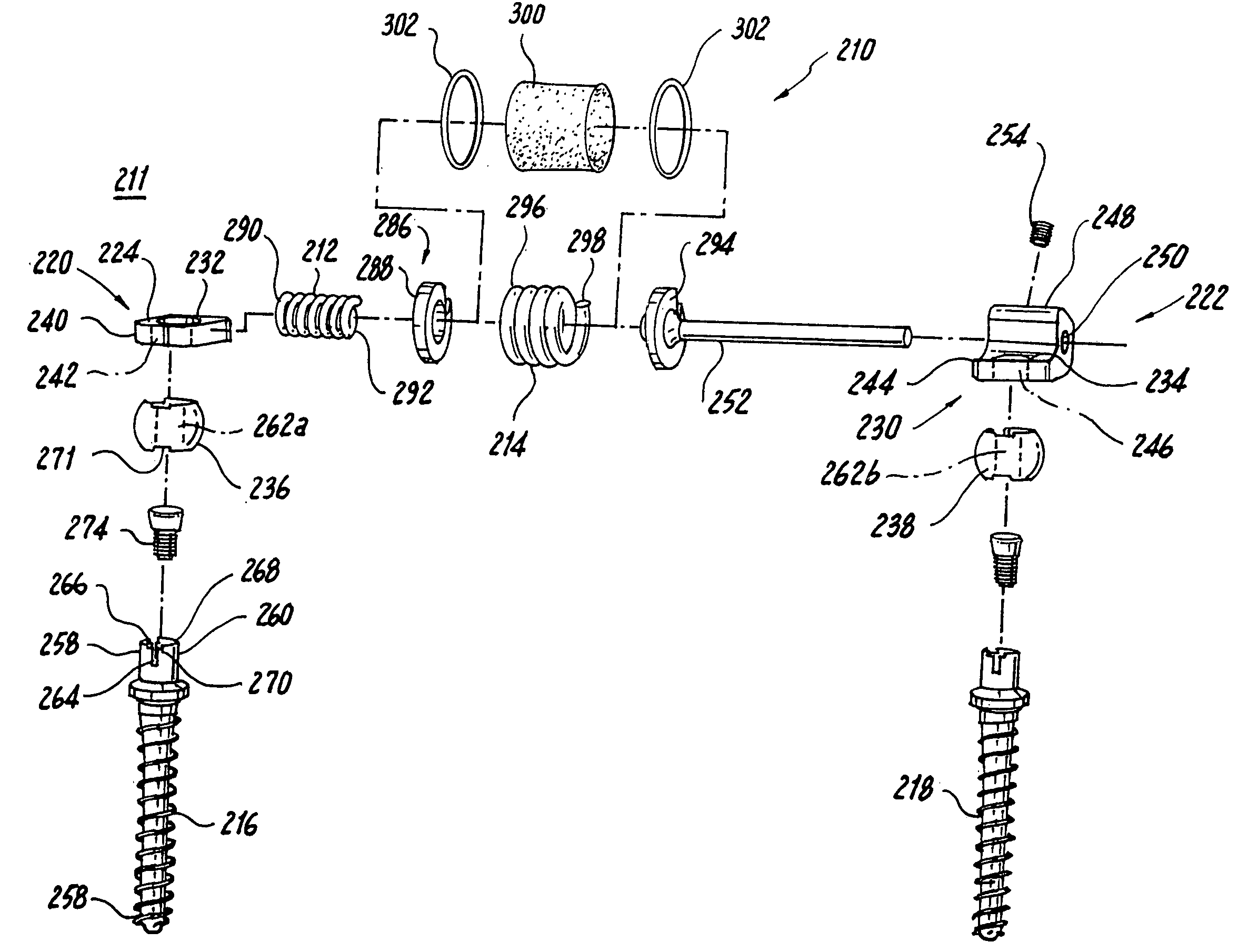
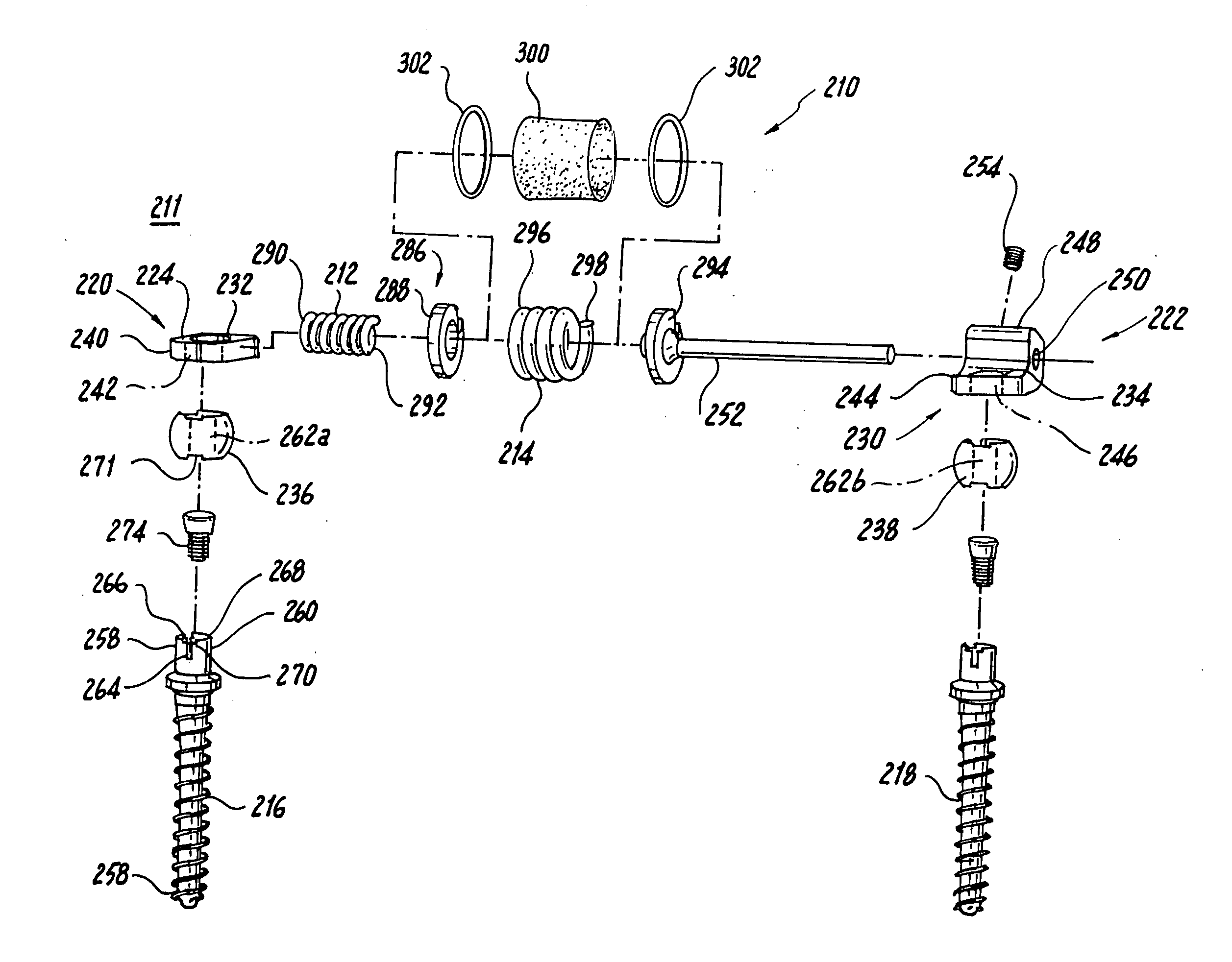
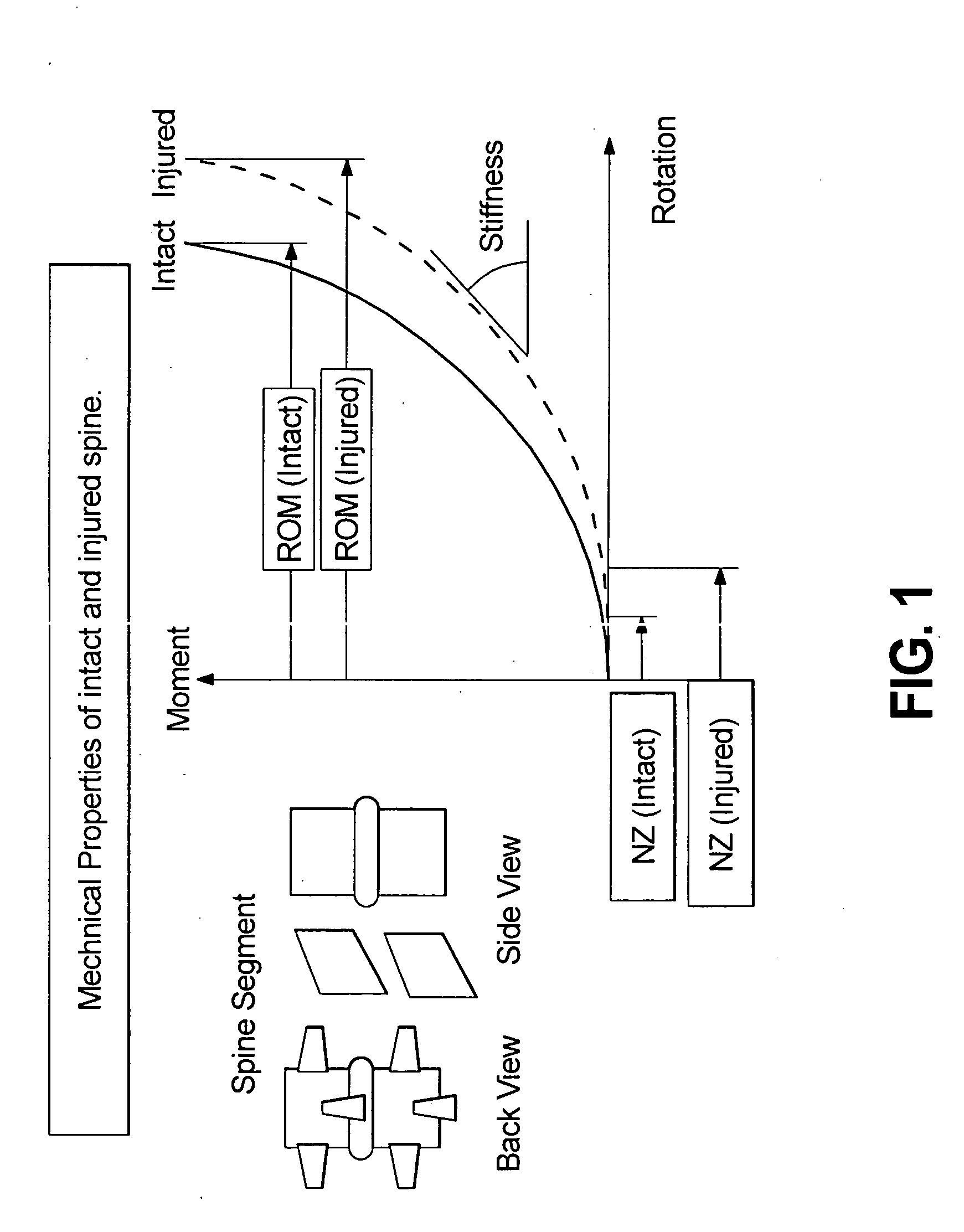
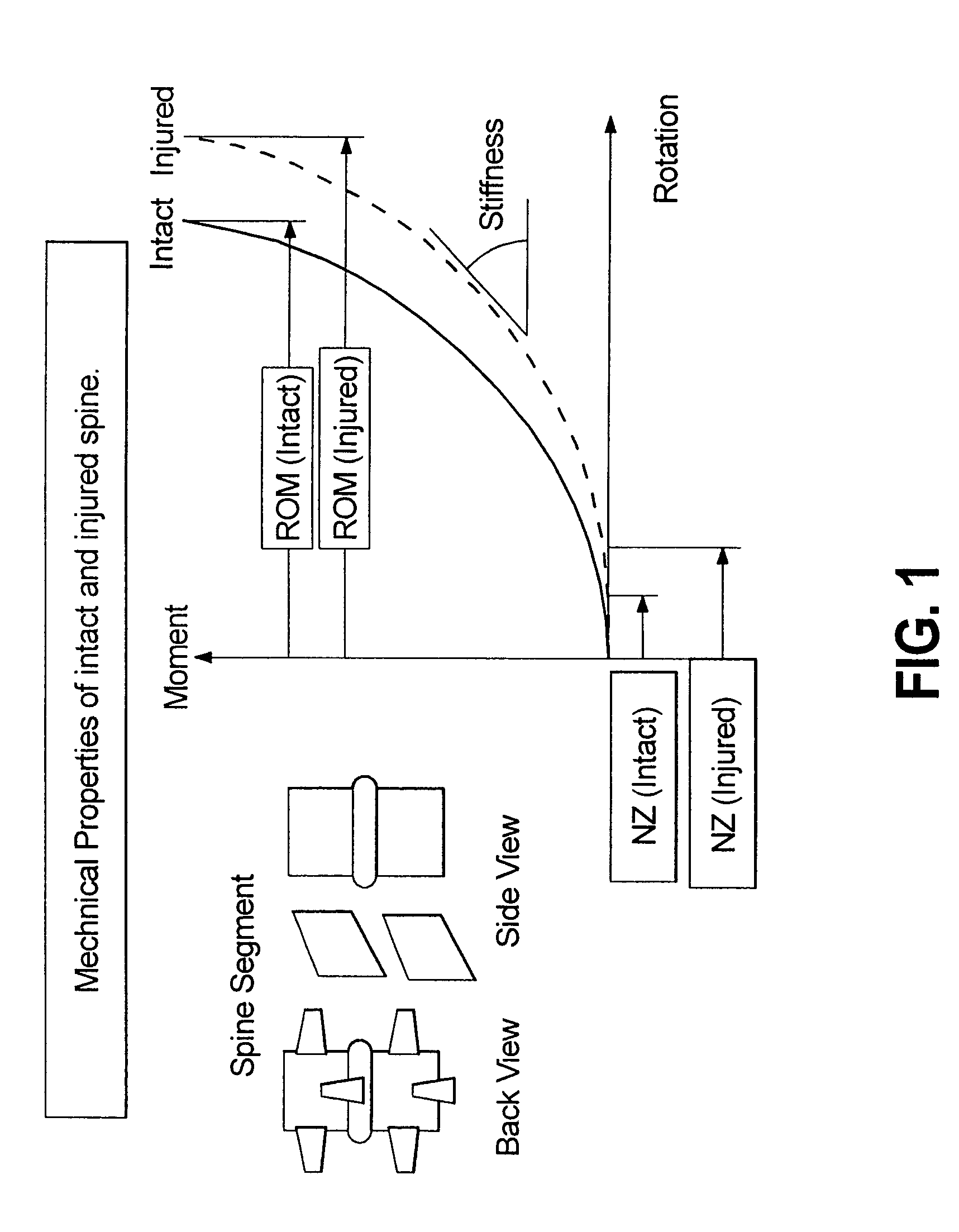
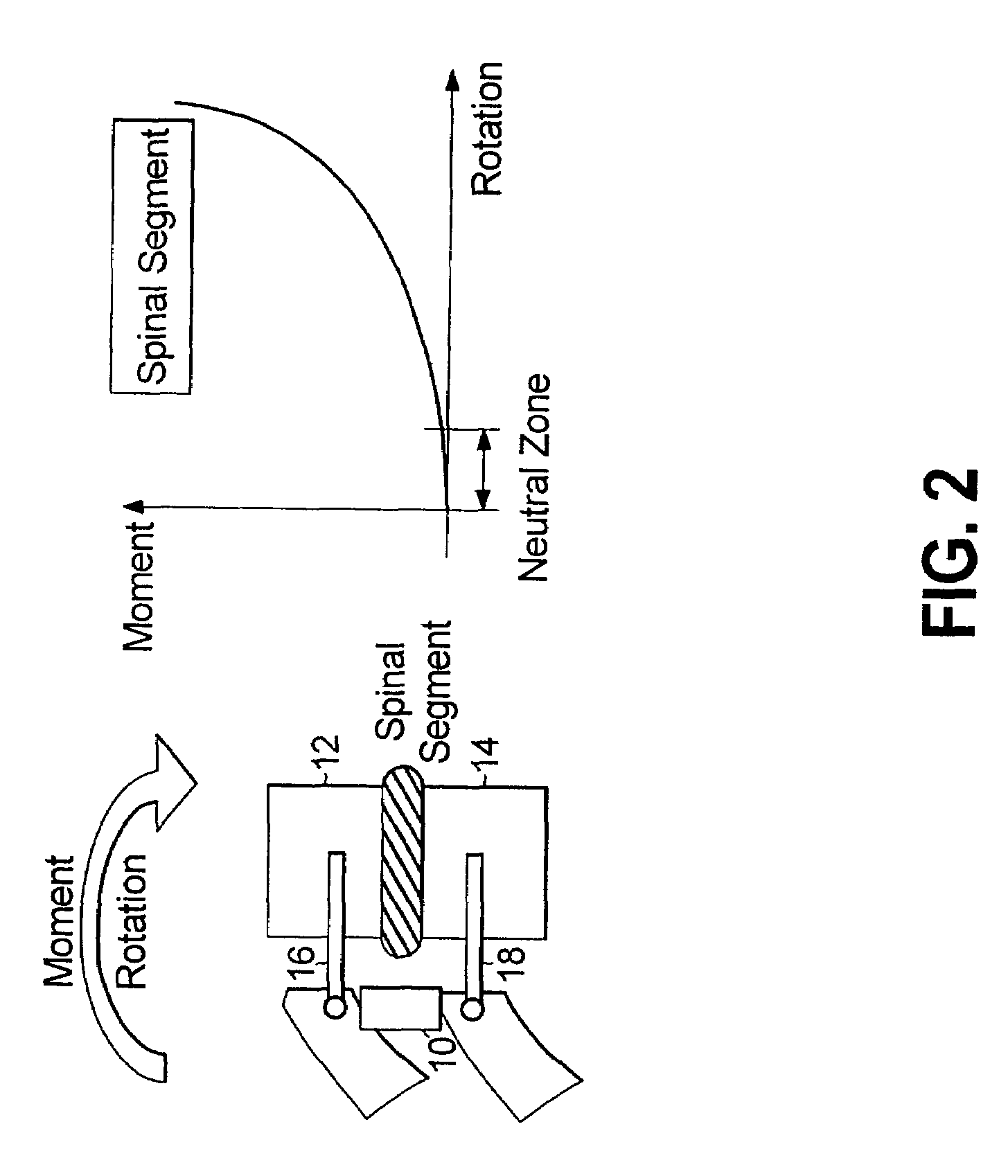
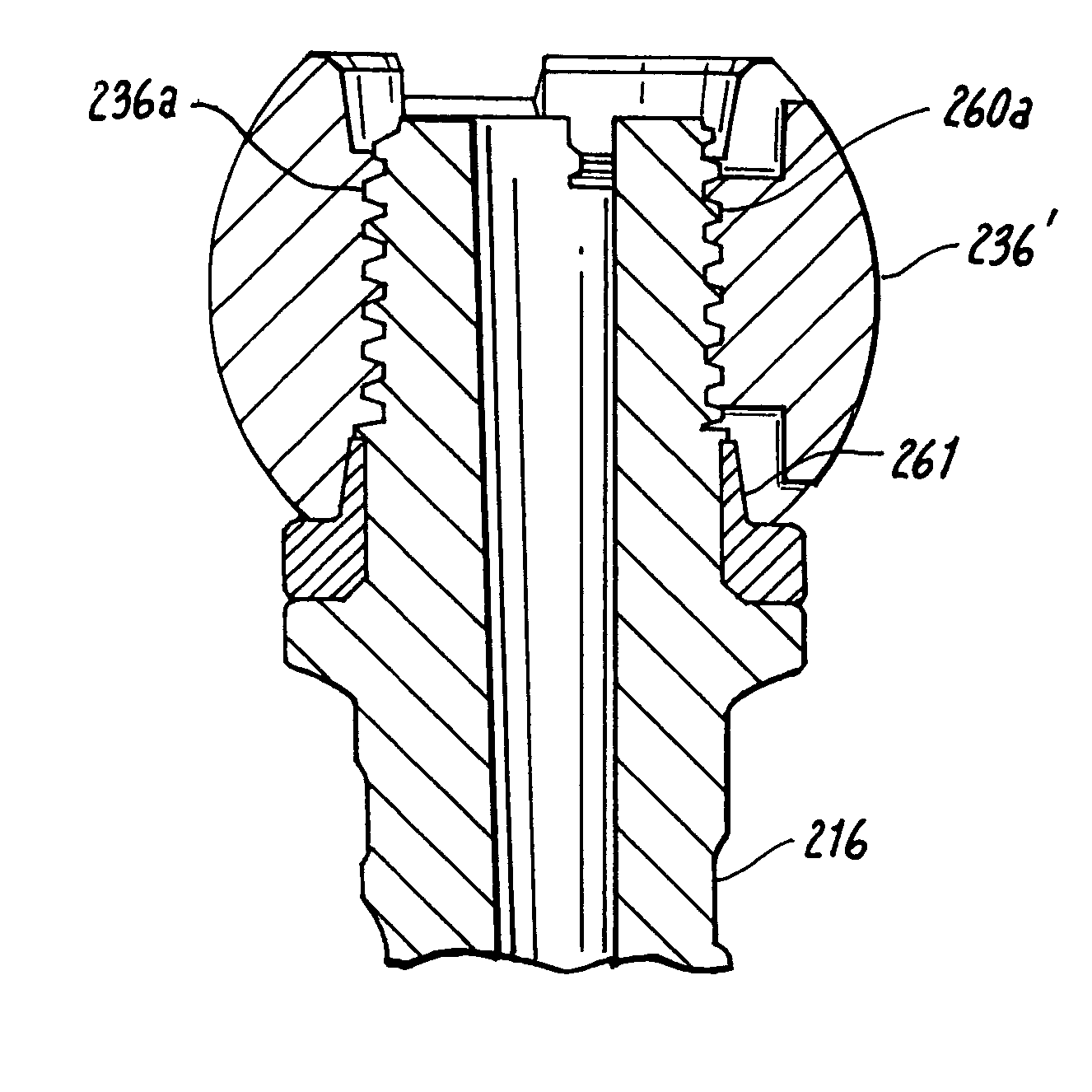
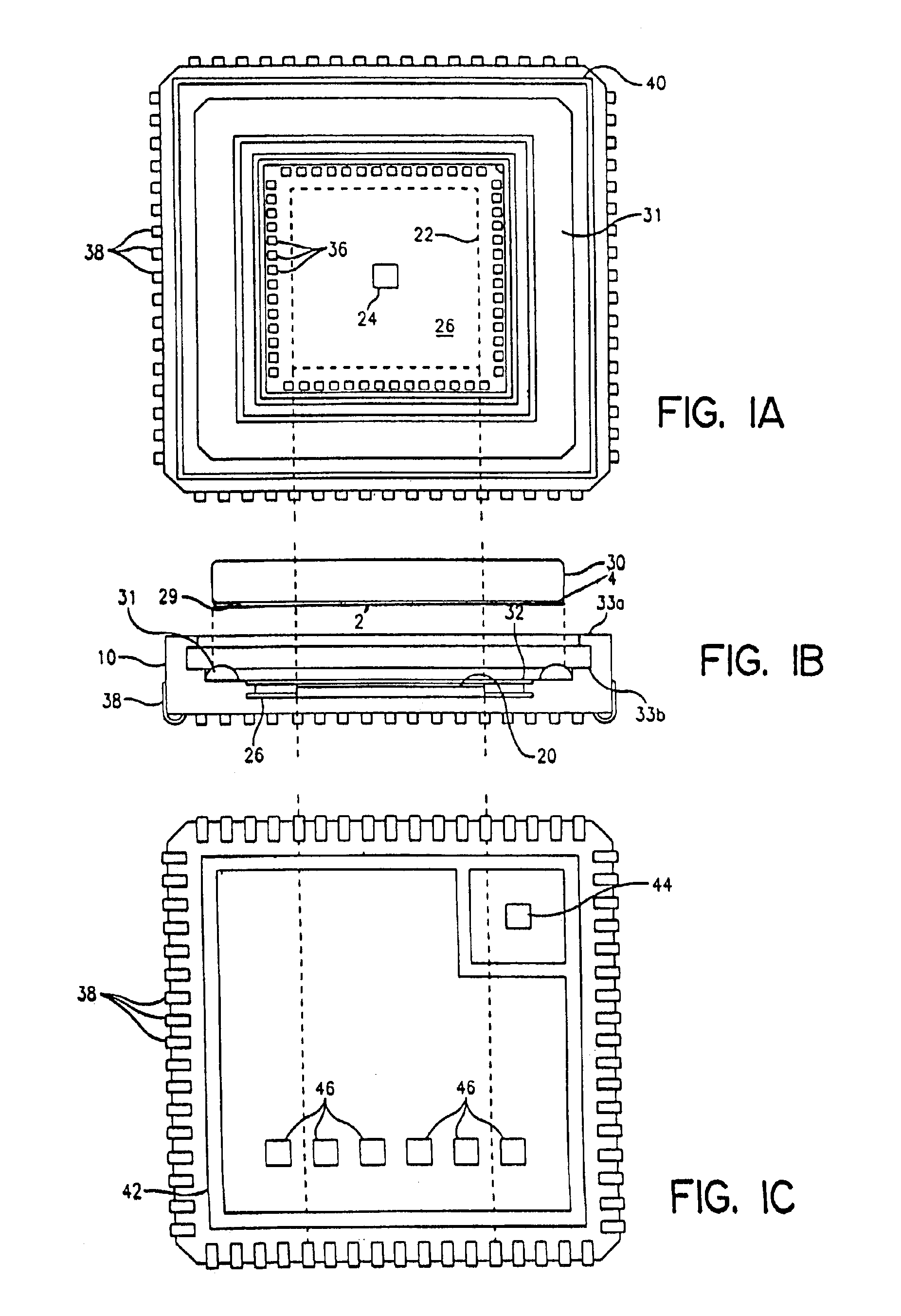
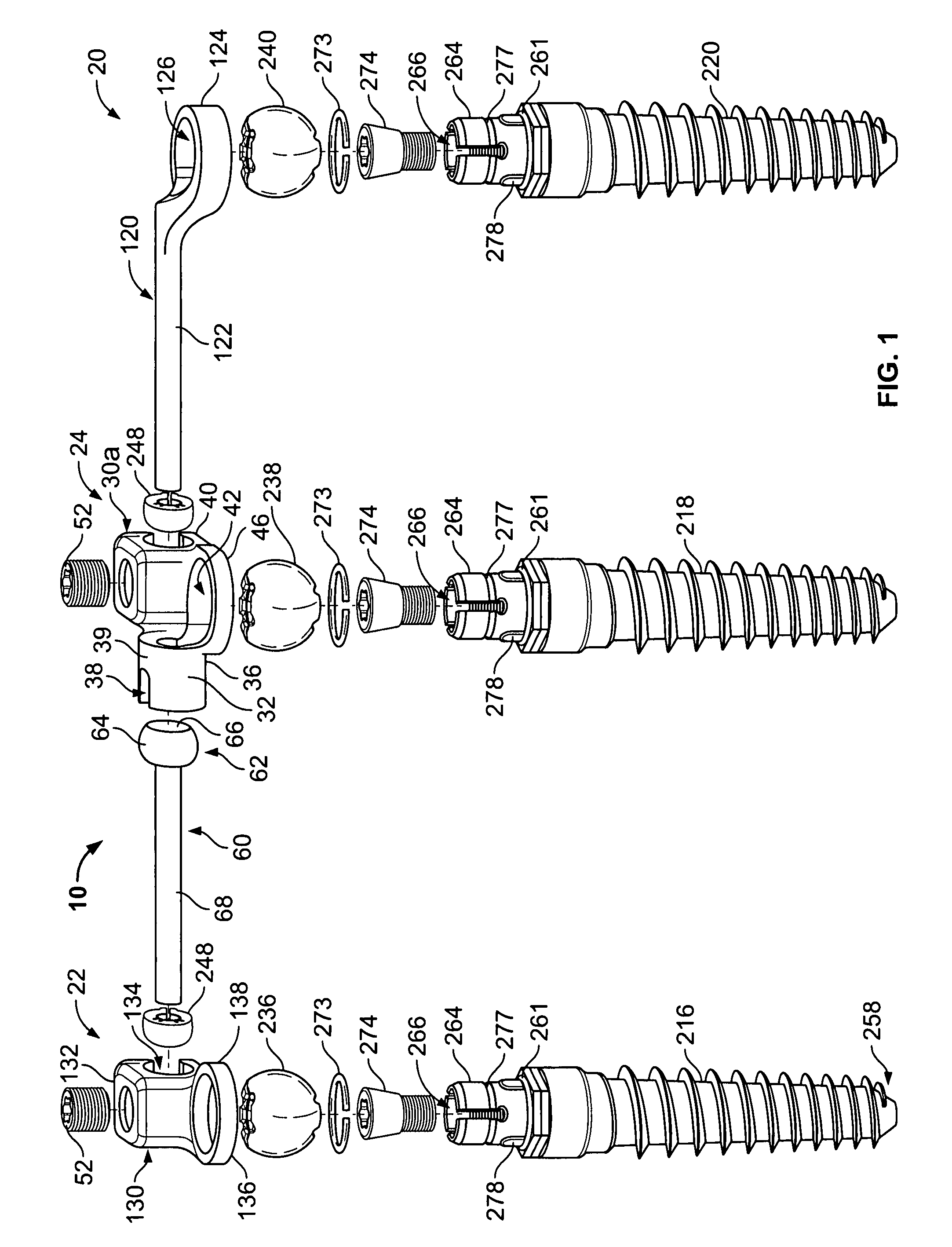
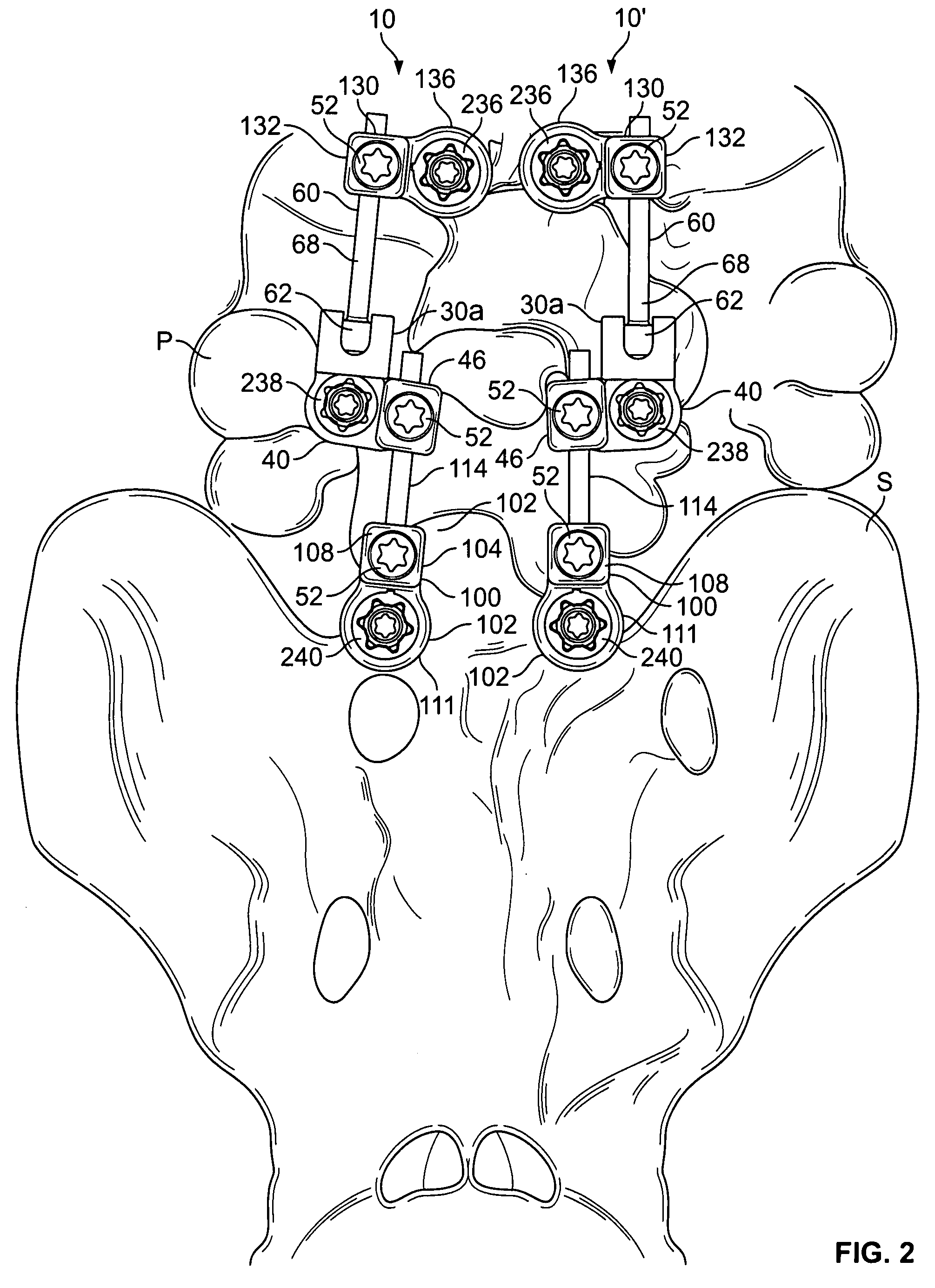
Multi-level spinal stabilization system
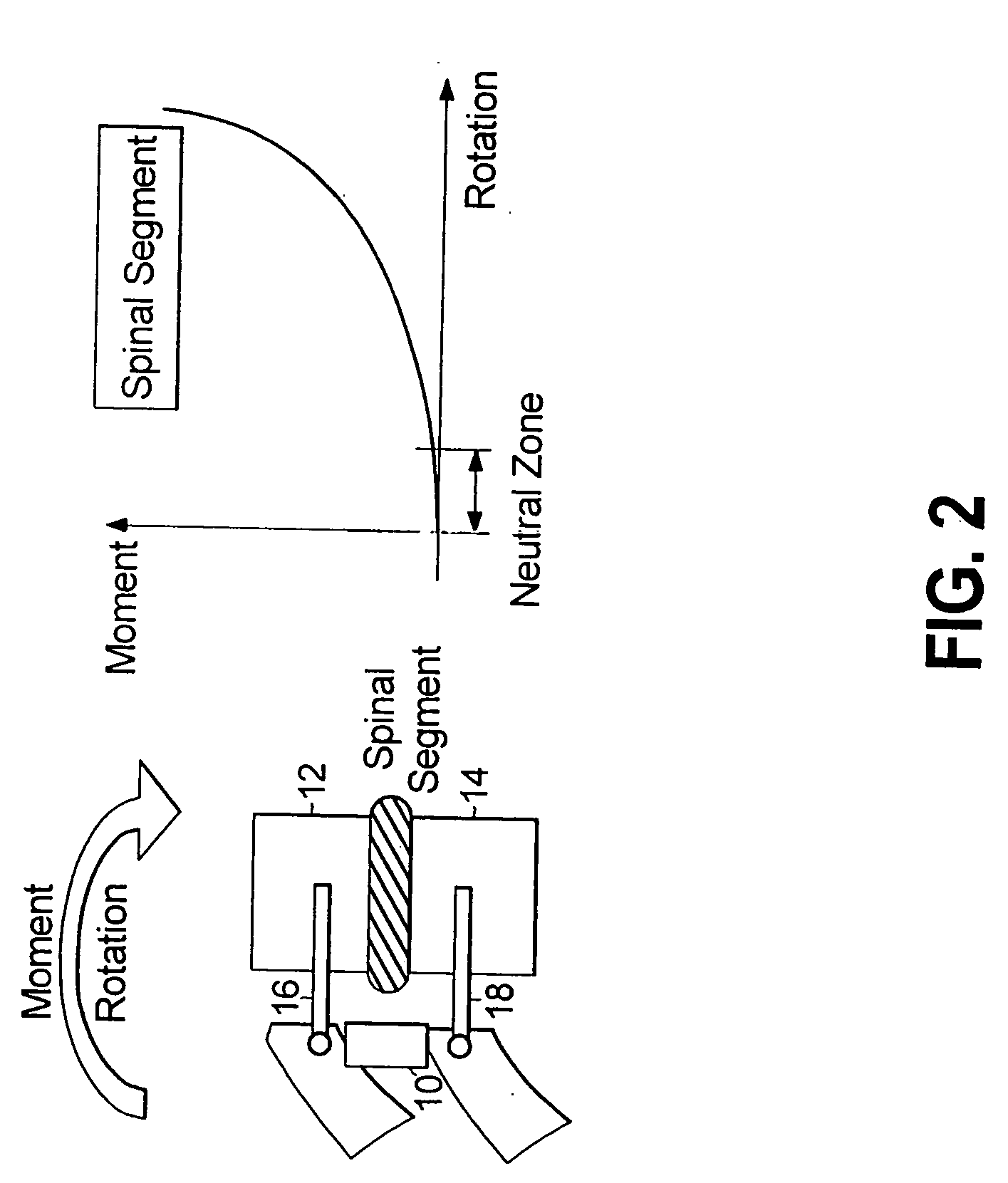
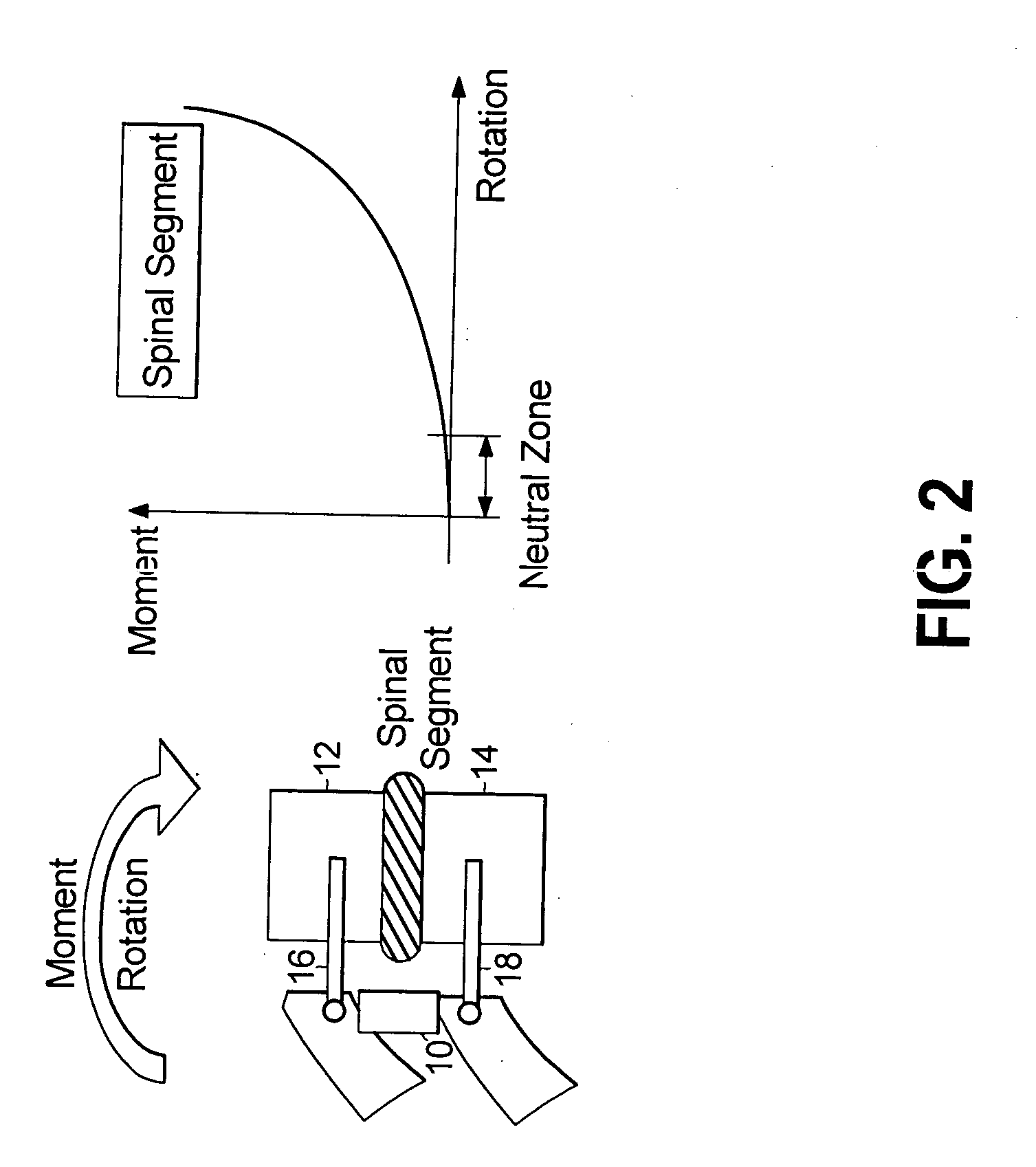
ActiveUS20080312692A1Clinically efficacious resultEasy to installSuture equipmentsInternal osteosythesisRotational freedomUniversal joint
Multi-level spinal stabilization devices, systems and methods are provided that include at least one multi-level connector, one elongated member with an enlarged head, at least one pedicle screw, and at least one mechanism that supports three degrees of rotational freedom relative to both the elongated member and the pedicle screw each. The mechanism may include universal joint mechanisms or ball and socket mechanisms. In the case of the ball and socket mechanisms, the enlarged head of the elongated member cooperates with a first socket member of the multi-level connector to define a dynamic junction that allows the socket member to move relative to the enlarged head of the elongated member while remaining engaged therewith.
Owner:RACHIOTEK
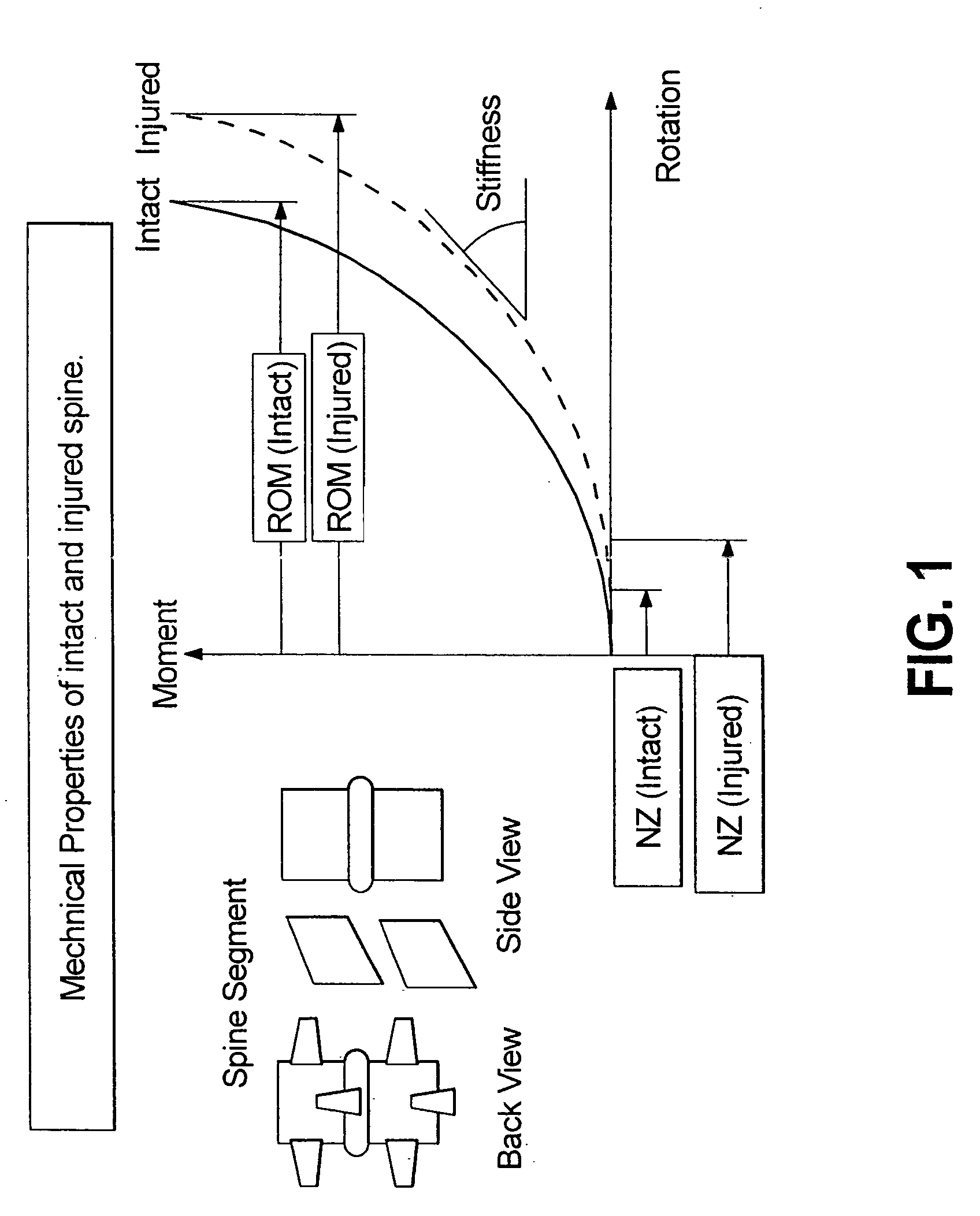
Systems and methods accommodating relative motion in spine stabilization
InactiveUS20050182409A1The result is validEase of installation and in applicationSuture equipmentsInternal osteosythesisUniversal jointEngineering
A motion interface structure for use with a pedicle screw is provided, the motion interface structure defining a central passage having an internal face. A helical thread is formed on at least a portion of the internal face of the central passage. The motion interface element is designed to cooperate with an upstanding region of a pedicle screw. The upstanding region includes a threaded region that is adapted to threadingly engage the helical thread associated with the motion interface element. The motion interface element may take the form of a spherical element or a universal joint mechanism. The pedicle screw and motion interface element may be incorporated into a spinal stabilization system that includes one or more additional pedicle screw / motion interface element subassemblies. The spinal stabilization system may also include a dynamic stabilizing element that provides clinically efficacious results.
Owner:RACHIOTEK
Pedicle screw devices, systems and methods having a preloaded set screw
InactiveUS20050177164A1The result is validEase of installation and in applicationSuture equipmentsInternal osteosythesisSet screwPedicle screw fixation
A pedicle screw assembly is provided that includes a pedicle screw and a preloaded set screw. The set screw is preloaded in a threaded, central aperture formed in the head region of the pedicle screw. An interference is advantageously formed on the set screw to prevent dislodgement of the set screw, e.g., during shipment and / or clinical placement of the pedicle screw. An upwardly extending collet is generally formed in the head region of the pedicle screw, the collet being sized to receive a spherical element therearound. Advancement of the set screw relative to the pedicle screw secures the spherical element relative to the pedicle screw. The spherical element typically includes a socket member that cooperates with a dynamic stabilizing member. The pedicle screw assembly and dynamic stabilizing member are advantageously used as part of a spinal stabilization system to provide clinically efficacious results.
Owner:APPLIED SPINE TECH
Method and system for processing regions of interest for objects comprising biological material
InactiveUS20040085443A1Easy to analyzeGood for comparisonImage enhancementImage analysisTissue microarrayBiological materials
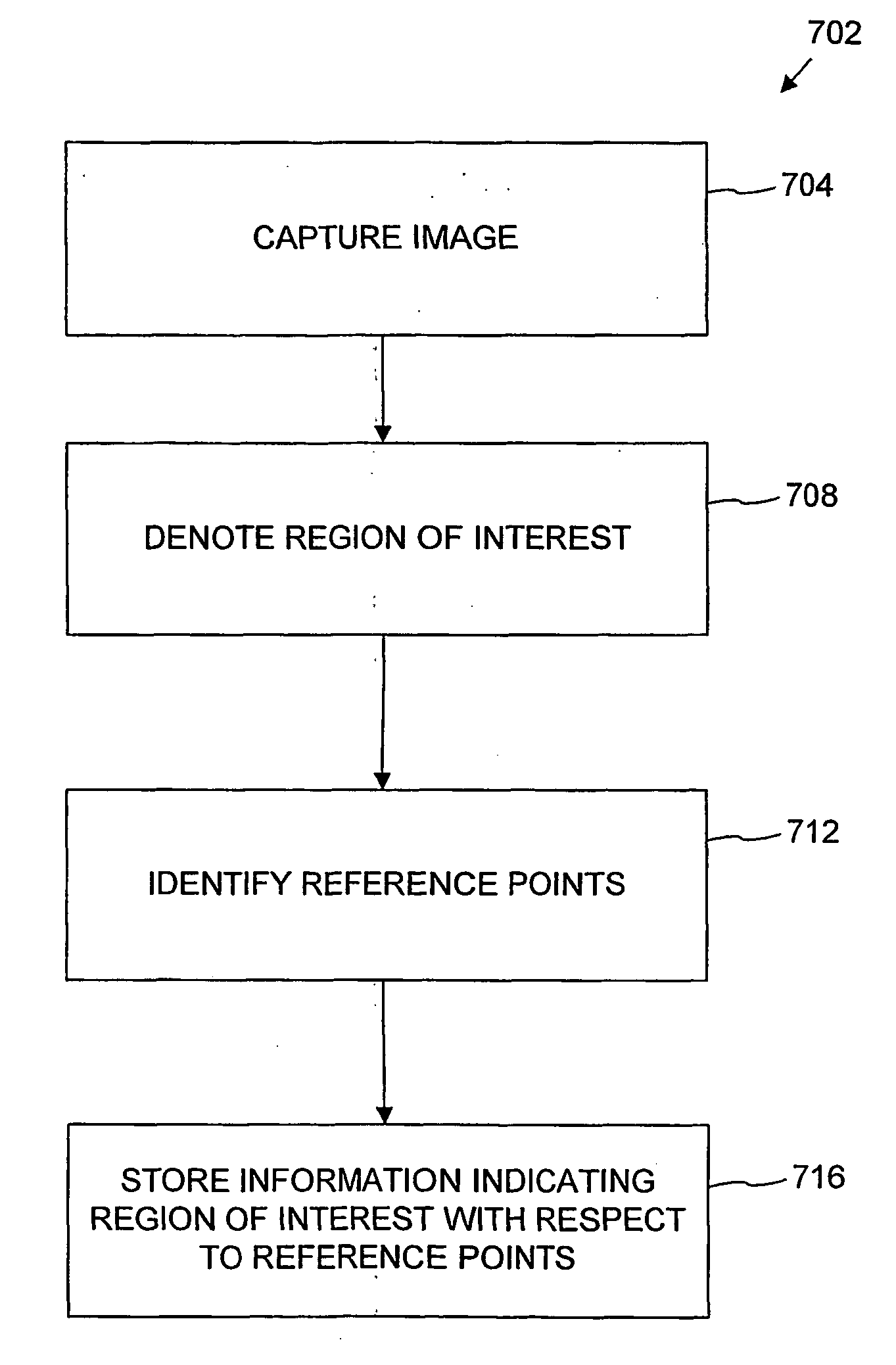
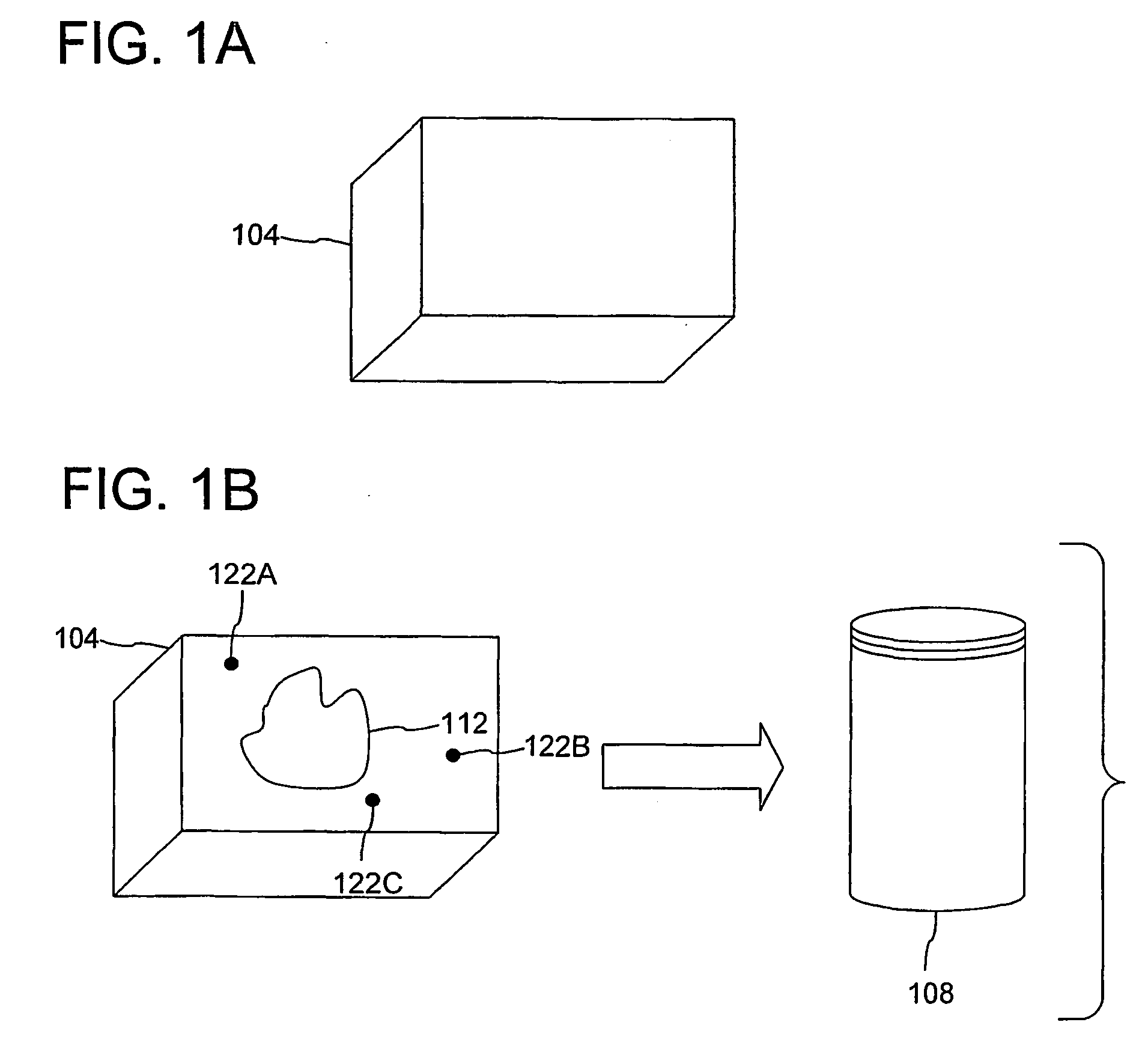
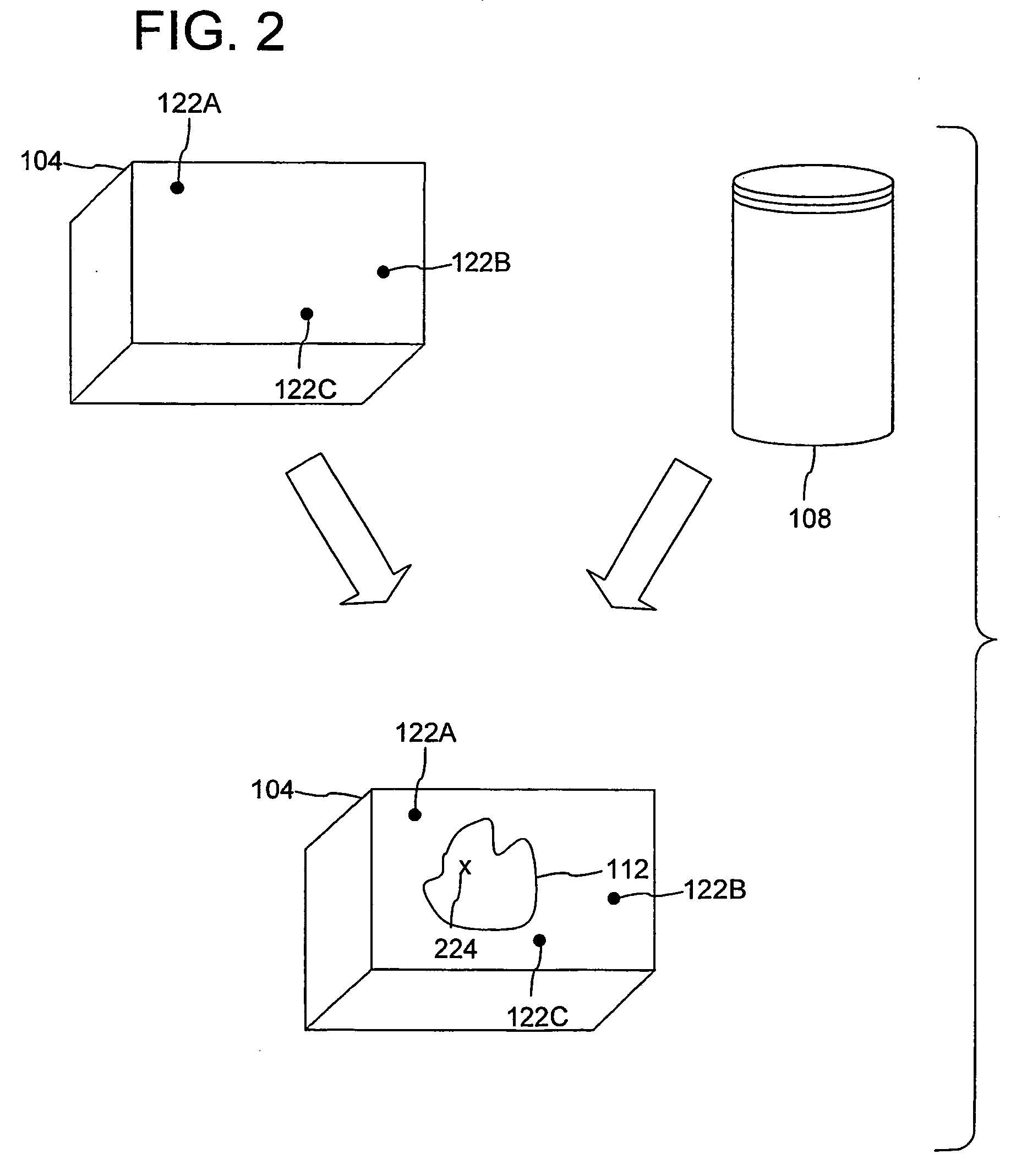
A method and apparatus are disclosed for processing regions of interest for objects comprising biological material. A region of interest can be denoted for a physical object and information indicating the region of interest can be stored in a computer-readable medium for later retrieval. Subsequently, when the object is retrieved, the information indicating the region of interest can be used to generate information specifying a physical location within the region of interest. An operation can then be performed on the physical location within the region of interest. Reference pints within the object can assist in regeneration of the region of interest, and the reference points can be arranged in such a fashion that processing can take rotation of the object into account. The invention includes various features advantageous for constructing tissue microarrays.
Owner:GOVERNMENT OF THE UNITED STATES OF AMERICAS AS REPRESENTED BY THE SEC OF THE DEPT OF HEALTH & HUMAN SERVICES THE +1
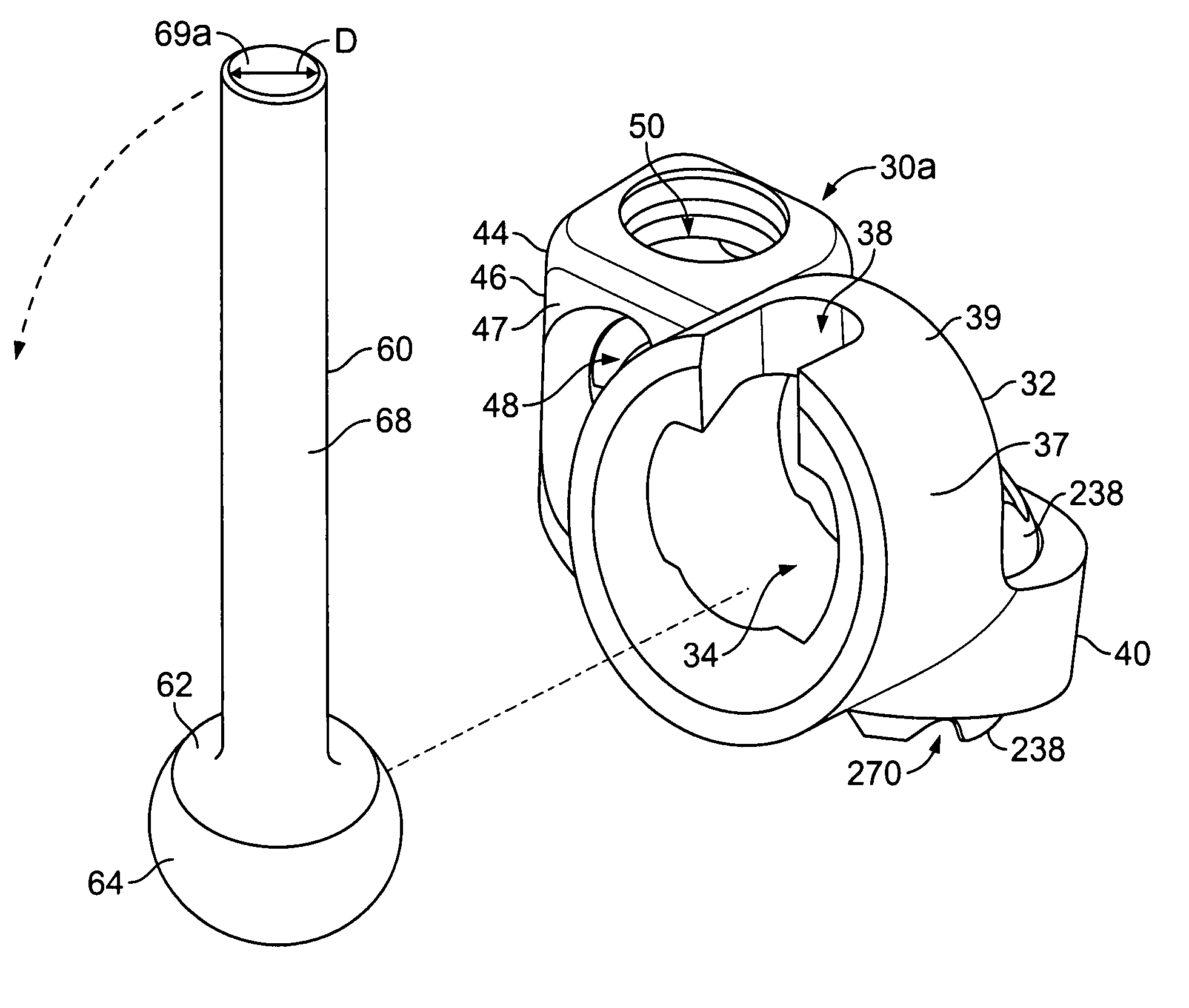
Mounting mechanisms for pedicle screws and related assemblies
ActiveUS7615068B2The result is validEase of installation and in applicationSuture equipmentsInternal osteosythesisSet screwEngineering
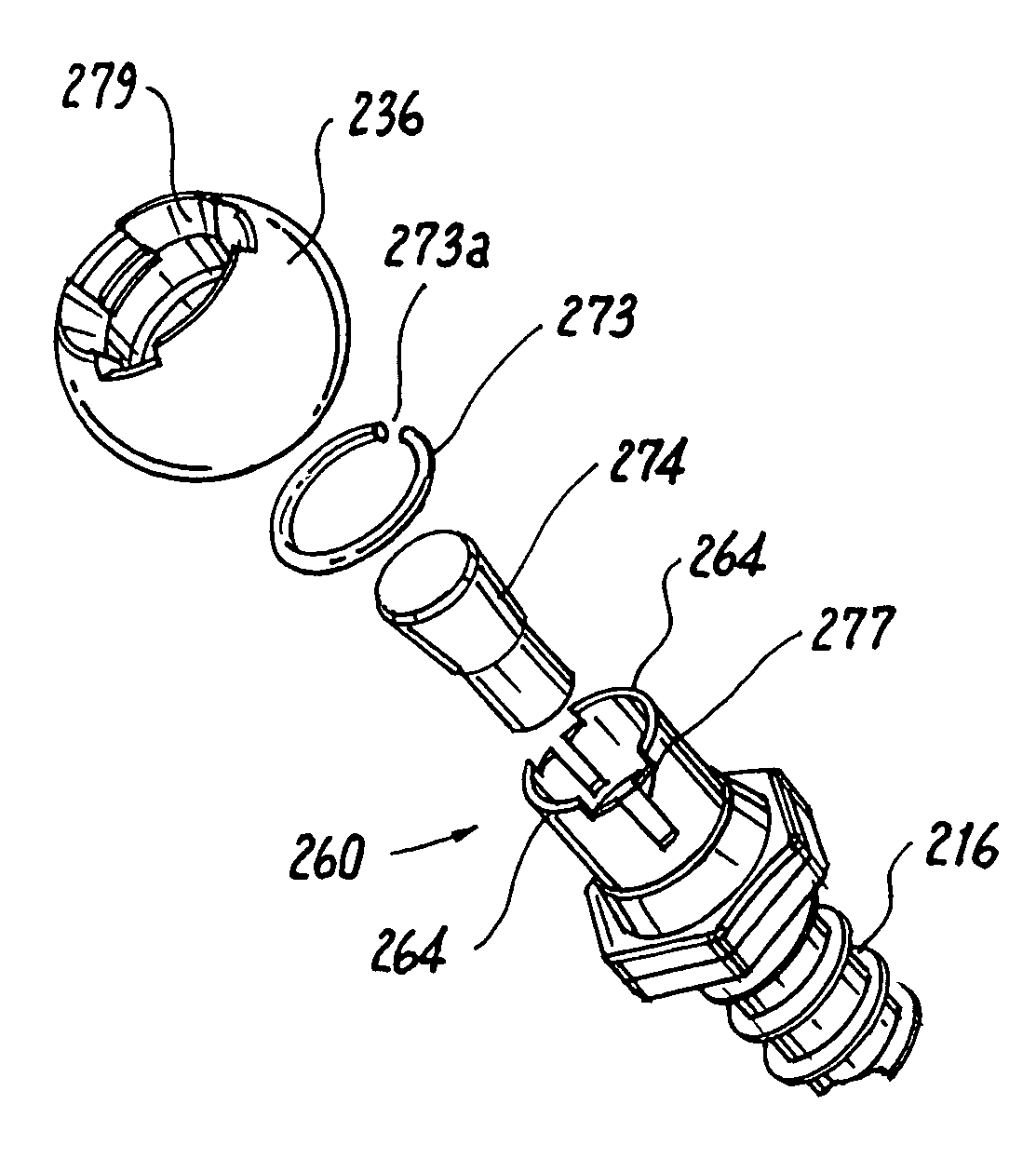
A pedicle screw is provided that includes an upwardly extending collet. The collet may include downwardly extending slots that define deflectable segments therebetween. When a spherical element or other structure, e.g., a non-dynamic stabilizing element, is positioned around the collet, introduction of a set screw causes outward deflection of the upstanding segments into engagement with the spherical element. A snap ring may be interposed between the collet and the spherical element to facilitate positioning therebetween. In an alternative embodiment, a non-slotted collet is employed. In such embodiment, the collet and the spherical element may be threadingly engaged and may include a snap ring therebetween. The pedicle screw subassemblies may be incorporated into a spinal stabilization system which may include a dynamic stabilizing member to provide clinically efficacious results.
Owner:RACHIOTEK
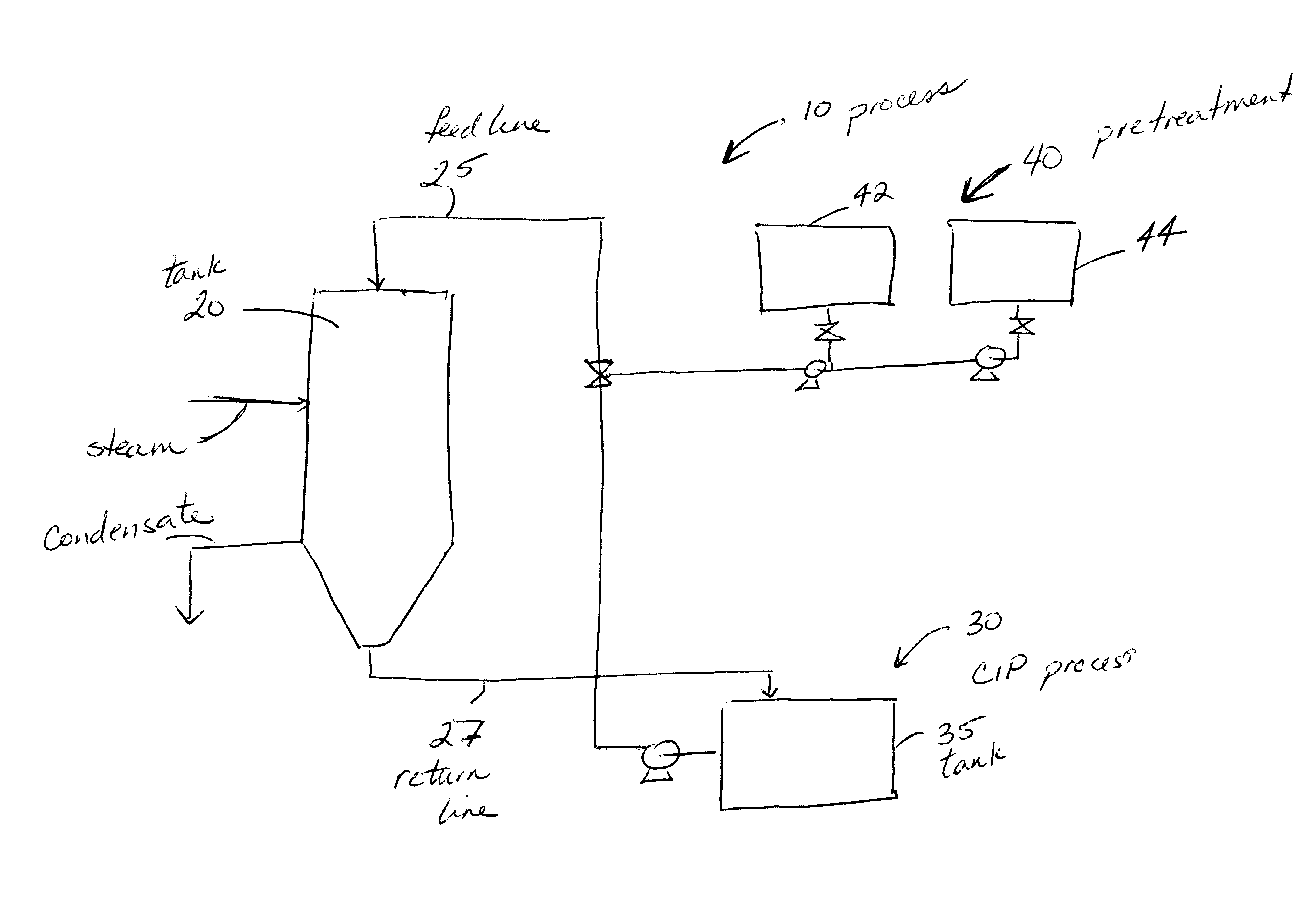
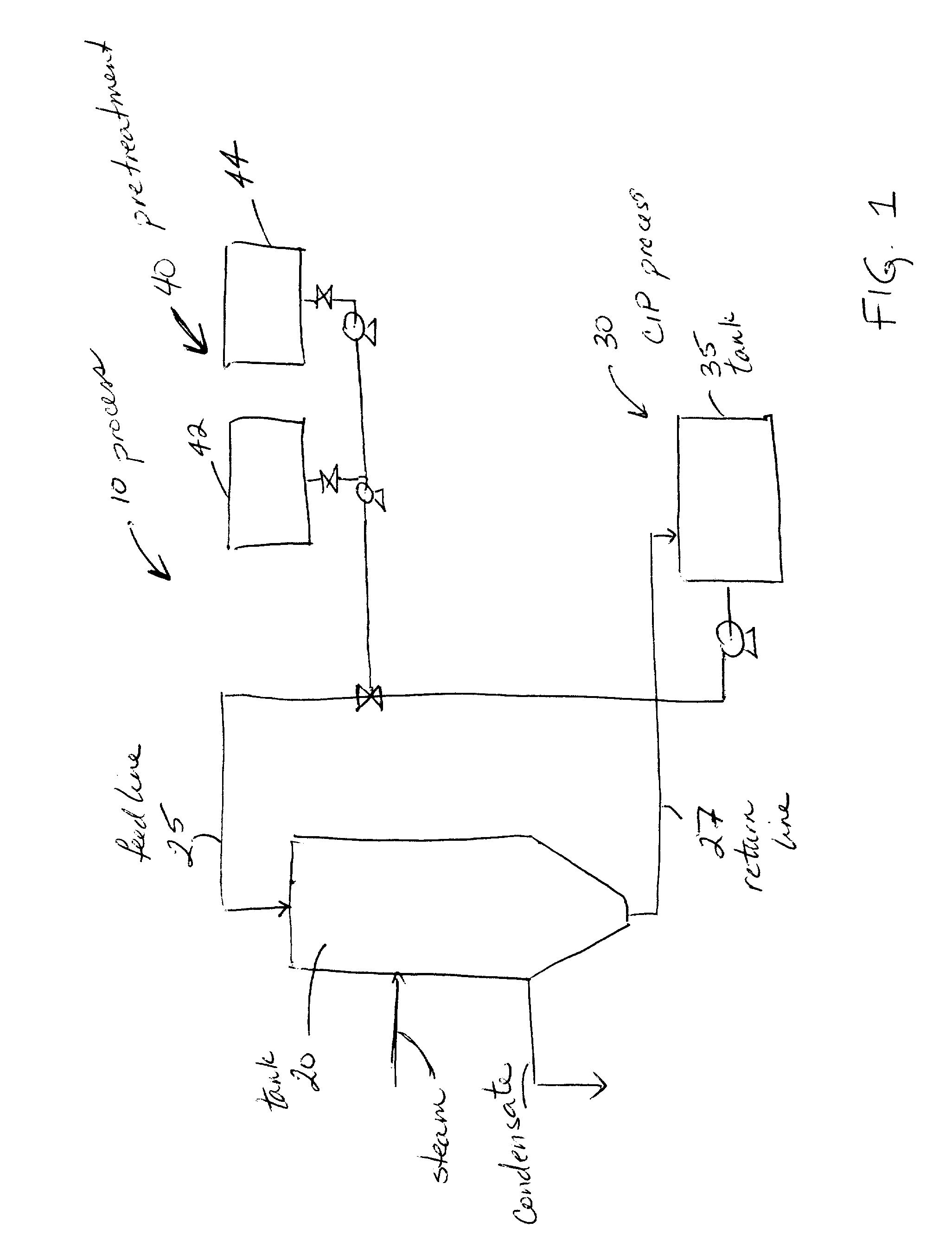
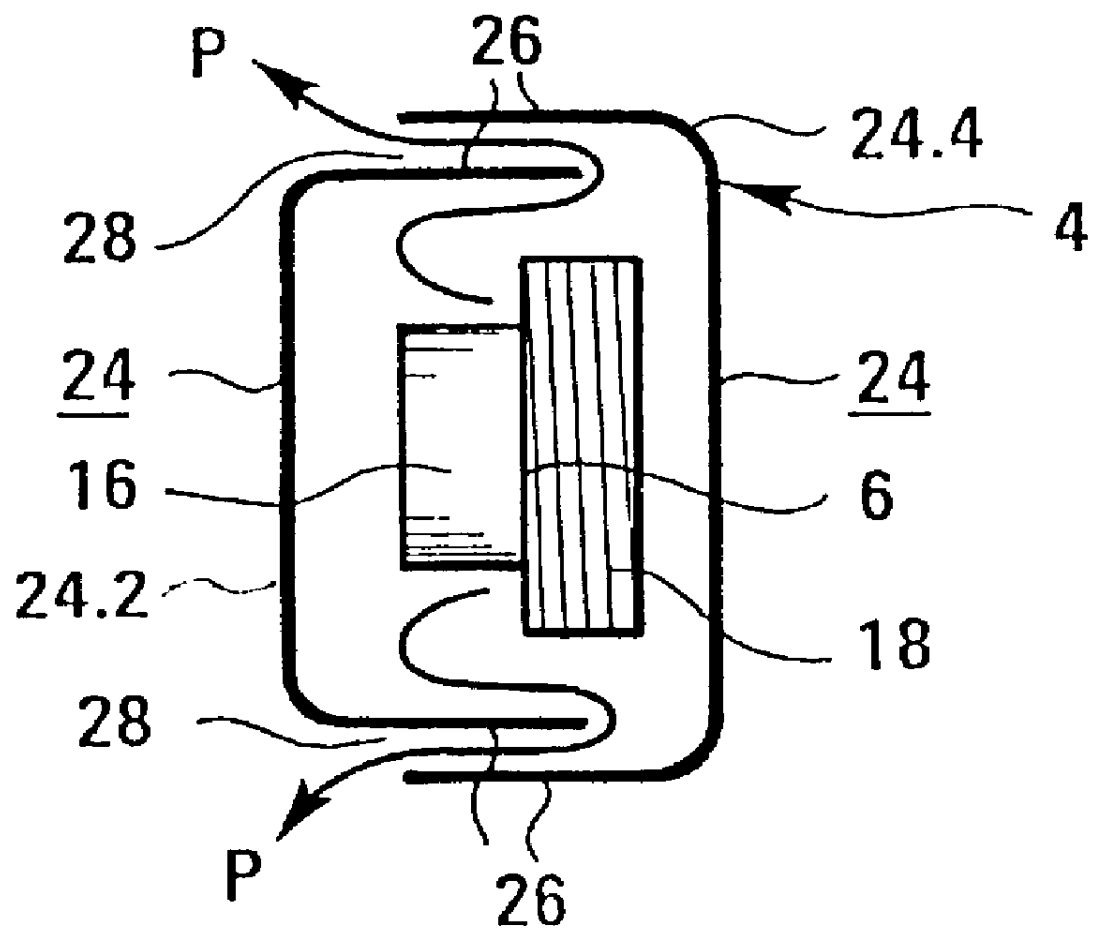
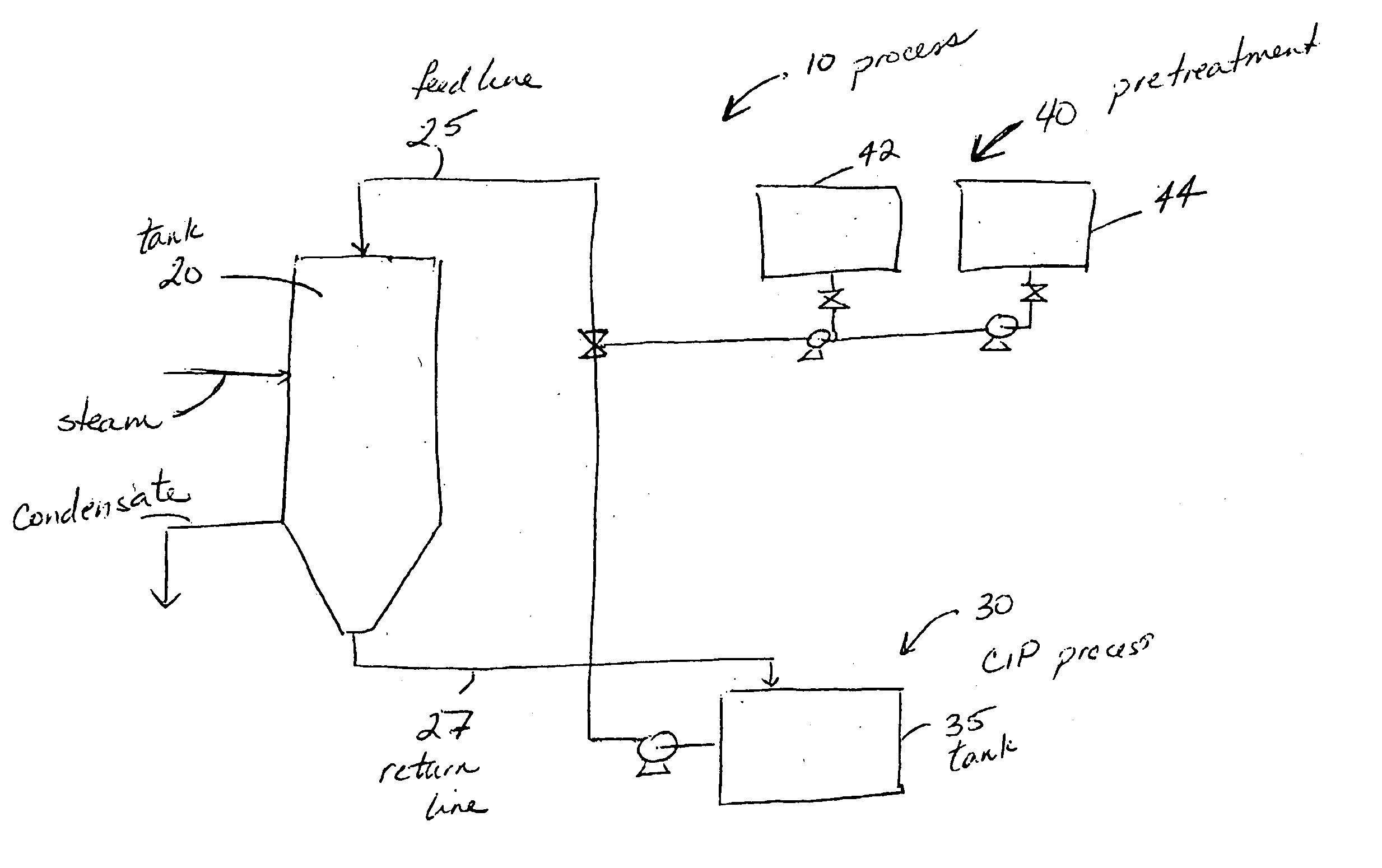
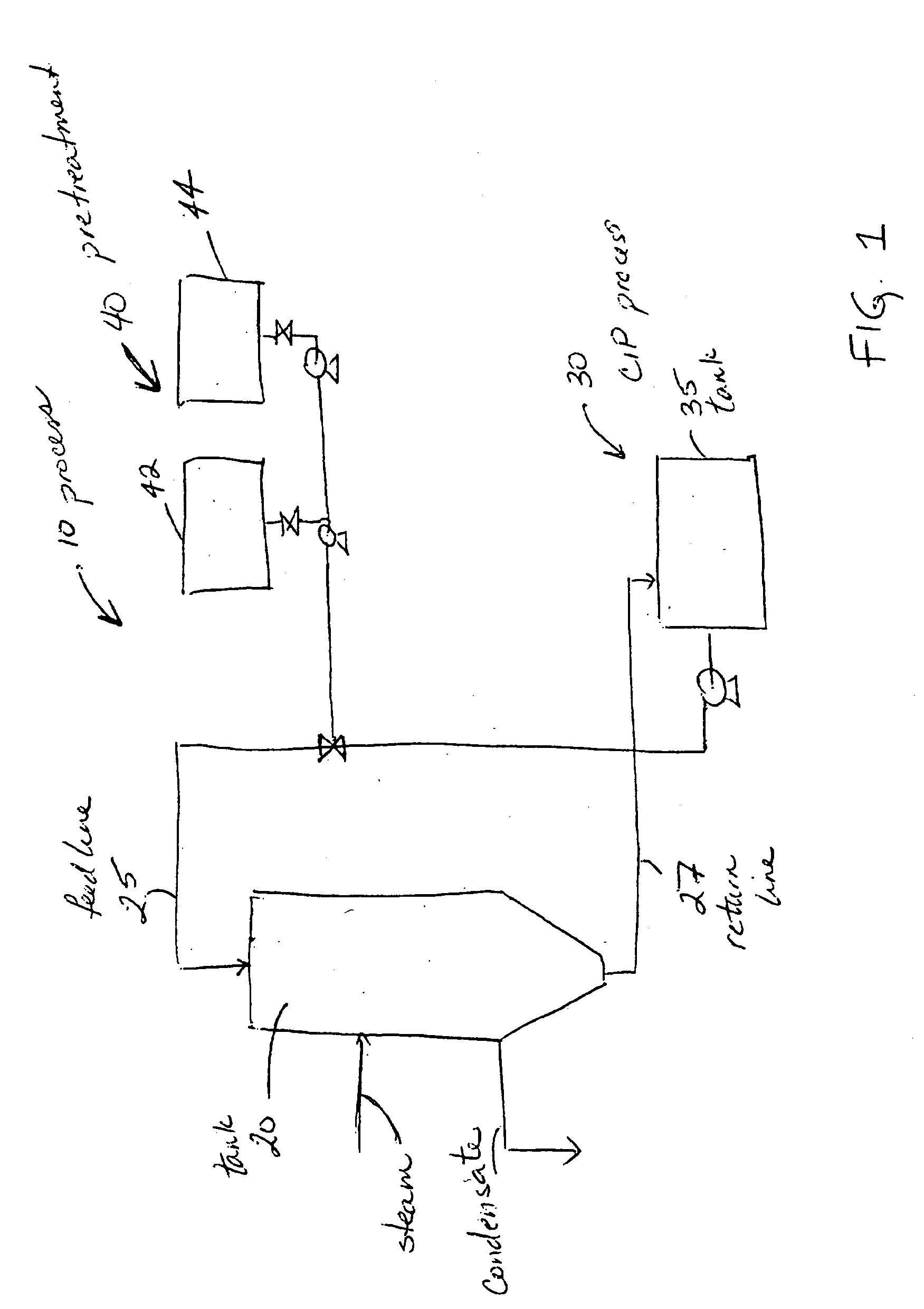
Methods for cleaning industrial equipment with pre-treatment
InactiveUS20080105282A1The result is validHigh degree of softeningSurface-active detergent compositionsNon-surface-active detergent compositionsAdditive ingredientIndustrial equipment
A method of cleaning equipment such as heat exchangers, evaporators, tanks and other industrial equipment using clean-in-place procedures and a pre-treatment solution prior to the conventional CIP cleaning process. The pre-treatment step improves the degree of softening of the soil, and thus facilitates its removal. The pre-treatment solution can be a strong acidic solution, a strong alkaline solution, or comprise a penetrant. A preferred strong acidic solution is an acid peroxide solution. In some embodiments, the pre-treatment may include no strong alkali or acid ingredient; rather, the penetrant provides acceptable levels of pre-treatment.
Owner:ECOLAB USA INC
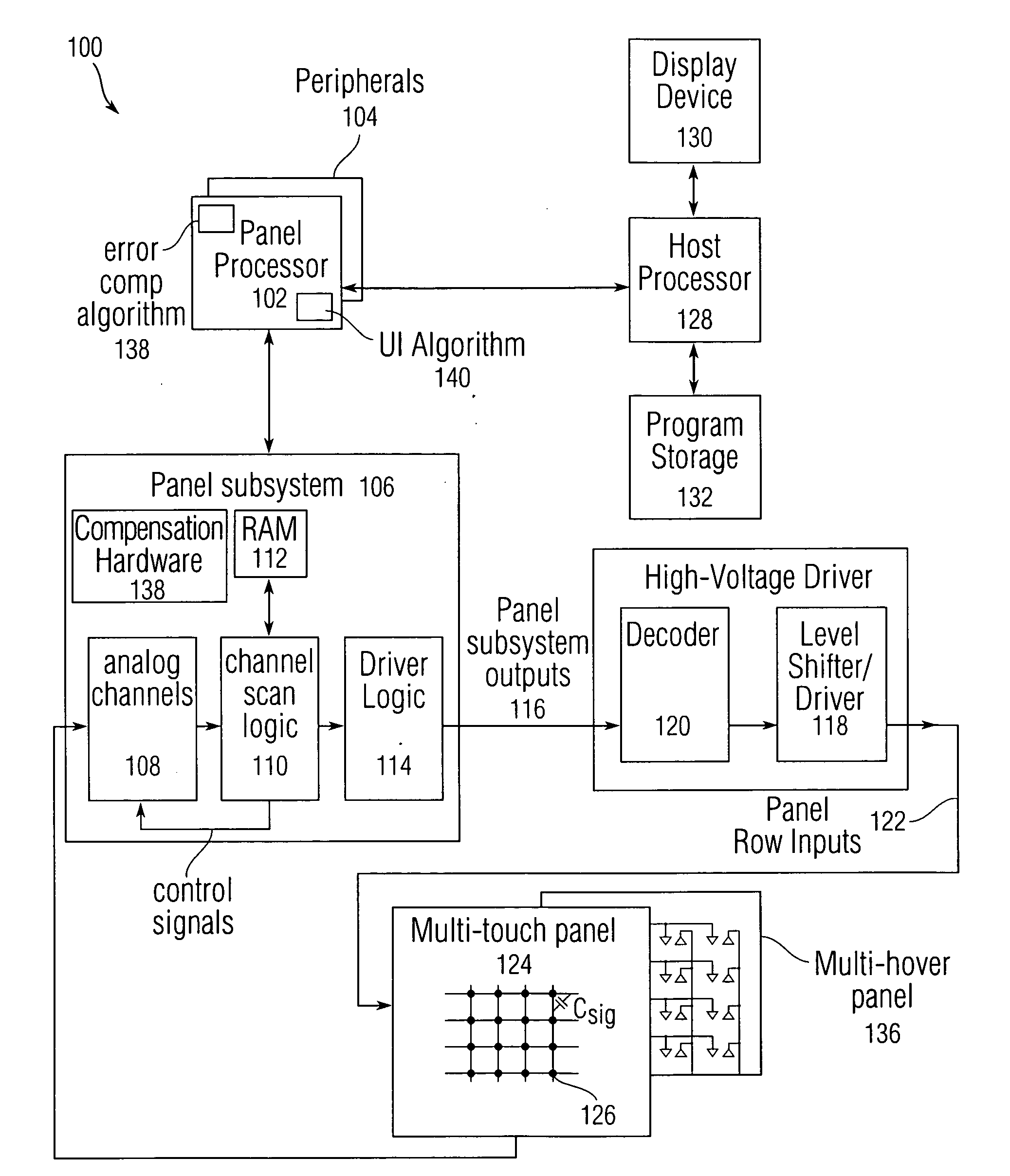
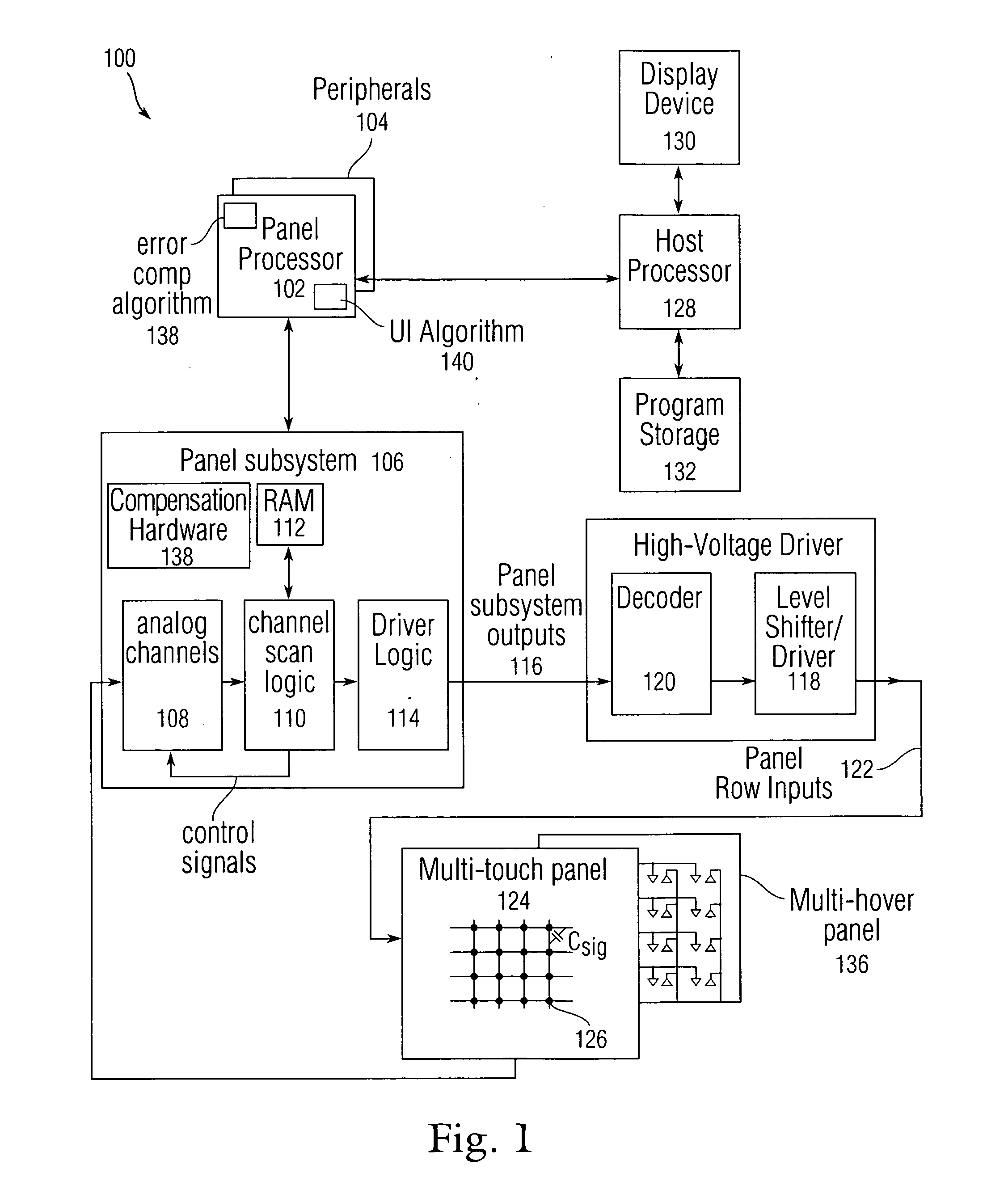
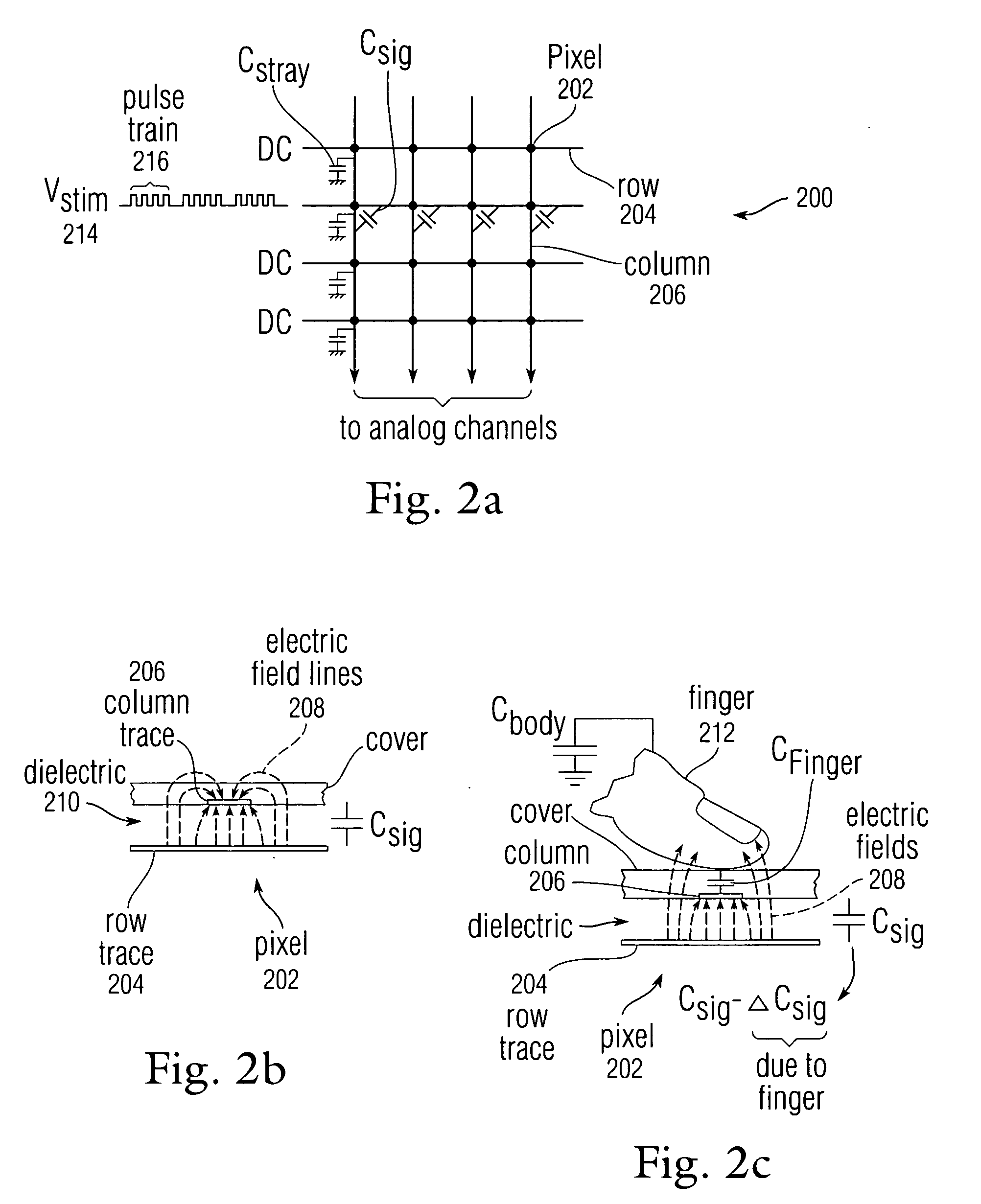
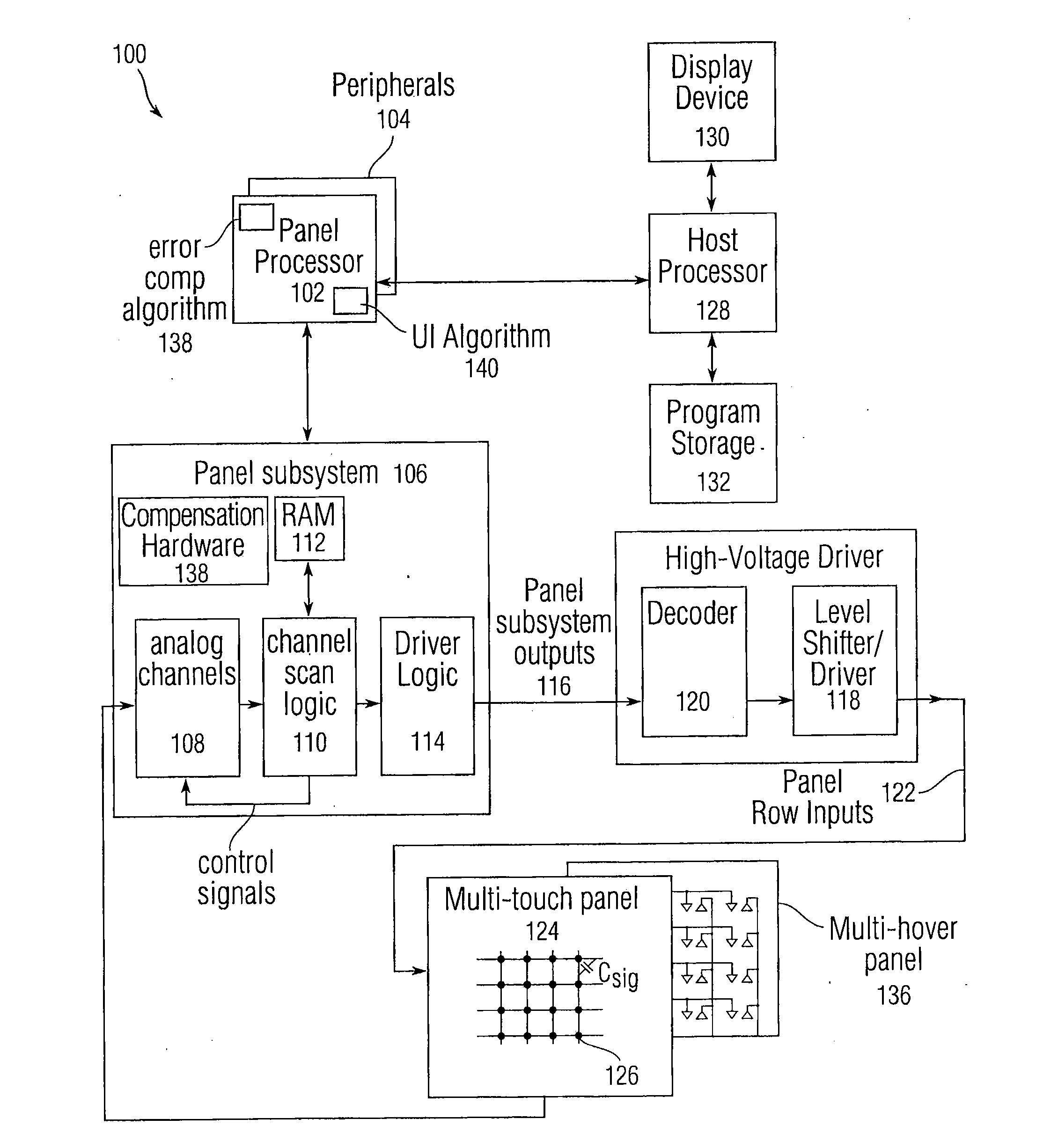
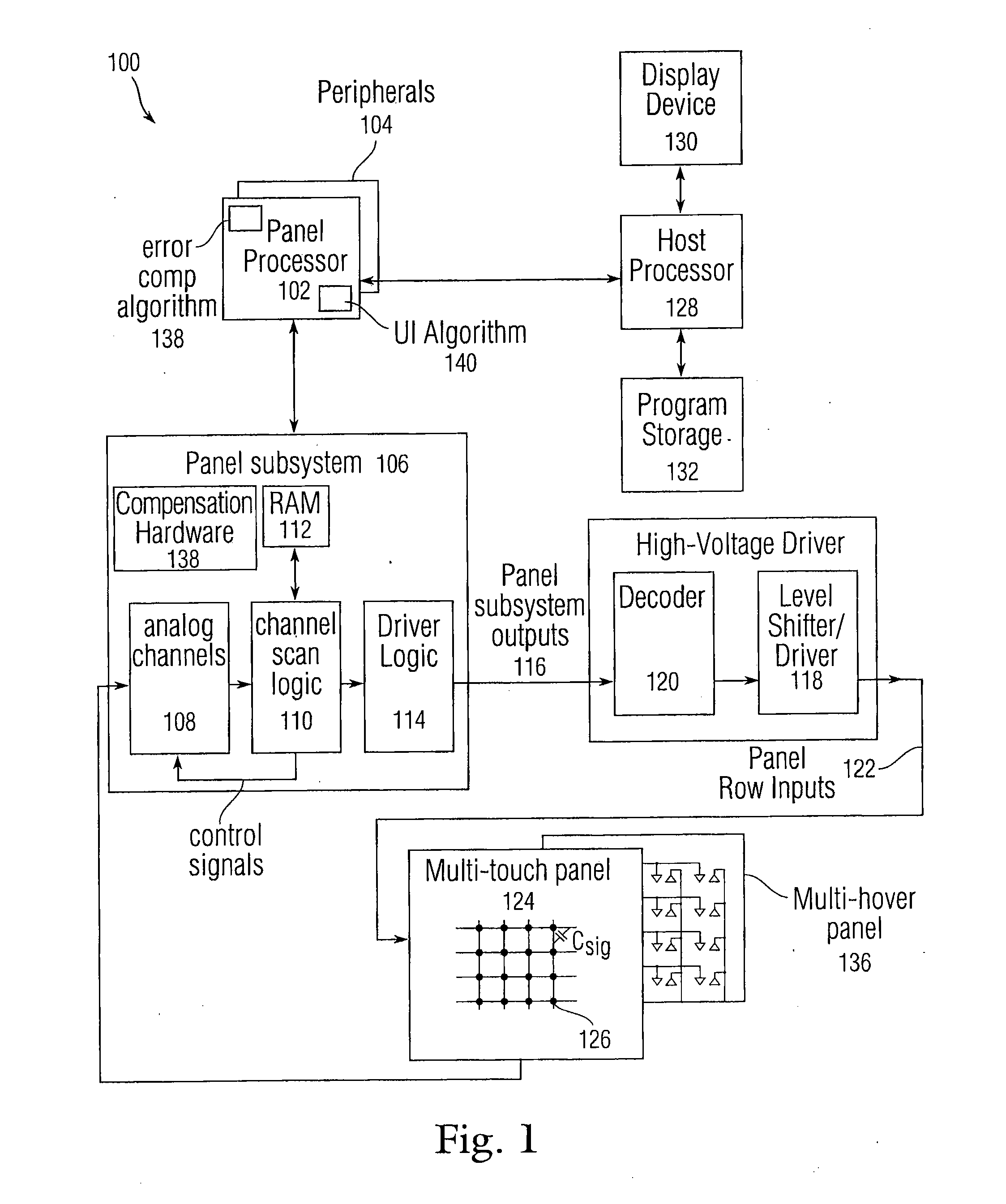
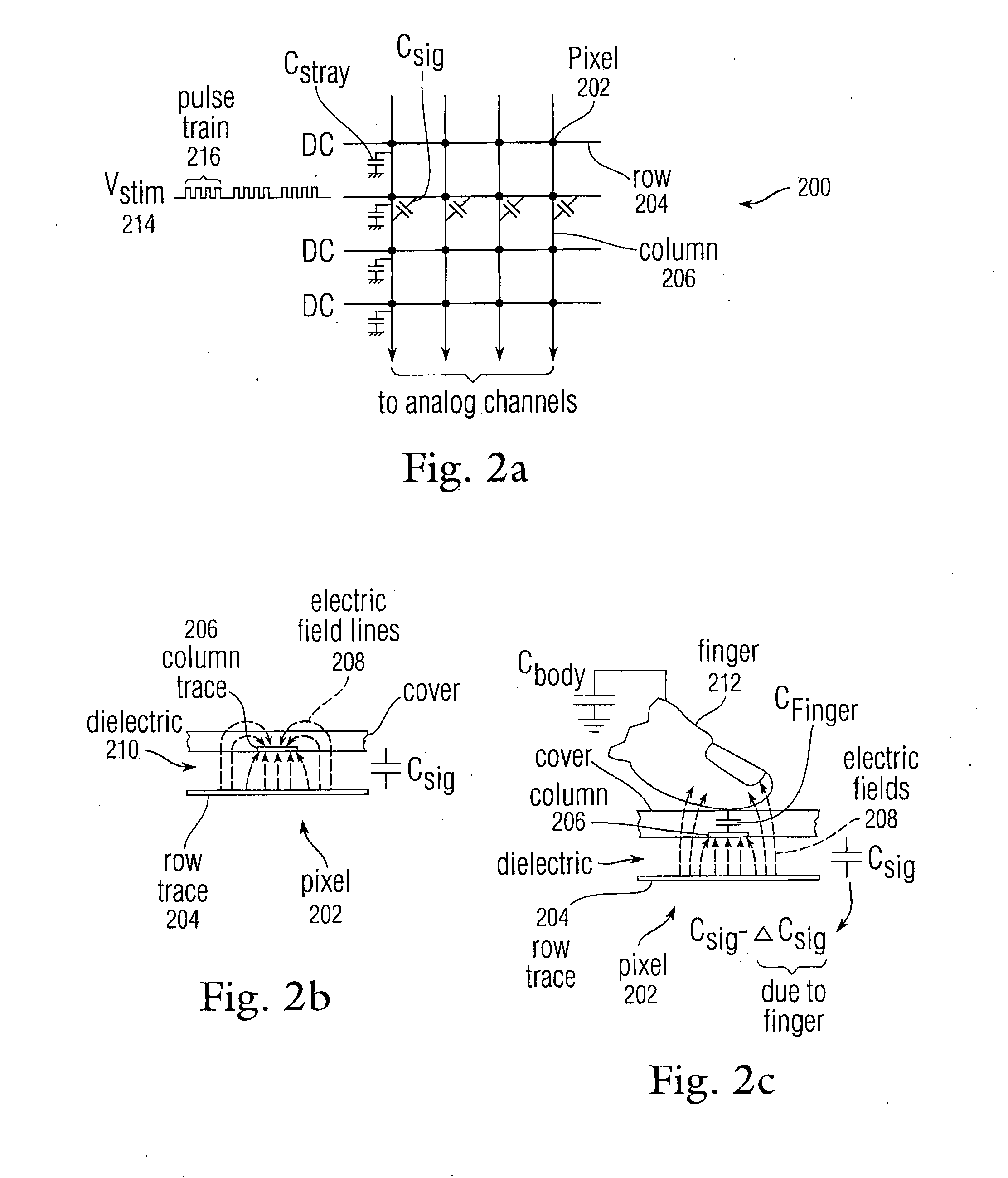
Full scale calibration measurement for multi-touch surfaces
ActiveUS20080158176A1Easy to eliminateLow costInput/output processes for data processingFull scaleNon-volatile memory
Normalization of regions of a sensor panel capable of detecting multi-touch events, or a sensor panel capable of detecting multi-hover events, is disclosed to enable each sensor in the sensor panel to trigger a virtual button in a similar manner, given the same amount of touch or hover. Each sensor produces an output value proportional to the level or amount of touch or hover. However, due to processing, manufacturing and physical design differences, the sensor output values can vary from region to region or panel to panel for a given amount of touch or hover. To normalize the sensor output values across regions, gain and offset information can be obtained in advance, stored in nonvolatile memory, and later used to normalize the sensor output values so that all regions in the sensor panel can trigger virtual buttons similarly, providing a uniform “response function” at any location on the sensor panel.
Owner:APPLE INC
Pedicle screw assembly with bearing surfaces
InactiveUS7635379B2The result is validEase of installation and in applicationSuture equipmentsInternal osteosythesisSpinal columnMedicine
Owner:RACHIOTEK
Full scale calibration measurement for multi-touch surfaces
ActiveUS20110037735A1Easy to eliminateLow costInput/output processes for data processingEngineeringFull scale
Normalization of regions of a sensor panel capable of detecting multi-touch events, or a sensor panel capable of detecting multi-hover events, is disclosed to enable each sensor in the sensor panel to trigger a virtual button in a similar manner, given the same amount of touch or hover. Each sensor produces an output value proportional to the level or amount of touch or hover. However, due to processing, manufacturing and physical design differences, the sensor output values can vary from region to region or panel to panel for a given amount of touch or hover. To normalize the sensor output values across regions, gain and offset information can be obtained in advance, stored in nonvolatile memory, and later used to normalize the sensor output values so that all regions in the sensor panel can trigger virtual buttons similarly, providing a uniform “response function” at any location on the sensor panel.
Owner:APPLE INC
Method for synthesizing solids such as diamond and products produced thereby
InactiveUS6342195B1Enhanced interactionIncreasing amount of possibleUltra-high pressure processesDiamondHydrogenBoron nitride
The present invention relates generally to methods for the synthesis of various solids such as diamonds, diamonds films, boron nitride and other similar materials. This invention specifically relates to utilizing novel sources of reaction species (e.g., in the case of diamond formation, novel sources of carbon and / or hydrogen and / or seeds) for the manufacture of various materials and the use of such materials for various commercial purposes.
Owner:PENN STATE RES FOUND
Fast byzantine paxos
ActiveUS7620680B1Accurate authenticationProvide securityMultiple digital computer combinationsTransmissionDigital signatureClient-side
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices, and provide a minimum of message delays between receiving a client request and providing a response, when each device within the system verifies the sender of any message it receives, and the propriety of the message. The sender can be verified through message authentication schemes or digital signature schemes. The propriety of a message can be verified by receiving a sufficiently large number of equivalent, properly authenticated messages. If the number of malicious devices is represented by the variable “M”, a sufficient number of equivalent, properly authenticated messages to verify that the message is true can be any number of messages greater than M. Furthermore, to verify that a leader device is not maliciously submitting different proposals to different devices using the same proposal number, a quorum of devices can be required to select a proposal, where a quorum is a sufficiently large number of devices such that any other quorum has, as a majority of its devices, non-malicious devices from the first quorum. Therefore, the distributed computing system can operate properly with M number of malicious failures and F number of total failures, and with a minimum of message delays, if the number of constituent devices in the distributed computing system is greater than 3F+2M. Additionally, if the distributed computing system can revert to a more traditional algorithm if too many devices fail or become malicious, it can use a message-delay-reducing algorithm while having as few as 2Q+F+2M+1 constituent devices, where Q is the number of devices that can fail and still allow the system to use a message-delay-reducing algorithm.
Owner:MICROSOFT TECH LICENSING LLC
Portable hypoxic apparatus
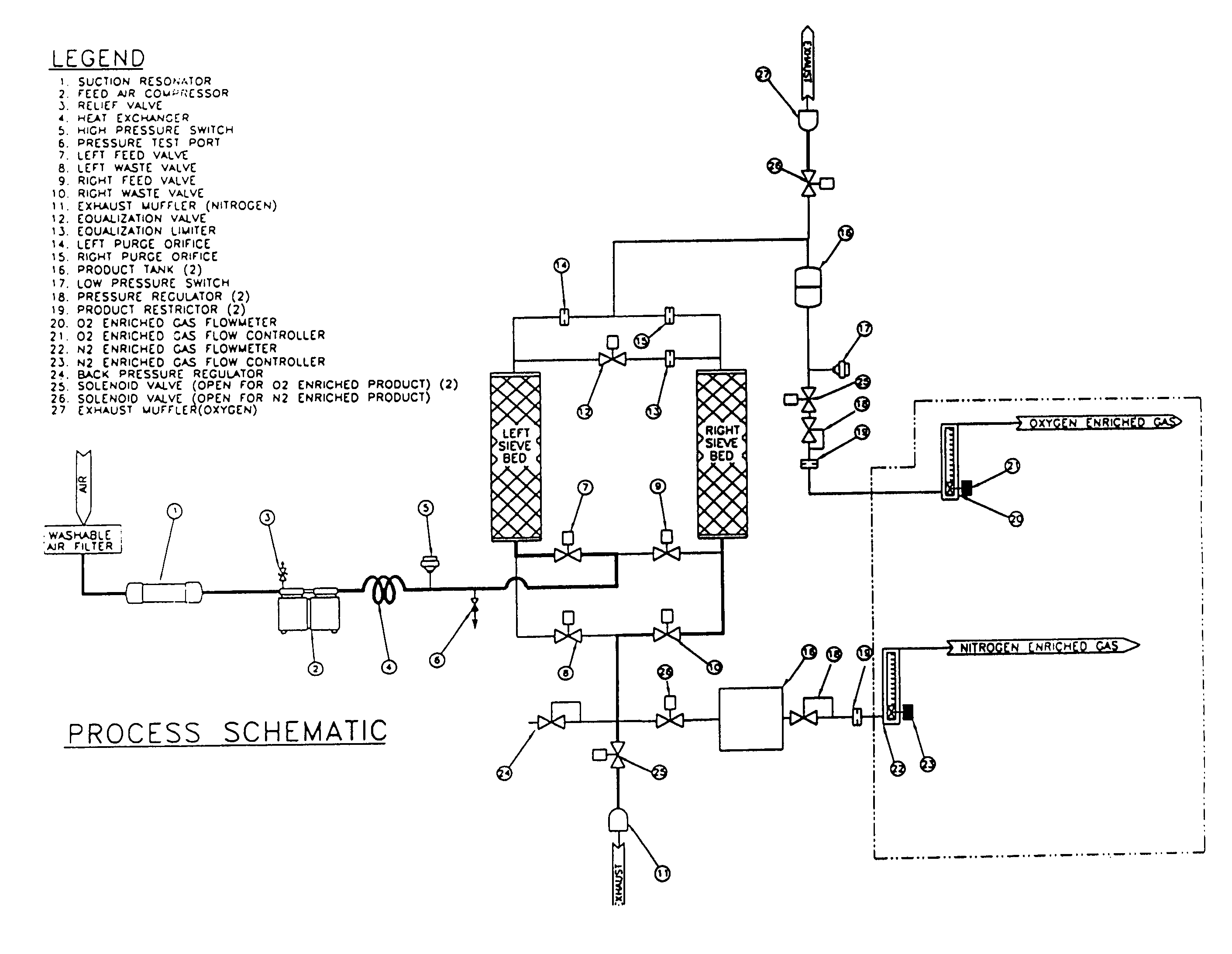
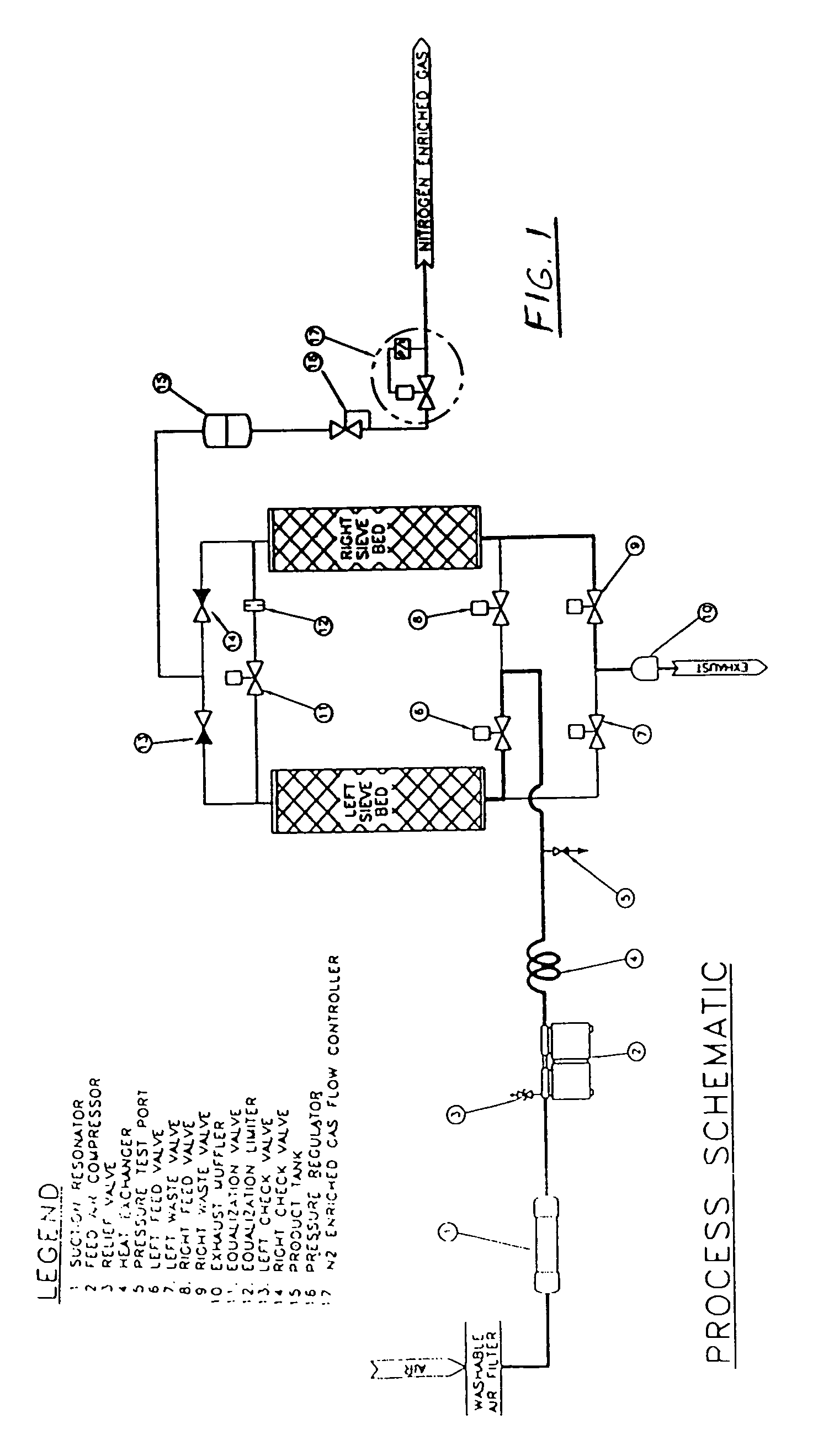
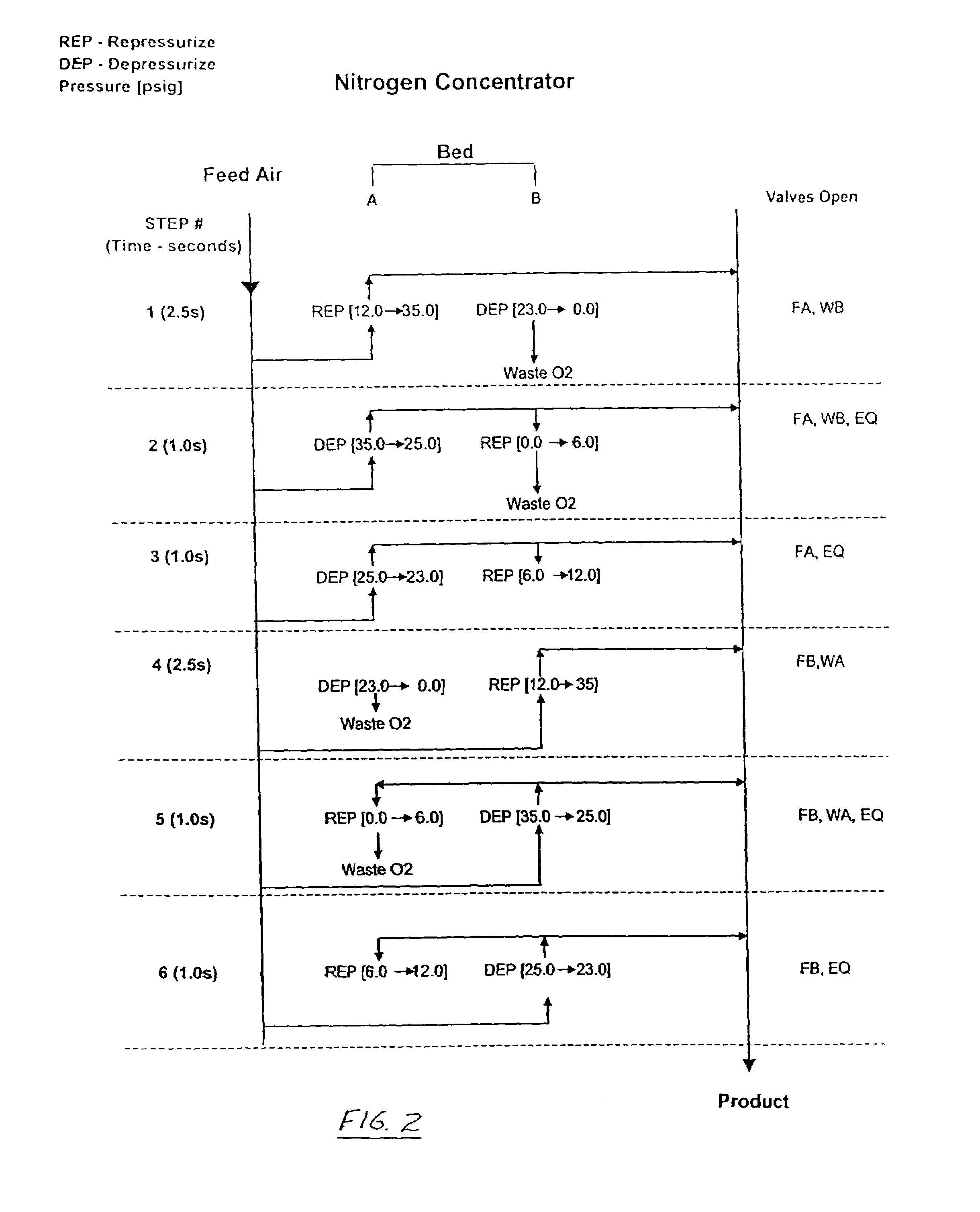
ActiveUS7011092B2Increase and decrease effective flow rateImprove efficiencyRespiratorsGas treatmentNitrogenProduct gas
Hypoxic delivery apparatus producing from ambient air a product gas having a lower levels of oxygen concentration and delivering the product gas to a user of the apparatus in pulse doses. Alternatively, the apparatus may include a selector for alternately delivering either a nitrogen enriched gas or an oxygen enriched gas to the user.
Owner:CAIRE
Therapeutic treatments using botulinum neurotoxin
ActiveUS20090232850A1Eliminates sensory inputImprove developmentBacterial antigen ingredientsNervous disorderDiseaseObstructive Pulmonary Diseases
Methods for treating a coronary risk factor (such as hypertension, diabetes, hyperlipidemia and obesity) and / or a respiratory disorder (such as asthma, chronic obstructive pulmonary disease and bronchitis) and / or arthritis by local administration of a botulinum neurotoxin to at least one of a head, neck or shoulder location (for example, by subdermal, subcutaneous or intramuscular administration of the botulinum neurotoxin) of a patient with a coronary risk factor, respiratory disorder or arthritis.
Owner:ALLERGAN INC
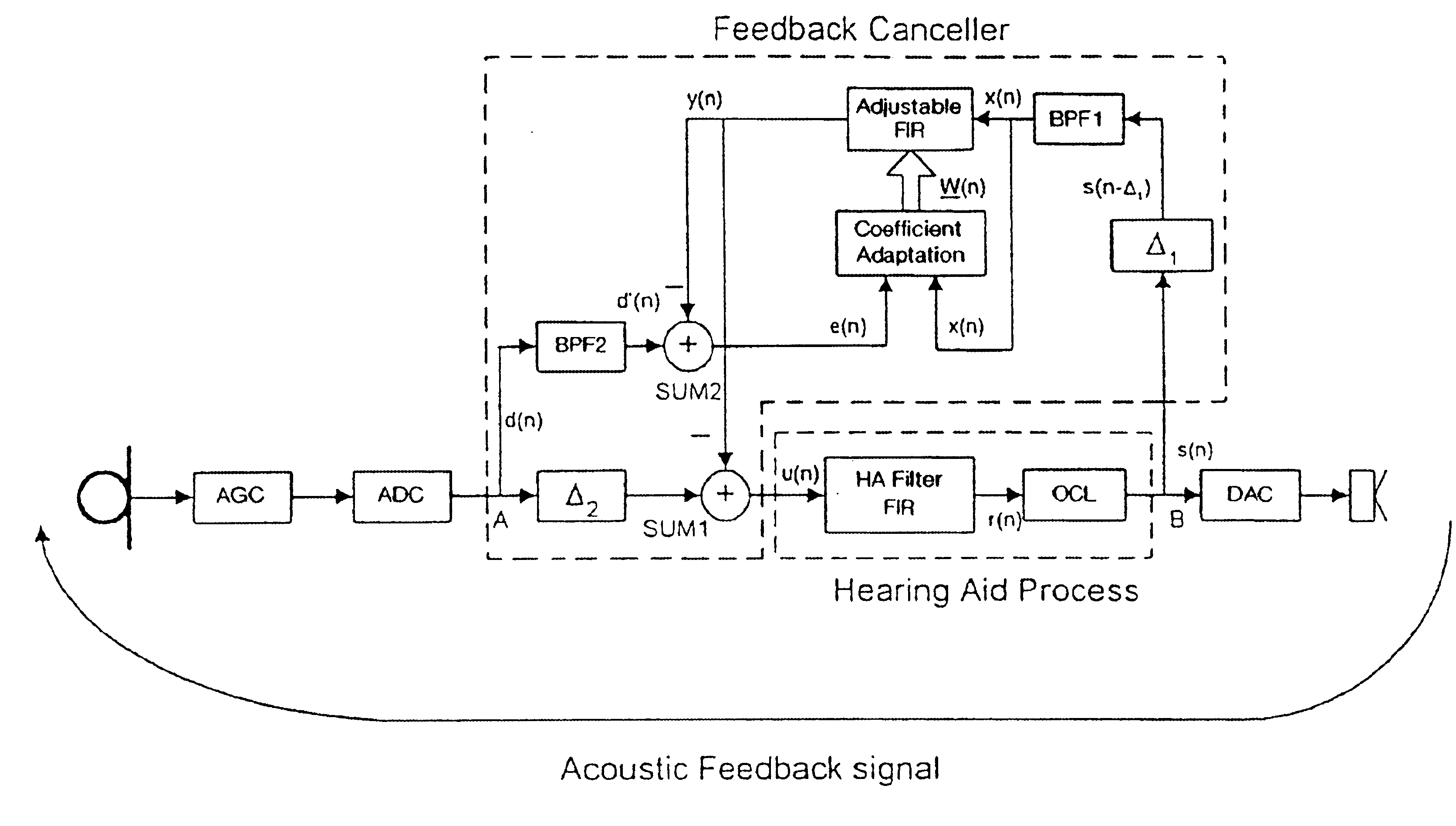
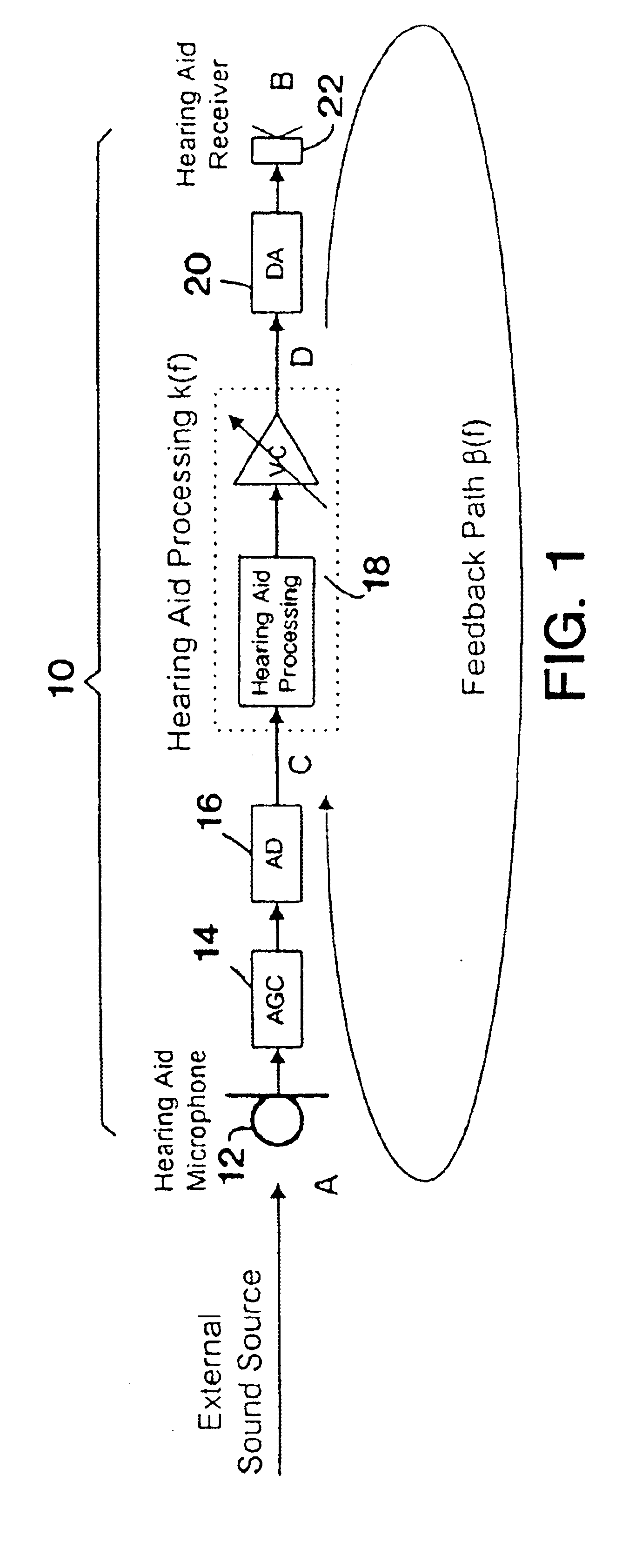
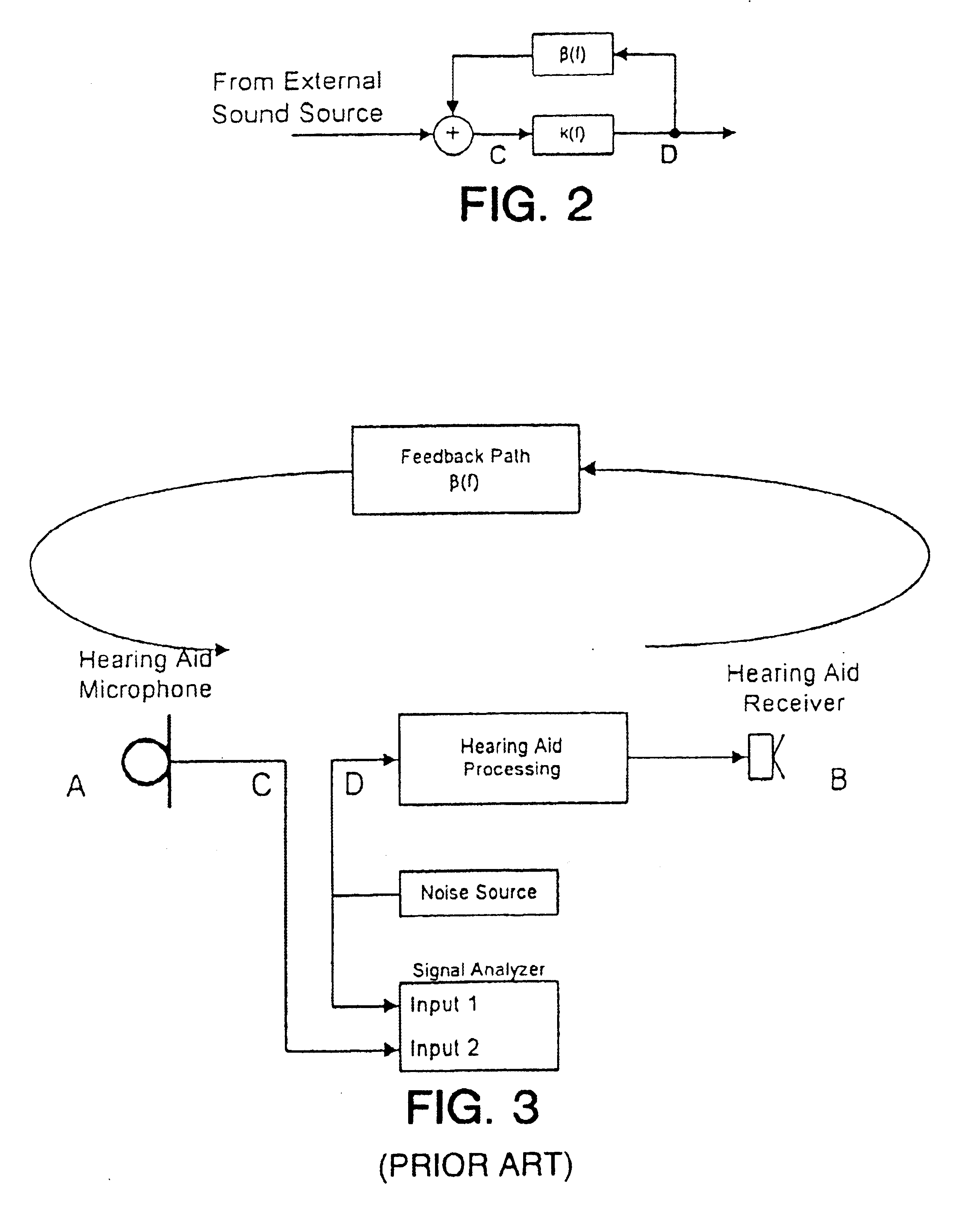
Band-limited adaptive feedback canceller for hearing aids
InactiveUS6876751B1Minimal signal distortionThe result is validSignal processingAdaptive networkEngineeringImproved method
An improved method for adaptively cancelling acoustic feedback in hearing aids and other audio amplification devices. Feedback cancellation is limited to a frequency band that encompasses all unstable frequencies. By limiting the bandwidth of the feedback cancellation signal, the distortion due to the adaptive filter is minimized and limited only to the unstable feedback regions. A relatively simple signal processing algorithm is used to produce highly effective results with minimal signal distortion.
Owner:HOUSE EAR INSTITUTE
Method and system for detecting asphalt mixture
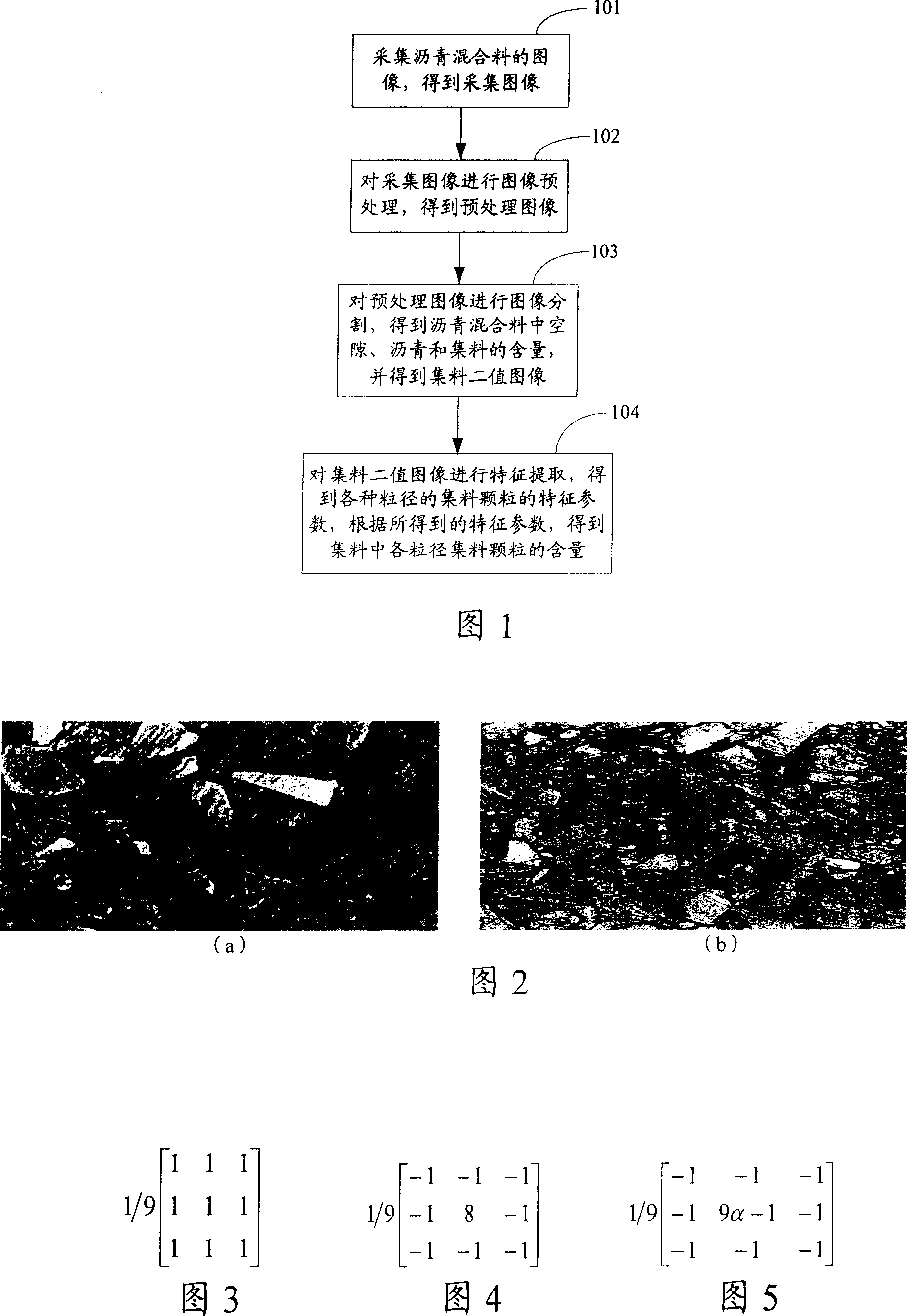
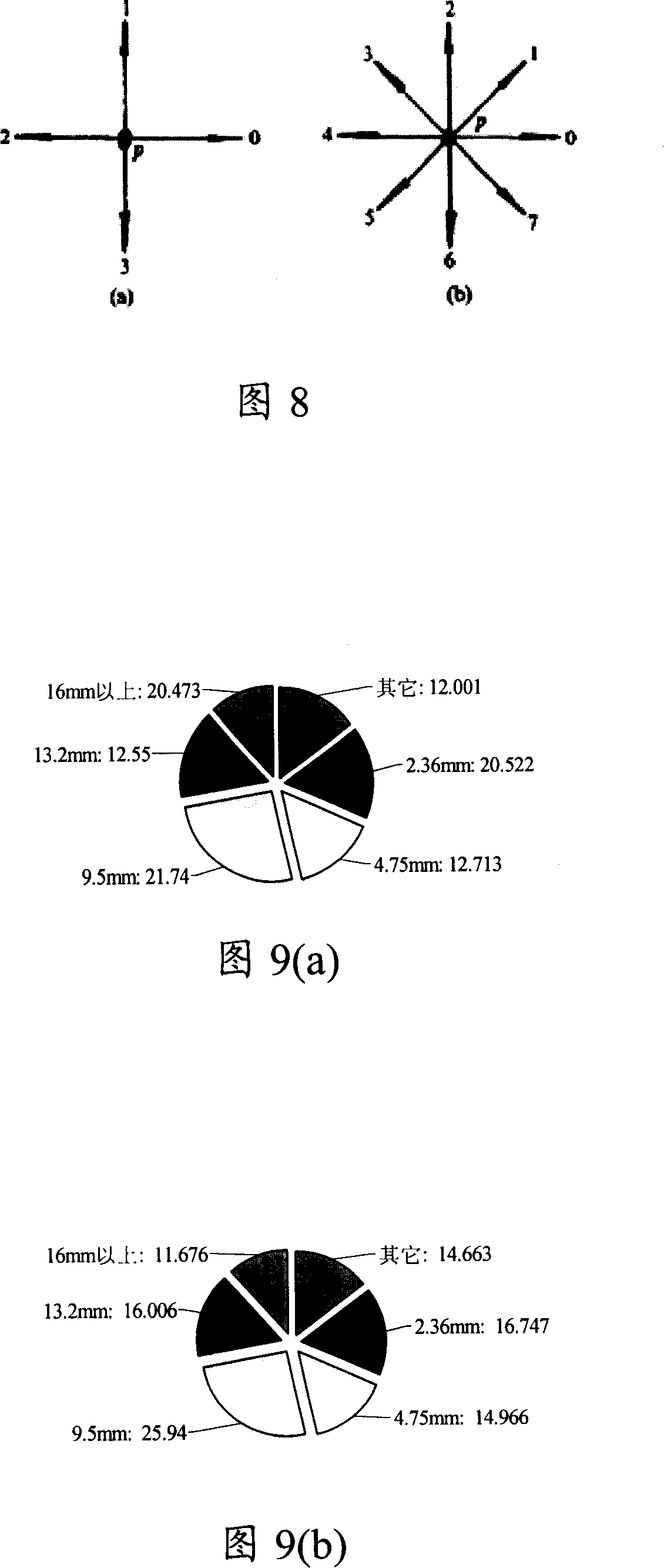
InactiveCN101153850AEfficient automatic detectionLow costImage enhancementMaterial analysis by optical meansImaging processingPavement engineering
The invention discloses a detection method of bituminous mixture, including the following steps: digital image collection of bituminous mixture is completed; image processing of the acquired digital image is completed to obtain the content of compositions of the bituminous mixture. Moreover, the invention also discloses a detection system for the bituminous mixture. Both the method and the system can complete effective separation and extraction of bitumen, airgap, aggregate and aggregate particle of different particle diameter and realize direct determination and calculation of volumetric composition characteristic parameter of the bituminous mixture through converting the obtained characteristic parameter into volume ratio; moreover, the invention improves the mechanical property of the bituminous mixture and provides reliable basis for the scientificity in bituminous pavement engineering research.
Owner:CHANGAN UNIV
Apparatus for the treatment of disorders of tissue and/or the joints
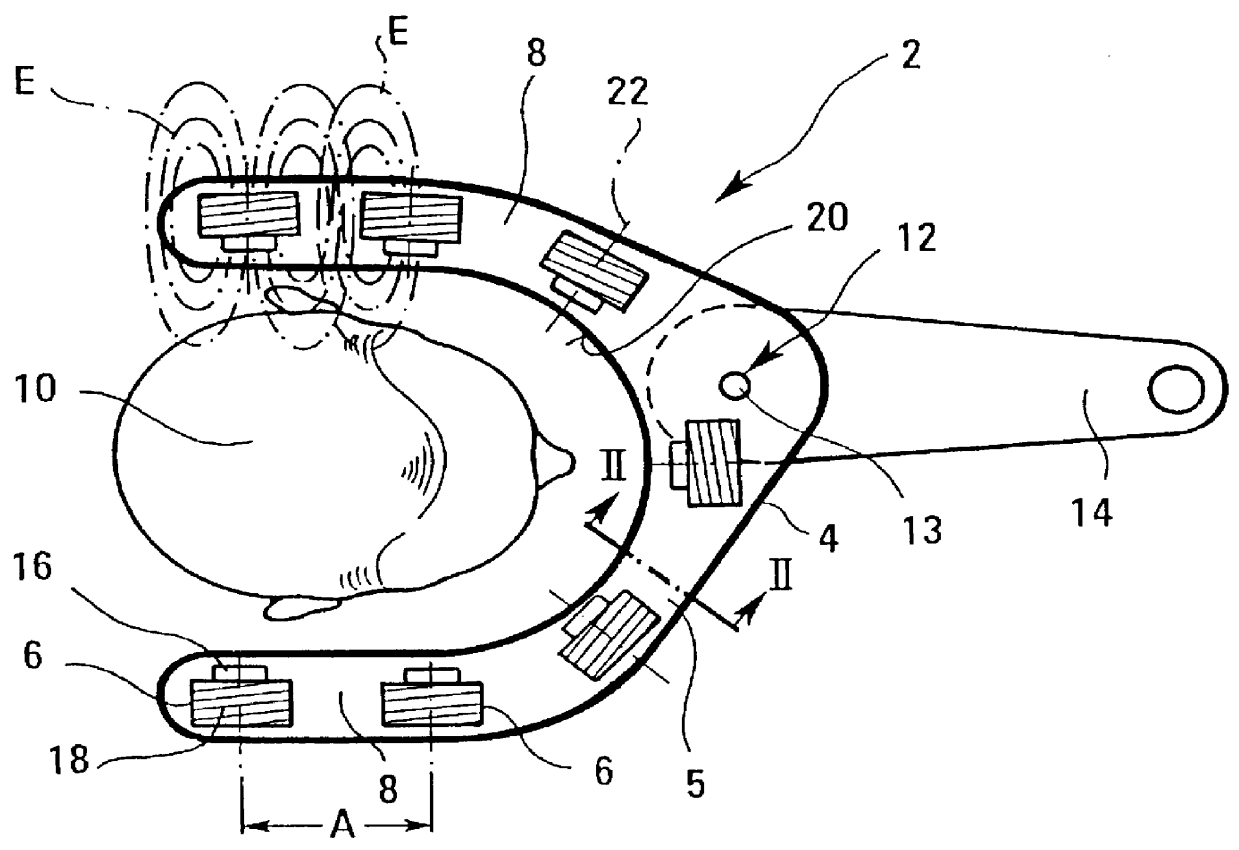
InactiveUS6048302APromote healingSecure supportElectrotherapySurgeryElectromagnetic fieldBiomedical engineering
An apparatus for the treatment of disorders of tissue and / or the joints in the area of the jaw or neck of a patient (10), particularly for the treatment of periodontosis, is depicted, wherein the apparatus comprises a housing (4) that surrounds at least the area of the jaw or neck to be treated. A number of coils (6) is also provided for generating at least one electromagnetic field (E) which can be applied to the area to be treated. The coils (6) are arranged in the interior (5) of the housing (4).
Owner:BIO MAGNETIC THERAPY SYST
Method for cleaning industrial equipment with pre-treatment
ActiveUS20060042665A1Effective resultImproves degree of softeningInorganic/elemental detergent compounding agentsAnionic surface-active compoundsPre treatmentEvaporator
A method of cleaning equipment such as heat exchangers, evaporators, tanks and other industrial equipment using clean-in-place procedures and a pre-treatment solution prior to the conventional CIP cleaning process. The pre-treatment step improves the degree of softening of the soil, and thus facilitates its removal. The pre-treatment solution can be a strong acidic solution, a strong alkaline solution, or comprise a penetrant. A preferred strong acidic solution is an acid peroxide solution. In some embodiments, the pre-treatment may include no strong alkali or acid ingredient; rather, the penetrant provides acceptable levels of pre-treatment.
Owner:ECOLAB USA INC
Ceria-based mixed-metal oxide structure, including method of making and use
InactiveUS20030186805A1Increase surface areaSimple structureRare earth metal oxides/hydroxidesMaterial nanotechnologyPtru catalystCerium(IV) oxide
A homogeneous ceria-based mixed-metal oxide, useful as a catalyst support, a co-catalyst and / or a getter, is described. The mixed-metal oxide has a relatively large surface area per weight, typically exceeding 150 m<2> / g, a structure of nanocrystallites having diameters of less than 4 nm, and including pores larger than the nanocrystallites and having diameters in the range of 4 to about 9 nm. The ratio of the pore volumes, VP, to skeletal structure volumes, VS, is typically less than about 2.5, and the surface area per unit volume of the oxide material is greater than 320 m<2> / cm<3>, such that the structural morphology supports both a relatively low internal mass transfer resistance and large effective surface area for reaction activity of interest. The mixed metal oxide is made by co-precipitating a dilute metal salt solution containing the respective metals, which may include Zr, Hf, and / or other metal constituents in addition to Ce, replacing water in the co-precipitate with a water-miscible low surface-tension solvent, and relatively quickly drying and calcining the co-precipitate at moderate temperatures. A highly dispersive catalyst metal, such as Pt, may be loaded on the mixed metal oxide support from a catalyst-containing solution following a selected acid surface treatment of the oxide support. The mixed metal oxide, as catalyst support, co-catalyst or getter, is applied in various reactions, and particularly water gas shift and / or preferential oxidation reactions as associated with fuel processing systems, as for fuel cells and the like.
Owner:INT FUEL CELLS
Method and device for providing ozone sanitation of various objects
InactiveUS20030156978A1Great profit marginMaximal efficacyLavatory sanitoryMeat/fish preservation by freezing/coolingChemistryMicrobiological growth
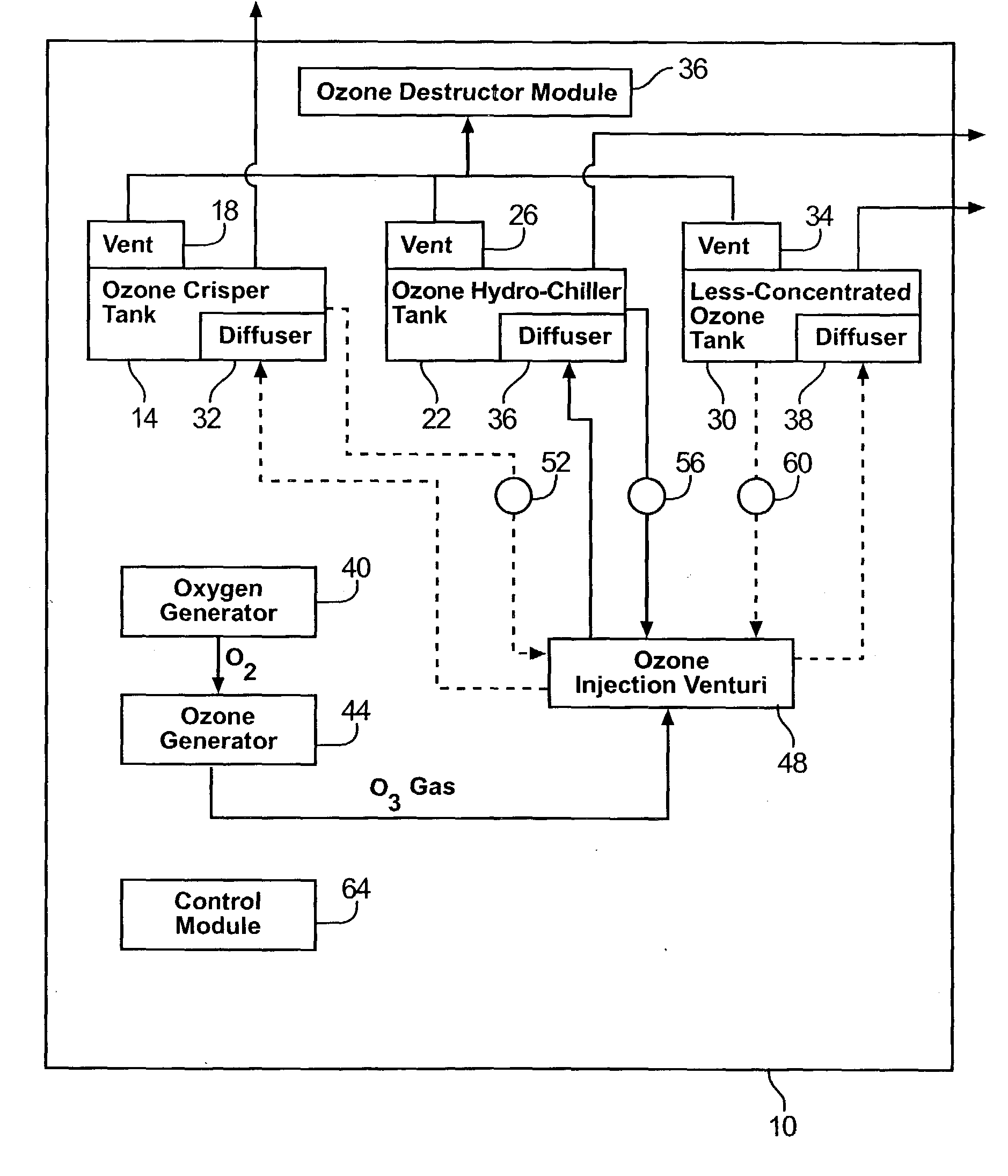
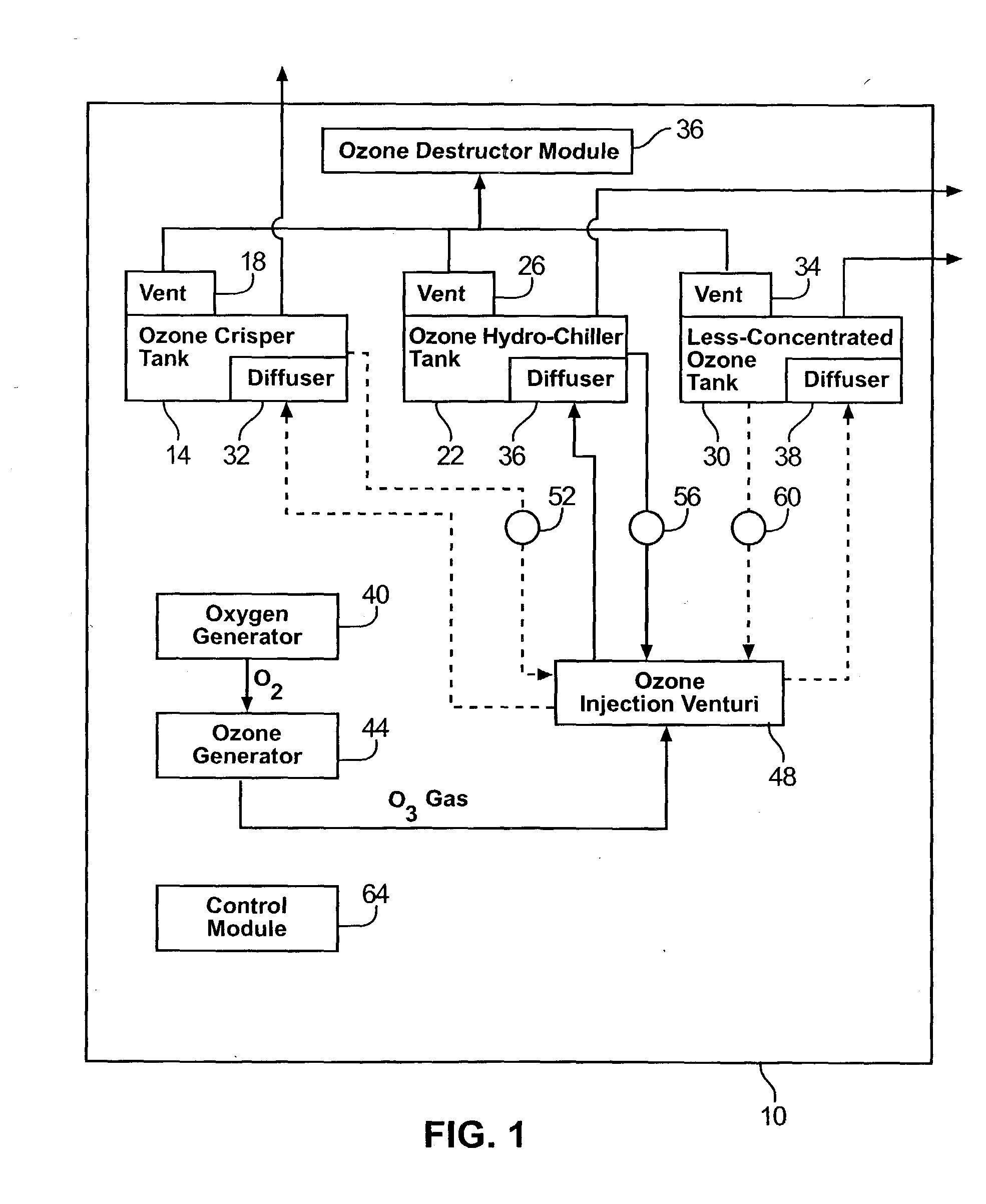
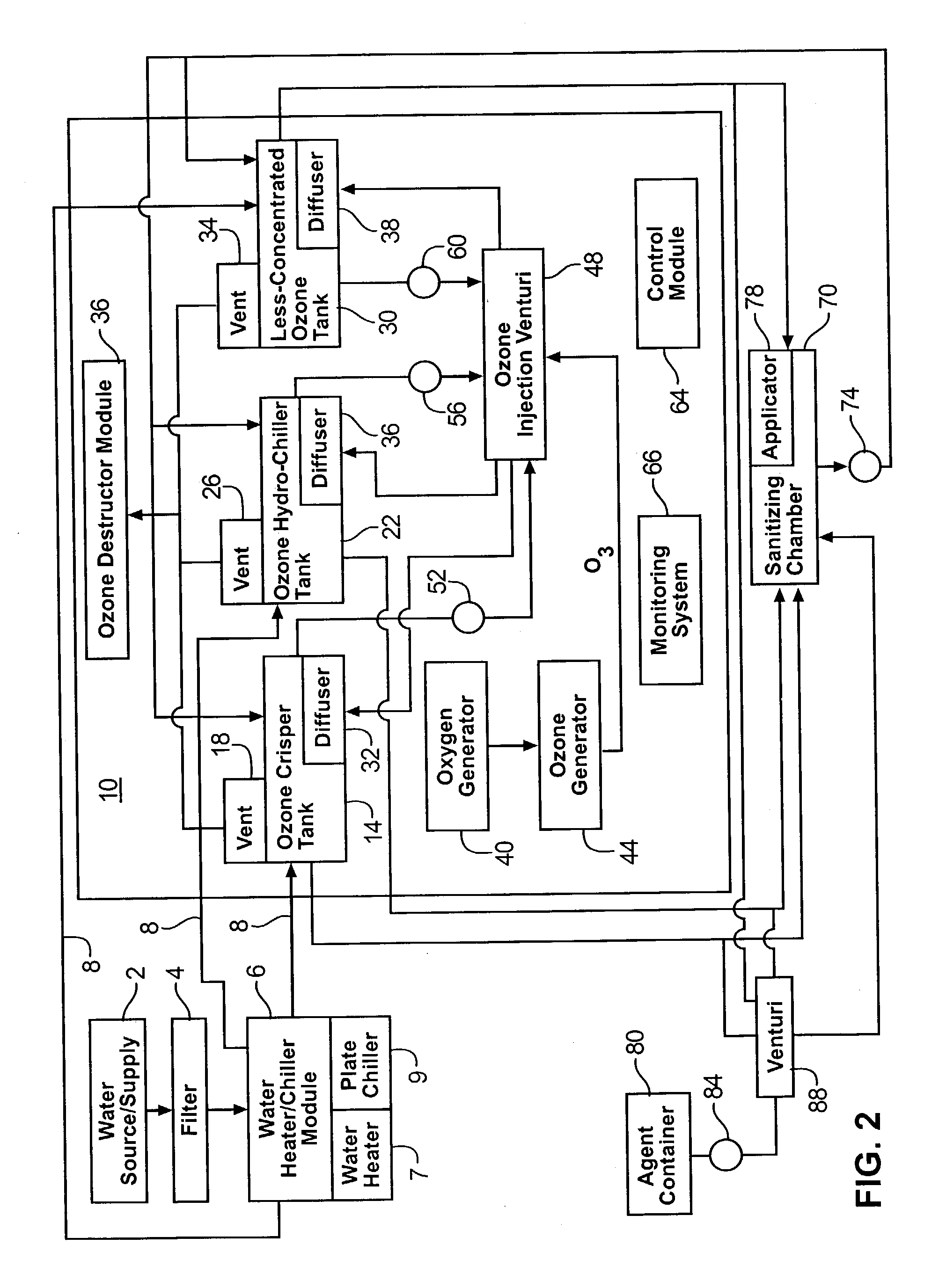
The present invention features an ozone sanitation device and system and a method of using the same to sanitize various objects in various environments. The present invention is particularly adapted to be used to sanitize food products, such as fruit and vegetable products as well as others at the site of the marketing and selling of such products. The ozone sanitation device functions to combat harmful pathogens by reduce microbial growth and bacteria existing on the treated object. The device comprises an ozone generator that produces ozone gas that mixes with temperature controlled water to create an ozonated water solution to be applied to an object for treatment. Moreover, the present invention features several methods of using the ozone sanitation device to treat various objects, as well as a method for restoring water to dehydrated objects, such as fruits and vegetables. The method provides a continuous process and comprises using a tepid wash solution cycle and a chilled wash solution cycle of water and the application of ozone and oxygen.
Owner:FRESH FOOD TECH
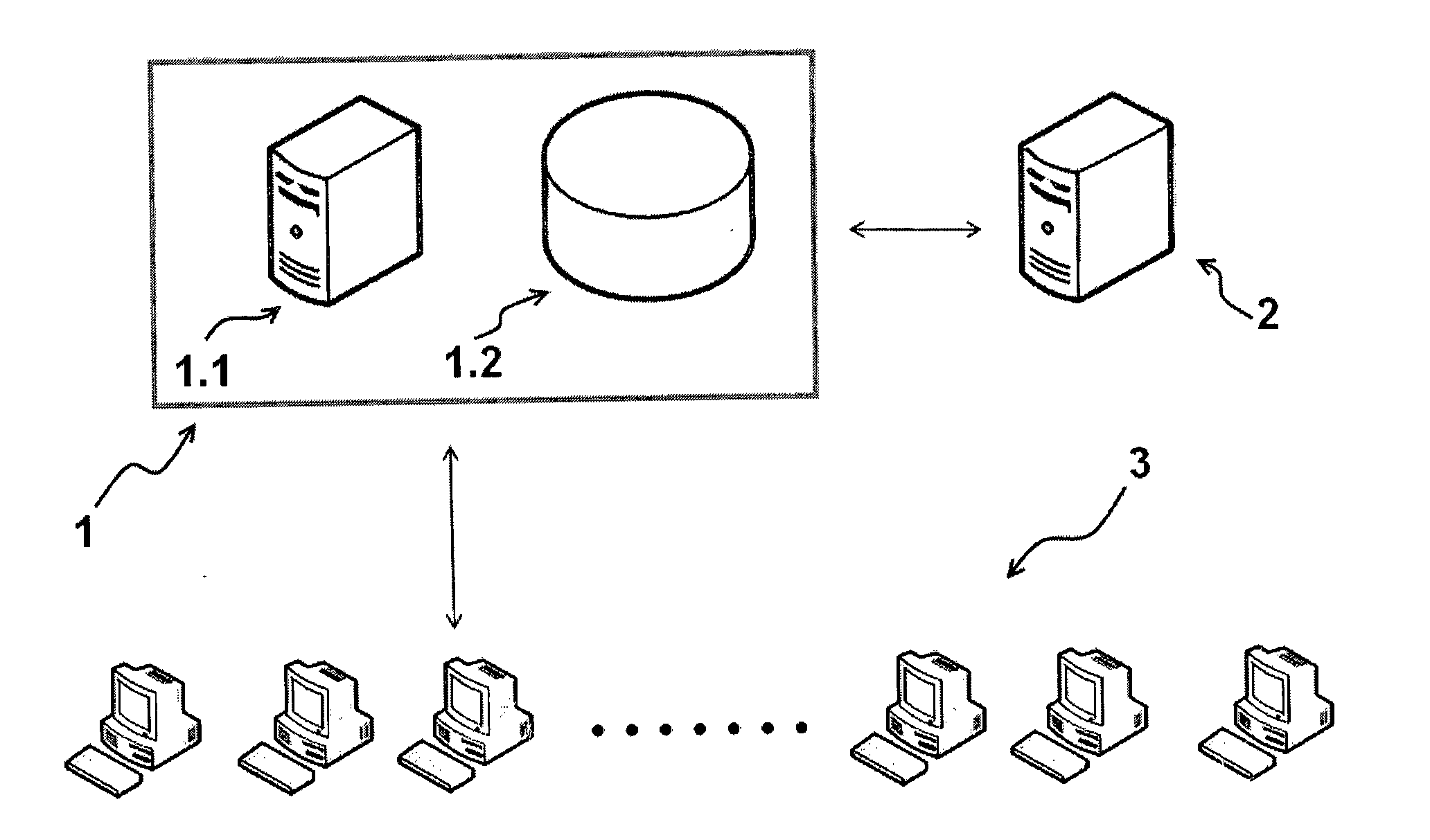
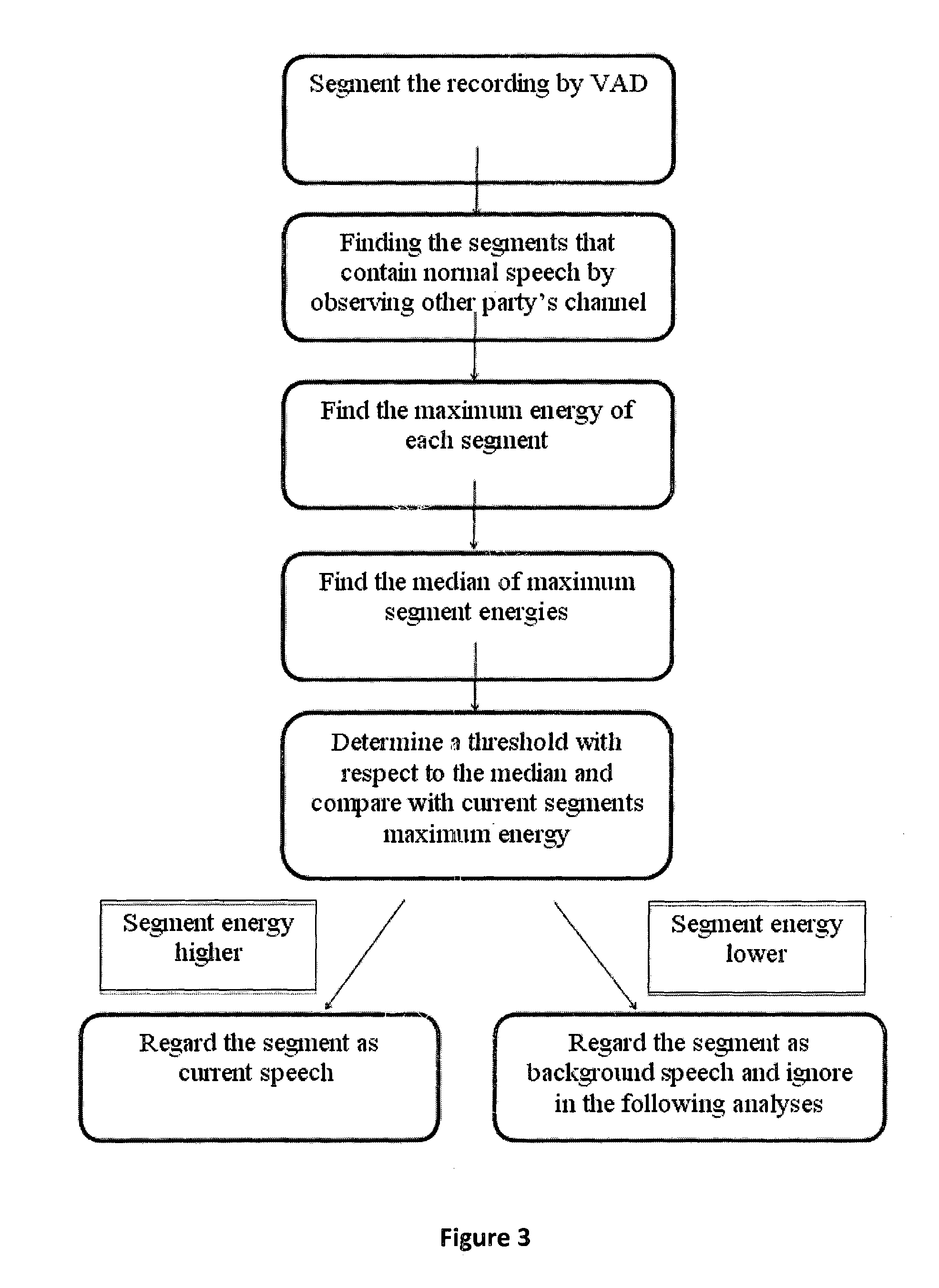
Speech analytics system and methodology with accurate statistics
ActiveUS20150350438A1Eliminate disadvantageLow costAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersSpeech analyticsSpeech sound
The present invention relates to implementing new ways of automatically and robustly evaluating agent performance, customer satisfaction, campaign and competitor analysis in a call-center and it is comprising; analysis consumer server, call pre-processing module, speech-to-text module, emotion recognition module, gender identification module and fraud detection module.
Owner:SESTEK SES & ILETISIM BILGISAYAR TEKNOLOJILERI SANAYII & TICARET ANONIM SIRKETI
Unitary vacuum tube incorporating high voltage isolation
InactiveUS6837766B2Improve isolationLinear distance increasesGas filling substance selectionCathode-ray/electron-beam tube vessels/containersGreen tapeHigh pressure
A housing for microelectronic devices requiring an internal vacuum for operation, e.g., an image detector, is formed by tape casting and incorporates leads between interior and exterior of the housing where the leads are disposed on a facing surface of green tape layers. Adjacent green tape layers having corresponding apertures therein are stacked on a first closure member to form a resulting cavity and increased electrical isolation or channel sub-structures are achievable by forming adjacent layers with aperture dimension which vary non-monotonically. After assembly of the device within the cavity, a second closure member is sealed against an open face of the package in a vacuum environment to produce a vacuum sealed device.
Owner:EOTECH LLC
Multi-level spinal stabilization system
ActiveUS8313515B2The result is validEase of installation and in applicationInternal osteosythesisJoint implantsSpinal columnPhysical medicine and rehabilitation
Multi-level spinal stabilization devices, systems and methods are provided that include at least one multi-level connector, one elongated member with an enlarged head, at least one pedicle screw, and at least one mechanism that supports three degrees of rotational freedom relative to both the elongated member and the pedicle screw each. The mechanism may include universal joint mechanisms or ball and socket mechanisms. In the case of the ball and socket mechanisms, the enlarged head of the elongated member cooperates with a first socket member of the multi-level connector to define a dynamic junction that allows the socket member to move relative to the enlarged head of the elongated member while remaining engaged therewith.
Owner:RACHIOTEK
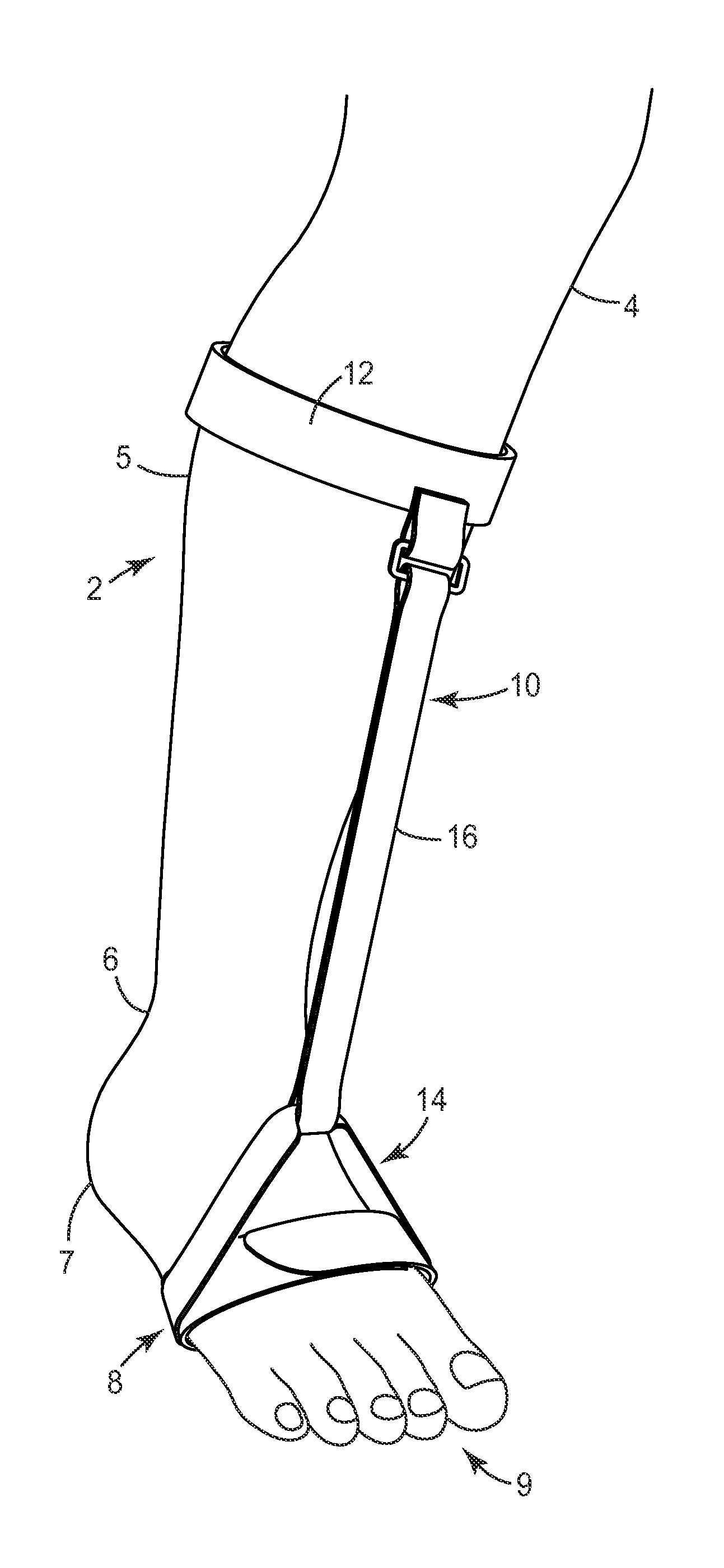
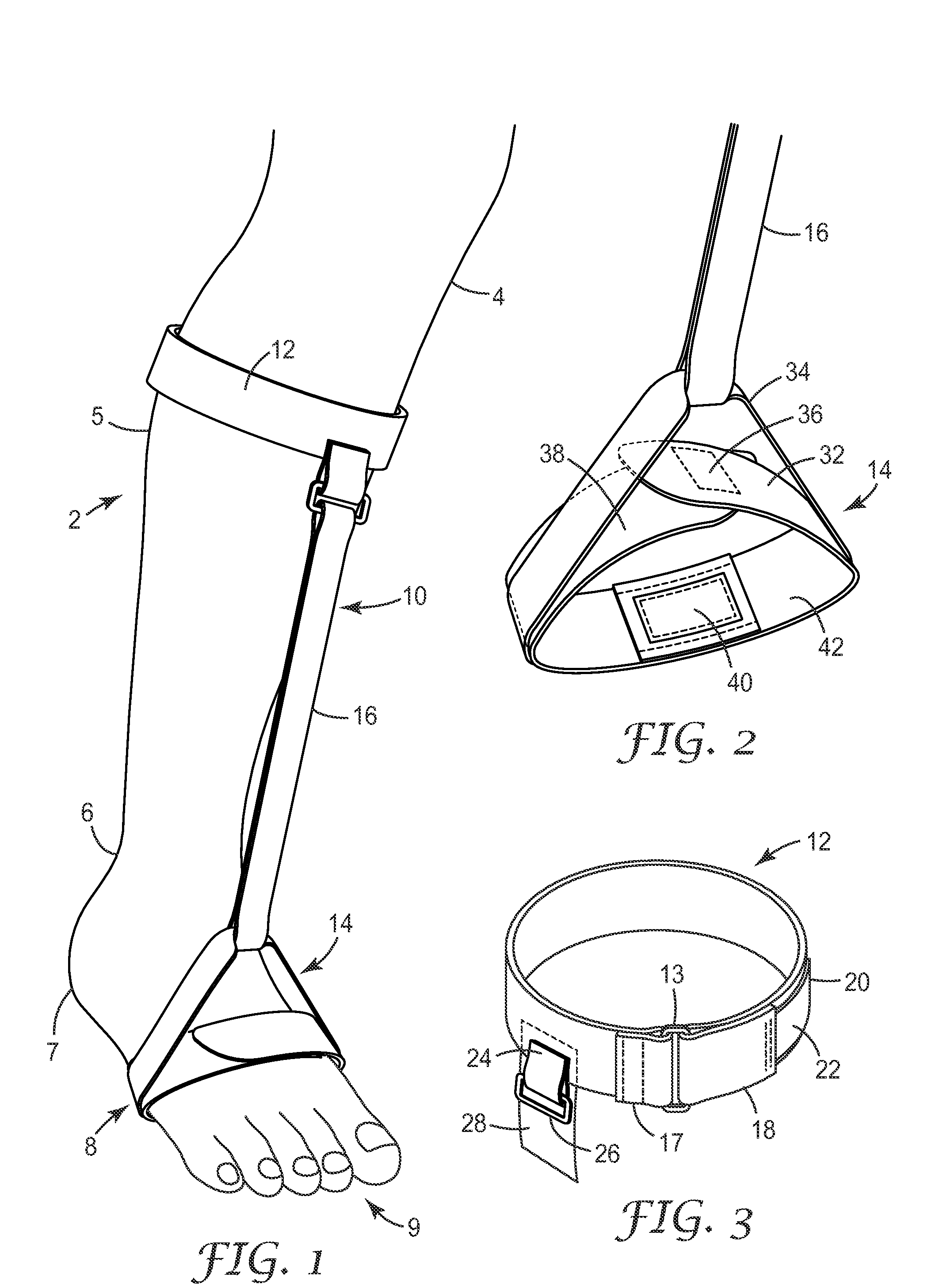
Foot support device
InactiveUS7753864B2Relieve painAvoid positioningRestraining devicesNon-surgical orthopedic devicesPhysical medicine and rehabilitationPlantar surface
Owner:3M INNOVATIVE PROPERTIES CO
Byzantine paxos
InactiveUS7565433B1Proper behavior of the systemThe result is validComputer controlSimulator controlDigital signatureMessage authentication code
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices when each device within the system verifies the sender of any message it receives, and the propriety of the message. The sender can be verified through message authentication schemes or digital signature schemes, though message authentication can provide a more computationally efficient solution. The propriety of a message can be verified by receiving a sufficiently large number of equivalent, properly authenticated messages such that, even if every malicious device transmitted a message, at least one message would have been sent by a properly functioning device. If the number of malicious devices is represented by the variable “M”, a sufficient number of equivalent, properly authenticated messages to verify that the message is true can be any number of messages greater than M. Furthermore, the receipt of more than 2M equivalent properly authenticated messages can allow the receiving device to prove the propriety of the message to any device it forwards the messages onto. The proper operation of the distributed computing system can, therefore, proceed in the face of M number of malicious failures and F number of total failures, which can include malicious and non-malicious failures, if the number of constituent devices in the distributed computing system is greater than 2F+M.
Owner:MICROSOFT TECH LICENSING LLC
Multiplayer Competition Game Device, Game Machine and Game Program
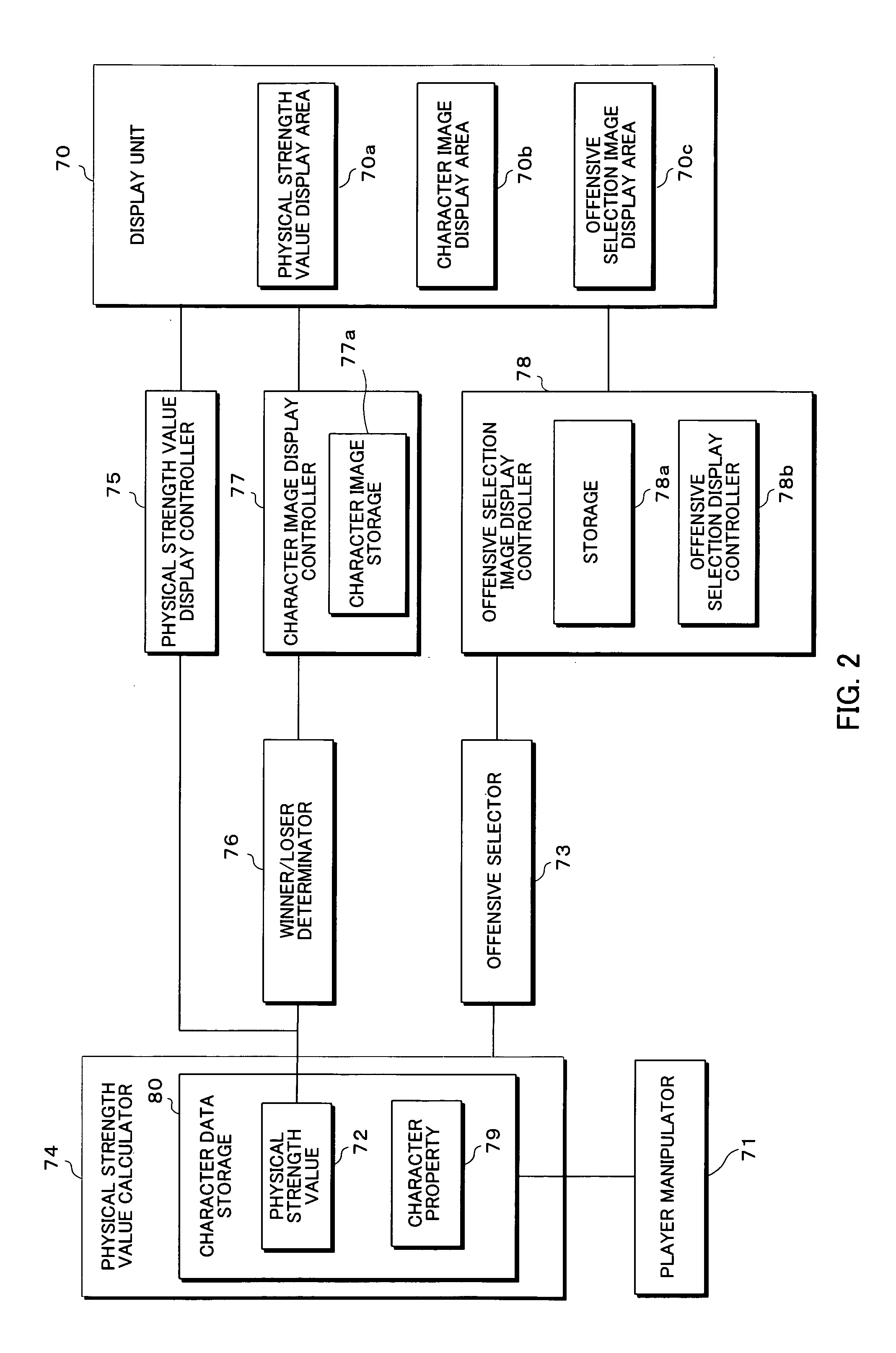
ActiveUS20080287175A1Effective resultClarify offensive typeRoulette gamesApparatus for meter-controlled dispensingPhysical strengthComputer graphics (images)
After the offensive selection element images are moved along the joining direction to the offensive selection image display area (70c) and displayed one after another in an alternating manner thereon, based on the control of the offensive selector (73), the images are halted and displayed in a matrix-wise arrangement. The character property (79) and physical strength value (72) are stored in association with the character, and the character corresponding to a physical strength value (72) equal to or lower than a predetermined final value is determined to be the loser, the physical strength value of the attacked character being calculated using the offensive value and a formula corresponding to the character property and the offensive type. Furthermore, the image of the character determined to be the loser by the winner / loser determinator (76) is varied.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
Method of making a spark plug
InactiveUS6923699B2Restrict movementHigh melting pointLine/current collector detailsSpark gapsBiomedical engineeringGrounding electrodes
A method of making a spark plug having a noble metal chip joined to an electrode main body of a ground electrode by interposing therebetween an intermediate member. The method comprises the steps of prior to joining the noble metal chip to the electrode main body, joining the intermediate member and the noble metal chip together, placing a noble metal chip and intermediate member assembly on the electrode main body in a way as to allow the intermediate member to contact the electrode main body, and welding the electrode main body and the intermediate member together while restricting relative movement of the electrode main body and the intermediate member without applying an urging force to a joint between the intermediate member and the noble metal chip.
Owner:NGK SPARK PLUG CO LTD
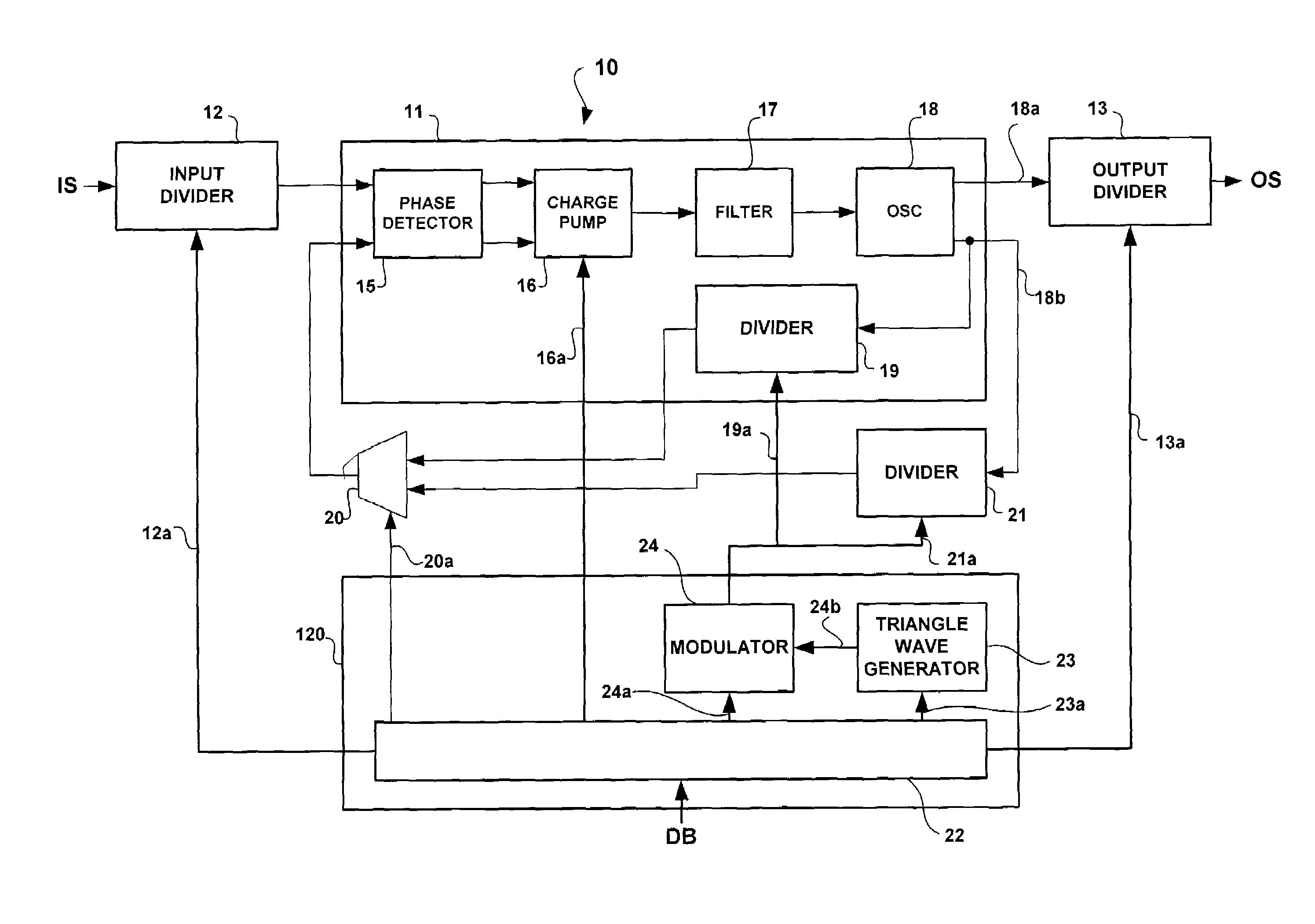
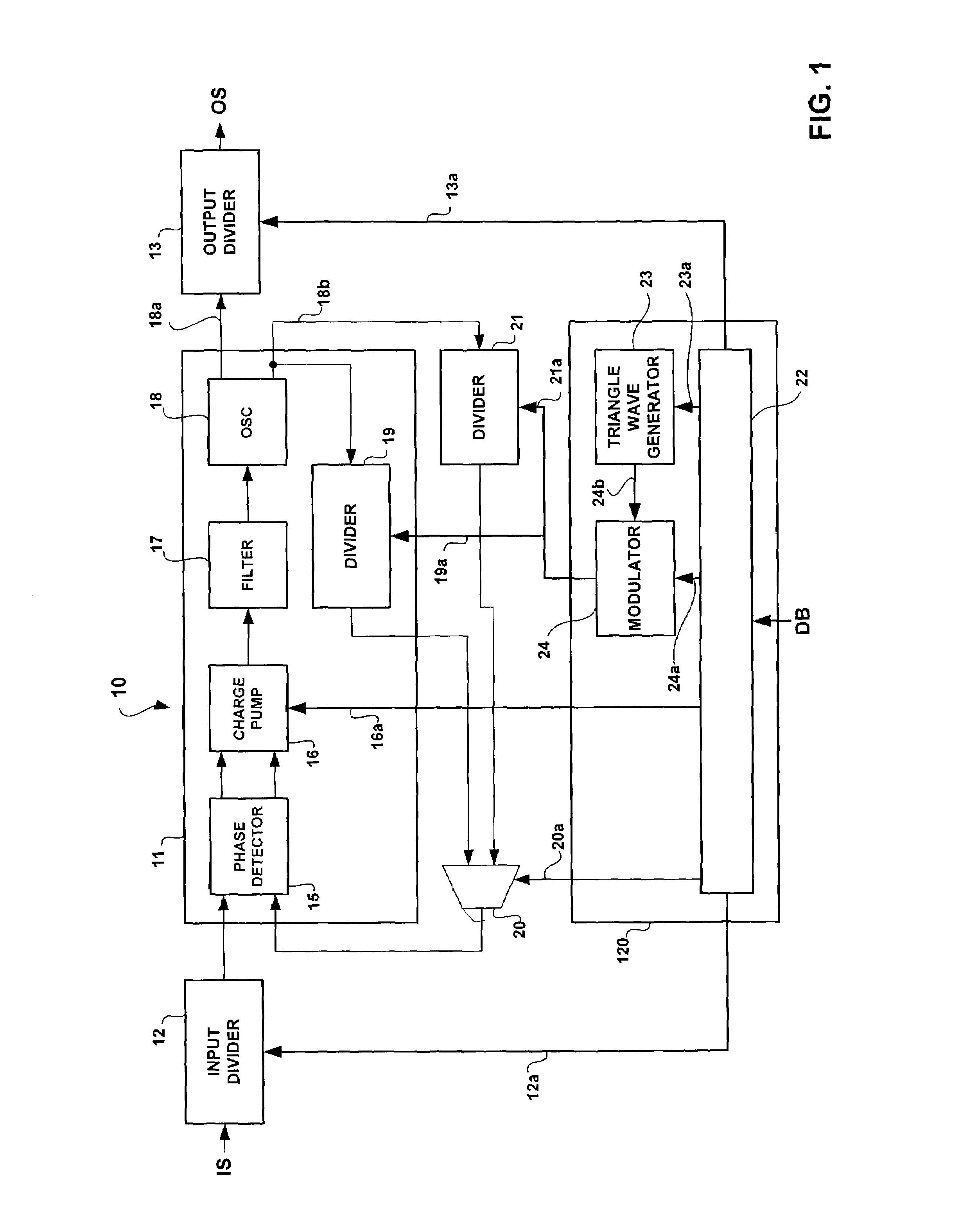
Process for generating a variable frequency signal, for instance for spreading the spectrum of a clock signal, and device therefor
ActiveUS7079616B2The result is validAvoid the needPulse automatic controlTransmissionPhase detectorElectronic systems
The use of a PLL including a phase detector responsive to the phase difference between an input signal and a feedback signal and which pilots an oscillator in function of this difference, is envisaged. The PLL also includes a feedback path that is responsive to the signal generated by the oscillator and which generates said feedback signal via at least one divider with a variable division ratio. The division ratio of said divider is modulated via a sigma-delta modulator, the input of which is fed with a triangular-wave modulating signal. The preferred application is that of a spread spectrum clock generator (SSCG) for digital electronic systems.
Owner:STMICROELECTRONICS SRL
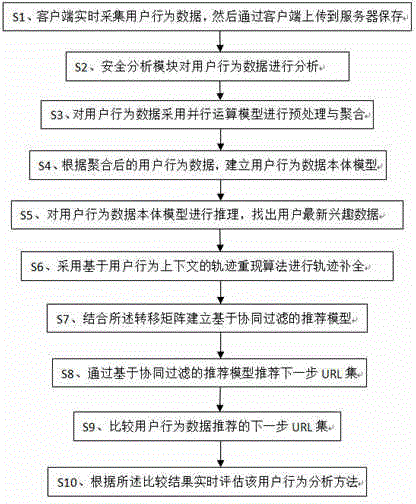
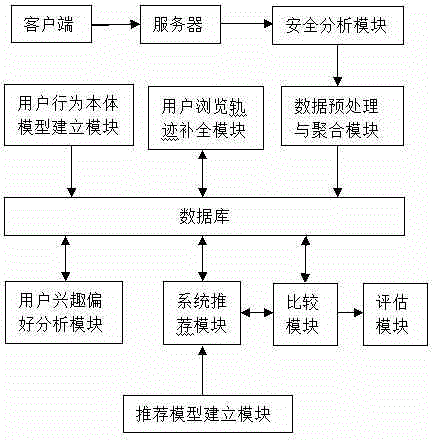
User behavior analysis method and system based on big data
InactiveCN104462213AGain interest in timeEffective and accurate pushWebsite content managementSpecial data processing applicationsEngineeringContext data
The invention discloses a user behavior analysis method and system based on big data. According to the method, user behavior data are collected through a client side in real time, user behaviors and contextual information of a page URL are combined, the real scene that a user browses Web pages is reproduced to the greatest extent, comprehensive user behavior tracks are extracted, and effective data assurance is provided for analyzing the user behaviors; security assurance is provided for the user behavior data through a safety analysis module, and a user behavior data body model is used for modeling the user behaviors, so that behavior information semantic levels are shared and reused, and the interoperability and the reliability of the model are improved; the user behavior and context data are collected in real time for analysis, so that a result is more reliable; body and behavior information is stored through a column storage database, and therefore the foundation of massive data management is laid; the powerful processing capacity and the large-scale data storage capacity of the cloud computing technology, the body and a reasoning and knowledge discovery method of the body are combined, the massive user behavior data are analyzed in real time to obtain user interest in time, and then effective and accurate user push is achieved.
Owner:成都逸动无限网络科技有限公司
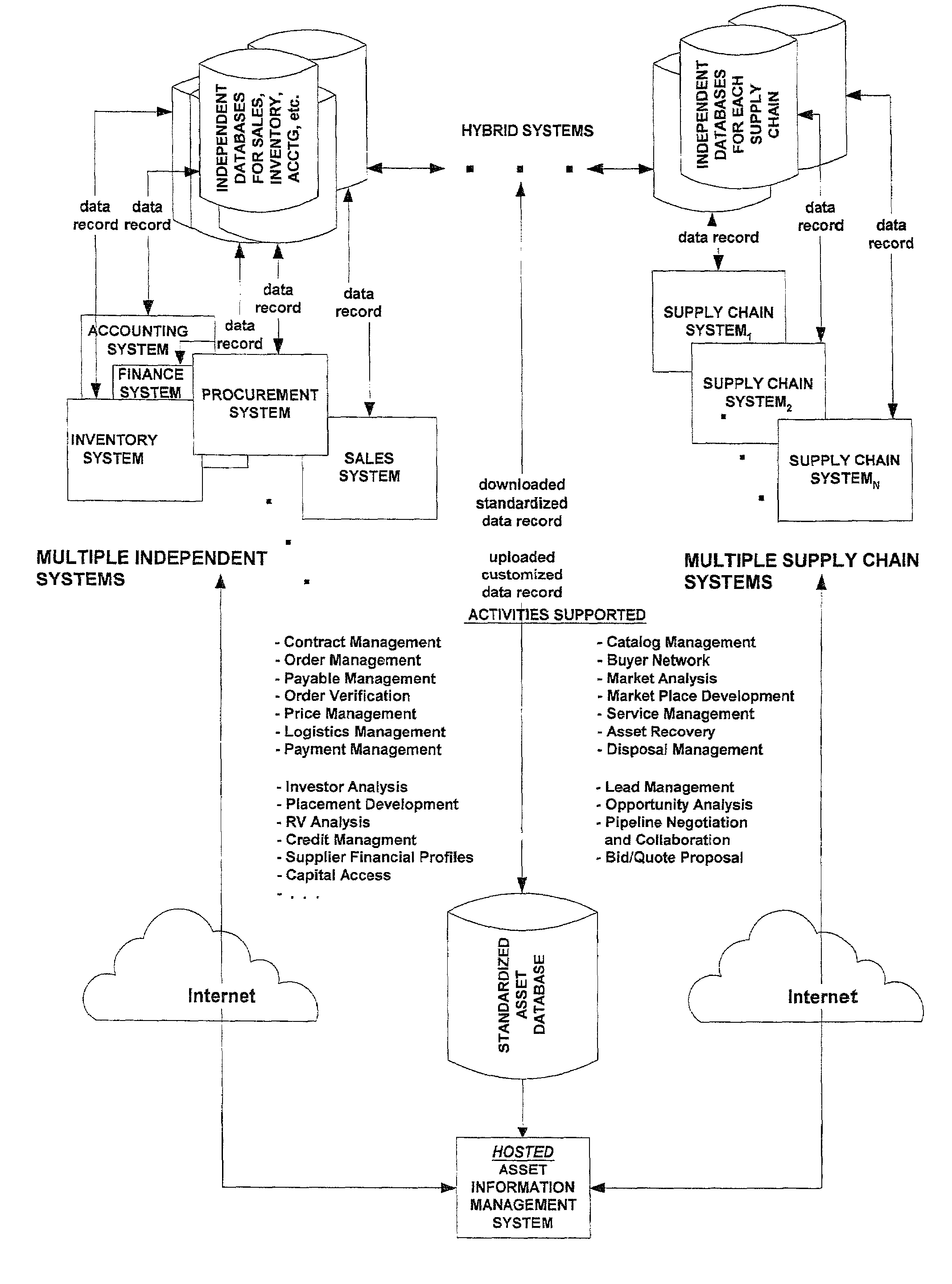
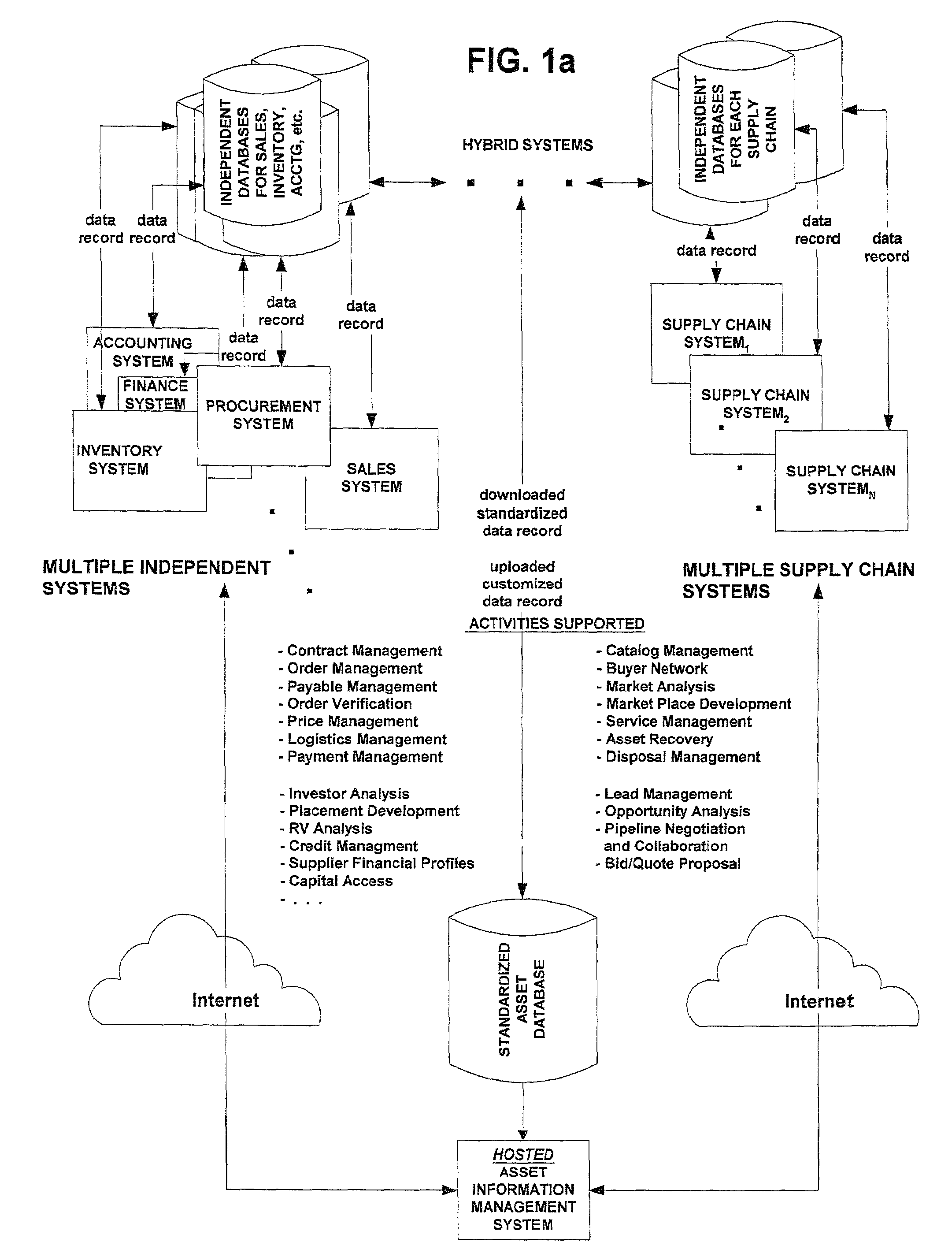
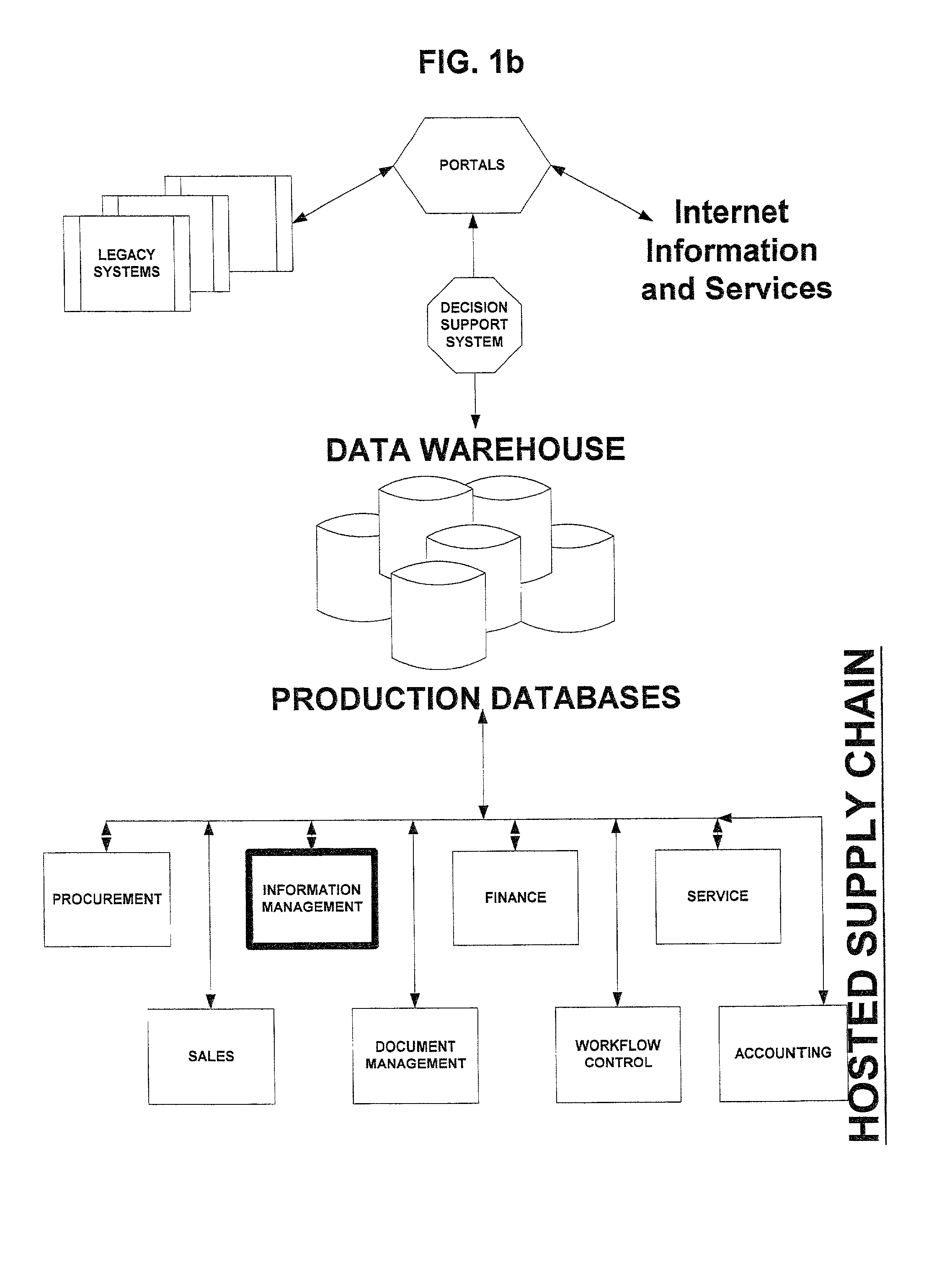
Hosted asset information management system and method
InactiveUS7552134B2Low costThe result is validSpecial service provision for substationDigital data processing detailsLegacy systemEngineering
A system and method for managing asset information is presented for both a standalone architecture and as a component of a total asset management system. The range of users for the system and method of the present invention spans single users to partners of a supply, chain and in the latter case, cross-organization asset detail information is provided to supply chain partners. The system and method of the present invention is intended to be interfaced with other components of a total asset management system, e.g., a procurement system for asset acquisition, and may be interfaced to legacy systems.
Owner:EPLUS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com