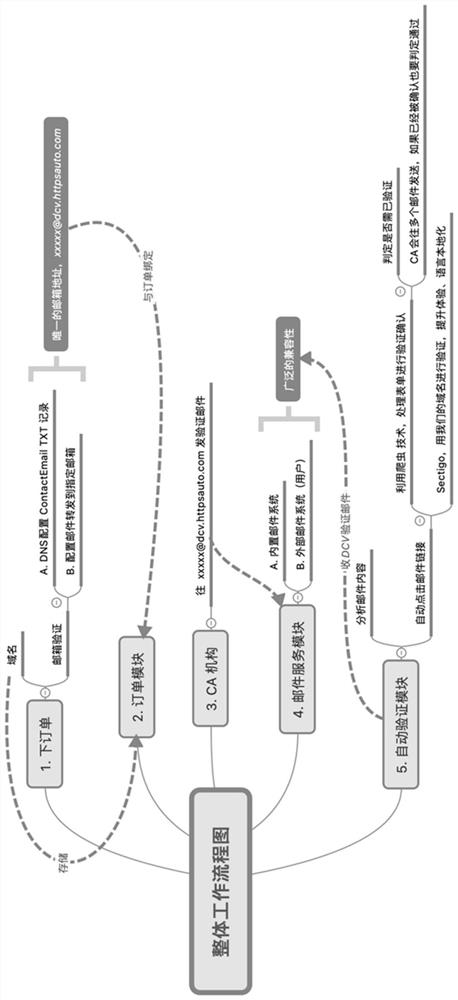
System and method for safely verifying domain name ownership during years of SSL certificate application
A technology of security verification and verification method, which is applied in the system field of securely verifying domain name ownership when applying for multi-year SSL certificates. Realize the effect of security verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
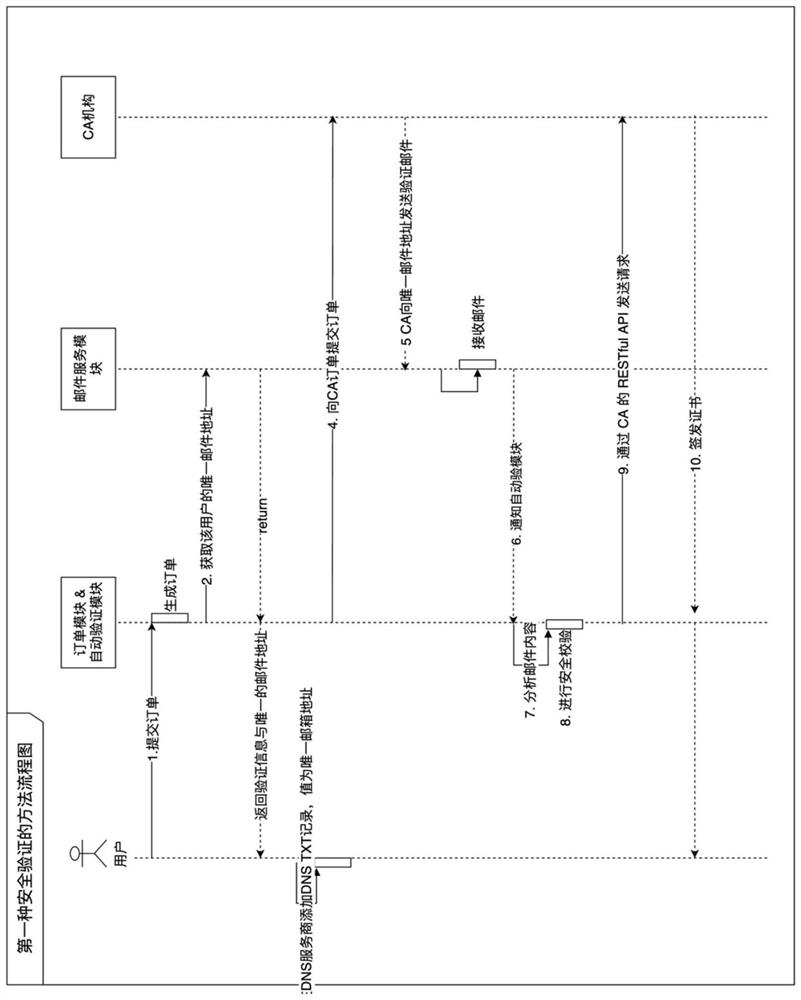
[0094] In this example, the first verification method is given, such as figure 2 As shown, it specifically includes the following steps:
[0095] 1. The applicant submits [domain name to be verified 1] to the order module and selects the DCV method as email verification, and initiates a certificate application;
[0096] 2. The order module stores [domain name to be verified 1] and generates [order number 1] associated with it, and obtains the specified unique email address from the mail service module and returns it to the applicant. In this example, [order number 1] + [ [Random value] is encrypted to obtain [ciphertext unique value] to generate a specified unique email address, and its format is as follows:
[0097] The unique value of ciphertext @dcv.httpsauto.com (agent verification domain name);
[0098] 3. The applicant sets the mailbox used to receive the verification email as the above-mentioned unique email address through the DNS TXT record, and notifies...
Embodiment 2
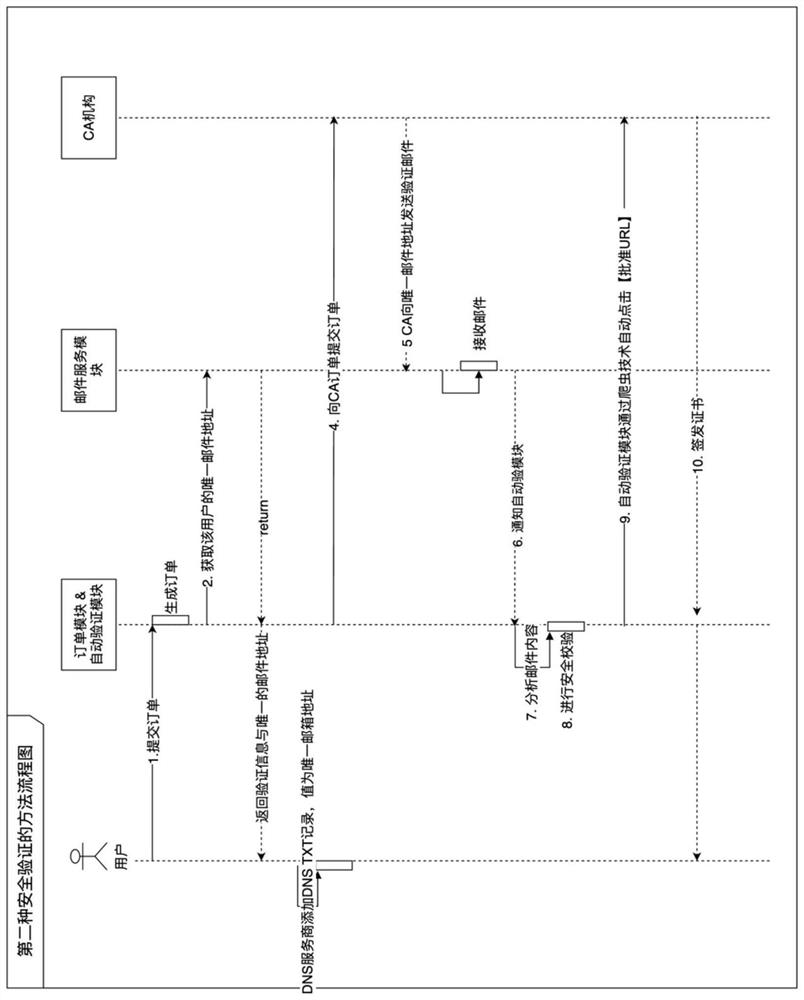
[0117] In this example, the second verification method is given, such as image 3 As shown, it specifically includes the following steps:
[0118] 1. The applicant submits [domain name to be verified 1] to the order module and selects the DCV method as email verification, and initiates a certificate application;
[0119] 2. The order module stores [domain name to be verified 1] and generates [order number 1] associated with it, and obtains the specified unique email address from the mail service module and returns it to the applicant. In this example, [order number 1] + [ [Random value] is encrypted to obtain [ciphertext unique value] to generate a specified unique email address, and its format is as follows:
[0120] The unique value of ciphertext @dcv.httpsauto.com (agent verification domain name);
[0121] 3. The applicant sets the email address for receiving DCV emails as the specified unique email address through the DNS TXT record, and notifies the above ord...
Embodiment 3
[0138] In this example, the third verification method is given, such as Figure 4 As shown, it specifically includes the following steps:
[0139] 1. The applicant submits [domain name to be verified 1] to the order module and selects the DCV method as email verification, and initiates a certificate application;
[0140] 2. The order module stores [domain name to be verified 1] and generates [order number 1] associated with it, and obtains the specified unique email address from the mail service module and returns it to the applicant. In this example, [order number 1] + [ [Random value] is encrypted to obtain [ciphertext unique value] to generate a specified unique email address, and its format is as follows:
[0141] The unique value of ciphertext @dcv.httpsauto.com (agent verification domain name);
[0142] 3. The applicant will set up any one of the 8 mailboxes used to receive DCV mails to be automatically forwarded, and forward the verification mail from the C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com