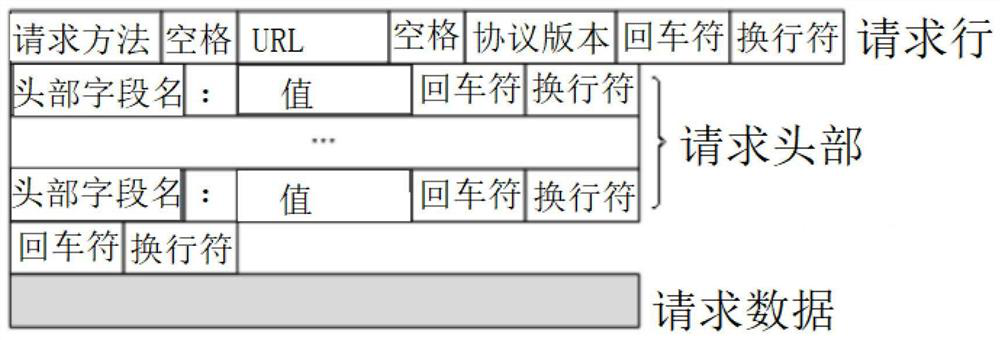
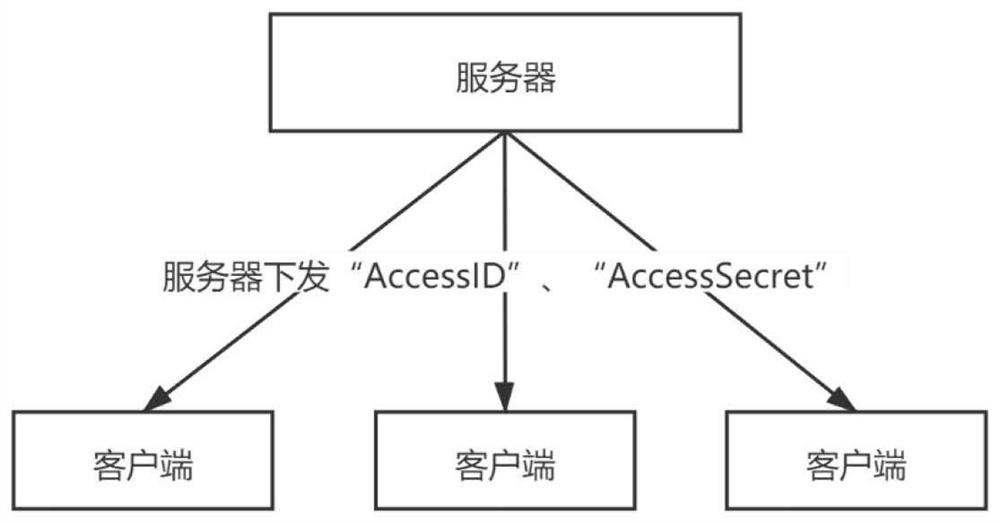
API (Application Program Interface) authentication method and system
A technology of API interface and authentication method, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as hidden dangers, insecurity, and inability to use, and achieve the effect of resisting network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] This embodiment provides an API interface authentication method;
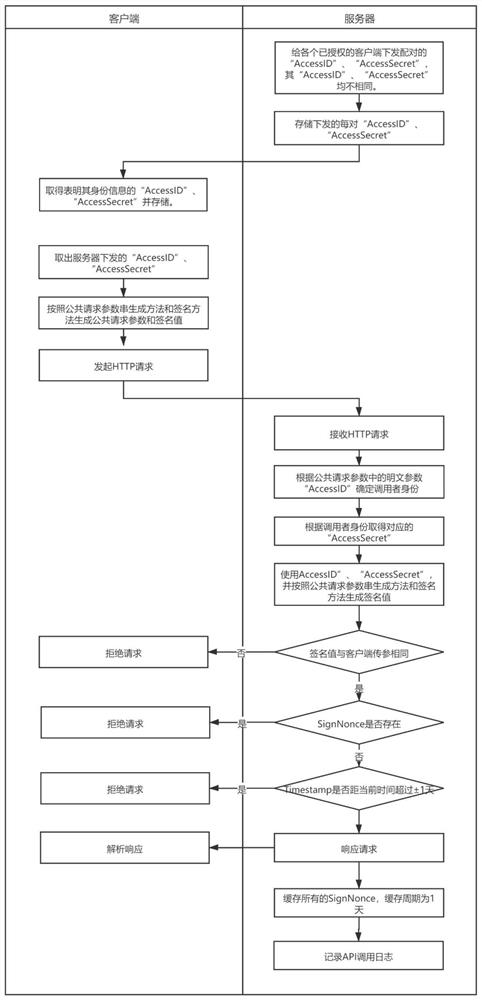
[0051] Such as image 3 As shown, an API interface authentication method is applied to the server, including:
[0052] S101: Receive the HTTP request initiated by the API interface caller client, determine the identity of the API interface caller client, and generate public request parameters and signature values; the HTTP requests are all provided with a public address pre-generated by the API interface caller client. Request parameters and signature values;
[0053]S102: Compare the signature value generated by the server with the signature value transmitted by the client; if the comparison result is the same, proceed to S103; if the comparison result is different, reject the request;
[0054] S103: Determine whether the signature unique random number SignNonce exists; if yes, reject the request; if not, enter S104;
[0055] S104: Determine whether the requested timestamp Timestamp exceeds the set t...
Embodiment 2
[0141] This embodiment provides a server;
[0142] A server configured to:
[0143] Receive the HTTP request initiated by the API interface caller client, determine the identity of the API interface caller client, and generate public request parameters and signature values; the HTTP requests are all provided with public request parameters pre-generated by the API interface caller client and signed value;
[0144] Compare the signature value generated by the server with the signature value transmitted by the client; if the comparison result is the same, go to the next step; if the comparison result is different, reject the request;
[0145] Determine whether the signature unique random number SignNonce exists; if yes, reject the request; if not, go to the next step;
[0146] Determine whether the requested timestamp Timestamp exceeds the set time range from the current moment; if yes, reject the request; if not, respond to the request, cache all signed unique random numbers S...
Embodiment 3
[0149] This embodiment provides an API interface authentication system;
[0150] Such as figure 2 As shown, an API interface authentication system includes: a server and an API interface caller client;
[0151] The API interface caller client initiates an HTTP request to the server; the HTTP request is provided with public request parameters and signature values pre-generated by the API interface caller client;
[0152] The server receives the HTTP request initiated by the API interface caller client, determines the identity of the API interface caller client, and generates public request parameters and signature values;
[0153] The server compares the signature value generated by the server with the signature value transmitted by the client; if the comparison result is the same, it judges whether the signature unique random number SignNonce exists; if the comparison result is different, the request is rejected;
[0154] The server judges whether the signature unique ran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com