Data security access method based on service side
A technology for data security and access methods, applied in the field of computer networks, can solve problems such as poor security and large resource consumption, and achieve the effect of improving security and reducing resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
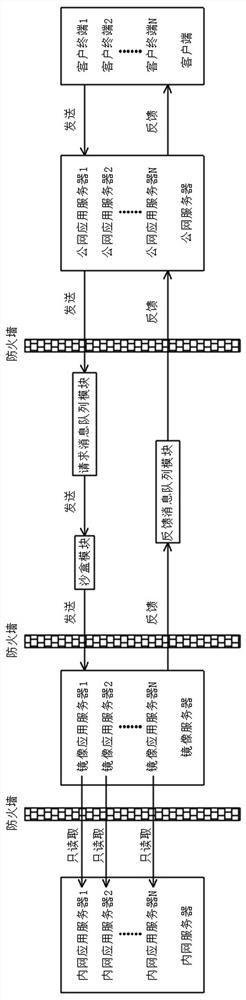
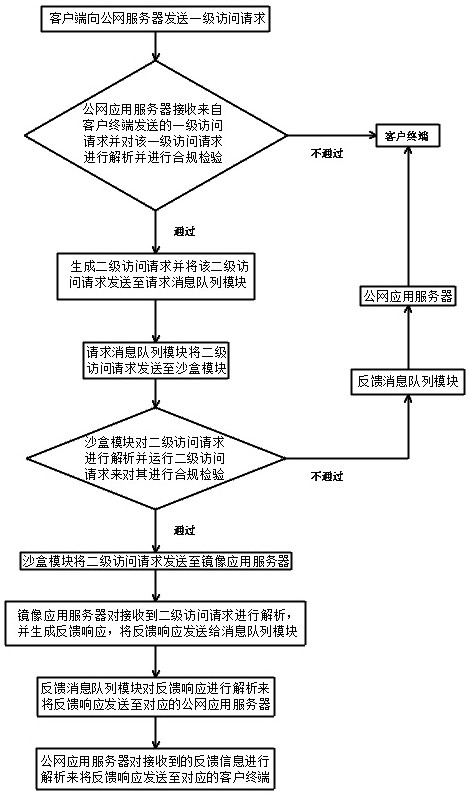
[0040] A service-side-based data security access method in this embodiment, refer to Figure 1-2 : First set up the public network server, message queue module, mirror server and intranet server, and construct the network system of the public network server, message queue module, mirror server, intranet server and terminal equipment. Among them, the public network server includes several public network application servers set in the external network, the message queue module includes a request message queue module and a feedback message queue module, the mirror server includes several mirror application servers, and the intranet server includes Several intranet application servers, the client includes several client terminals set in the extranet.
[0041] It is worth noting that the mirror server can only replicate information in real time to the specified area in the intranet server. In this way, the intranet server can be isolated from the access request through the mirror ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com