Large-scale RFID system lost tag identification method based on balanced collision binary tree
A technology of tag identification and binary tree, applied in the field of radio frequency identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
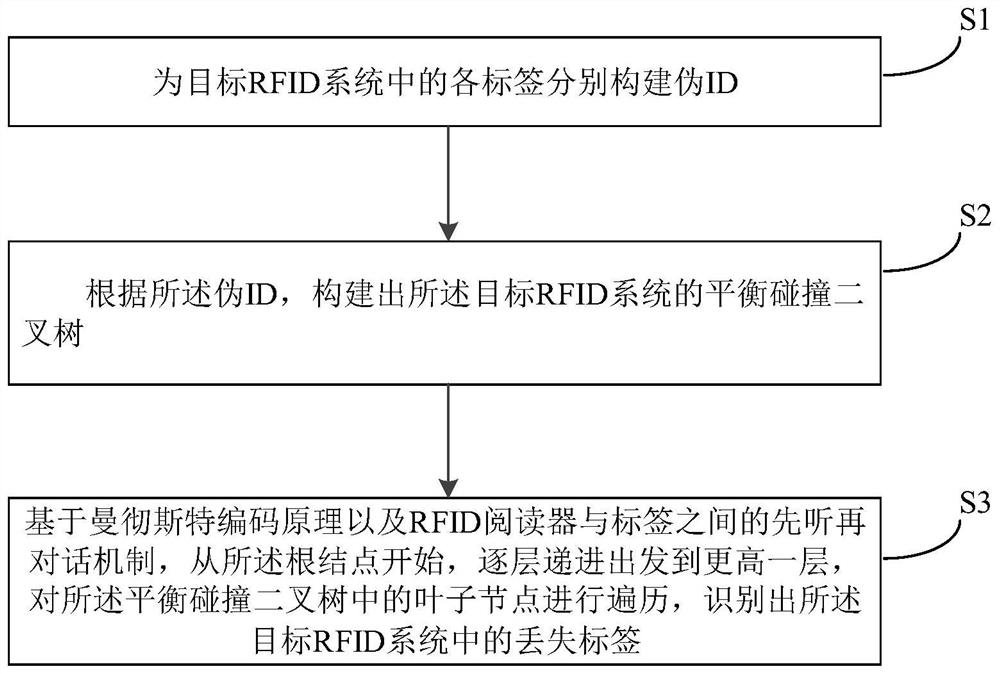
[0057] Please refer to figure 1 , a method for identifying lost tags in a large-scale RFID system based on a balanced collision binary tree, comprising the following steps:
[0058] S1, respectively constructing pseudo IDs for each tag in the target RFID system;
[0059] S2. Construct a balanced collision binary tree of the target RFID system according to the pseudo ID;
[0060] Wherein, the balanced collision binary tree is composed of a root node, a leaf node above the root node with an out-degree of 0, and an internal node with an out-degree of 2; the leaf node is used to execute a singleton time slot or is a collision slot containing two tags; the internal node is only used to store data, and does not perform tag response and identification operations;
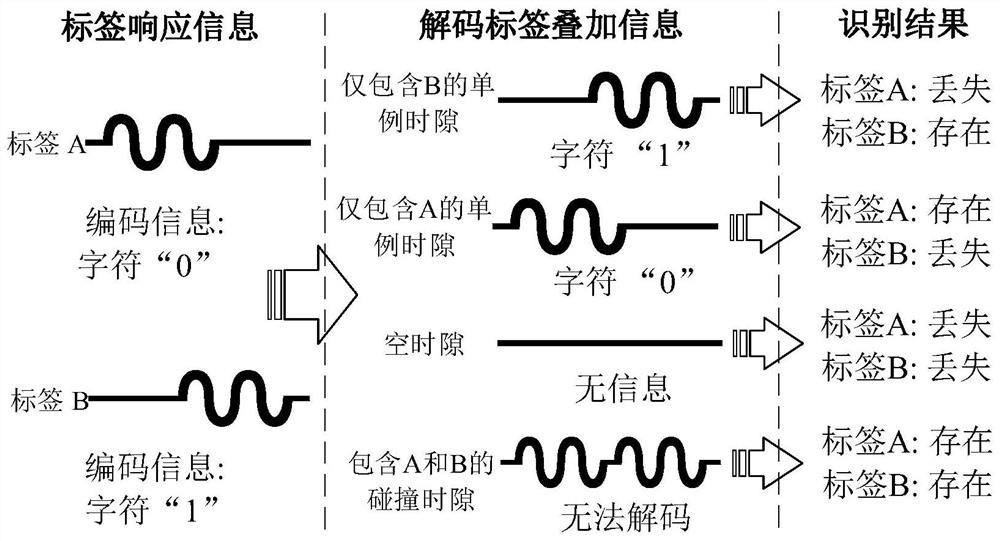
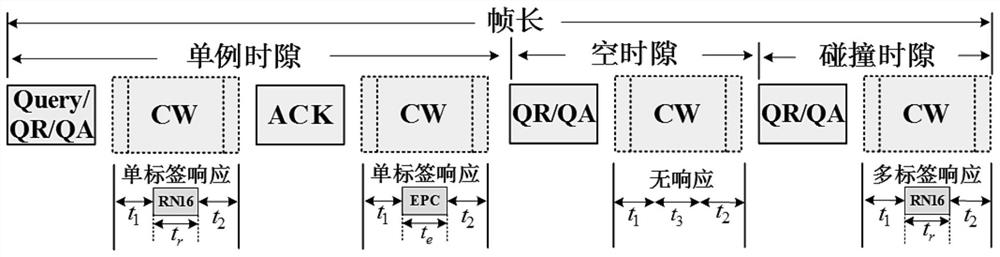
[0061] S3, based on the Manchester coding principle and the first-listen-then-dialogue mechanism between the RFID reader and the tag, starting from the root node, proceeding layer by layer to a higher layer, and collidin...
Embodiment 2
[0117] A large-scale RFID system lost tag recognition system based on a balanced collision binary tree, please refer to Figure 11 , including a pseudo-ID building module 1, a balanced collision binary tree building module 2, and a traversal identification module 3; Connect the traversal identification module 3; wherein:
[0118] The pseudo-ID construction module 1 is used to construct pseudo-IDs for each tag in the target RFID system respectively;
[0119] The balanced collision binary tree construction module 2 is used to construct a balanced collision binary tree of the target RFID system according to the pseudo ID;
[0120]Wherein, the balanced collision binary tree is composed of a root node, a leaf node above the root node with an out-degree of 0, and an internal node with an out-degree of 2; the leaf node is used to execute a singleton time slot or is a collision slot containing two tags; the internal node is only used to store data, and does not perform tag response ...
Embodiment 3
[0123] A medium on which a computer program is stored, and when the computer program is executed by a processor, the steps of the method for identifying lost tags in a large-scale RFID system based on a balanced collision binary tree in Embodiment 1 are realized.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com