Abnormal traffic processing method and system based on combination of TR069 protocol and log analysis
A technology of abnormal traffic and processing method, applied in the field of abnormal traffic, can solve the problems of lack of timeliness and low accuracy of analysis and filtering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings.
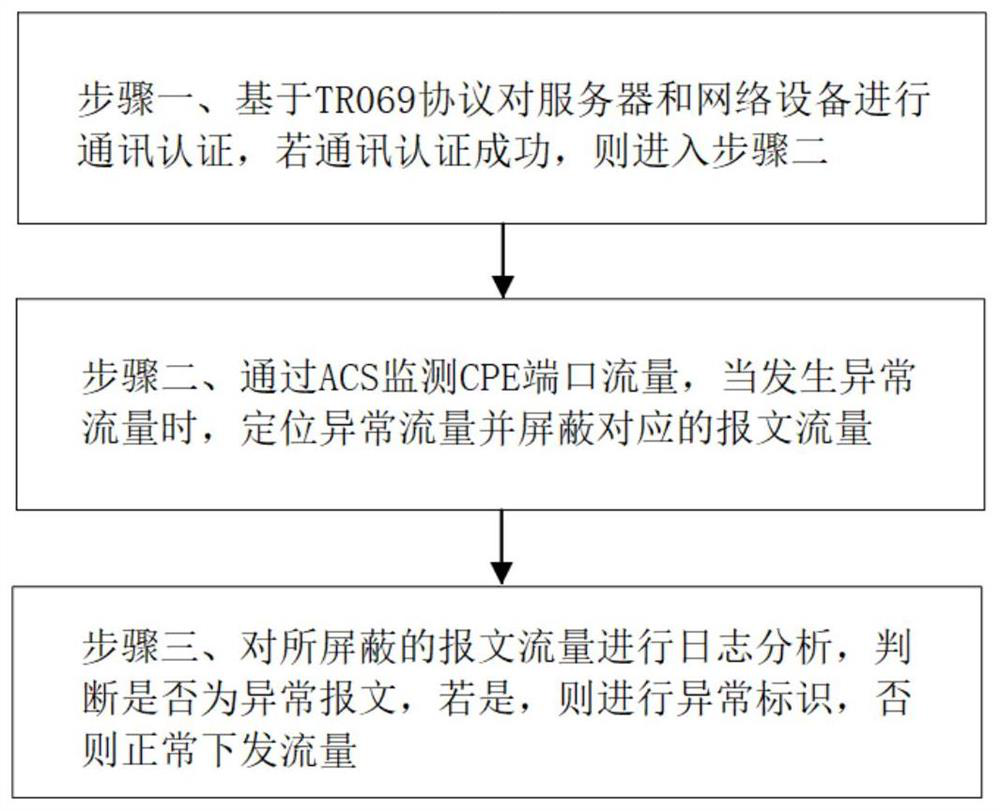
[0044] see figure 1 , the present invention is based on the TR069 protocol combined with log analysis method for dealing with abnormal traffic, including:
[0045] Step 1. The device verification module performs communication verification on the server and network device based on the TR069 protocol. If the communication verification is successful, enter step 2, specifically:
[0046] Manage and monitor network devices that support TR069 protocol based on TR069 protocol;
[0047] The program deployed by the network management server ACS in the TR069 protocol is actively executed to complete the communication authentication configuration operation for the CPE. If the communication authentication is successful, go to step 2.
[0048] In TR-069, the network management server is called ACS (Auto Configuration Server).
[0049] Step 2. The traffic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com