Anti-counterfeiting method for network access living body authentication image of telecommunication user
A technology of living body authentication and living body image, applied in image data processing, image data processing, instruments, etc., can solve the problems of fixed encryption method and cracking by criminals, and achieve the effect of ensuring efficiency, strong performance, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
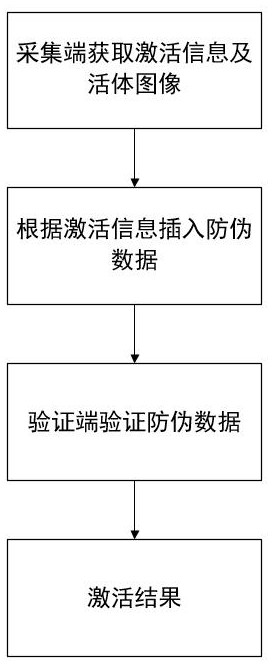
[0035] An anti-counterfeiting method for live body authentication images of telecom users, comprising the following steps:
[0036] Step 1, the acquisition terminal acquires activation information and live images;
[0037] Step 2, inserting anti-counterfeiting data according to the activation information;
[0038] Step 3, the verifier verifies the anti-counterfeiting data;
[0039] Step 4, output the activation result.
Embodiment 2
[0041] An anti-counterfeiting method for live body authentication images of telecom users, comprising the following steps:
[0042] Step 1, the acquisition terminal acquires activation information and live images;
[0043] The activation information is an ID number; the live image can be acquired by a camera at the collection end.
[0044] Step 2, inserting anti-counterfeiting data according to the activation information;
[0045] The process of inserting anti-counterfeiting data according to the activation information includes:
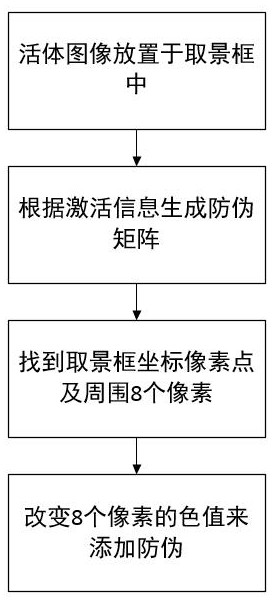
[0046] 21) Place the live image in the viewfinder, the size of the viewfinder is x*y;
[0047] 22) Generate an anti-counterfeiting matrix according to the activation information;
[0048] 23) Find the coordinate pixel of the viewfinder frame and its surrounding 8 pixels;
[0049] 24) Change the color value of the 8 pixels around the frame coordinate pixel to add anti-counterfeiting.
[0050] Step 3, the verifier verifies the anti-counterfeiting ...
Embodiment 3
[0057] An anti-counterfeiting method for live body authentication images of telecom users, comprising the following steps:
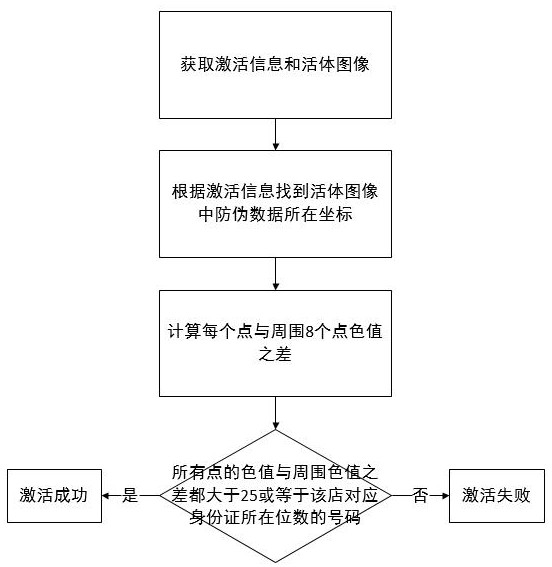
[0058] Step 1, the acquisition terminal acquires activation information and live images;
[0059] The activation information is an ID number; the live image can be acquired by a camera at the collection end.
[0060] Step 2, inserting anti-counterfeiting data according to the activation information;
[0061] The process of inserting anti-counterfeiting data according to the activation information includes:
[0062] 21) Place the live image in the viewfinder, the size of the viewfinder is x*y;
[0063] 22) Generate an anti-counterfeiting matrix according to the activation information;
[0064] 23) Find the coordinate pixel of the viewfinder frame and its surrounding 8 pixels;
[0065] 24) Change the color value of the 8 pixels around the frame coordinate pixel to add anti-counterfeiting.
[0066] The specific process of generating the anti-counterfei...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com