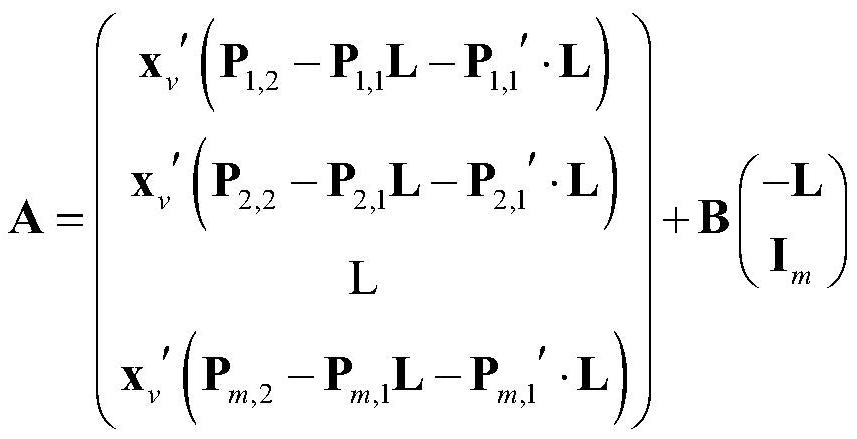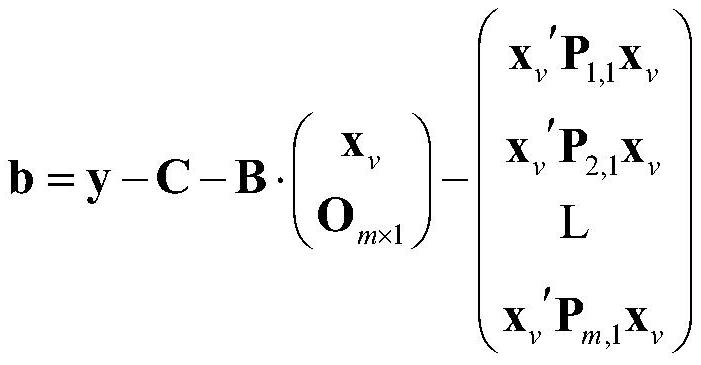Quantum-computing-resistant identity-based digital signature scheme
A digital signature and quantum computing technology, which is applied in the field of information security, can solve problems such as large amount of calculation and inability to resist quantum computing, and achieve the effect of strong implementation performance, improved security, and simple calculation form
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
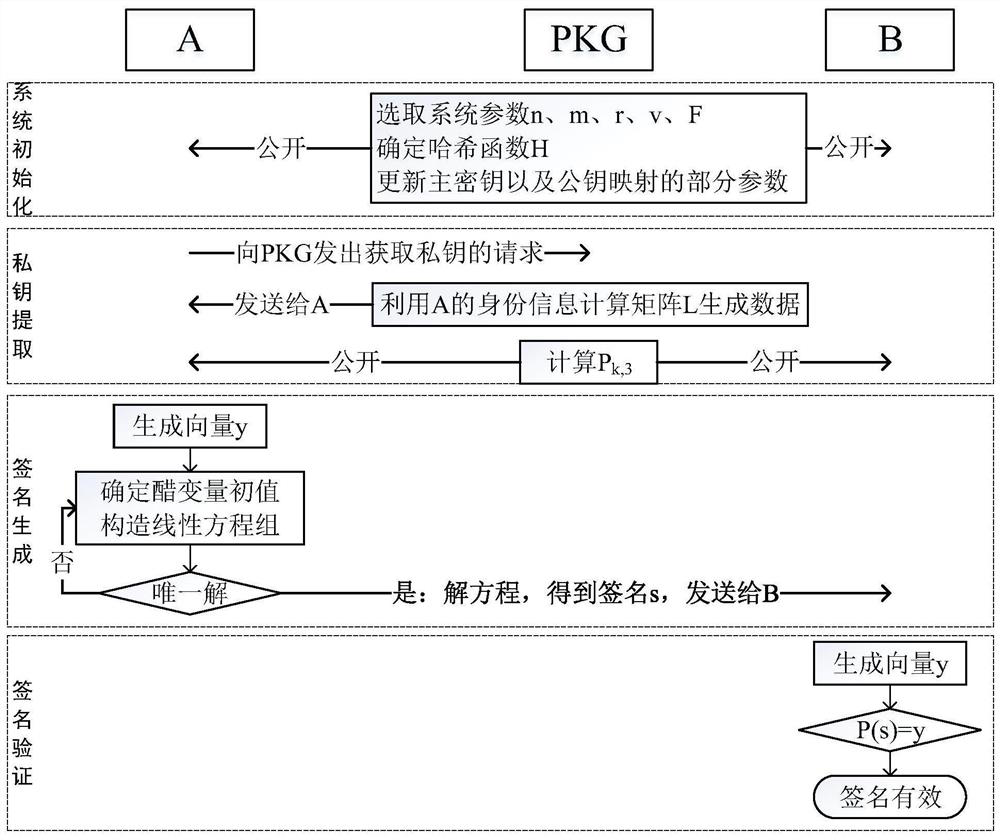
[0073] The identity-based digital signature proposed by the present invention will be described below in combination with specific implementation methods.
[0074] Define A and B as protocol participants, A as the signer, B as the verifier, PKG as the trusted key generator, and generate signatures in the following four stages.
[0075] 1. System initialization
[0076] 1.1.PKG selects appropriate integers n, m and r, remembers v=n-m, and determines the finite field F=GF(2 r )structure.
[0077] 1.2. The hash function H used in the PKG determination scheme.
[0078] 1.3. PKG updates the master key, updates some parameters B, C and P of the public key mapping P k,1 ,P k,2 ,1≤k≤m (if no
[0079] Update the public key mapping P, you can skip this step):
[0080] PKG randomly selects the system master key masterKey, and performs the following operations:
[0081] dataPk=masterKey Ptimestamp
[0082] For k=1 to m
[0083] dataPk=H(dataPk,v 2 )
[0084] P k,1 =assignment(...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com