Trusted root management method and device, equipment and storage medium
A management method and technology of root of trust, applied in the field of information security, can solve the problems of application scenarios that are difficult to support a single server, high complexity of virtual root of trust, limited computing power, etc., to improve convenience, enhance security, The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0022] Unless otherwise defined, all technical and scientific terms used herein have the same meaning as commonly understood by one of ordinary skill in the technical field of the invention. The terms used herein in the description of the present invention are for the purpose of describing specific embodiments only, and are not intended to limit the present invention.
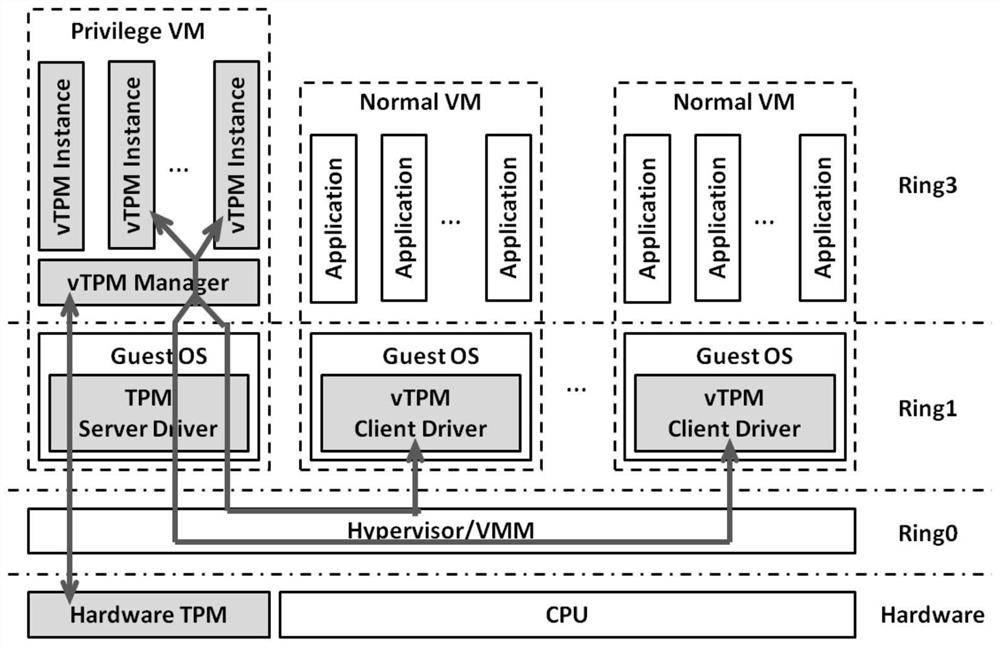
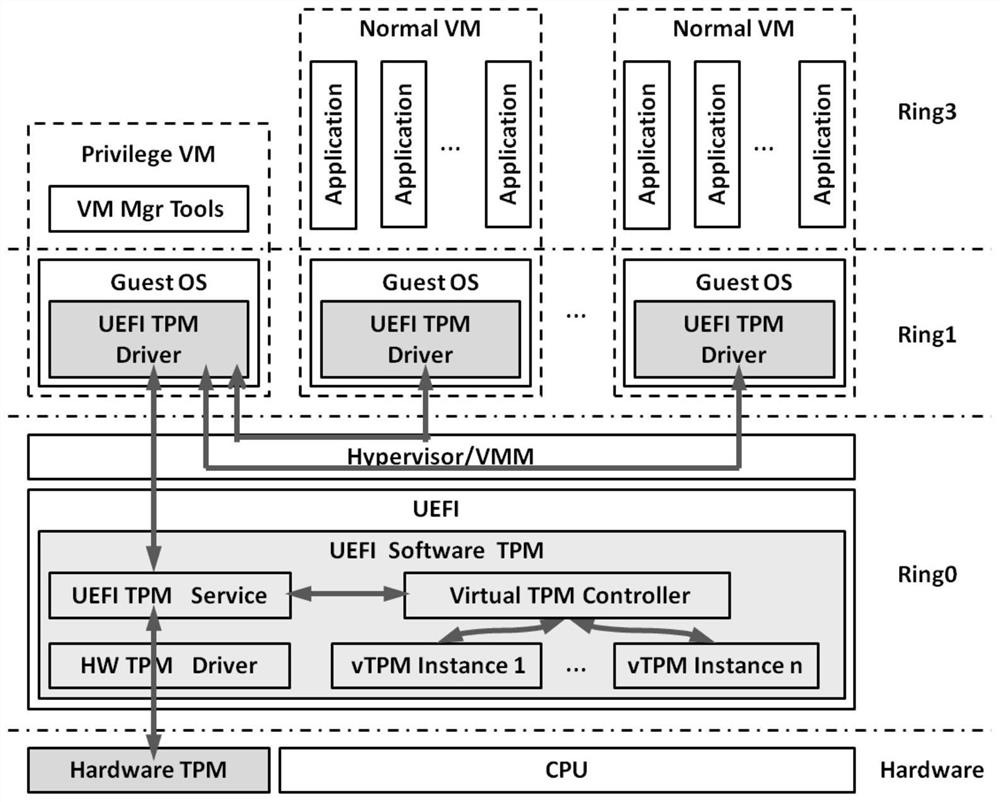
[0023] Due to the establishment of a virtual root of trust server, the use of the virtual root of trust is complicated, the management cost is high, and it is difficult to support many single-server application scenarios. In related technologies, a virtual trusted root manager can also be built on a Hypervisor (virtual machine manager, also known as a VMM (virtual machine monitor)), so as to generate and manage a virtual trusted root manager for a virtual machine running on the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com