Asynchronous strike anti-hotlinking method and system based on CDN edge computing network
An edge computing and anti-theft link technology, applied in the Internet field, can solve problems such as complex authentication strategies, achieve the effects of reducing real-time configuration requirements, strengthening strikes, and solving poor real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
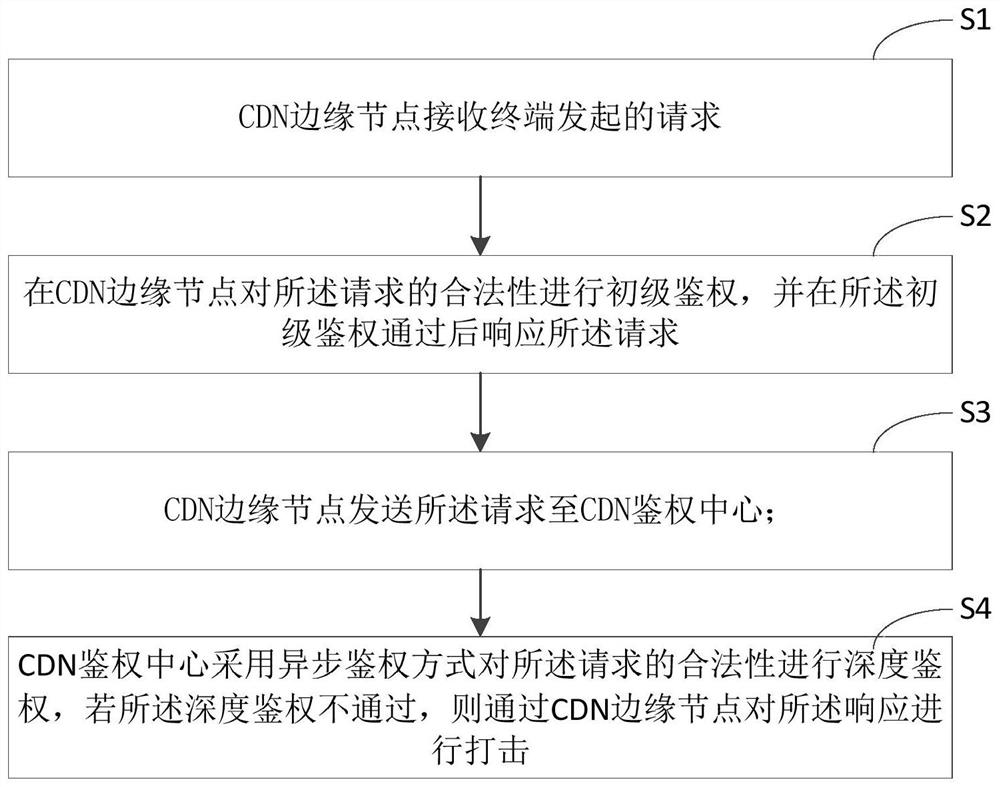
[0060] Such as figure 1 As shown, a method for asynchronously combating anti-leech chaining based on a CDN edge computing network in an embodiment of the present invention includes the following steps:
[0061] S1: The CDN edge node receives the request initiated by the user terminal client.
[0062] Specifically, the user terminal client initiates a content request to the CDN edge node carrying the request verification information according to the rules. For example: https: / / play.livestream.baidu.com / xxxxxxx? k1=v1&k2=v2, where the verification parameters such as k1 and k2 can be defined according to the agreement.
[0063] S2: Perform primary authentication on the legality of the request at the CDN edge node according to local authentication rules, and respond to the request after the primary authentication is passed.
[0064] Specifically, the primary authentication specifically refers to authentication using a common, conventional authentication strategy with low authen...
Embodiment 2
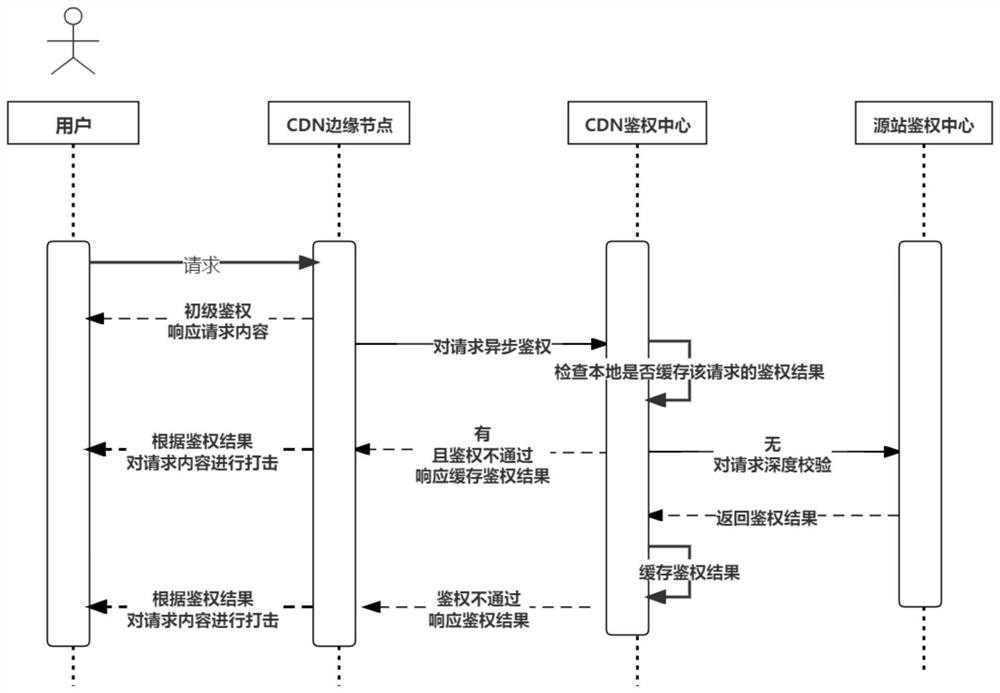
[0093] In this embodiment, on the basis of the first embodiment, the process of performing in-depth authentication in an asynchronous authentication mode by the asynchronous strike system is further limited.
[0094] see figure 2 , in this embodiment, the S4 of Embodiment 1 may specifically include:
[0095] S41: The CDN authentication center judges whether a cached authentication result corresponding to the request is cached locally, and the cached authentication result is within the validity period;
[0096] If there is a valid cached authentication result, when the corresponding authentication of the cached authentication result fails, the CDN edge node will strike against the response according to the cached authentication result; When the corresponding authentication is passed, no action is taken, and the CDN edge node continues to respond to the request content;
[0097] If there is no valid cached authentication result, send the request to the source site authenticat...
Embodiment 3
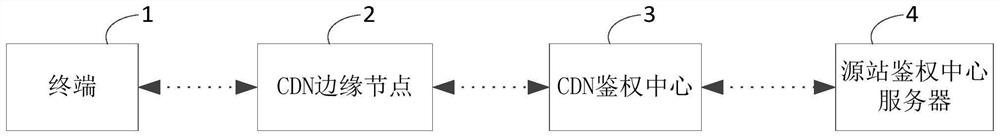
[0125] This embodiment corresponds to the above-mentioned embodiments, and provides an asynchronous anti-leeching system based on CDN edge computing network, please refer to figure 2 and image 3 , the system includes: a communication-connected terminal 1, a CDN edge node 2, and a CDN authentication center 3;
[0126] The CDN edge node 2 is used to receive the request initiated by the terminal; and to perform primary authentication on the legitimacy of the request, and to respond to the request after the primary authentication is passed; and to send the Request to the CDN authentication center;
[0127] The CDN authentication center 3 is used to perform in-depth authentication on the legitimacy of the request in an asynchronous authentication manner, and if the in-depth authentication fails, strike the response through the CDN edge node;
[0128] Wherein, the authentication complexity of the primary authentication is lower than the complexity of the deep authentication.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com