Scalable authentication for trusted execution environments
An execution environment and authentication technology, applied in user identity/authority verification, secure communication devices, instruments, etc., can solve problems such as no operating system protection, inability to access memory, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
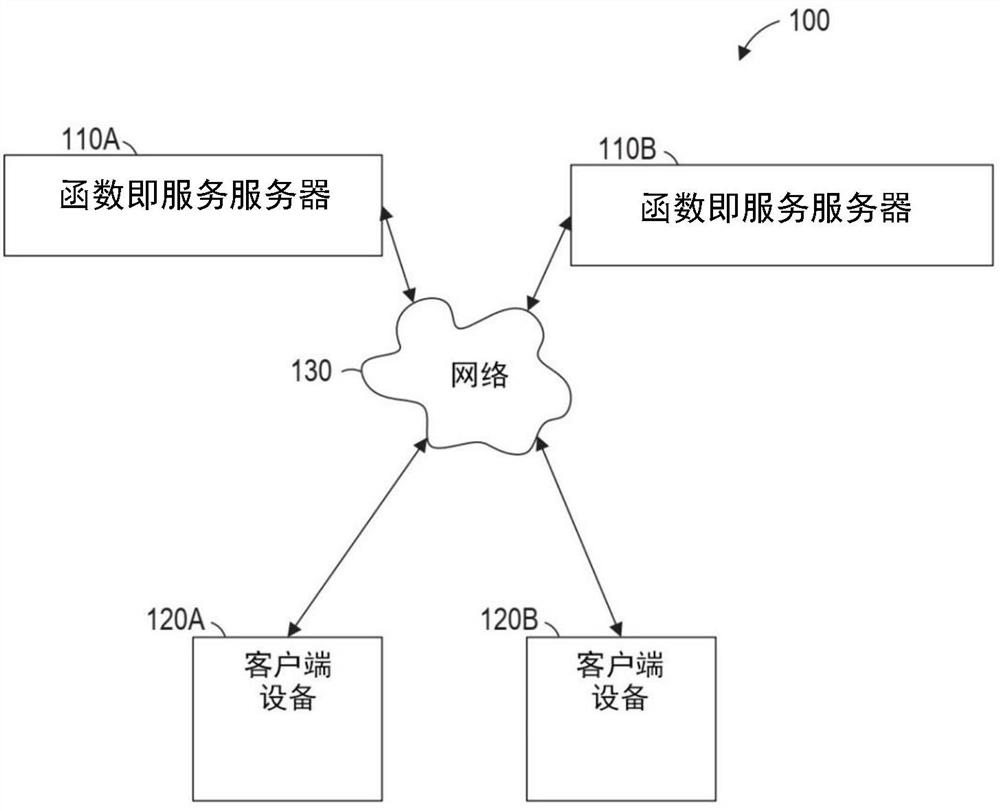
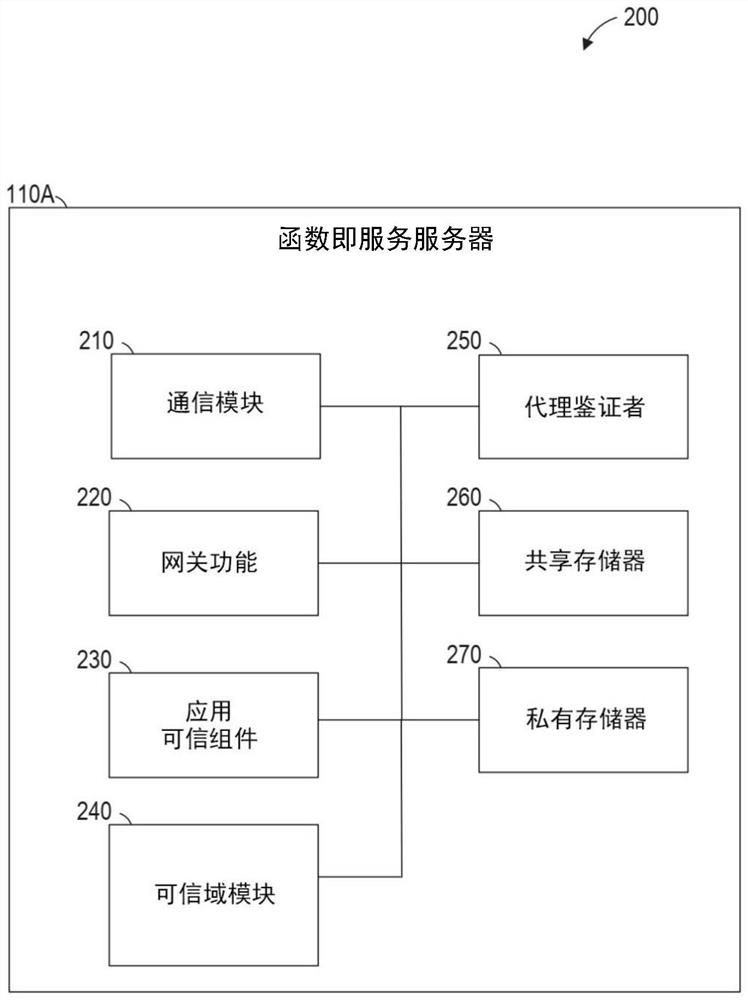
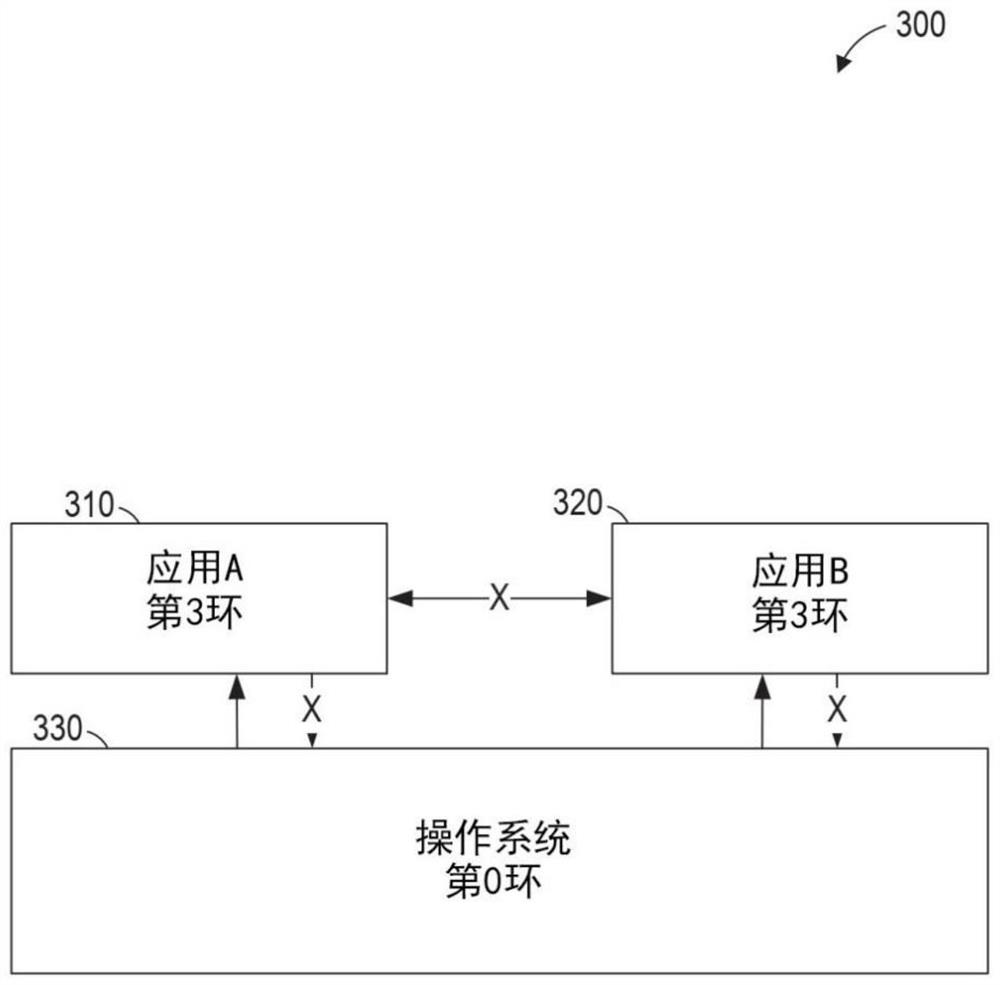
[0089]Example 1 is a system for providing remote attestation of a trusted execution environment (TEE), the system comprising: at least one processor; a network interface operatively coupled to the processor; and coupled to the at least one processor to a memory storing instructions that, when executed by the processor, cause the at least one processor to perform operations comprising: creating a first TEE for a first function; creating a second TEE for a second function; providing a gateway for remote access to the first function; receiving a request from a client device via the network interface to verify the integrity of the second TEE; and in response to the request: executing the first function for all generating authentication data by the second TEE; and providing the authentication data to the client device via the network interface.
[0090] In example 2, the subject matter of example 1 includes, wherein generating the attestation data for the second TEE includes genera...
example 11
[0099] Example 11 is a method of providing remote attestation of a trusted execution environment (TEE), the method comprising: creating, by a processor, a first TEE for a first function; creating, by the processor, a second TEE for a second function; the processor provides a gateway for remote access to the first function; receives a request from a client device via a network interface to verify the integrity of the second TEE; in response to the request: performing the processing by the processor; generating authentication data for the second TEE by the first function; and providing the authentication data to the client device via the network interface.
[0100] In Example 12, the subject matter of Example 11 includes, wherein generating the attestation data for the second TEE includes generating a signature structure from within the second TEE, the signature structure including an identity of the second TEE , attributes of the second TEE, and a message authentication code (M...
example 21
[0109] Example 21 is a non-transitory computer-readable medium having instructions for causing at least one processor to provide remote attestation of a Trusted Execution Environment (TEE) by performing operations comprising: creating a first function for a first function. a TEE; creating a second TEE for a second function; providing a gateway for remote access to the first function; receiving a request from a client device via a network interface to verify the integrity of the second TEE; responding to the request : executing the first function to generate authentication data for the second TEE; and providing the authentication data to the client device via the network interface.
[0110] In Example 22, the subject matter of Example 21 includes, wherein generating the attestation data for the second TEE includes generating a signature structure from within the second TEE, the signature structure including an identity of the second TEE , attributes of the second TEE, and a mes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com