Botnet software detection method based on API calling and network behaviors
A technology of API calling and software detection, applied in the field of computer science, can solve the problem of less malicious code identification, achieve the effect of improving accuracy, improving efficiency, and reducing the size of the graph
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
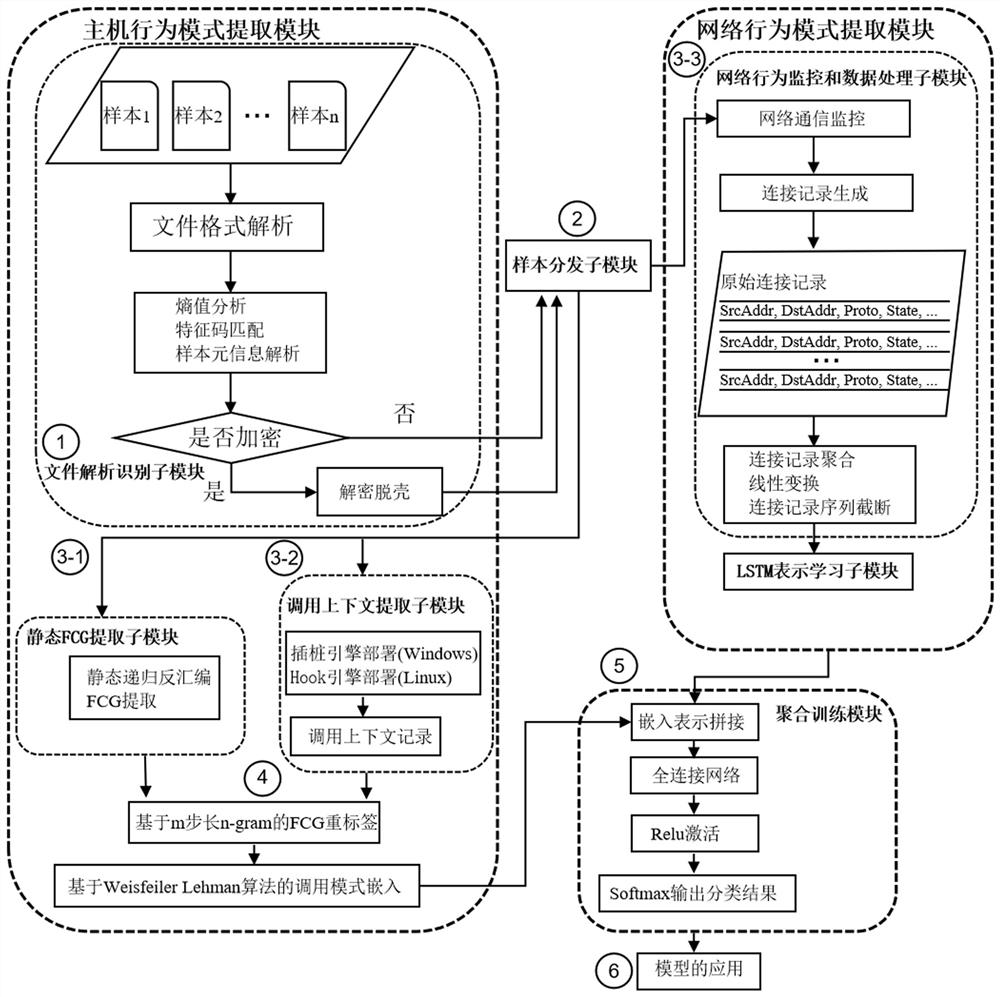
[0028] like figure 1 As shown, a method for detecting bots based on API calls and network behaviors includes the following steps:
[0029] A method for detecting bots based on API calls and network behaviors, comprising a host behavior pattern extraction layer module, a network behavior pattern extraction layer module and an aggregation training module; wherein:
[0030] 1) The host behavior pattern extraction layer module, including the file parsing and identification sub-module, the static FCG extraction sub-module, the sample distribution sub-module and the calling context extraction sub-module, as follows:
[0031] 1-1) Analysis and identification of sample files: The file analysis and identification sub-module uses the signature database of various files to identify the type of executable program, and analyzes the sample to be analyzed using a specific file format to obtain its file meta information, import table and symbol table; and determine whether the sample file is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com