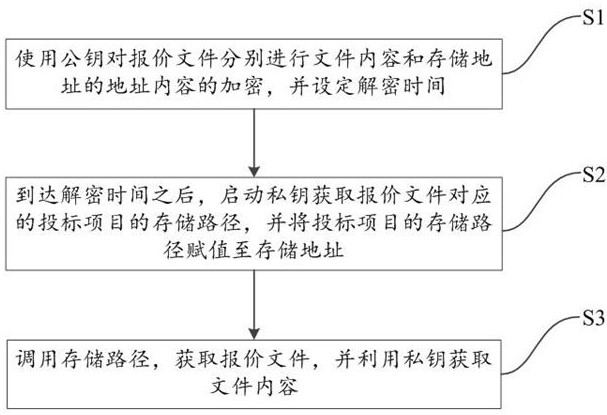
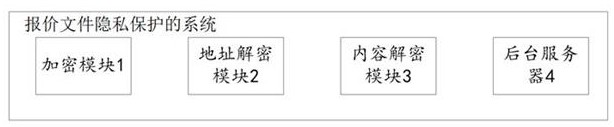
Quotation file privacy protection method and system
A privacy protection and file technology, applied in the field of data encryption and decryption, can solve the problems of easy cracking and poor data security, and achieve the effect of improving user experience, improving confidentiality performance, and overcoming easy cracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] For a better understanding of the present application, various aspects of the present application will be described in more detail with reference to the accompanying drawings. It should be understood that these detailed descriptions are merely illustrative of exemplary embodiments of the present application and are not intended to limit the scope of the present application in any way. Throughout the specification, the same reference numerals refer to the same elements. The expression "and / or" includes any and all combinations of one or more of the associated listed items.
[0021] In the drawings, the size, size, and shape of elements have been slightly adjusted for ease of illustration. The drawings are examples only and are not drawn strictly to scale. As used herein, the terms "approximately," "approximately," and similar terms are used as terms of approximation, not of degree, and are intended to describe measurements that would be recognized by those of ordinary ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com