Method for realizing data exchange between two different mutually isolated networks
A technology for network data and data exchange, which is applied in the field of data exchange and can solve problems such as low data exchange efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
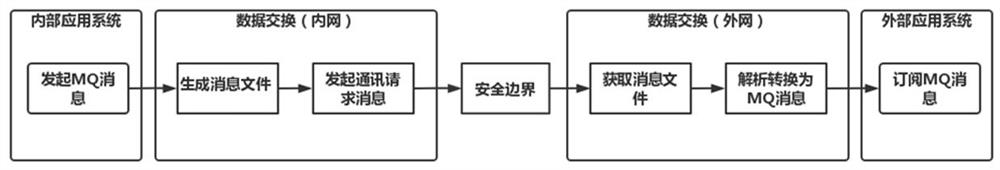
[0026] combine figure 1 As shown, a method for realizing data exchange between two different networks that are isolated from each other includes:
[0027] Step A1, the first application system (internal application system) sends an MQ message to the first network data exchange system (data exchange (intranet)), the data exchange (intranet) obtains the MQ message and converts it into a message file, and sends the MQ message to the security boundary ( Gatekeeper or one-way import device) initiates a communication request message;
[0028] Step A2, the security boundary ferries the message file to the second network data exchange system (data exchange (external network)) in the form of file ferry or TCP message;
[0029] Step A3: The data exchange (external network) parses the message file and converts it into an MQ message for subscription and consumption by the second application system (external application system).
[0030] In the MQ asynchronous operation mode, the externa...
Embodiment 2
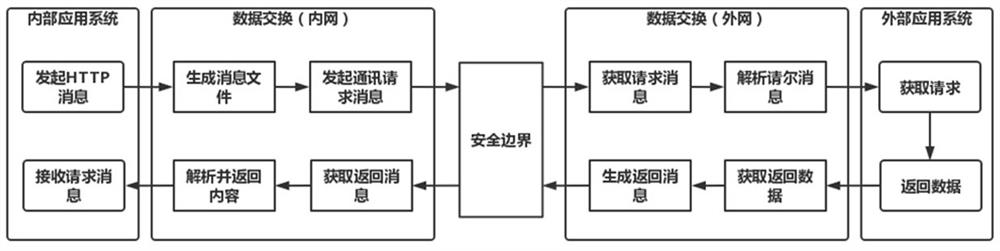
[0032] combine figure 2 As shown, when the first application system is an internal application system, the first network data exchange system is an intranet data exchange system, the second application system is an external application system, and the second network data exchange system is an external network data exchange system, a A method to achieve data exchange between two different networks that are isolated from each other, including:
[0033] Step B1, the internal application system sends an HTTP message to the intranet data exchange system (data exchange (intranet)), the data exchange (intranet) obtains the HTTP message and converts it into a message file, and initiates a communication request message to the security boundary;
[0034] Step B2, the security boundary ferries the request message to the external network data exchange system (data exchange (external network)) in the form of file ferry or TCP message;
[0035] Step B3, (the data exchange (external networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com