Identity authentication method based on non-homogeneous token, network equipment and terminal storage equipment
An identity authentication and non-homogeneous technology, which is applied in the field of identity authentication methods based on non-homogeneous certificates, network equipment and terminal storage devices, can solve problems such as user inconvenience, false information, and attacks, and prevent data tampering Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0080] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. It should be noted that the specific implementation of this example is based on the premise of this technology, and a detailed implementation process and implementation steps are given, but the protection scope of the present invention is not limited to Not limited to this embodiment.
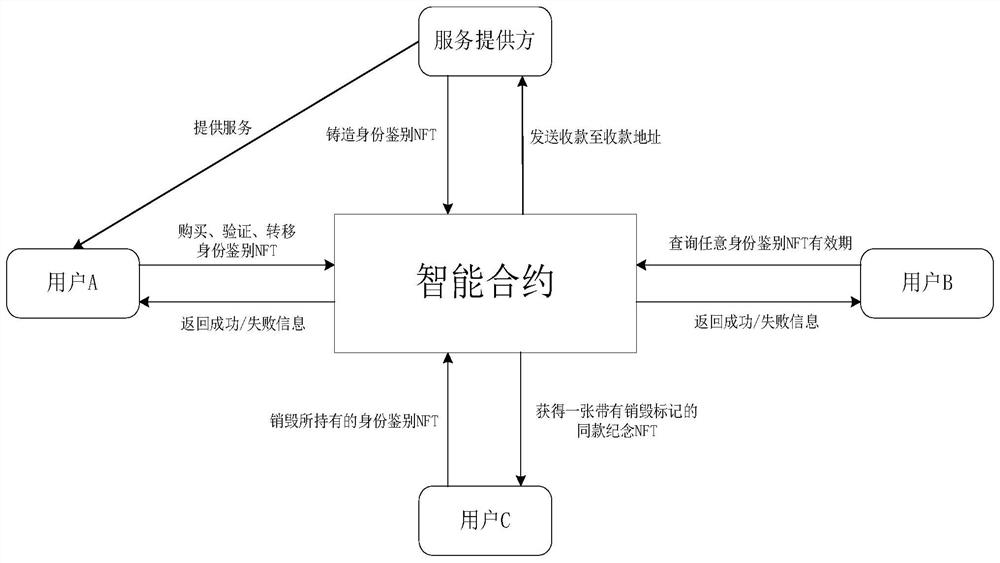
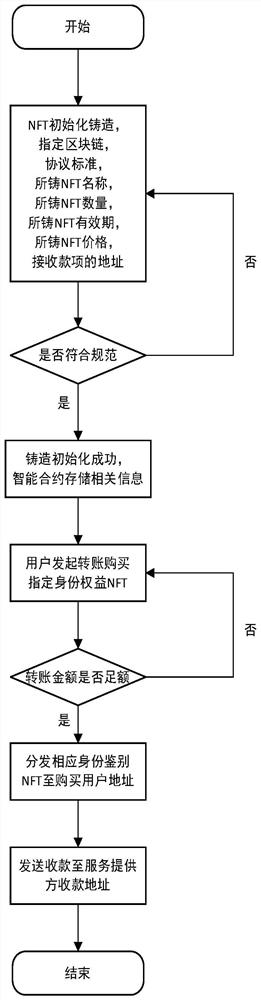
[0081] like figure 1 Character interaction diagram and figure 2 The identity authentication NFT casting and distribution flow chart shows that the service provider, that is, the minting party, invokes the smart contract to initialize the NFT casting. The user purchases the NFT corresponding to the identity rights, and the smart contract or the service provider distributes the NFT to the purchasing user. The main steps are as follows:
[0082] Step 1.1 Smart contract deployment and initialization, on the supported public chain, alliance chain or private chain, co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com