Java third-party dependency vulnerability detection method and system and storage medium
A vulnerability detection and dependency technology, applied in the direction of platform integrity maintenance, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
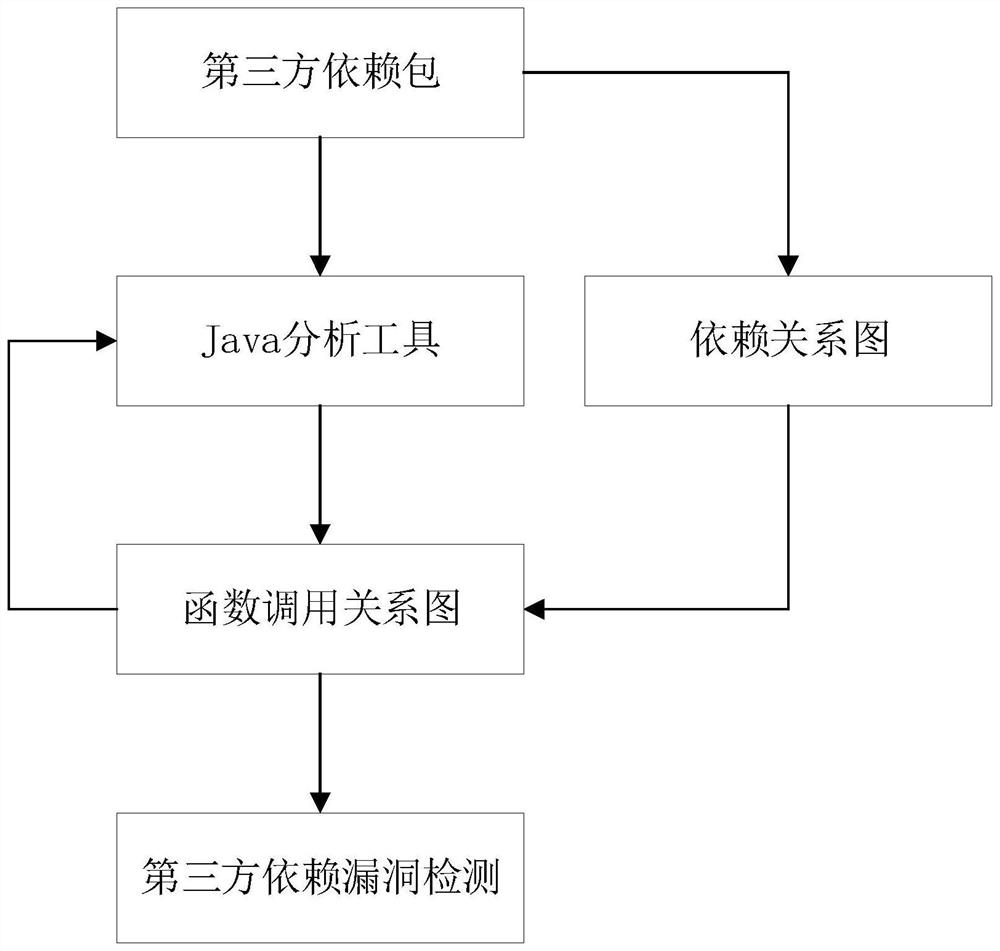
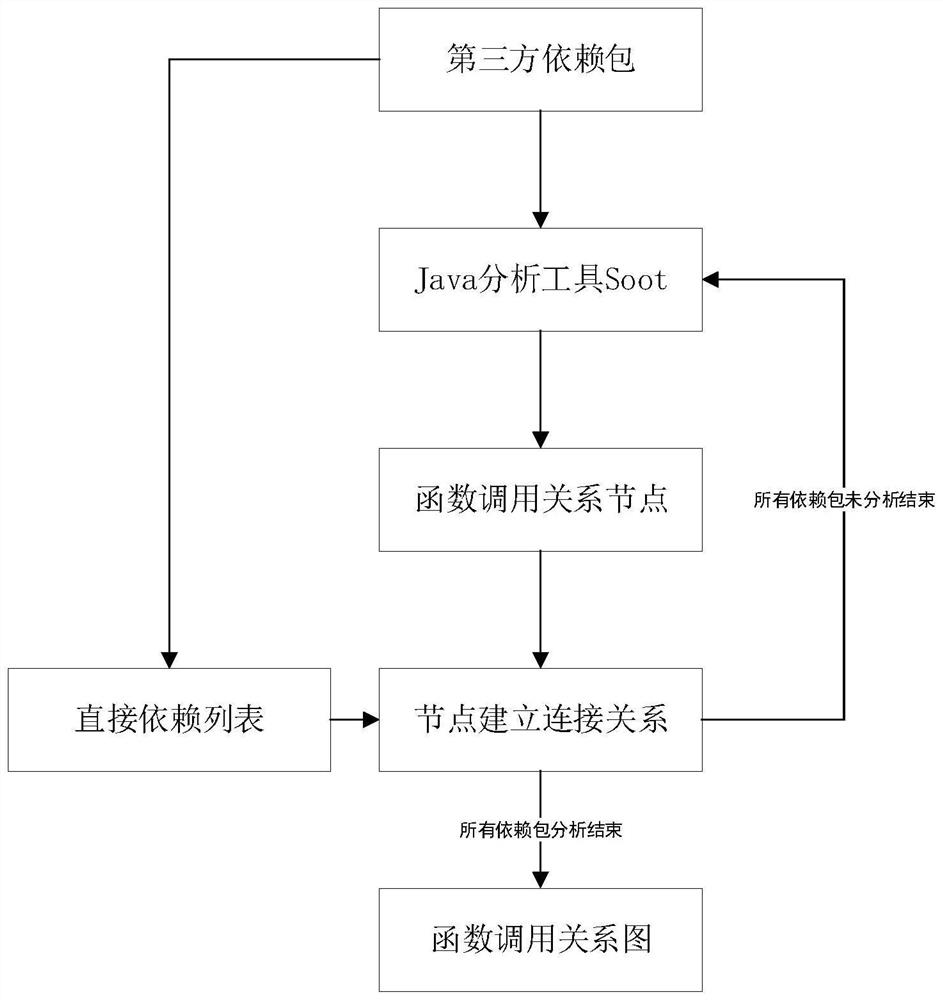
[0038] like figure 1 As shown, it is an overall flow chart of a Java third-party dependency vulnerability detection method provided by an embodiment of the present invention, and the specific steps are as follows:
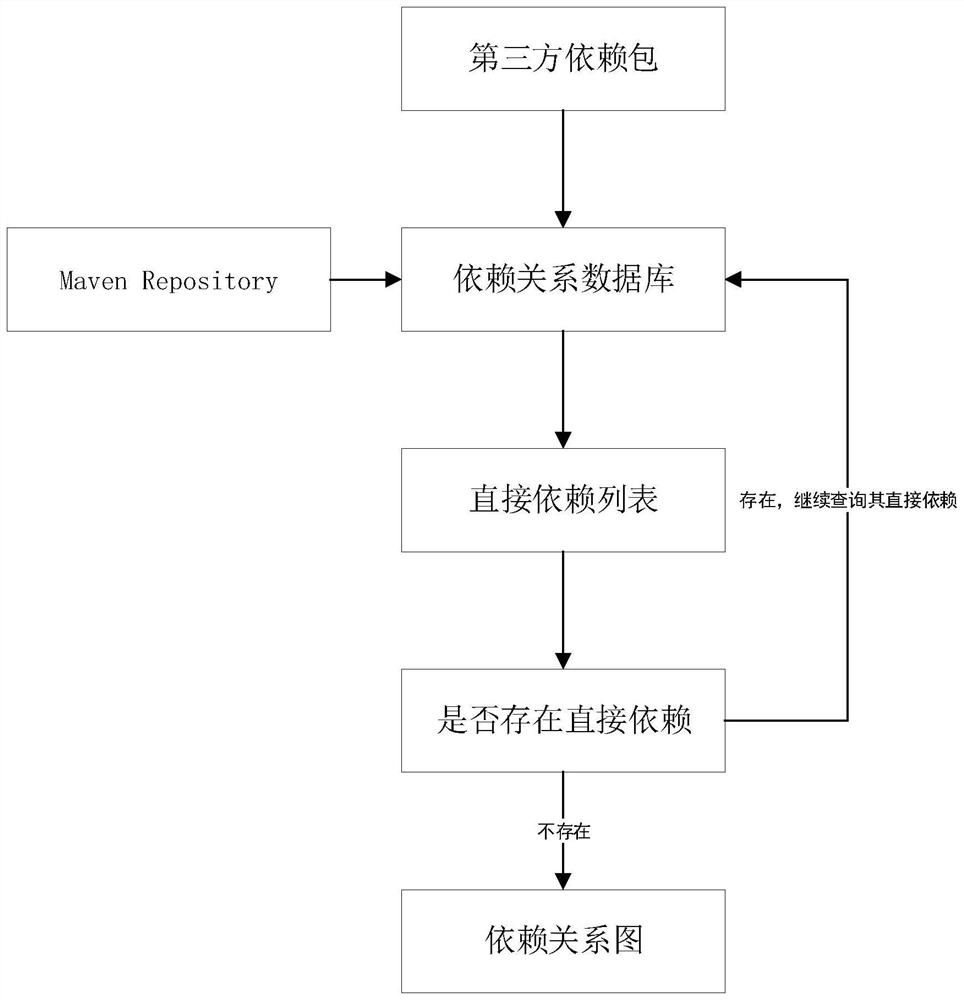
[0039] To query the dependency graph of the third-party dependencies to be detected, you need to obtain the dependencies of the third-party dependencies in MavenRepository, build the corresponding dependency database, and store the third-party dependencies in the database.
[0040] The specific process is as figure 2 As shown, when querying the third-party dependencies that need to be detected, all related third-party dependencies are found from the database. First, the direct dependencies are obtained from the dependency database, and then the first-level dependencies are obtained in turn. For their directly related dependencies, repeat this operation until the dependencies have no direct related dependencies, so as to obtain the third-party dependency graph to ...
Embodiment 2
[0062] The present invention also provides a Java third-party dependency vulnerability detection system and a computer-readable storage medium. The detection system includes a processor and a storage medium, wherein the storage medium is used to store instructions, and the processor is used to operate according to the instructions to execute a Java first-order storage medium. The steps of the third-party-dependent vulnerability detection method.
Embodiment 3
[0064] A computer program is stored on the computer-readable storage medium, and when the program is executed by the processor, implements the steps of a Java third-party dependency vulnerability detection method.
[0065] As will be appreciated by those skilled in the art, the embodiments of the present application may be provided as a method, a system, or a computer program product. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including, but not limited to, disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com