Message safety protection method based on boundary gateway protocol message
A border gateway protocol and security protection technology, applied in data exchange details, user identity/authority verification, data collection prevention, etc., can solve problems such as routing black holes, damage, and hidden dangers of data bureau message transmission mechanism, and achieve The effect of protecting safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
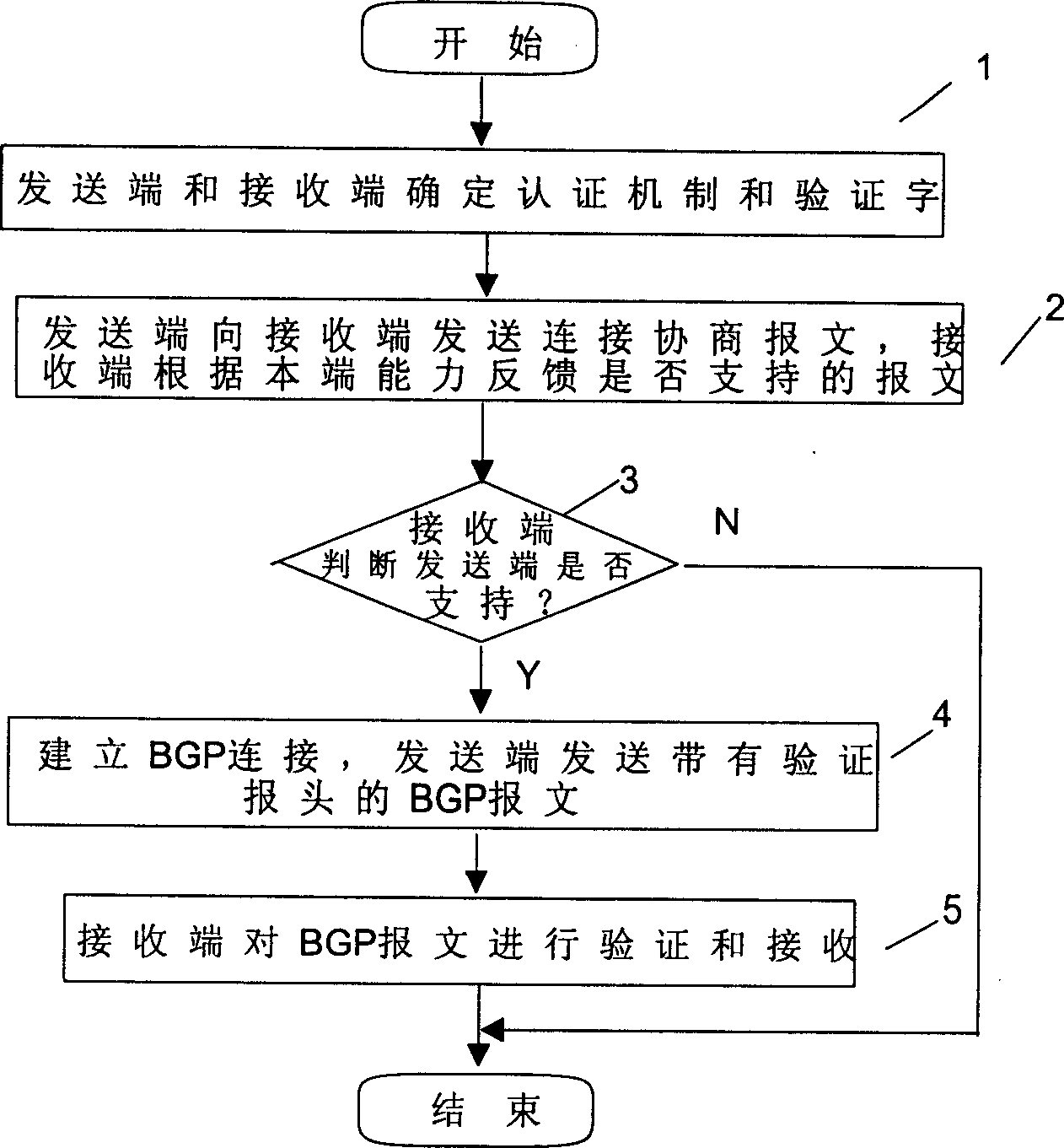
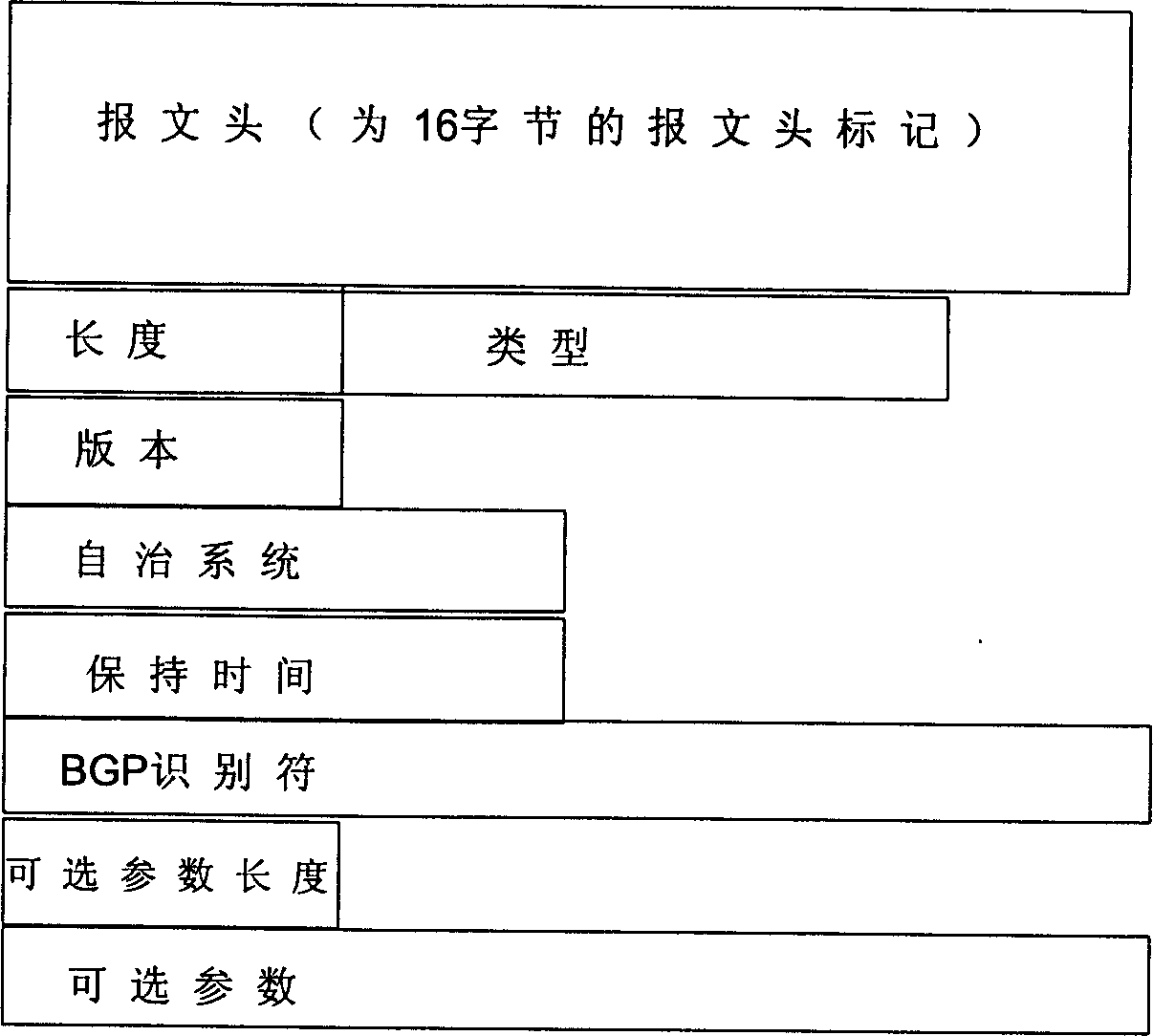
[0018] The realization of the present invention is that when establishing a BGP connection, both sides of the sending end and the receiving end of the BGP message exchange verification words through the OPEN message, so that after the ability negotiation to the message verification, the first 16 bits of the message header based on the BGP protocol are changed. Byte mark field, that is, use the BGP message header mark field to dynamically verify the message, so as to realize the protection of the entire BGP message, and thus protect the BGP connection. Although the illegal person can intercept the BGP message from the TCP message flow, but because the header of the BGP is not known, the message has no way to synchronize, so the specific content of the BGP message cannot be obtained.
[0019] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0020] figure 1 It is an embodiment flowchart of the method of the present ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com