Short message security method and SIM card for implementing short message security
A security method and short message technology, applied in the field of short message security and SIM card, can solve the problems of low reliability, can not effectively prevent personal privacy leakage, etc., achieve the effect of good use flexibility and improve the reliability of encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
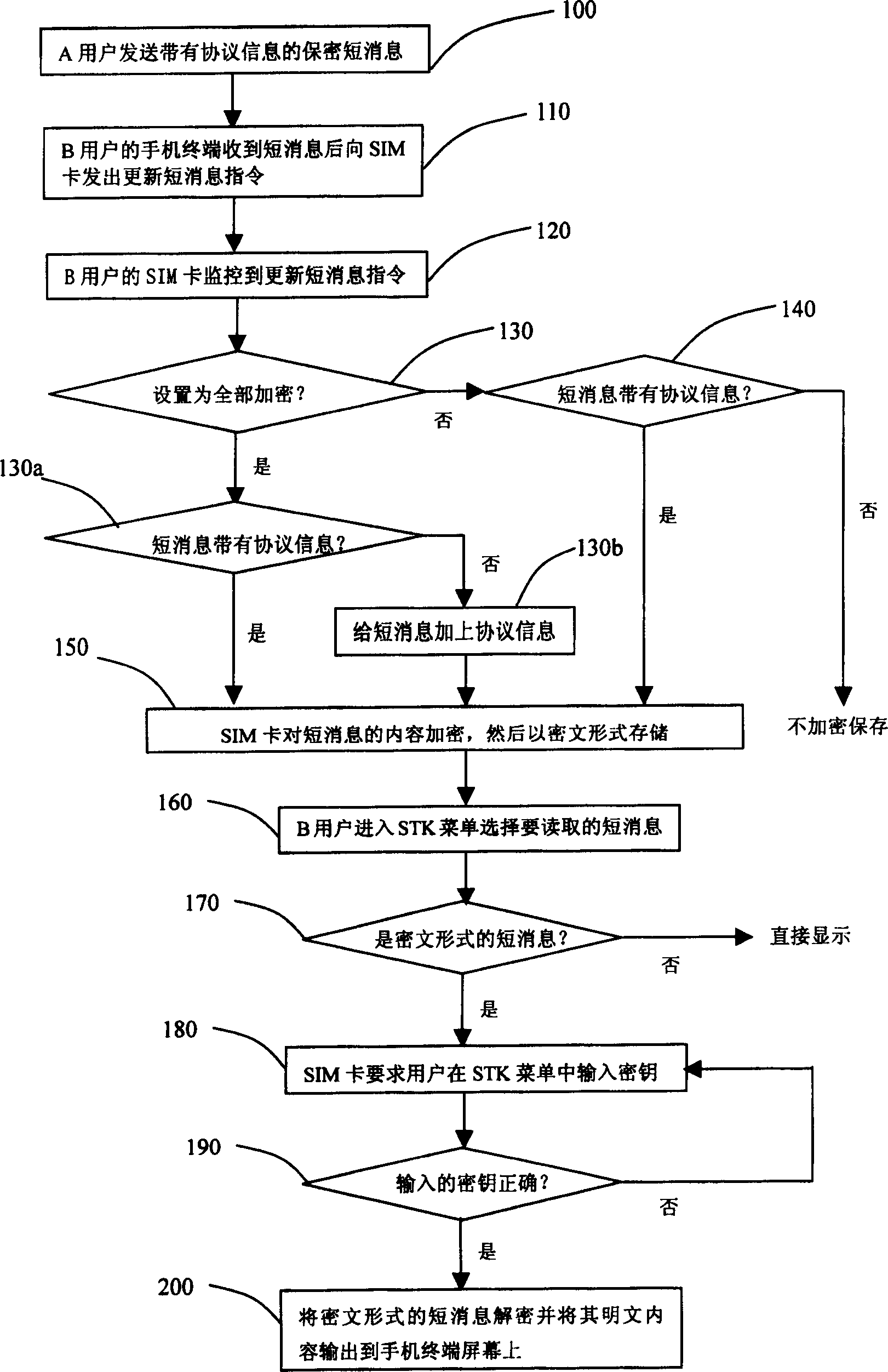
[0060] The receiver of this embodiment can choose to set the method of adopting all confidentiality or agreement confidentiality for the received short message. Such as figure 2 As shown, the short message security method of this embodiment includes the following steps:
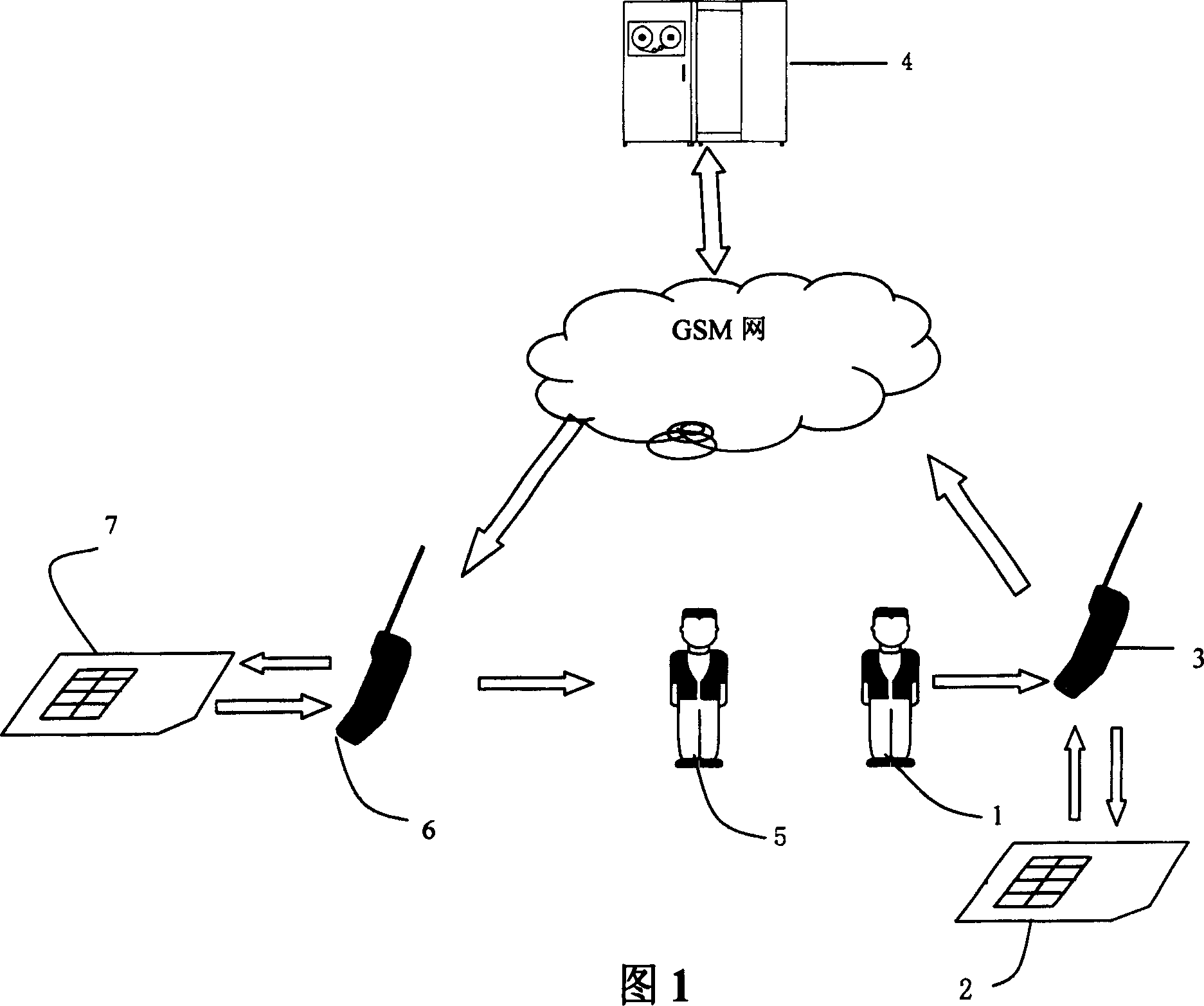
[0061] Step 100: User A chooses to send a confidential short message through the STK menu, the SIM card adds protocol information to the content of the short message, and then sends it to the short message center through the mobile terminal;
[0062] Step 110: The short message center forwards the short message to the mobile phone terminal of user B, and the mobile phone terminal of user B initiates an update short message instruction to the SIM card;
[0063] The above is the sending process.
[0064] Step 120, the SIM card of user B monitors the update short message instruction;
[0065] Step 130: Determine whether the current setting is full encryption?
[0066] If yes, read the short message data and determi...
no. 2 example
[0099] This embodiment adopts a full encryption method, and the process is as follows Figure 5 As shown, the contents of steps 100-2~200-2 are the same as figure 2 The corresponding steps are the same.
[0100] When sending, the sending method of the first embodiment is adopted, but it can also be sent directly through a mobile phone;
[0101] During the receiving process, there is no need to determine whether there is agreement information in the current security mode setting and the short message, that is, it is cancelled. figure 2 In steps 130 and 140, after the update short message instruction is monitored, all the received short messages are encrypted and stored in 6F3C in the form of ciphertext;
[0102] During the reading process, there is no need to judge whether the read short message is a cipher text short message, that is, cancel figure 2 In step 170, the other steps of selecting read, identity verification and decryption display are the same, and the transfer opera...
no. 3 example
[0108] This embodiment adopts a fixed protocol encryption method, and the process is as follows Figure 7 As shown, the contents of steps 100-3~200-3 are figure 2 The corresponding steps are the same.
[0109] The sending process is the same as that of the first embodiment;
[0110] During the receiving process, the judgment of the selection setting is not performed, that is, cancel figure 2 In step 130, after receiving the short message, the steps for judging and encrypting and storing the short message with the protocol information are the same as the first embodiment;
[0111] The reading process is the same as that of the first embodiment, which consists of the steps of selecting to read, judging whether a short message in ciphertext form, identity verification and decryption display, etc., and subsequent dump operations can also be performed.
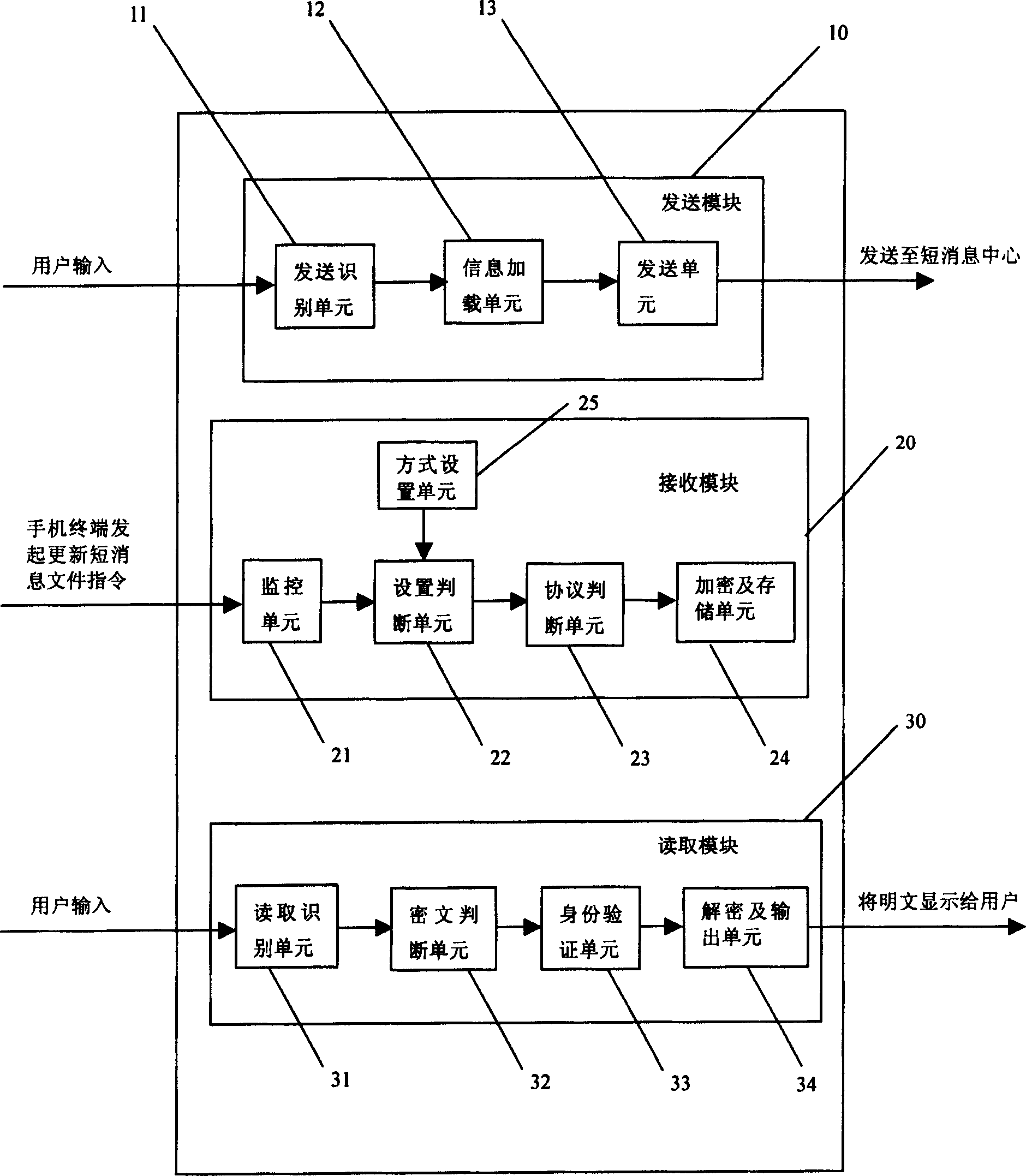
[0112] The following describes the structure of the SIM card used to implement the short message security method of this embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com