Identification mode of contents file producer and its program
An authentication method and producer's technology, applied in user identity/authority verification, digital data processing components, preventing unauthorized use of memory, etc., can solve problems such as unrealistic direct communication between content creators and receivers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
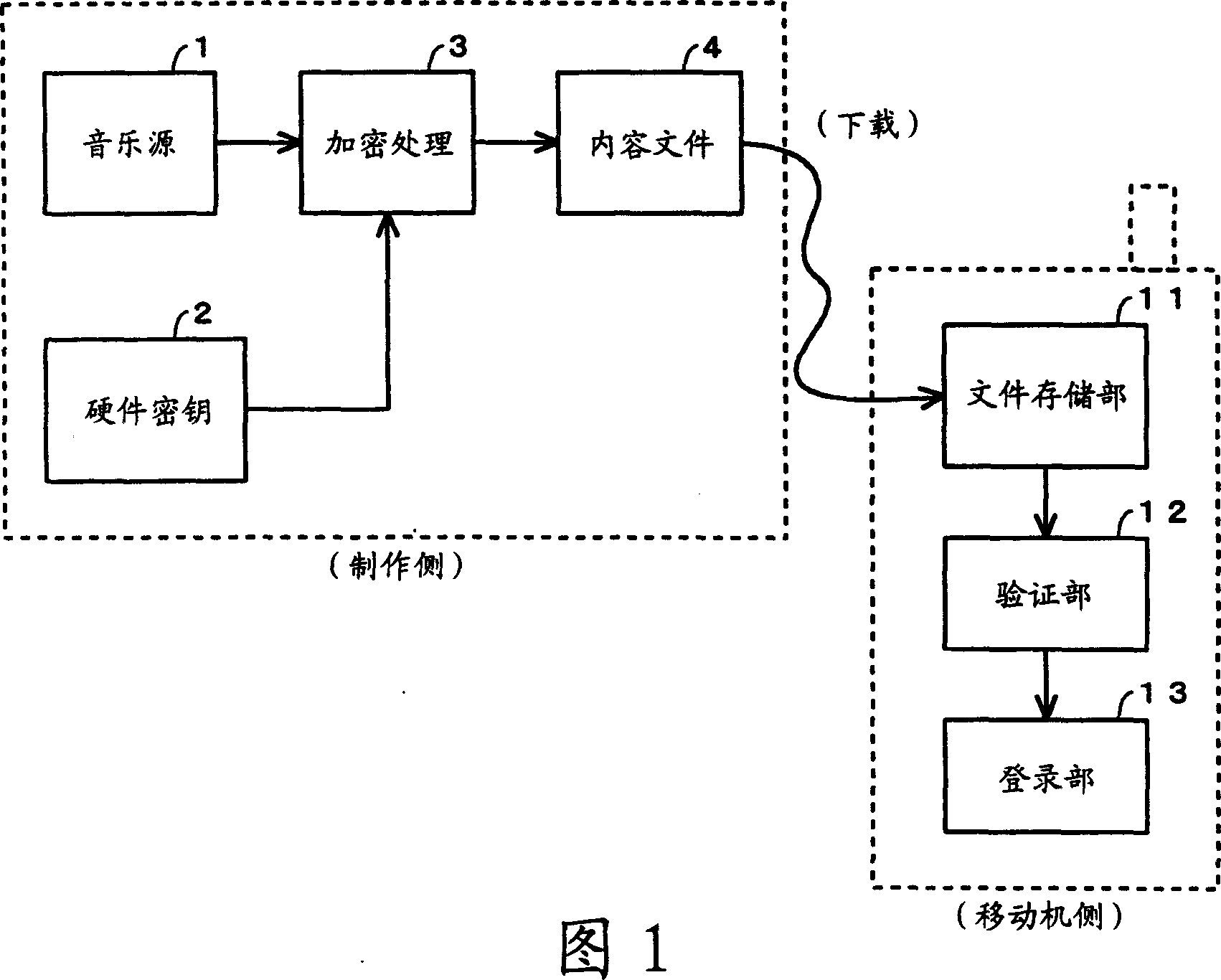
[0026] Hereinafter, the present invention will be described in detail with reference to the accompanying drawings. FIG. 1 is a schematic system diagram of a service for providing multimedia content files for mobile phones using the present invention.
[0027] The sending side (creating side) of the content file applies a certain hardware key 2 (secret information held only by the producing side) to the content data, such as the music source 1, performs encryption processing 3, and obtains the content file 4. That is, the sending side (creating side) creates the content file 4 with its own content creation tool (including the hardware key 2 and the encryption process 3).
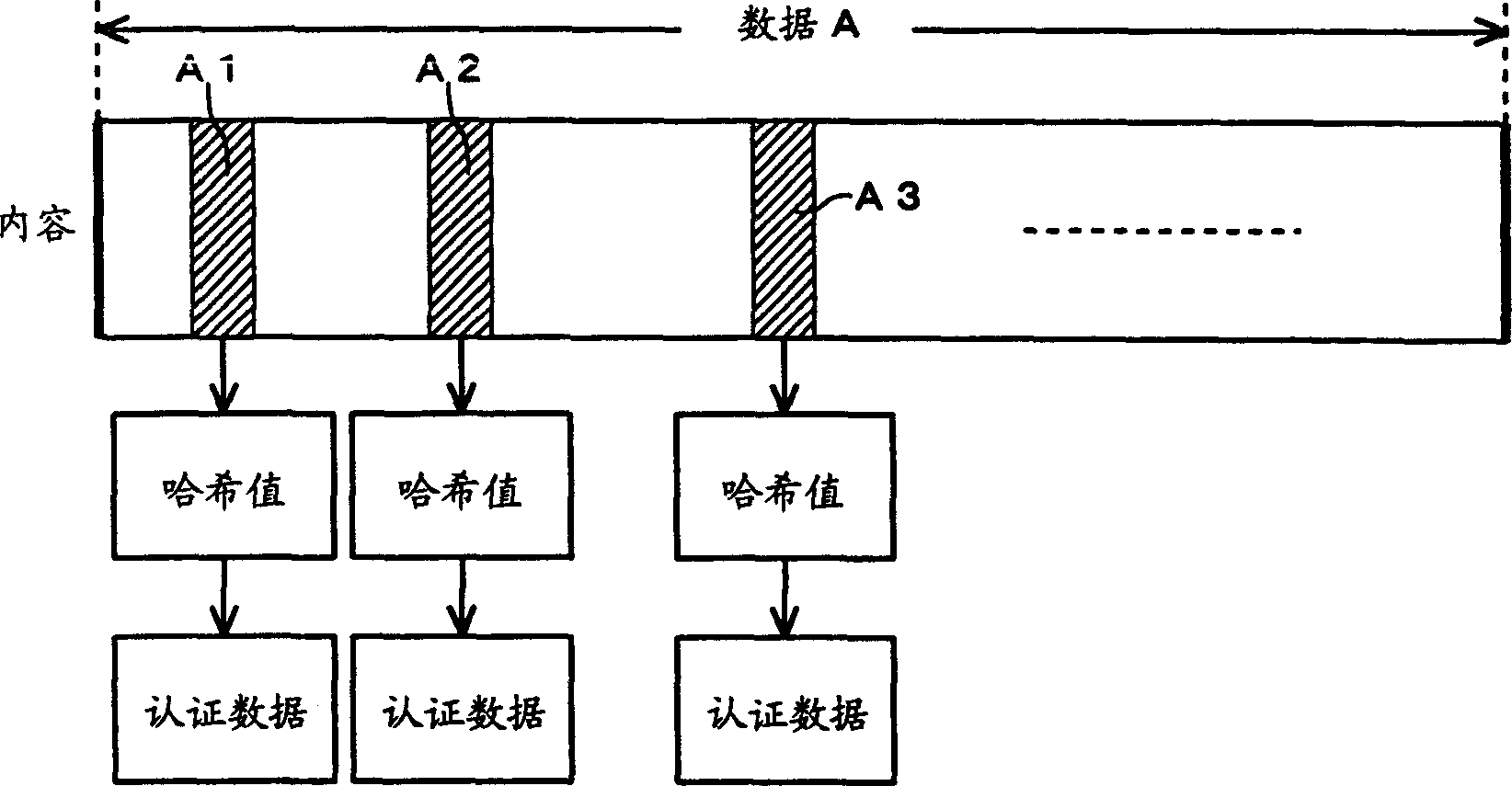
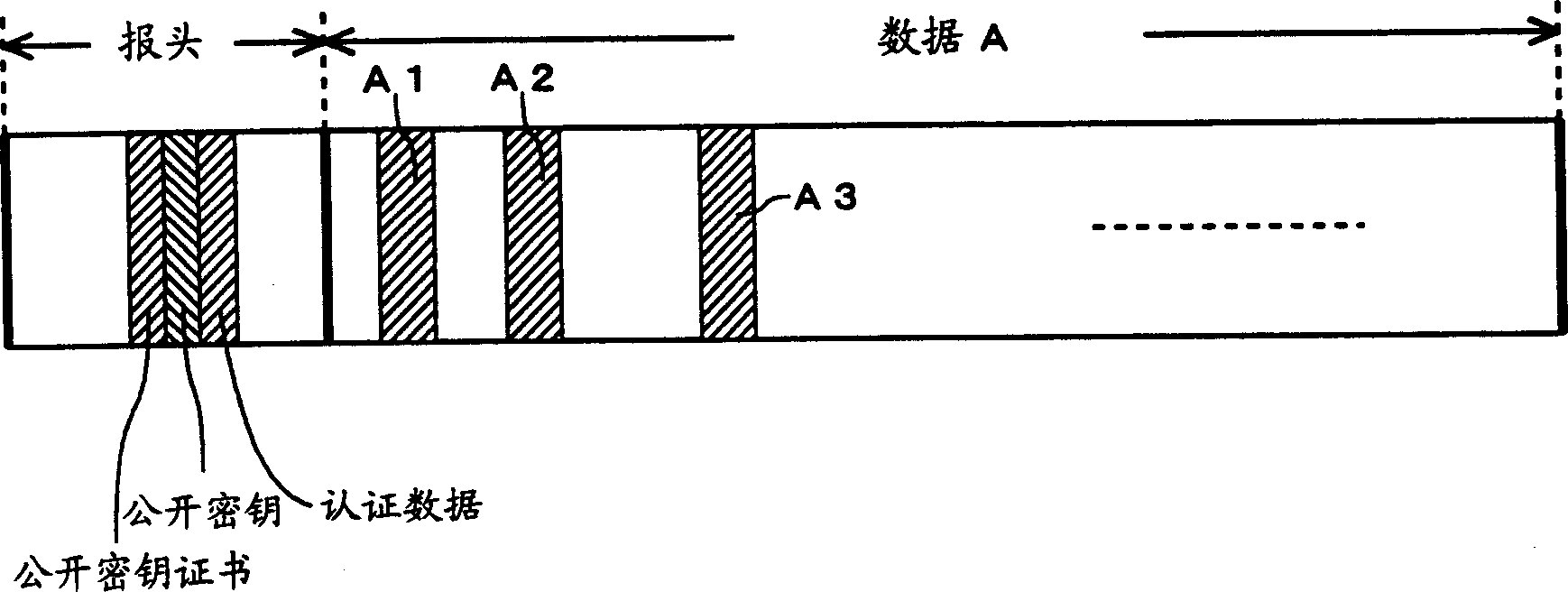
[0028] On the other hand, the receiving side (mobile device side) downloads the content file 4 and temporarily stores it in the file storage unit 11 . The verification unit 12 verifies whether the downloaded content file is created by an authorized authoring tool, and if it is verified that it was created by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com